FOCUS FRIDAY: Addressing the Sisense Client and CrushFTP Vulnerabilities: A TPRM Approach
Written by: Ferdi Gül & Ferhat Dikbiyik
Welcome to this week’s Focus Friday, where we delve into critical vulnerabilities that are reshaping Third-Party Risk Management (TPRM) practices. Today, we spotlight two high-profile issues: the CrushFTP VFS and Sisense Data Breach incidents. Our discussion will not only cover the specifics of these incidents but also illustrate how Black Kite’s FocusTags™ can drive proactive risk management strategies.
Expected Ripple Effect of Sisense Data Breach
What happened in Sisense?
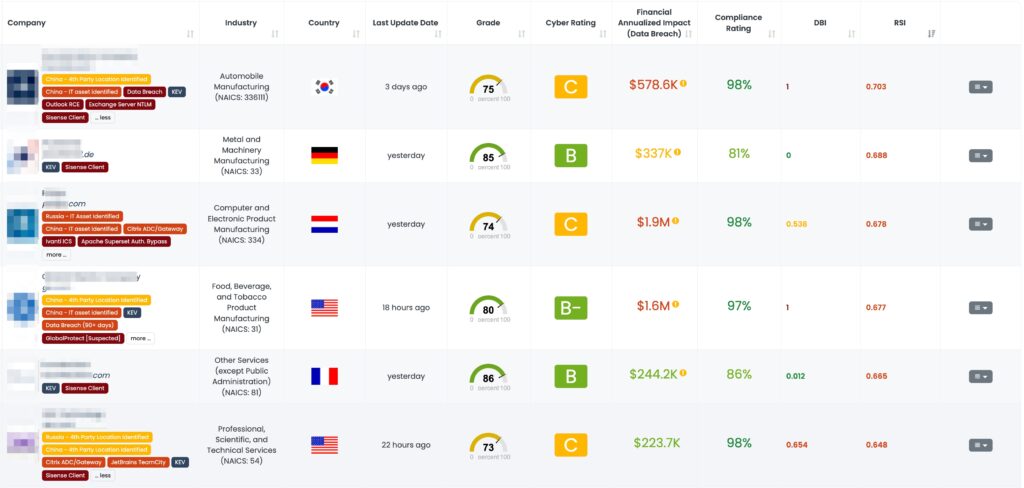
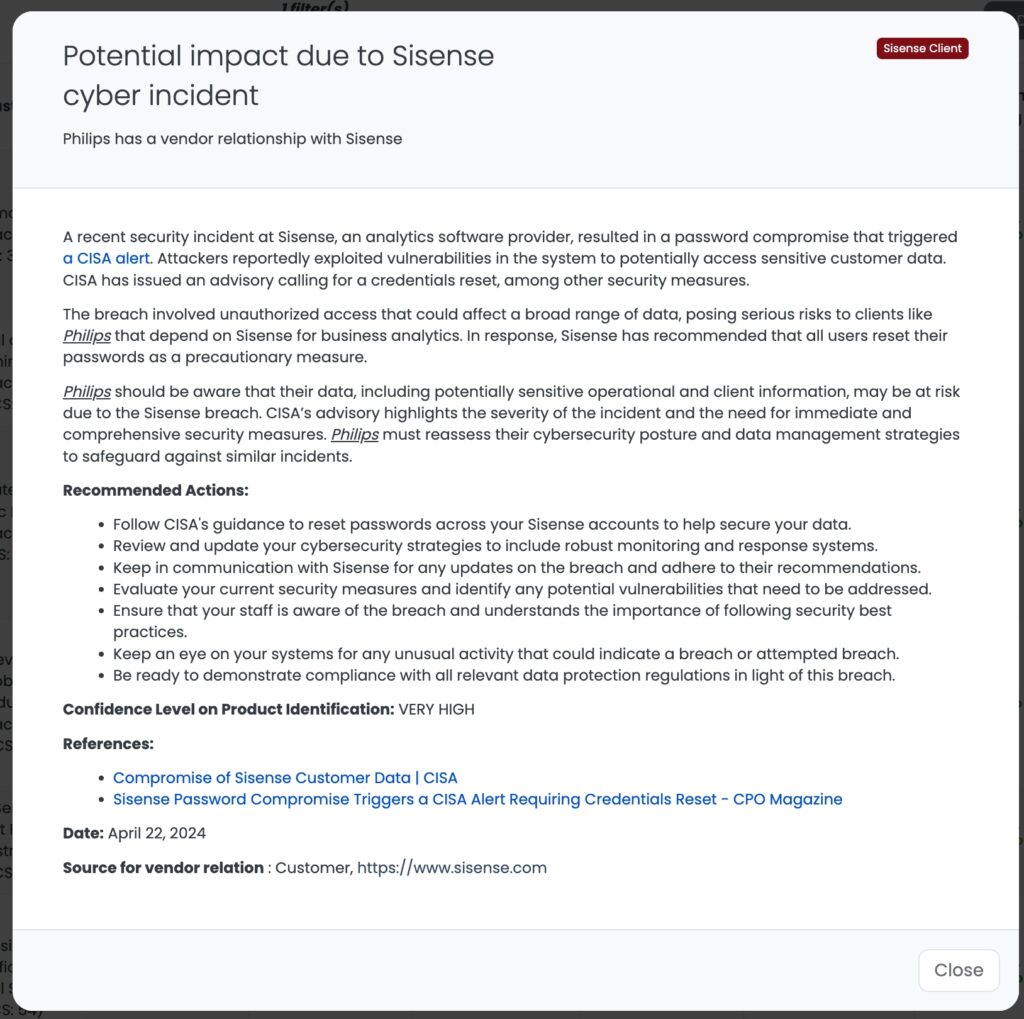
A recent security breach at Sisense involved unauthorized access that triggered a CISA alert in April 2024. This breach potentially compromised sensitive customer data through vulnerabilities that were exploited by attackers. Given Sisense’s role in embedding analytics into various business applications, the impact goes beyond data exposure to possibly altering analytical processes and outcomes.
The compromise at Sisense was severe, affecting numerous credential types across a broad client base, including major sectors like healthcare and telecommunications. Notably, Sisense’s systems, which utilize a variety of credentials such as SSO secrets and customer database passwords, were infiltrated, leading to potential unauthorized access to sensitive data.
Security experts are concerned about the extensive nature of the breach, with millions of credentials potentially at risk. The use of Sisense by large corporations means the breach could lead to further infiltrations into the networks of its customers, heightening the risk of supply chain attacks. Companies linked to Sisense, like Hive, which serves entities such as Starbucks and Uber, are advised to be especially vigilant.
