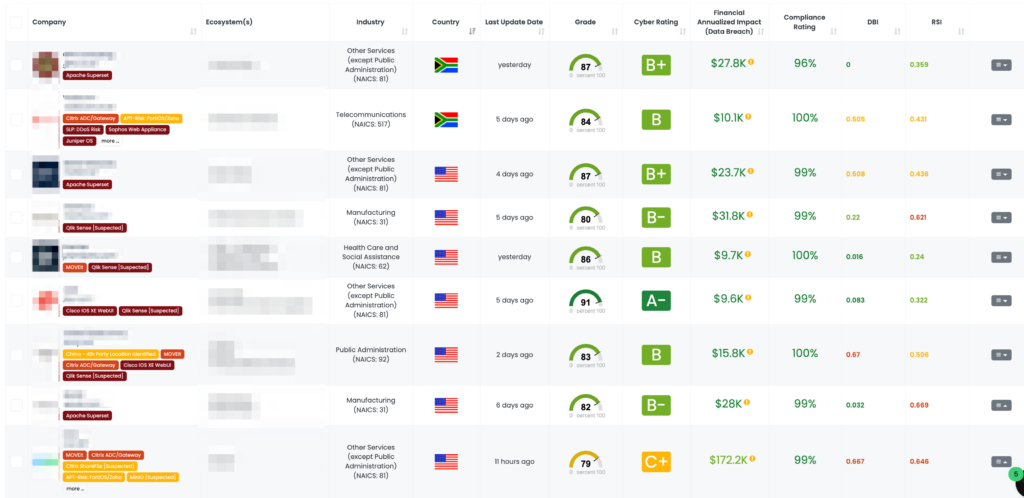
Focus Friday: Third-Party Risks in Qlik Sense, Adobe ColdFusion, and Atlassian Confluence Vulnerabilities
Written by: Kat Desy
Written by: Ferhat Dikbiyik
Additional Contributions: Ferdi Gül and Yavuz Han
Edited by: Katherine Desy
Welcome to another insightful edition of Focus Friday, where we continue to bridge Third-Party Risk Management (TPRM) with cutting-edge cyber intelligence. In this week’s exploration, we delve into the realm of software vulnerabilities, spotlighting recent challenges in Qlik Sense, Adobe ColdFusion, and Atlassian Confluence. Leveraging Black Kite’s Focus Tags™, we aim to shed light on the intricacies of these vulnerabilities, offering a deeper understanding of their impact on vendor networks. These insights are not just about identifying risks but also about empowering TPRM professionals with the knowledge needed to fortify their defenses against these evolving digital threats.
Qlik Sense Vulnerabilities: Assessing the TPRM Impact of Recent Exploits
What are the recent Qlik Sense vulnerabilities?
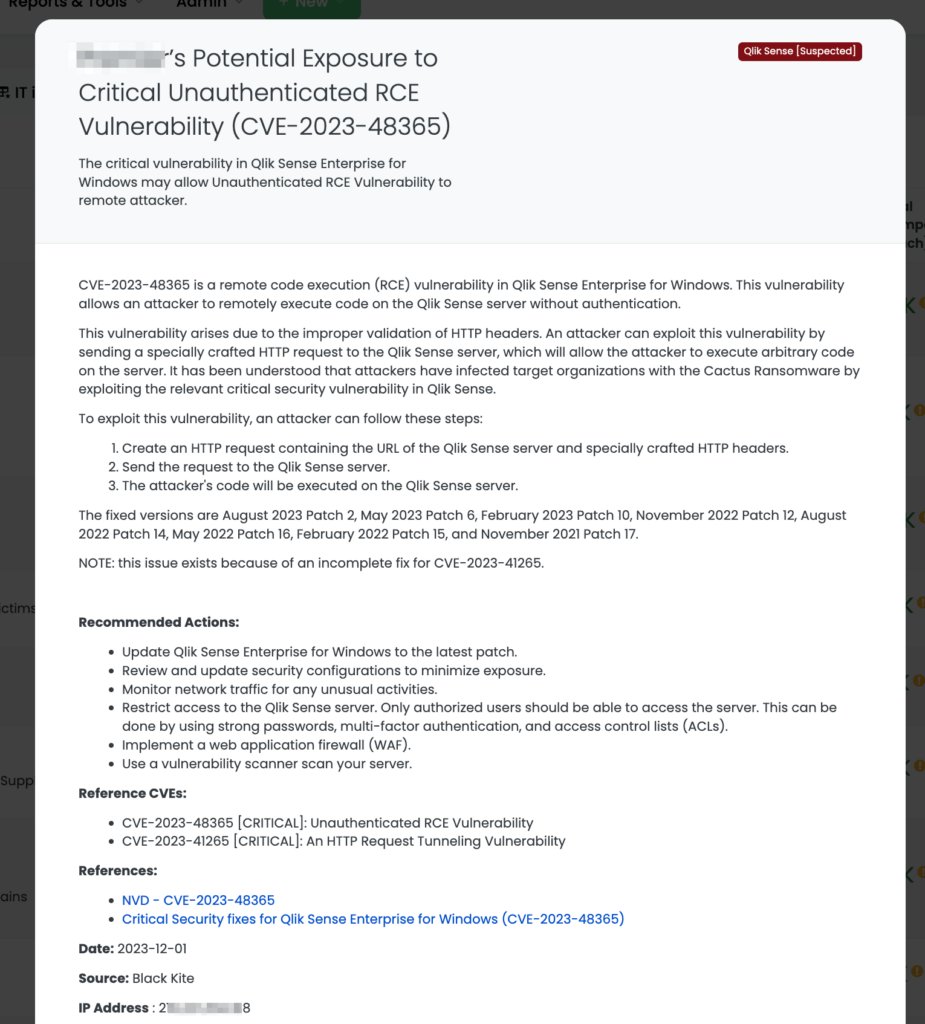
The recent Qlik Sense vulnerabilities, CVE-2023-41266 and CVE-2023-41265, have been notably exploited in a ransomware campaign by the Cactus group. CVE-2023-41266 is a path traversal issue, and CVE-2023-41265 allows for privilege escalation and remote code execution. Both vulnerabilities were added to the CISA’s Known Exploited Vulnerabilities (KEV) Catalog on December 7.
Analysis by the Black Kite Research team on Cactus’s dark web blog reveals 65 victims, predominantly in the US and Europe, with significant impacts on the Manufacturing and Professional Services sectors. Most victims are small to medium-sized enterprises, with 60% having an annual revenue below $50 million, and 73% below $100 million. This exploitation pattern highlights the vulnerabilities’ profound impact on small and medium businesses across various industries.
