FOCUS FRIDAY: Enhancing TPRM Through Insight on the Critical XZ Utils Vulnerability
Written by: Ferhat DikbiyikAdditional Contributions: Ferdi Gül
Today, we spotlight a significant vulnerability within XZ Utils, a commonly used data compression tool, and explore the ramifications this issue holds for TPRM professionals. Let’s navigate through the complexities of this vulnerability and how the innovative capabilities of Black Kite’s FocusTags™ help.
What is CVE-2024-3094?
CVE-2024-3094 represents a stark demonstration of the critical vulnerabilities that lurk within widely used tools like XZ Utils, versions 5.6.0 and 5.6.1, and underscores the paramount importance of proactive threat detection. Discovered as a severe backdoor that facilitates remote code execution (RCE), this vulnerability not only highlights the severity, with a CVSS score of 10, but also brings to the fore the sophistication of attack methods employed, including file carving and custom decryption.
The discovery of the vulnerability brings into question whether the foresight provided by thorough third-party risk management (TPRM) practices could have anticipated the threat. The backdoor, concealed within the liblzma library, is activated upon installation, granting attackers unfettered access to execute code remotely. This scenario exemplifies the challenges faced in detecting and mitigating such vulnerabilities, which are designed to be stealthy and adaptable for future malicious endeavors.
Despite not being cataloged in CISA’s Known Exploited Vulnerabilities (KEV) at the time of its discovery, the swift issuance of an alert by CISA on March 29, 2024, points to the recognition of its potential for widespread compromise. The vulnerability’s implications are vast, with the possibility of attackers gaining control over affected systems, altering or stealing data, introducing malware, or adding the systems to a botnet.
The TPRM perspective detailed in our previous analysis, “Could TPRM Have Foreseen the XZ-Utils CVE-2024-3094 Crisis?,” underscores the necessity for a vigilant, informed approach to cybersecurity. Understanding the mechanisms and potential indicators of such vulnerabilities is crucial for TPRM professionals to effectively assess and mitigate the risks posed to their organizations and vendors. The case of CVE-2024-3094 serves as a compelling argument for the integration of predictive risk management strategies, which could potentially alert organizations to vulnerabilities before they are exploited by malicious actors.
What Should TPRM Professionals Do Next?
Given the vulnerability’s impact, TPRM professionals need to scrutinize their vendors, especially those utilizing affected Linux distributions like Fedora, Alpine, Debian, and OpenSUSE-Tumbleweed, for potential risk exposures. The risk extends to system integrity, data confidentiality, and the broader network security, making it a significant concern for vendor risk management.
For those looking to delve deeper into the technicalities and implications of CVE-2024-3094, our previous blog post serves as a comprehensive resource with an in-depth analysis and insights on the vulnerability. This post provides a foundation for understanding the significance of our ongoing efforts to address such critical vulnerabilities through Black Kite’s FocusTags™.
Key Questions for Vendors
- Have you identified any installations of XZ Utils versions 5.6.0 or 5.6.1 within your systems?
- What measures have you taken to mitigate the vulnerabilities found in CVE-2024-3094?
- Can you provide documentation of the downgrade process to the last known secure version of XZ Utils?
- Have you monitored and identified any suspicious activities related to this vulnerability in your network traffic?
Remediation Recommendations for Vendors
- Downgrade immediately to XZ Utils version 5.4.6 and confirm the patch via package manager tools specific to your operating system.
- Conduct a comprehensive system inventory to pinpoint affected XZ Utils installations, utilizing detection commands for thorough assessment.
- If unable to downgrade promptly, activate the backdoor’s “kill switch” as a temporary measure.
- Ensure the integrity of packages by sourcing from trusted origins and validating their authenticity.
Black Kite’s Response to CVE-2024-3094
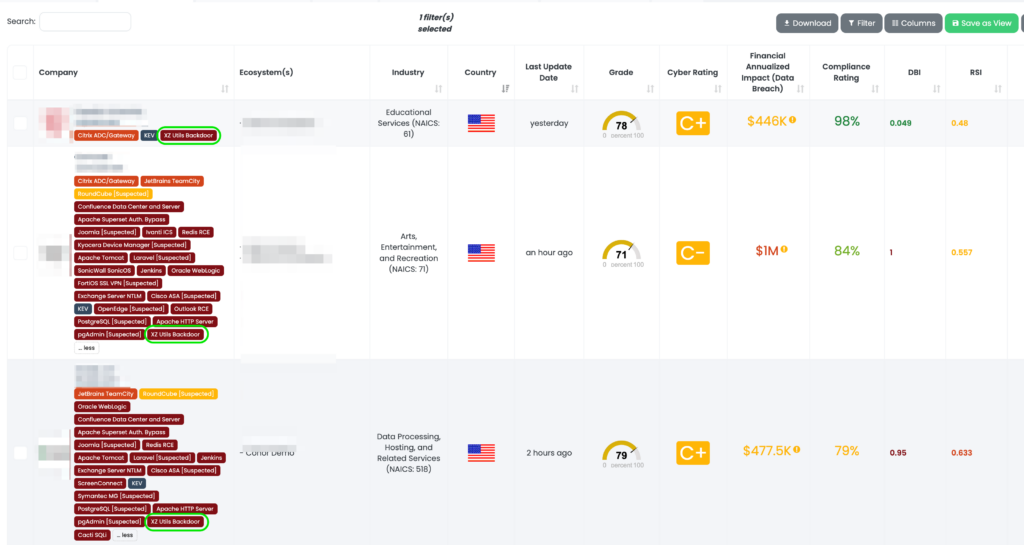
Black Kite published the XZ Utils tag on April 2, 2024, providing critical intelligence on potentially vulnerable assets and vendors. TPRM professionals can operationalize this data by pinpointing and prioritizing risk assessments on vendors utilizing affected XZ Utils versions, streamlining the remediation process, and enhancing cybersecurity posture effectively.
