FOCUS FRIDAY: TPRM CHALLENGES IN THE FACE OF IVANTI ICS, CACTI, SONICWALL, CONFLUENCE, AND CITRIX VULNERABILITIES
Written by: Kat Desy
Written by: Ferhat Dikbiyik
Additional Contributions: Ferdi Gül and Yavuz Han
Edited by: Katherine Desy
Welcome to this week’s Focus Friday, where we delve into the intricate world of Third-Party Risk Management (TPRM) through the lens of high-profile cybersecurity incidents. In this edition, we cast a spotlight on a range of critical vulnerabilities impacting widely used systems like Ivanti ICS, Cacti, SonicWall, Confluence Data Center and Server, and Citrix ADC/Gateway. As TPRM professionals, it’s crucial to stay informed and prepared against these evolving threats. We’ll explore these vulnerabilities, understand their implications, and provide insights on how Black Kite’s Focus Tags™ aid in navigating these complex challenges.
Ivanti ICS: Critical Command Injection and High Authentication Bypass Vulnerabilities
What are the CVE-2024-21887 and CVE-2023-46805 Vulnerabilities in Ivanti ICS?
Ivanti Connect Secure (ICS), previously known as Pulse Connect Secure and Ivanti Policy Secure gateways, faces two significant vulnerabilities: CVE-2024-21887 and CVE-2023-46805. The first, a command injection vulnerability with a CVSS score of 9.1, allows unauthorized remote execution via a file upload function flaw. This vulnerability affects versions 9.x and 22.x. The second, CVE-2023-46805, is an authentication bypass vulnerability, rated high severity with a CVSS score of 8.2, stemming from a flaw in the authorization function. These vulnerabilities can lead to full remote server control, data theft, and malware execution.
Why Should TPRM Professionals Pay Attention to These Ivanti ICS Vulnerabilities?
These vulnerabilities are critical for TPRM professionals to monitor. They pose significant risks including unauthorized remote control, data theft, and potential participation in malicious activities like botnet joining or malware distribution. Furthermore, the exploitation of these vulnerabilities by a Chinese nation-state level threat actor, UTA0178, underscores their severity.
Key Questions for Vendors Regarding Ivanti ICS Vulnerabilities
TPRM professionals should ask vendors specific questions:
- Have you assessed your systems for the presence of Ivanti Connect Secure versions 9.x and 22.x?
- What measures are in place to detect and mitigate unauthorized access or command execution via these vulnerabilities?
- Can you provide a timeline for patching these vulnerabilities in your systems?
- How are you monitoring for potential exploitation or suspicious activities related to these vulnerabilities?
Remediation Recommendations for Vendors
Vendors should:
- Promptly install updates once patches are available.
- Implement strong password policies for gateways.
- Restrict gateway access to trusted users only.
- Vigilantly monitor network traffic for anomalies.
- Apply available workarounds if the latest version is not released.
How TPRM Professionals Can Leverage Black Kite for Ivanti ICS Vulnerabilities
Black Kite published this tag on as early as January 11, 2024, providing actionable intelligence for TPRM professionals. By identifying vendors using affected Ivanti ICS versions and offering detailed asset information, Black Kite enables targeted risk management, minimizing the impact of these vulnerabilities.
