Focus Friday: Snowflake-Linked Breaches from a TPRM Supply Chain Perspective
Written by: Ferhat Dikbiyik
The recent breaches connected to Snowflake’s cloud storage service have sent shockwaves through the cybersecurity community. With compromised credentials leading to unauthorized access and data theft, the ripple effect on supply chains is profound. In this Focus Friday, we explore the third-party risk management (TPRM) implications of these incidents, providing insights on how organizations can safeguard their vendor ecosystems using Black Kite’s FocusTagsTM.
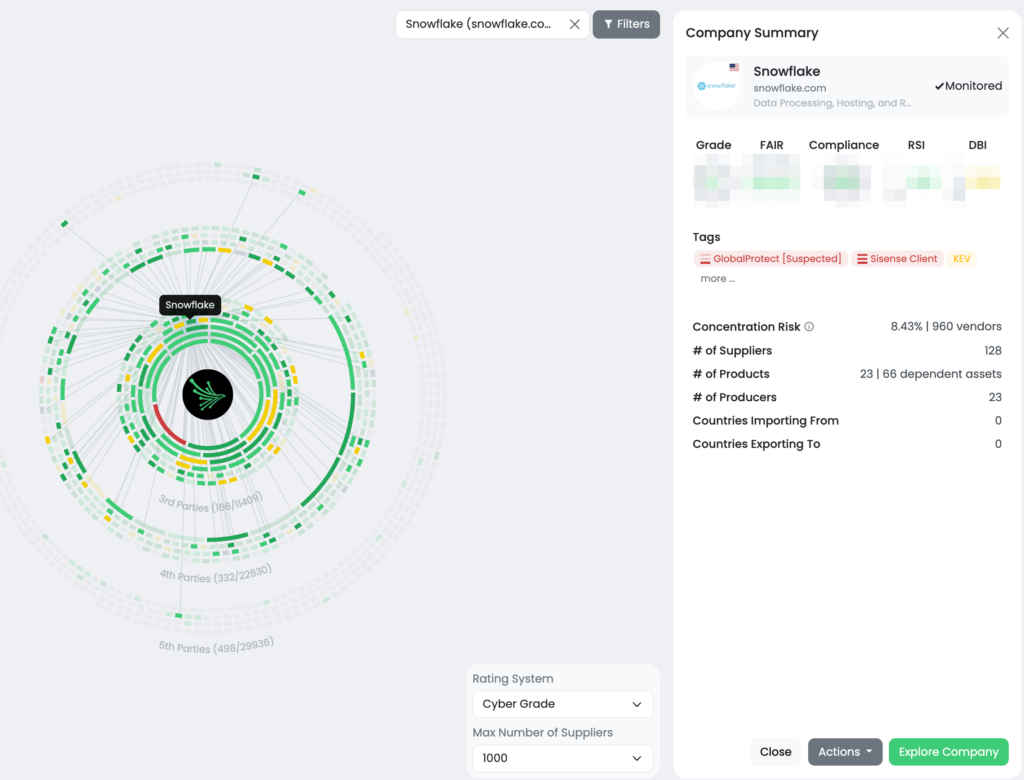
What happened in Snowflake?
In late May 2024, a significant security breach at Snowflake was discovered when attackers exploited vulnerabilities via a compromised employee account. This breach led to unauthorized access to sensitive customer data. The attackers utilized info-stealing malware to gain credentials, which allowed them to infiltrate Snowflake’s infrastructure. The breach quickly raised alarms, given the high-profile nature of many of Snowflake’s clients, including Ticketmaster and Santander Bank.
Snowflake’s immediate response involved alerting its customers and recommending the implementation of multi-factor authentication (MFA) and continuous monitoring of account activities. These measures aimed to prevent further unauthorized access and mitigate the damage. Despite these efforts, the attackers managed to extract a vast amount of sensitive data, leading to significant concerns about the potential ripple effects across the supply chain.
HudsonRock, a cybersecurity research firm, released a detailed report on the breach, which was later removed from public access due to its sensitive content. The report indicated that the attackers had accessed credentials from thousands of Snowflake accounts. This revelation underscored the severe risks associated with the breach and the broader implications for Snowflake’s extensive customer base.
The attackers claimed to have accessed data from multiple high-profile clients and demanded a ransom to prevent the sale of the stolen information. The incident highlighted the substantial technological concentration risk posed by Snowflake, as approximately 10,000 companies and organizations rely on its cloud computing and analytical services. The breach’s impact extended beyond direct customers, affecting vendors and partners, emphasizing robust TPRM practices.
Why should TPRM professionals care about the Snowflake incident?