Why should TPRM professionals focus on this incident?
This breach is particularly critical for TPRM professionals due to Sisense’s widespread integration into over 2,000 companies’ core business functions. The potential alteration or manipulation of analytical data could lead to misinformed business decisions, highlighting the need for robust third-party risk management practices even among vendors not directly using Sisense services.
Imagine a large retail corporation that integrates Sisense into its customer relationship management system to analyze shopping trends and personalize offers. If Sisense’s security is compromised, the breach could lead to unauthorized access to customer data, impacting consumer trust and potentially leading to financial and reputational damage. This incident could then ripple out to affect partners and vendors within the retail supply chain who rely on the integrity of this data for their operations and strategic planning.
What questions should TPRM professionals ask vendors about the Sisense incident?
TPRM professionals should pose targeted inquiries to understand the full scope of the Sisense breach on their vendors, such as:
- What is the extent of the impact of the Sisense breach on your embedded analytics systems?
- Have there been any unauthorized changes to analytical outputs?
- What immediate measures have you implemented post-incident?
- How are you verifying the integrity of analytics post-breach?
Remediation recommendations for vendors affected by the Sisense breach
Vendors should:
- Follow CISA’s guidance to reset passwords and secure credentials potentially exposed.
- Conduct a thorough security assessment to verify the integrity of embedded analytics tools and rectify potential vulnerabilities.