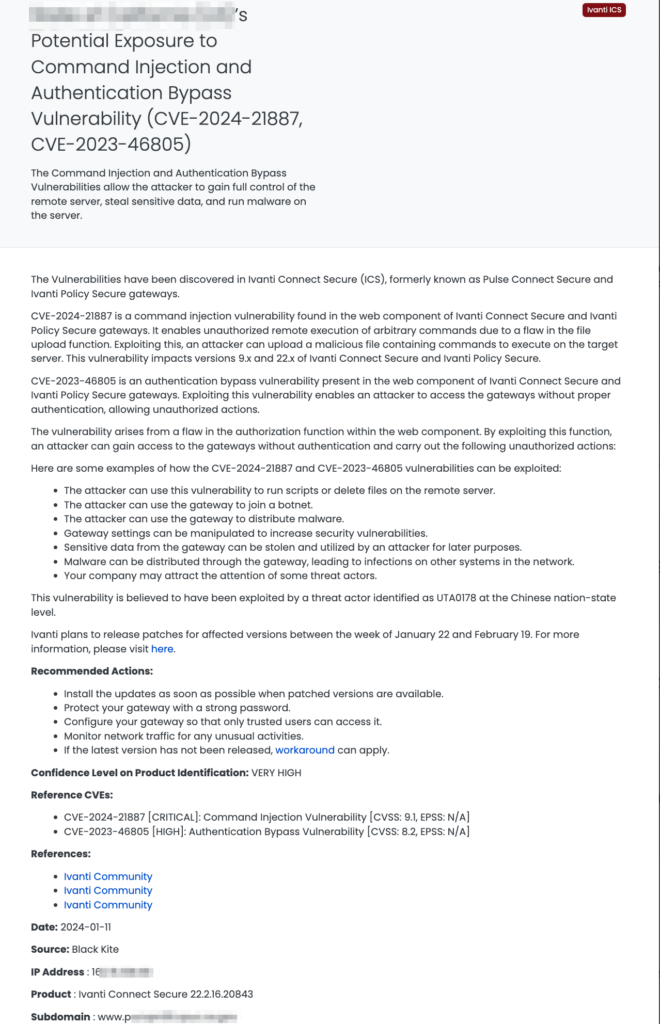
Cacti SQLi: High-Risk Blind SQL Injection Vulnerability
What is the CVE-2023-51448 Vulnerability in Cacti?
CVE-2023-51448 is a high-severity Blind SQL Injection (SQLi) vulnerability in Cacti, specifically affecting version 1.2.25. It has a CVSS score of 8.8 and an EPSS probability of 0.071%. This vulnerability allows an authenticated attacker with ‘Settings/Utilities’ permission to execute arbitrary SQL commands on the Cacti database. It was first reported by Synopsys CyRC researcher Matthew Hogg. The vulnerability occurs due to unsanitized input in the ‘selected_graphs_array’ parameter of a GET request, leading to potential disclosure of sensitive database contents and other severe impacts.
Why Should TPRM Professionals Be Concerned About CVE-2023-51448?
This vulnerability poses a significant risk for unauthorized data access and manipulation within the Cacti monitoring tool. TPRM professionals must be vigilant, as the exploitation of this flaw could lead to sensitive data theft, unauthorized modification of user accounts or configurations, and even potential arbitrary code execution, depending on the database setup.
Essential Questions for Vendors Regarding CVE-2023-51448
TPRM professionals should query vendors with specific concerns:
- Have you identified the use of Cacti version 1.2.25 within your network?
- What measures have you implemented to prevent unauthorized SQL command execution through this vulnerability?
- Can you detail your upgrade plans to patch this vulnerability?
- How do you monitor and detect any potential exploitation attempts related to CVE-2023-51448?
Remediation Recommendations for Affected Vendors
Vendors should:
- Upgrade to Cacti version 1.2.26 or later, which addresses this vulnerability.
- Limit access to the ‘Settings/Utilities’ permission required for exploiting this flaw.
- Enforce strong password policies to reduce the risk of unauthorized access.
- Continuously monitor network activities for signs of exploitation or unusual changes.
Leveraging Black Kite for CVE-2023-51448 Management
Published by Black Kite on January 11, 2024, this Focus Tag™ enables TPRM professionals to effectively identify and manage vendors using vulnerable Cacti versions. Black Kite’s detailed intelligence, including asset-specific risk information like IP addresses and subdomains, provides a significant advantage in targeting and mitigating this high-risk vulnerability.
SonicWall SonicOS: Critical Stack-Based Buffer Overflow Vulnerabilities
What are CVE-2023-0656 and CVE-2022-22274 in SonicWall SonicOS?