TPRM Perspective on Qlik Sense Vulnerabilities and the Cactus Ransomware Campaign
The recent exploitation of Qlik Sense vulnerabilities by the Cactus ransomware group presents a unique challenge from a Third-Party Risk Management (TPRM) perspective. This situation highlights the necessity for TPRM professionals to evaluate not only the direct risks associated with software vulnerabilities but also the indirect risks posed by their exploitation, particularly by ransomware groups. The Cactus group’s focus on smaller enterprises, especially in the US and Europe, underscores the need for TPRM teams to assess their vendors’ cybersecurity measures, especially those using Qlik Sense, and their potential susceptibility to such targeted attacks.
Given the specifics of the attack vectors used by Cactus, such as privilege escalation and path traversal, TPRM professionals should thoroughly evaluate their vendors for any signs of compromise and ensure that they have implemented robust security measures. It is crucial for TPRM strategies to evolve with these emerging threats, encompassing a broader spectrum of risk factors, including ransomware susceptibility, vendor size, industry, and geographical location. This comprehensive approach is essential for mitigating risks and safeguarding against the multifaceted nature of cyber threats in today’s interconnected digital landscape.
What Questions Should TPRM Professionals Ask Vendors Using Qlik Sense in Light of the Cactus Ransomware Campaign?