- Strengthen monitoring systems to detect and respond to anomalies in data analytics processes promptly.
Leveraging Black Kite in Response to the Sisense Incident
Black Kite’s Focus Tag on the Sisense incident was published on April 22, 2024. This tag equips TPRM professionals with critical insights, such as detailed subdomain analysis, enabling them to identify and monitor vendors potentially impacted by the Sisense breach. By leveraging this specific intelligence, TPRM professionals can efficiently prioritize their risk management activities, focusing on vendors most likely to be affected. This operational approach allows for targeted mitigation efforts and enhances the overall security posture by addressing the most critical vulnerabilities first.
CVE-2024-4040 in CrushFTP: A TPRM Perspective
What is the CVE-2024-4040 vulnerability?
The vulnerability was listed in CISA’s Known Exploited Vulnerabilities catalog on April 24, 2025. CVE-2024-4040 is a severe vulnerability in CrushFTP that allows remote attackers to take complete control of a vulnerable server. It affects all versions of CrushFTP before 10.7.1 and 11.1.0. CVE-2024-4040 is classified as a server-side template injection (SSTI) vulnerability. This means an attacker can inject malicious code into templates that the server then processes. In the case of CVE-2024-4040, a successful exploit could allow attackers to read files from the server’s filesystem, bypass authentication to gain administrative access, and even execute code on the server. Public exploit code is available, making it easier for attackers to exploit this vulnerability. A successful exploit of CVE-2024-4040 can have far-reaching consequences for organizations such as data breach, privilege escalation, and remote code execution.
Technical Details
CrushFTP’s default configuration poses a significant security risk due to its use of reversible DES encryption for passwords. This vulnerability could potentially allow attackers to retrieve user passwords in plaintext and also establish remote code execution (RCE). RCEs are highly used by ransomware groups and their affiliates to infiltrate the systems and deploy ransomware.
When examining the published technical analyses, attackers are observed to follow the steps below when exploiting the CVE-2024-4040 vulnerability:
- Basic Requirements:
- The attacker must initially have access to the targeted version of CrushFTP.
- A tool capable of making HTTP requests to the server must be used to gain access. For example, curl or a similar tool.
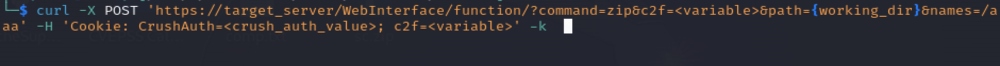
- Sending Requests to the Server:
- Curl or a similar tool is used to send an HTTP request to the server. Direct your requests to the target server. For example:
- Arbitrary File Read:
- To perform file reading on the target server, send the file path to the server using the <INCLUDE> tag. This allows the server to read a specific file and return its contents as a response. For example:

- Authentication Bypass:
- Session tokens in CrushFTP are stored in a file. By reading these tokens, authentication can be bypassed. First, read the session file on the server using the <INCLUDE> tag. Then, perform malicious actions by bypassing authentication with these session tokens.
What is the scope of CVE-2024-4040?
CrushFTP servers that use the VFS functionality are susceptible, though the specific versions impacted are still being identified by security researchers. According to the vendor advisory, the following CrushFTP versions are vulnerable as of April 23, 2024:
- All legacy CrushFTP 9 installations
- CrushFTP 10 versions prior to v10.7.1
- CrushFTP 11 versions prior to v11.1.0
Recent research suggests that more than 11,000 CrushFTP servers could be potentially accessed externally through CrushFTP VFS. It’s important to consider that this number might not include endpoints that solely rely on other access methods offered by CrushFTP VFS.
Timeline for CVE-2024-4040:
April 19, 2024 (Friday)
- CrushFTP sent out notices about CVE-2024-4040 to customers.
April 22, 2024 (Monday)
- The vulnerability is publicly disclosed (published) on platforms like NVD (National Vulnerability Database) and assigned the CVE-ID CVE-2024-4040.