SonicWall SonicOS faces two significant vulnerabilities: CVE-2023-0656 and CVE-2022-22274. Both are stack-based buffer overflow vulnerabilities, with CVE-2023-0656 rated as high (CVSS: 7.5, EPSS: 0.115%) and CVE-2022-22274 as critical (CVSS: 9.8, EPSS: 0.366%). CVE-2023-0656 allows a remote unauthenticated attacker to cause a Denial of Service (DoS), potentially crashing the firewall. CVE-2022-22274, on the other hand, not only poses a DoS threat but also allows for potential remote code execution (RCE), enabling an attacker to take control of the affected device. These vulnerabilities primarily impact the web management interface of SonicWall firewalls.
Why Should TPRM Professionals Be Concerned About These SonicWall SonicOS Vulnerabilities?
These vulnerabilities are crucial for TPRM professionals due to their potential impact on network security. The risks include DoS attacks, which could disrupt critical business operations, and RCE, which could lead to data theft, unauthorized system control, and further malicious activities. With over 178,000 SonicWall firewalls potentially exposed, the scope of these vulnerabilities is significant.
Key Questions for Vendors Regarding SonicWall SonicOS Vulnerabilities
TPRM professionals should inquire with vendors about:
- Confirmation of the use of SonicWall SonicOS in their infrastructure and the versions in use.
- Steps taken to patch or mitigate the vulnerabilities, especially in light of their severity.
- Strategies in place to detect and respond to potential exploitation attempts.
- The status of their network security in relation to the SonicWall vulnerabilities, including any incident response plans.
Remediation Recommendations for Vendors
Vendors should:
- Update SonicWall Firewall to the fixed version.
- Restrict access to the web management interface to mitigate risks.
- Use a firewall or antivirus program to provide additional layers of security.
- Regularly review and update security settings to prevent exploitation.
- Monitor network traffic for signs of unusual activities or potential attacks.
Leveraging Black Kite for SonicWall SonicOS Vulnerability Management
Published on January 16, 2024, by Black Kite, this Focus Tag™ highlights the importance of these vulnerabilities for TPRM professionals. It enables them to identify and address the risks posed by the affected SonicWall devices in their vendor’s networks. By providing comprehensive asset information, including IP addresses and subdomains associated with the vulnerabilities, Black Kite offers a significant advantage in efficiently managing these risks.

Confluence Data Center and Server: Critical and High Template Injection Vulnerabilities
What are CVE-2023-22527 and CVE-2023-22522 in Confluence Data Center and Server?
Confluence Data Center and Server have been identified with two severe vulnerabilities: CVE-2023-22527 and CVE-2023-22522. CVE-2023-22527, a critical vulnerability (CVSS: 10), involves template injection leading to Remote Code Execution (RCE). It allows unauthenticated attackers to execute arbitrary code on affected instances. CVE-2023-22522, a high-severity vulnerability (CVSS: 8.8, EPSS: 0.11%), also involves RCE through template injection. These vulnerabilities are particularly dangerous because they enable attackers to gain access to and modify system files, compromise user accounts, distribute ransomware, and utilize a botnet.
Why Should TPRM Professionals Be Concerned About These Confluence Vulnerabilities?
The critical nature of these vulnerabilities, especially their potential for RCE, makes them a significant concern for TPRM professionals. The vulnerabilities can lead to severe consequences, including data breaches, system compromise, and the spread of malware. Given the widespread use of Confluence in enterprise environments, the impact could be extensive and damaging.
Key Questions for Vendors Regarding Confluence Vulnerabilities
TPRM professionals should focus on the following questions:
- Are you currently using any affected versions of Confluence Data Center and Server?
- What steps have you taken to patch or mitigate these vulnerabilities?
- Can you provide details on how you are monitoring your Confluence environment for signs of exploitation?
- What are your incident response plans in case of an exploitation attempt?
Remediation Recommendations for Affected Vendors
Vendors should:
- Immediately patch to the latest version of Confluence.
- Disable the “Confluence Data Templates” feature as a temporary workaround.
- Enable Confluence’s Content Security Policy (CSP) settings.
- Run Confluence through a proxy or WAF.
- Limit access to the Confluence admin interface.
- Regularly backup Confluence data and be prepared for rapid recovery.