Snowflake is a cornerstone for approximately 10,000 companies and organizations, providing essential cloud computing and analytical services. The breach has created a significant technological concentration risk, with the potential to compromise highly sensitive data processed and maintained by Snowflake or accessed via Snowflake credentials. The ripple effect of this incident can extend beyond direct customers to their vendors, partners, and even customers of those vendors.
TPRM professionals need to pay close attention to this incident, even if they do not directly interact with Snowflake. The interconnected nature of modern supply chains means that a breach in one critical provider can cascade through numerous organizations. The compromised credentials and stolen data from this breach could be used to exploit other systems, leading to widespread vulnerabilities and potential data breaches. Therefore, it is crucial for TPRM professionals to assess their vendor ecosystems and identify any indirect connections to Snowflake.
Furthermore, the breach underscores the importance of understanding technological concentration risks. Organizations heavily reliant on a single provider for critical services must recognize the potential impact of such incidents. TPRM professionals should evaluate their exposure to Snowflake and consider diversifying their technological dependencies to mitigate similar risks in the future. This incident serves as a stark reminder of the need for robust third-party risk management strategies to safeguard against the cascading effects of a major security breach.
What questions should TPRM professionals ask vendors about the incident mentioned in the FocusTagTM?
TPRM professionals should ask their vendors the following specific questions:
- Do you use Snowflake’s cloud storage services? If so, have you implemented multi-factor authentication (MFA) for all user accounts?
- Have you recently updated your security protocols to address credential-based attacks?
- Are you actively monitoring for indicators of compromise (IoCs) related to the Snowflake breach?
- What measures are you taking to protect data stored on cloud platforms like Snowflake?
- Have you communicated with Snowflake regarding the incident and followed their security recommendations?
- How are you ensuring the security of data accessed via Snowflake credentials?
Remediation Recommendations for Vendors to This Risk
To mitigate risks associated with the Snowflake incident, vendors should:
- Implement MFA on all Snowflake accounts.
- Monitor account activities for unusual behavior.
- Follow Snowflake’s guidance on detecting unauthorized access.
- Update cybersecurity strategies and ensure all staff are aware of the incident.
- Maintain communication with Snowflake for updates and further recommendations.
How TPRM Professionals Can Leverage Black Kite for This Incident
Black Kite determines which vendors are using Snowflake by analyzing subdomains, job postings, and other external sources. This comprehensive approach helps identify Snowflake clients accurately. In response to the recent breach, Black Kite published the Snowflake Client Focus Tag, enabling TPRM professionals to quickly pinpoint at-risk vendors and assess their exposure.
Customers can filter their monitored entities using the Snowflake Client tag, allowing them to focus on the vendors most likely to be affected by the breach. This targeted approach means that instead of sending questionnaires to vendors blindly, Black Kite customers can directly reach out to those at risk, streamlining their efforts and resources.

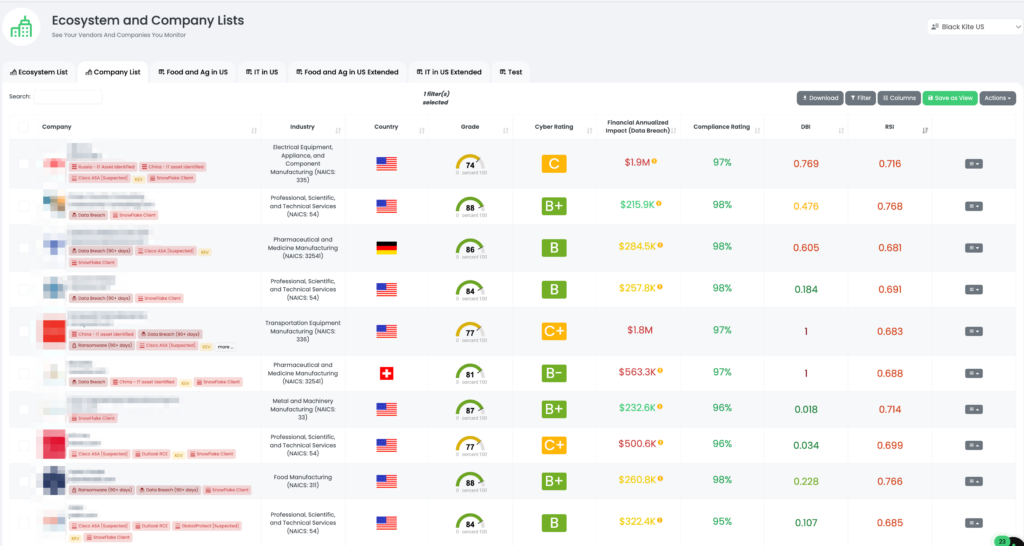
Black Kite’s new Supply Chain Tool offers an advanced way to uncover risks beyond direct third parties. Customers can search for Snowflake within their supply chain and visualize the concentration risk. The tool enables TPRM professionals to filter their supply chain (including 3rd, 4th, and 5th parties) based on Snowflake usage, and further narrow down the search by adding additional filters such as cyber grade, risk score, and compliance ratings.