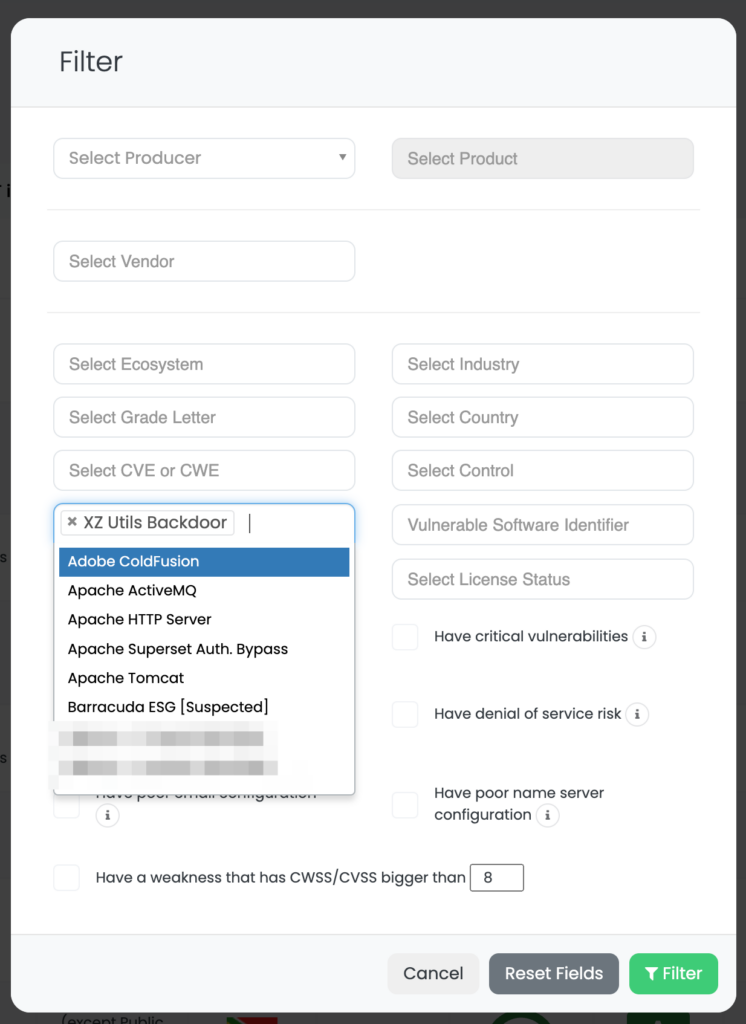
Amidst the backdrop of escalating cyber threats, Black Kite distinguishes itself as the first and, as of the publication date, the only vendor risk intelligence provider to offer a sophisticated filtering capability for CVE-2024-3094. This feature stands as a testament to Black Kite’s commitment to advancing TPRM efficacy, enabling clients to precisely identify and focus on vendors impacted by this critical vulnerability.
By leveraging Black Kite’s intelligence and adhering to recommended practices, organizations can significantly reduce their vulnerability to critical threats like CVE-2024-3094.

Enhancing TPRM Efficacy with Black Kite’s FocusTags™
In an era where cyber threats loom larger and more intricate than ever, the agility to preempt and neutralize risks is paramount. Black Kite’s FocusTags™ emerge as a pivotal ally in this quest, revolutionizing the TPRM landscape with unparalleled insights and foresight. Through the lens of the latest critical vulnerability in XZ Utils, let’s unpack the myriad ways these tags catalyze robust risk management efforts:
- Proactive Vulnerability Detection: Black Kite’s FocusTags™ cut through the noise, enabling TPRM teams to promptly pinpoint which vendors are vulnerable to newly discovered threats like CVE-2024-3094. This immediacy is crucial for initiating timely mitigation strategies.
- Strategic Risk Calibration: These tags go beyond mere identification; they facilitate a nuanced understanding of the severity and potential impact of vulnerabilities. By quantifying risk, they guide TPRM professionals in prioritizing their response efforts effectively, ensuring resources are directed where they are most needed.
- Facilitated Vendor Dialogue: Armed with data from FocusTags™, TPRM teams can engage vendors in meaningful conversations about specific vulnerabilities. This targeted approach fosters a collaborative environment for addressing and remedying security gaps.
- Comprehensive Risk Perspective: In today’s complex cyber landscape, a macro view is essential. FocusTags™ affords a holistic outlook, encapsulating a wide array of vulnerabilities and threats. This comprehensive visibility empowers TPRM professionals to fortify defenses and champion a more resilient cybersecurity posture.
The critical XZ Utils vulnerability unveiled in this week’s blog exemplifies the indispensable role Black Kite’s FocusTags™ play in elevating TPRM practices. By transforming intricate cyber threat intelligence into actionable insights, Black Kite empowers organizations to navigate the cybersecurity terrain with confidence and precision. As we continue to witness the evolution of cyber threats, the strategic integration of such innovative tools into TPRM frameworks is not just beneficial—it’s essential for safeguarding against the unforeseeable challenges of tomorrow.
Learn more about this breach in our blog, “Could TPRM Have Foreseen the XZ-Utils CVE-2024-3094 Crisis?”
About Focus Friday
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
Want to take a closer look at Focus Tags™?
Take our platform for a test drive and request a demo today.