- Monitor access logs and network traffic for suspicious activities.
Leveraging Black Kite for Confluence Vulnerability Management
Black Kite published this tag on December 7, 2023, and updated it on January 16, 2024, highlighting the ongoing relevance of these vulnerabilities. TPRM professionals can utilize Black Kite’s intelligence to identify vendors using affected Confluence versions and manage the associated risks. Black Kite’s asset-specific information, including IP addresses and subdomains, offers a distinct advantage in efficiently addressing these vulnerabilities.

Citrix ADC/Gateway: New and Ongoing Critical Vulnerabilities
What are the Latest Vulnerabilities in Citrix ADC/Gateway?
Citrix ADC and Gateway devices are facing new vulnerabilities: CVE-2023-6549 (Buffer Overflow, HIGH, CVSS: 8.2) and CVE-2023-6548 (Code Injection, MEDIUM, CVSS: 5.5). These vulnerabilities are in addition to the previously identified critical vulnerabilities CVE-2023-3519 (Unauthenticated RCE, CRITICAL, CVSS: 9.8, EPSS: 89.042%) and CVE-2023-4966 (Information Disclosure, CRITICAL, CVSS: 9.4, EPSS: 92.52%), known as CitrixBleed. These vulnerabilities have been exploited by ransomware groups like Lockbit, leading to significant security concerns.
In response to these critical vulnerabilities, CISA added these vulnerabilities to its KEV Catalog, urging federal agencies to patch Citrix RCE within a week, emphasizing the urgency and severity of these vulnerabilities.
Why is Focus on These New Vulnerabilities Crucial for TPRM Professionals?
The introduction of new vulnerabilities, combined with the critical nature of the existing ones, escalates the risks associated with Citrix products. Given their wide usage, the potential for exploitation leading to data breaches, system compromise, and malicious activities is high. The historical exploitation of CitrixBleed by threat actors amplifies the need for an immediate and vigilant response from TPRM professionals.
Key Questions for Vendors Regarding Citrix ADC/Gateway Vulnerabilities
- Have you assessed the impact of the new vulnerabilities, CVE-2023-6549 and CVE-2023-6548, in your Citrix products?
- What measures are in place to mitigate both the new and existing vulnerabilities, especially in light of past exploitations?
- Can you detail your monitoring processes for detecting signs of exploitation related to these vulnerabilities?
- How have you updated your incident response strategies in response to these vulnerabilities?
Remediation Recommendations for Affected Vendors
- Prioritize updating to the latest versions of Citrix ADC and Gateway.
- Implement strict access control and firewall configurations to safeguard against unauthorized access.
- Conduct regular audits and reviews of device logs for abnormal activities.
- Isolate the management interface from regular network traffic and avoid its exposure to the internet.
- Engage in proactive network traffic monitoring to detect potential exploits.
Leveraging Black Kite for Enhanced Management of Citrix Vulnerabilities
Black Kite’s Focus Tag™, updated on January 17, 2024, incorporates these new vulnerabilities while still acknowledging the previously identified critical vulnerabilities exploited by ransomware groups. This comprehensive approach enables TPRM professionals to adopt a holistic strategy in managing the risks associated with Citrix ADC and Gateway devices. Black Kite’s detailed asset information, including insights into affected IP addresses and subdomains, empowers TPRM professionals to target their risk mitigation efforts effectively.
ENHANCING TPRM STRATEGIES WITH BLACK KITE’S FOCUS TAGS™
In an era where cybersecurity threats are both rampant and sophisticated, Black Kite’s Focus Tags™ emerge as a beacon of clarity and actionability for Third-Party Risk Management (TPRM) professionals. This week’s focus on diverse vulnerabilities like those in Ivanti ICS, Cacti SQLi, and SonicWall SonicOS exemplifies the critical role of these tags. Here’s how they redefine TPRM dynamics:
- Prompt Vulnerability Insight: The immediate identification of affected vendors by these vulnerabilities allows TPRM teams to react swiftly, minimizing potential impacts.