In response to the Cactus ransomware campaign exploiting Qlik Sense vulnerabilities, TPRM professionals should ask more specific questions:
- “Have you identified any indications of compromise related to CVE-2023-41266, CVE-2023-41265, or CVE-2023-48365 in your Qlik Sense deployments?”
- “What specific actions have you taken to mitigate the risks associated with these vulnerabilities since their disclosure?”
- “Can you provide details on any incident response plans or security upgrades implemented following the Cactus ransomware campaign revelations?”
- “How are you ensuring that your Qlik Sense environment remains resilient against similar ransomware threats in the future?”
Remediation Steps for Vendors Subject to These Vulnerabilities
For vendors using Qlik Sense Enterprise for Windows, the following remediation steps are recommended:
- Update Qlik Sense to the latest patch as specified by the vendor, addressing CVE-2023-48365 and related vulnerabilities.
- Conduct a thorough review and update of security configurations to minimize exposure risks.
- Implement continuous monitoring of network traffic to detect and respond to unusual activities.
- Restrict access to the Qlik Sense server, ensuring it’s accessible only to authorized personnel, with strong passwords, multi-factor authentication, and access control lists (ACLs).
- Consider deploying a web application firewall (WAF) and using a vulnerability scanner to regularly scan the server.
For more details on the vulnerabilities and recommended actions, see the Qlik Community advisory.
Leveraging Black Kite for Enhanced TPRM Strategy Amid Qlik Sense Vulnerabilities
Black Kite provides a comprehensive solution for TPRM professionals addressing the Qlik Sense vulnerabilities and associated ransomware risks. Not only does Black Kite help in identifying vendors that may be at risk, but it also pinpoints the specific IT assets that have Qlik Sense installed. Black Kite applied a Focus Tag™ for Qlik Sense on December 1, 2023.
This targeted information enables TPRM teams to:
- Quickly focus their risk assessment and mitigation efforts on the most relevant vendors.
- Engage in detailed discussions with these vendors about specific assets that need urgent attention and patching.
- Monitor the ongoing compliance and security posture of these identified assets to prevent future vulnerabilities.
- This approach ensures a more efficient and focused TPRM strategy, enabling a robust defense against complex cybersecurity threats like the Cactus ransomware campaign.
In addressing the Qlik Sense vulnerabilities and the Cactus ransomware campaign, Black Kite offers a multifaceted approach to TPRM. Beyond identifying vendors using Qlik Sense and pinpointing the specific IT assets with the software installed, Black Kite’s Ransomware Susceptibility Index® (RSI™) plays a crucial role. The RSI™ assesses the likelihood of an organization falling victim to a ransomware attack using data and machine learning, considering factors like company size, industry, and existing vulnerabilities. By integrating RSI™ insights, TPRM professionals can prioritize and tailor their risk management strategies, focusing on vendors with higher susceptibility to ransomware threats like Cactus. This comprehensive approach, combining asset identification with ransomware risk assessment, provides a robust framework for TPRM in the face of evolving cyber threats.
For more details on RSI™, visit Black Kite’s RSI™ page.
Resurgence of Adobe ColdFusion Vulnerability: A TPRM Focus on CVE-2023-26360
What is Adobe ColdFusion CVE-2023-26360 vulnerability?
