Focus Friday: Addressing the Critical CVE-2023-7102 Vulnerability in Barracuda ESG
Written by: Kat Desy
Written by: Ferhat Dikbiyik
Additional Contributions: Ferdi Gül and Yavuz Han
Edited by: Katherine Desy
Welcome to this week’s Focus Friday, where we spotlight a critical vulnerability in Barracuda’s Email Security Gateway (ESG) Appliance, identified as CVE-2023-7102. This vulnerability, involving Arbitrary Code Execution and Parameter Injection, has raised significant security concerns, particularly following reports of its exploitation by threat actors. With the widespread use of Barracuda ESG in various organizations, understanding and addressing this vulnerability is crucial. In this blog, we’ll explore the nature of CVE-2023-7102, its potential impacts, and how Black Kite’s Focus Tags™ assist TPRM professionals in managing this emerging threat.
Analyzing the CVE-2023-7102 Vulnerability in Barracuda’s Email Security Gateway
What Constitutes the Barracuda ESG Vulnerability CVE-2023-7102?
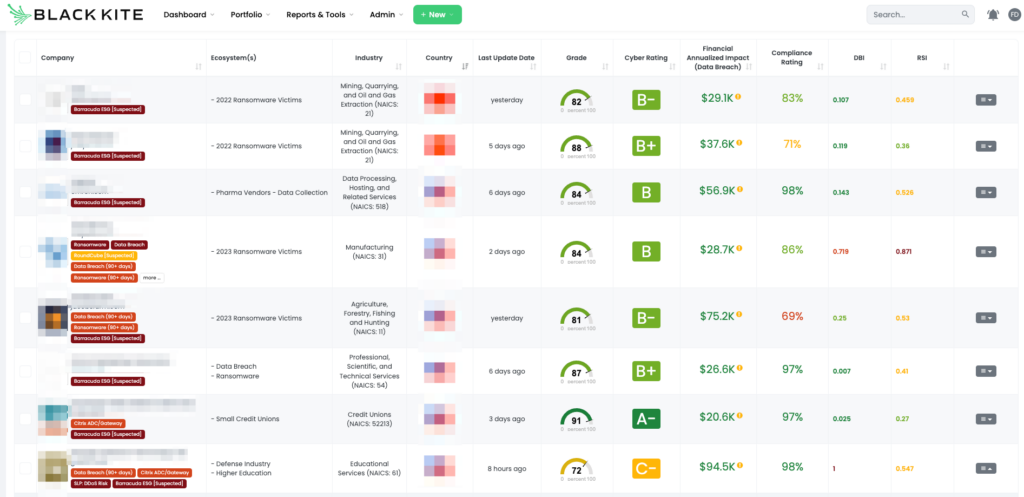
CVE-2023-7102, a critical vulnerability in Barracuda’s Email Security Gateway (ESG) Appliance, poses a significant security threat. This vulnerability allows arbitrary code execution and parameter injection due to a flaw in the Spreadsheet::ParseExcel library used for parsing Excel files. The library’s lack of validation for user-supplied input in Excel number formats enables attackers to manipulate the number format property in an Excel file, leading to potential code execution. Barracuda identified that this vulnerability was exploited by the China-based actor UNC4841, using it to deploy SEASPY and SALTWATER malware on affected ESG devices. The vulnerability impacts all Barracuda ESG Appliance devices with versions from 5.1.3.001 to 9.2.1.001, making it a concern for a broad range of users and applications. Barracuda’s response included a patch released on December 22, 2023, to address compromised ESG appliances and the associated malware indicators.
Why Is CVE-2023-7102 in Barracuda ESG a Concern for TPRM Professionals?
The CVE-2023-7102 vulnerability in Barracuda ESG is particularly concerning for Third-Party Risk Management (TPRM) professionals due to its potential for arbitrary code execution and parameter injection in a widely-used email security appliance. The exploitation of this vulnerability can lead to unauthorized access, data breaches, and malware deployment within an organization’s network. Given the widespread application of Barracuda ESG across various industries, TPRM professionals need to ensure their vendors using this appliance have implemented the necessary security measures and patches to mitigate the risk.