April 23, 2024 (Tuesday)
- The vulnerability was analyzed and the FocusTagTM processing was completed by Black Kite’s Research Team.
April 24, 2024 (Wednesday)
- CISA adds CVE-2024-4040 to their Known Exploited Vulnerabilities Catalog. They advise users to apply mitigations provided by CrushFTP or discontinue using the product if no mitigation exists.
Technical Analysis was published by Rapid7.
TPRM Implications
For Third-Party Risk Management (TPRM) professionals, CVE-2024-4040 underscores the importance of diligent vendor assessment and risk oversight. This vulnerability highlights potential downstream impacts on partners and clients, stressing the need for comprehensive security assessments to safeguard the supply chain.
To mitigate CVE-2024-4040 risks, TPRM professionals should ensure:
- Immediate communication with CrushFTP vendors to verify patch applications.
- Urgent patching of affected systems using the latest CrushFTP software updates.
- Regular monitoring for any signs of exploitation or further vulnerabilities.
- Enhanced security protocols, including stricter access controls and network segmentation.
Engaging with vendors
When assessing vendor security in light of CVE-2024-4040, consider asking:
- Have you patched the affected CrushFTP versions?
- How are you monitoring for potential exploitation?
- What additional security measures have you implemented post-update?
- Can you provide recent security audit results to assess your vulnerability response?
These targeted inquiries help TPRM professionals evaluate the security posture of vendors and make informed decisions to manage associated risks effectively. This approach not only addresses immediate concerns but also strengthens overall cybersecurity resilience against future threats.
How can vendors detect and remediate CVE-2024-3094?
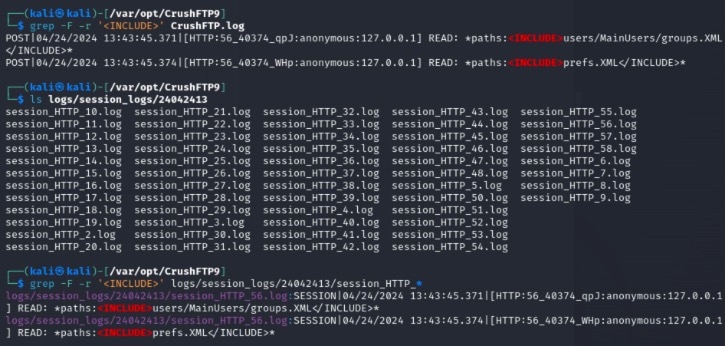
Vendors can address CVE-2024-3094 by applying patches released by CrushFTP (versions 10.7.1 and 11.1.0), scanning systems with tools like the Airbus CERT script on GitHub, and reviewing logs (CrushFTP.log* and session_HTTP*.log) for suspicious IP addresses. Additionally, stricter access controls and network segmentation can minimize vulnerable attack surfaces, and SIEM solutions can be implemented for centralized log monitoring to detect unusual activity.
Scanners are available to identify vulnerable systems. Airbus CERT has made a public script available on GitHub. This script can be used to scan for the vulnerability.
In threat intelligence analysis within your organization, it’s beneficial to review the log files specified (‘CrushFTP.log*’ and Session Logs defined ‘session_HTTP_*.log’) in the directory where the application is installed. It’s strongly advised to check for any suspicious IP addresses.
You can use the following simple command manually or automate it and can test whether there is a suspicious IP within the ‘<INCLUDE>’ parameter and customize the query accordingly based on the test results:
$ grep -F -r ‘<INCLUDE>’ /path/to/CrushFTP/logs/
Remediation Recommendations:
- Implement stricter access controls to reduce potential attack surfaces.
- Review user permissions and implement network segmentation.
- Monitor server logs for unusual activities to detect potential exploits.
- Utilize Security Information and Event Management (SIEM) for centralized log analysis.
- Configure CrushFTP behind a DMZ (demilitarized zone) to enhance defense.
Mitigating vendor risk of CVE-2024-4040 with Black Kite’s FocusTags™
On April 24, 2024, Black Kite released the CVE-2024-4040 FocusTag, presenting a critical opportunity for organizations to bolster their cybersecurity resilience. It details how this vulnerability exposes critical weaknesses in certain network infrastructure components.