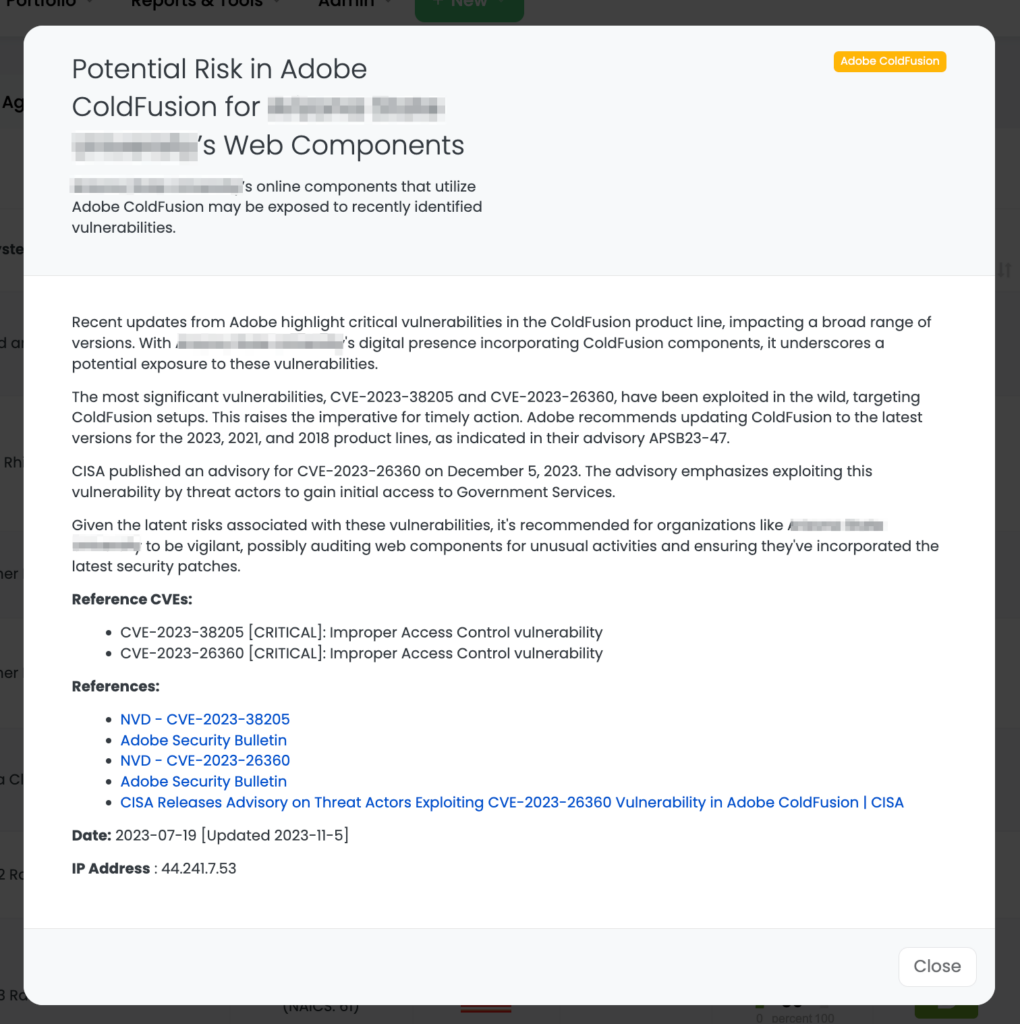
CVE-2023-26360 is a critical vulnerability in Adobe ColdFusion, with a CVSS base score of 9.8, indicating a severe level of threat. Characterized as an improper access control issue, its exploitation can result in arbitrary code execution. The severity of this vulnerability is underscored by its ability to allow attackers to bypass security controls and execute code, potentially leading to full system compromise, unauthorized data access, or further network infiltration.
CISA’s advisory on this vulnerability, released on December 5, 2023, was a response to its active exploitation, particularly targeting government servers. The advisory is crucial in highlighting the persistent risk and potential widespread impact of this vulnerability, particularly in high-value targets. It serves as a reminder of the importance of continuous vigilance and updated security measures, even for vulnerabilities that have been previously patched.
TPRM Strategies for Handling Adobe ColdFusion Vulnerabilities
In light of the recent CISA advisory and Adobe updates concerning vulnerabilities in ColdFusion, particularly CVE-2023-26360, TPRM professionals need to take specific actions to mitigate risks. These vulnerabilities, actively exploited in the wild, including government servers, underscore the importance of vigilance and proactive security measures for vendors using Adobe ColdFusion.
What Questions Should TPRM Professionals Ask Vendors Using Adobe ColdFusion?