Critical Questions TPRM Professionals Should Ask Regarding CVE-2023-7102 in Barracuda ESG
To address the CVE-2023-7102 vulnerability in Barracuda ESG, TPRM professionals should ask vendors specific, technical questions:
- “Have you applied the security update released by Barracuda on December 21, 2023, to address CVE-2023-7102 in your ESG appliances?”
- “What measures have you implemented to detect and mitigate any potential exploitation of this vulnerability?”
- “Can you detail your current protocol for inspecting and validating Excel files processed by Barracuda ESG appliances?”
- “How are you ensuring continuous monitoring of network traffic and activity logs for signs of unauthorized access or malware deployment related to this vulnerability?”
Recommended Remediation Actions for Vendors Impacted by CVE-2023-7102
Vendors impacted by the CVE-2023-7102 vulnerability in Barracuda ESG should take immediate remediation steps:
- Ensure that Barracuda ESG appliances are updated with the security patch released on December 21, 2023.
- Implement rigorous monitoring of network traffic and activity logs for signs of exploitation or unusual activities.
- Establish protocols to carefully inspect and validate Excel files being processed by the ESG appliances.
- Regularly review and update security configurations to strengthen defenses against potential attacks.
How Does Black Kite Facilitate TPRM in Addressing the CVE-2023-7102 Vulnerability?
Leveraging Black Kite in response to the CVE-2023-7102 vulnerability in Barracuda ESG offers a strategic advantage for TPRM professionals. Black Kite’s focused tagging and risk assessment tools enable quick identification of vendors using affected versions of Barracuda ESG. This facilitates targeted communication and ensures that vendors are aware of the vulnerability and the necessary remediation steps.
Additionally, Black Kite provides detailed insights into the specific IT assets at risk, allowing for more precise and effective risk management strategies. This approach not only streamlines the risk mitigation process but also enhances overall cybersecurity preparedness against such critical vulnerabilities.
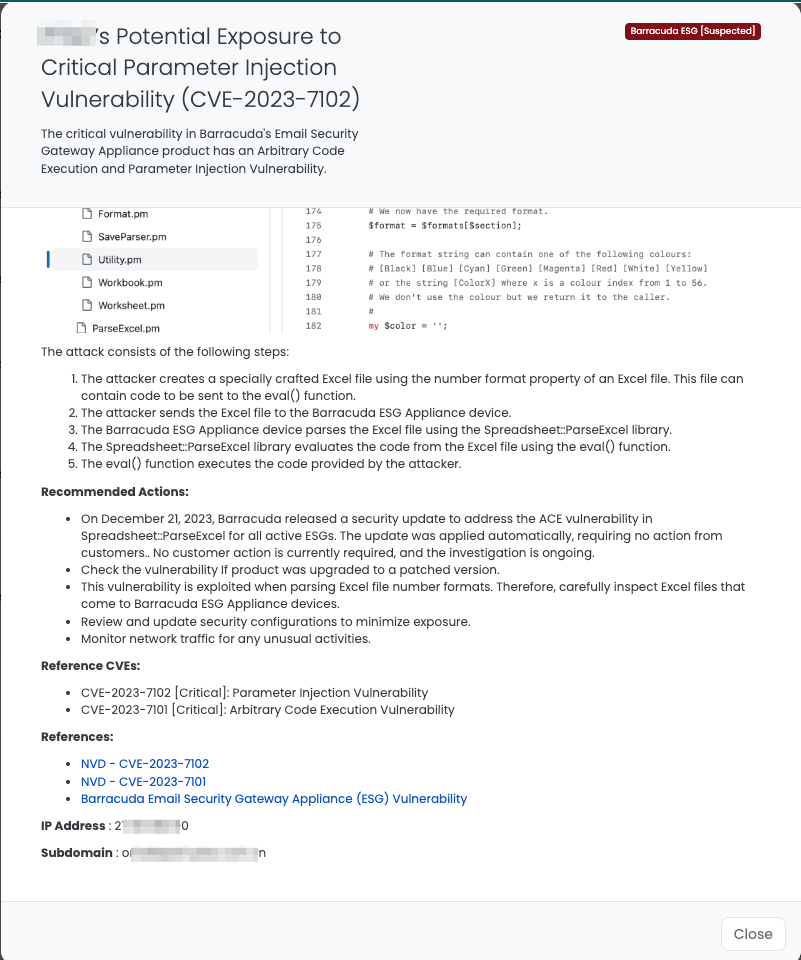
Enhancing TPRM with Black Kite’s Targeted Focus Tags™
Black Kite’s Focus Tags™ are pivotal in advancing Third-Party Risk Management (TPRM), especially given the recent critical vulnerabilities like CVE-2023-7102 in Barracuda ESG. These tags:
- Enable Immediate Risk Identification: Quickly pinpoint vendors affected by urgent vulnerabilities, ensuring rapid risk assessment and response.