Operationalizing this tool involves several steps. First, customers can enter specific parameters related to Snowflake, such as subdomains or job postings, to identify vendors that utilize Snowflake’s services. Once identified, these vendors can be assessed for their exposure to the recent breach. This targeted approach allows TPRM professionals to focus their efforts on the most at-risk entities, enhancing the efficiency of their risk management processes.

Additionally, the Supply Chain Tool’s filtering capabilities provide a comprehensive view of an organization’s extended supply chain. By visualizing the interconnections and potential concentration risks, TPRM professionals can better understand the overall impact of the Snowflake breach. This holistic approach enables proactive risk mitigation, ensuring that vulnerabilities are addressed promptly and effectively.
Black Kite customers can further leverage this tool by integrating it into their regular risk assessment routines. Regularly updating the filters and parameters based on the latest threat intelligence allows for continuous monitoring and early detection of potential risks. This proactive stance not only helps in managing current vulnerabilities but also prepares organizations for future threats, maintaining the integrity and security of their supply chain. For more details, visit Black Kite Supply Chain Module.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
About Focus Friday
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FocusTagsTM in the Last 30 Days:
- Snowflake Client
- Checkpoint SNX: CVE-2024-24919, An Information Disclosure Vulnerability in Check Point’s CloudGuard Network, Quantum Maestro, Quantum Scalable Chassis, Quantum Security Gateways, Quantum Spark Appliances
- DNSBomb: CVE-2023-28450, DNSBomb Attack in Dnsmasq, CoreDNS, Knot DNS, Simple DNS Plus, Technitium DNS, MaraDNS, CoreDNS
- Veeam VBEM: CVE-2024-29849, Authentication Bypass Vulnerability in Veeam Backup Enterprise Manager.
- Multi Connect: CVE-2023-43208, Deserialization of Untrusted Data Vulnerability, RCE Vulnerability in NextGen Healthcare Mirth Connect.
- Cacti: CVE-2024-25641, Remote Code Execution Vulnerability in Cacti
- Veeam SPC: CVE-2024-29212, Remote Code Execution Vulnerability in Veeam Service Provider Console
- TinyProxy: CVE-2023-49606, Use-After-Free Vulnerability, RCE Vulnerability in Tinyproxy
- ArubaOS: CVE-2024-26304, Buffer Overflow Vulnerability, Remote Code Execution Vulnerability in ArubaOS
- CrushFTP VFS: CVE-2024-4040, a Server Side Template Injection Vulnerability in CrushFTP
- Sisense Client
- FortiClient EMS: CVE-2023-48788, SQL Injection Vulnerability in Fortinet’s FortiClient Endpoint Management Server
- FortiOS SSL VPN: CVE-2024-21762, A Out-of-Bounds Write Vulnerability in FortiOS [Tag updated]
- Outlook RCE: CVE-2023-36439, RCE Vulnerability in Microsoft Exchange Server
- Change Healthcare Client
- JetBrains TeamCity: CVE-2023-42793, Authentication Bypass in JetBrains TeamCity CI/CD Servers; CVE-2024-27198, Authentication Bypass Vulnerability [Tag Updated]
- ScreenConnect:CVE-2024-1709, Authentication Bypass Vulnerability
- Cisco ASA [Suspected]CVE-2020-3259, Information Disclosure Vulnerability
- Exchange Server:CVE-2024-21410,Privilege Elevation Vulnerability
- QNAP QTS:CVE-2023-47218, CVE-2023-50358, OS Command Injection Vulnerability
- Symantec MG [Suspected]:CVE-2024-23615, CVE-2024-23614, Buffer Overflow Vulnerability (Remote Code Execution)
- FortiOS SSL VPN [Suspected]:CVE-2024-22024, An Out-of-Bounds Write Vulnerability
- RoundCube [Suspected] :CVE-2023-43770, Stored-XSS Vulnerability [Updated]
- Citrix ADC/Gateway:CVE-2023-6549 [Updated], Buffer Overflow Vulnerability
- Ivanti EPMM:CVE-2023-35082 [Updated], Authentication Bypass Vulnerability
References:
https://thehackernews.com/2024/06/snowflake-warns-targeted-credential.html
https://finance.yahoo.com/news/snowflake-hit-data-breach-whats-141942232.html
https://techcrunch.com/2024/06/05/snowflake-customer-passwords-found-online-infostealing-malware