- Risk Prioritization and Allocation: By correlating the severity of vulnerabilities with vendor importance, Focus Tags™ guide professionals in efficiently allocating their resources and efforts.
- Informed and Specific Vendor Dialogues: These tags enable TPRM professionals to engage in pointed discussions with vendors, directly addressing their exposure and defense strategies against these specific vulnerabilities.
- Comprehensive Threat Landscape Overview: Black Kite’s Focus Tags™ offer a panoramic view of current threats, enhancing the overall cybersecurity strategy and defense mechanism.
Through the lens of this week’s highlighted vulnerabilities, Black Kite’s Focus Tags™ demonstrate their indispensable value in transforming intricate cyber threat intelligence into practical, strategic insights. This capability is pivotal for TPRM professionals aiming to navigate and manage risks in an ever-evolving cybersecurity environment proactively and effectively.
Want to take a closer look at Focus Tags™?
Take our platform for a test drive and request a demo today.
Focus Tags™ in the last 30 days:
- Redis RCE: CVE-2023-41056, Remote Code Execution Vulnerability
- Ivanti ICS: CVE-2024-21887, Command Injection Vulnerability, CVE-2023-46805, Authentication Bypass Vulnerability
- Cacti SQLi: CVE-2023-51448, Blind SQL Injection (SQLi) Vulnerability
- Juniper OS:CVE-2024-21591 [Updated Tag], Remote Code Execution Vulnerability
- Kyocera Device Manager [Suspected]:CVE-2023-50916, Path Traversal Vulnerability
- Apache Tomcat:CVE-2023-46589, Improper Input Validation Vulnerability
- Laravel [Suspected]:CVE-2018-15133, Deserialization of Untrusted Data Vulnerability
- SonicWall SonicOS: CVE-2023-0656, A Stack-Based Buffer Overflow Vulnerability, DOS Attack, RCE Vulnerability
- Confluence Data Center and Server:CVE-2023-22527 [Updated Tag], Template Injection Vulnerability
- Citrix ADC/Gateway:CVE-2023-6549 [Updated], Buffer Overflow Vulnerability
- Adobe ColdFusion: CVE-2023-29300 and CVE-2023-38203, Deserialization of Untrusted Data Vulnerability [Updated]
- Joomla: CVE-2023-23752, Improper Access Control Vulnerability in Joomla
- Apache Superset Auth. Bypass: CVE-2023-27524, Insecure Default Initialization of Resource Vulnerability in Apache Superset
- NextCloud Servers: CVE-2023-49792, Trusted Proxy Remote Address Spoofing Vulnerability in Nextcloud Server and Enterprise Server
- Redis RCE: CVE-2023-41056, Remote Code Execution Vulnerability
- Ivanti ICS: CVE-2024-21887, Command Injection Vulnerability, CVE-2023-46805, Authentication Bypass Vulnerability
- Cacti SQLi: CVE-2023-51448, Blind SQL Injection (SQLi) Vulnerability
- Barracuda ESG: CVE-2023-7102, Parameter Injection Vulnerability
- Mlflow: CVE-2023-6753, A Path Traversal Vulnerability in MLflow.
References:
https://www.volexity.com/blog/2024/01/15/ivanti-connect-secure-vpn-exploitation-goes-global/
https://nvd.nist.gov/vuln/detail/CVE-2023-51448
https://github.com/Cacti/cacti/security/advisories/GHSA-w85f-7c4w-7594
https://bishopfox.com/blog/its-2024-and-over-178-000-sonicwall-firewalls-are-publicly-exploitable
https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2022-0003
https://nvd.nist.gov/vuln/detail/CVE-2022-22274
https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2023-0004
https://nvd.nist.gov/vuln/detail/CVE-2023-0656
https://confluence.atlassian.com/pages/viewpage.action
https://support.citrix.com/article/CTX561482/citrix-adc-and-citrix-gateway-security-bulletin-for-cve20233519-cve20233466-cve20233467 https://www.bleepingcomputer.com/news/security/cisa-pushes-federal-agencies-to-patch-citrix-rce-within-a-week/