TPRM professionals should inquire about vendors’ responses to these vulnerabilities:
- “Have you updated Adobe ColdFusion to the latest version as per Adobe’s recommendations for the 2023, 2021, and 2018 product lines?”
- “Can you confirm the implementation of security patches for CVE-2023-38205 and CVE-2023-26360?”
- “What measures have you taken to monitor and audit ColdFusion web components for unusual activities?”
Remediation Steps for Vendors Subject to These Vulnerabilities
For vendors utilizing Adobe ColdFusion, the following steps are recommended:
- Urgently update Adobe ColdFusion to the latest versions as outlined in Adobe’s APSB23-47 advisory.
- Apply security patches for the critical vulnerabilities CVE-2023-38205 and CVE-2023-26360 without delay.
- Regularly audit ColdFusion web components for any signs of unusual activities or potential breaches.
- Stay updated with the latest advisories from credible sources like Adobe and CISA, and ensure adherence to their recommendations.
These steps are crucial in mitigating the risks associated with CVE-2023-26360 and other related vulnerabilities, ensuring the security and integrity of the digital assets managed by Adobe ColdFusion.
Leveraging Black Kite for Adobe ColdFusion Vulnerability Management for TPRM
Black Kite’s capabilities are pivotal in effectively managing the risks associated with Adobe ColdFusion vulnerabilities, especially CVE-2023-26360. Initially, Black Kite provided Adobe ColdFusion tags on July 19 and subsequently updated them on December 5 following the CISA advisory.
Here’s how Black Kite aids in TPRM:
- Identification of Affected Vendors: Black Kite helps identify vendors using Adobe ColdFusion, enabling TPRM teams to focus their attention on potentially at-risk partners quickly.
- Specific Asset Tracking: By pinpointing the specific IT assets with Adobe ColdFusion, Black Kite allows for targeted risk assessments and remediation efforts.
- Continuous Monitoring and Updating: Black Kite’s platform ensures ongoing monitoring and updating of information regarding Adobe ColdFusion vulnerabilities, keeping TPRM teams informed about the latest developments and advisories.
- Operationalizing Advisory Information: With Black Kite, TPRM professionals can operationalize the information from CISA advisories and Adobe updates, integrating this data into their risk management strategies.
Utilizing Black Kite’s comprehensive approach allows organizations to stay ahead of potential threats posed by these vulnerabilities, ensuring that their third-party ecosystem remains secure and resilient.
Addressing the CVE-2023-22522 Vulnerability in Atlassian Confluence
Understanding CVE-2023-22522 in Atlassian Confluence
CVE-2023-22522, a critical template injection vulnerability in Atlassian Confluence Data Center and Server, was disclosed by Atlassian on December 5, 2023. This vulnerability, rated 9.0 (Critical) on the CVSS scale, allows an authenticated attacker, including one with anonymous access, to execute remote code on affected instances. Atlassian recommends patching to fixed versions as soon as possible to mitigate this vulnerability, which affects all versions from 4.0.0 onwards.
Questions TPRM Professionals Should Ask Regarding CVE-2023-22522
TPRM professionals should ask vendors using Atlassian Confluence the following questions:
- “Have you updated to the fixed versions of Confluence Data Center and Server as recommended by Atlassian?”
- “What measures have you taken to monitor and ensure no exploitation has occurred on your systems?”
- “How are you managing user access and authentication to prevent unauthorized template injections?”
Remediation Steps for CVE-2023-22522
Vendors using Atlassian Confluence should urgently:
- Patch their installations to the latest or fixed LTS versions specified by Atlassian.
- Implement monitoring protocols to detect any signs of exploitation.
- Review and enhance user access controls to prevent unauthorized injections.
- Establish robust incident response plans for timely action against future vulnerabilities.
Leveraging Black Kite for Atlassian Confluence CVE-2023-22522 Vulnerability Management in TPRM
In response to the Atlassian Confluence vulnerability CVE-2023-22522, Black Kite plays a crucial role in TPRM. Having provided a Focus Tag™ for this vulnerability on December 7, Black Kite enables TPRM professionals to:
- Identify Vulnerable Vendors: Determine which vendors in your network use affected versions of Atlassian Confluence.