assess and prioritize risks diligently, fortifying their defenses effectively.
Enhancing TPRM Capabilities with Black Kite’s FocusTags™
In today’s dynamic cybersecurity landscape, effective Third-Party Risk Management (TPRM) is crucial. Black Kite’s FocusTags™ for Sisense Client and CrushFTP VFS specifically address the unique challenges posed by these incidents. Here’s how these tags are critical in managing third-party risks:
- Immediate Threat Identification: Rapidly pinpoints vendors affected by the Sisense data breach or the CrushFTP vulnerability, enabling swift mitigation actions.
- Risk Prioritization: Assists in categorizing vendor risks, focusing on those with the highest exposure due to these specific incidents.
- Strategic Vendor Interactions: Facilitates detailed discussions with vendors about their exposure to the Sisense breach or CrushFTP vulnerability, ensuring they understand the risks and mitigation strategies.
- Comprehensive Security Enhancement: Provides insights into the cascading impacts of the Sisense breach and the critical vulnerabilities of CrushFTP, helping to bolster overall security posture and resilience.
With these FocusTags™, Black Kite translates intricate threat data into actionable intelligence, empowering TPRM professionals to proactively manage and mitigate risks associated with specific high-profile incidents.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
About Focus Friday
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FocusTagsTM in the Last 30 Days:
Focus Tags in the Last 30 days
- CrushFTP VFS: CVE-2024-4040, a Server Side Template Injection Vulnerability in CrushFTP
- Sisense Client
- FortiClient EMS: CVE-2023-48788, SQL Injection Vulnerability in Fortinet’s FortiClient Endpoint Management Server
- FortiOS SSL VPN: CVE-2024-21762, A Out-of-Bounds Write Vulnerability in FortiOS [Tag updated]
- Outlook RCE: CVE-2023-36439, RCE Vulnerability in Microsoft Exchange Server
- Change Healthcare Client
- JetBrains TeamCity: CVE-2023-42793, Authentication Bypass in JetBrains TeamCity CI/CD Servers; CVE-2024-27198, Authentication Bypass Vulnerability [Tag Updated]
- ScreenConnect:CVE-2024-1709, Authentication Bypass Vulnerability
- Cisco ASA [Suspected]CVE-2020-3259, Information Disclosure Vulnerability
- Exchange Server:CVE-2024-21410,Privilege Elevation Vulnerability
- QNAP QTS:CVE-2023-47218, CVE-2023-50358, OS Command Injection Vulnerability
- Symantec MG [Suspected]:CVE-2024-23615, CVE-2024-23614, Buffer Overflow Vulnerability (Remote Code Execution)
- FortiOS SSL VPN [Suspected]:CVE-2024-22024, An Out-of-Bounds Write Vulnerability
- RoundCube [Suspected] :CVE-2023-43770, Stored-XSS Vulnerability [Updated]
- Citrix ADC/Gateway:CVE-2023-6549 [Updated], Buffer Overflow Vulnerability
- Ivanti EPMM:CVE-2023-35082 [Updated], Authentication Bypass Vulnerability
- GoAnywhere [Suspected]:CVE-2024-0204, Authentication Bypass Vulnerability
- Redis RCE: CVE-2023-41056, Remote Code Execution Vulnerability
- Ivanti ICS: CVE-2024-21887, Command Injection Vulnerability, CVE-2023-46805, Authentication Bypass Vulnerability
- Cacti SQLi: CVE-2023-51448, Blind SQL Injection (SQLi) Vulnerability
References:
https://www.cisa.gov/news-events/alerts/2024/04/11/compromise-sisense-customer-data
https://www.reddit.com/r/cybersecurity/comments/1c850i2/all_versions_of_crush_ftp_are_vulnerable
https://nvd.nist.gov/vuln/detail/CVE-2024-4040
https://attackerkb.com/topics/20oYjlmfXa/cve-2024-4040/rapid7-analysis#