- Facilitate Risk Prioritization: Aid in categorizing risks, focusing on the severity of vulnerabilities and their impact on vendors.
- Support Informed Vendor Dialogue: Encourage detailed, relevant discussions with vendors, focusing on their specific security setups and responses to current vulnerabilities.
- Promote Comprehensive Security Strategies: Offer insights into the broader threat landscape, helping to form more dynamic and effective cybersecurity defenses.
Through Black Kite’s Focus Tags™, TPRM professionals gain valuable, actionable intelligence, enhancing their ability to manage emerging cyber threats effectively.
Want to take a closer look at Focus Tags™?
Take our platform for a test drive and request a demo today.
Focus Tags™ in the Last 30 days
- Barracuda ESG: CVE-2023-7102, Parameter Injection Vulnerability
- Mlflow: CVE-2023-6753, A Path Traversal Vulnerability in MLflow.
- Elemtor Plugin: CVE-2023-48777, File Upload / Remote Code Execution Vulnerabilities in The Elementor Website Builder versions identified before <=3.18.1
- APT Risk: FortiOS/Zoho: Vulnerabilities used by nation-state actors as part of Volt Typhoon campaign
- Atlassian Confluence Data Center and Server: CVE-2023-22522, Template Injection Vulnerability
- Adobe ColdFusion: CVE-2023-26360, Improper Access Control Vulnerability
- Qlik Sense: CVE-2023-48365, Unauthenticated RCE Vulnerability in Qlik Sense Enterprise for Windows
- Apache Superset: CVE-2023-40610, Privilege Escalation Vulnerability in Apache Superset <2.1.2 versions.
- OpenVPN Access: CVE-2023-46850, OpenVPN Access Server Flaw Exposes Sensitive Data and RCE Possible
- ownCloud: CVE-2023-49103, Information Disclosure Vulnerability in ownCloud’s Graphapi Component
- Atlassian Bamboo Data Center: CVE-2023-22516, RCE Vulnerability in Bamboo Data Center and Server Tagging
- Sophos Web Appliance: CVE-2023-1671 Pre-auth Command Injection Vulnerability in the version 4.3.10.3 and earlier
- Oracle Weblogic: CVE-2020-2551 Unauthenticated RCE Vulnerability over IIOP based on 10.3.6.0, 12.1.3.0, 12.2.1.3.0, 12.2.1.4.0
- Boeing Data Breach: Boeing Vendor Information disclosed in data breach
- Juniper Junos OS: CVE-2023–36845 Juniper Junos OS EX, SRX Series PHP External Variable Modification RCE Vulnerability
- SysAid: CVE-2023-47246 SysAid ITSM File System Path Traversal
- ServiceNow Data Exposure Flaw: ServiceNow clients
References:
https://www.barracuda.com/company/legal/esg-vulnerability
https://thehackernews.com/2023/12/chinese-hackers-exploited-new-zero-day.html