- Focus on Specific Assets: Pinpoint the exact IT assets within vendor environments that are vulnerable, for targeted risk assessments.
- Prioritize Remediation Efforts: Utilize Black Kite’s insights to prioritize vendors based on the severity of their exposure and the criticality of their services.
- Monitor Compliance and Updates: Keep track of vendors’ patching and compliance status to ensure they are responding adequately to this critical vulnerability.
This approach helps TPRM teams efficiently manage and mitigate the risks associated with CVE-2023-22522, enhancing overall cybersecurity resilience.
Maximizing TPRM Effectiveness with Black Kite’s Focus Tags
Black Kite’s Focus Tags™ are crucial in enhancing Third-Party Risk Management (TPRM) strategies. They offer:
- Real-Time Risk Identification: Instantly spotlighting vendors impacted by critical vulnerabilities, enabling rapid response.
- Targeted Risk Prioritization: Helping prioritize risks based on vendor criticality and vulnerability severity.
- Informed Vendor Engagement: Facilitating deeper, more meaningful discussions with vendors about their security measures and response strategies.
- Comprehensive Security Posture Enhancement: Providing a holistic view of the threat landscape, thus allowing for more strategic and effective cybersecurity defenses.
The value of Black Kite’s Focus Tags™ lie in their ability to transform complex cyber threat information into actionable intelligence, driving more efficient and effective TPRM practices.
Want to take a closer look at Focus Tags™?
Take our platform for a test drive and request a demo today.
Focus Tags™ in the Last 30 days
- Atlassian Confluence Data Center and Server: CVE-2023-22522, Template Injection Vulnerability
- Adobe ColdFusion: CVE-2023-26360, Improper Access Control Vulnerability
- Qlik Sense: CVE-2023-48365, Unauthenticated RCE Vulnerability in Qlik Sense Enterprise for Windows
- Apache Superset: CVE-2023-40610, Privilege Escalation Vulnerability in Apache Superset <2.1.2 versions.
- OpenVPN Access: CVE-2023-46850, OpenVPN Access Server Flaw Exposes Sensitive Data and RCE Possible
- ownCloud: CVE-2023-49103, Information Disclosure Vulnerability in ownCloud’s Graphapi Component
- Atlassian Bamboo Data Center: CVE-2023-22516, RCE Vulnerability in Bamboo Data Center and Server Tagging
- Sophos Web Appliance: CVE-2023-1671 Pre-auth Command Injection Vulnerability in the version 4.3.10.3 and earlier
- Oracle Weblogic: CVE-2020-2551 Unauthenticated RCE Vulnerability over IIOP based on 10.3.6.0, 12.1.3.0, 12.2.1.3.0, 12.2.1.4.0
- Boeing Data Breach: Boeing Vendor Information disclosed in data breach
- Juniper Junos OS: CVE-2023–36845 Juniper Junos OS EX, SRX Series PHP External Variable Modification RCE Vulnerability
- SysAid: CVE-2023-47246 SysAid ITSM File System Path Traversal
- ServiceNow Data Exposure Flaw: ServiceNow clients
- SLP: CVE-2023-29552 LSP DOS
- Confluence: CVE-2023-22518 Confluence Data Center and Confluence Server Improper Authorization Vulnerability
- Apache ActiveMQ: CVE-2023-46604 Remote Code Execution Vulnerability
References:
https://arcticwolf.com/resources/blog/qlik-sense-exploited-in-cactus-ransomware-campaign/
https://www.securityweek.com/qlik-sense-vulnerabilities-exploited-in-ransomware-attacks/
https://nvd.nist.gov/vuln/detail/CVE-2023-48365
https://helpx.adobe.com/security/products/coldfusion/apsb23-25.html
https://nvd.nist.gov/vuln/detail/CVE-2023-22522
https://confluence.atlassian.com/pages/viewpage.action?pageId=1319570362

