FOCUS FRIDAY: Addressing the Check Point’s Quantum Security Gateways and DNSBomb Attack Vulnerabilities: A TPRM Approach
Written by: Ferdi GülAdditional Contributions: Ferhat Dikbiyik
Welcome to this week’s Focus Friday, where we delve into critical vulnerabilities reshaping Third-Party Risk Management (TPRM) practices. Today, we spotlight two high-profile issues: Check Point’s Quantum Security Gateways and DNSBomb Attack incidents. Our discussion will not only cover the specifics of these incidents but also illustrate how Black Kite’s FocusTags™ can drive proactive risk management strategies.
CVE-2024-24919 in Check Point Quantum Security Gateways: A TPRM Perspective
What is the CVE-2024-24919 vulnerability?
CVE-2024-24919 is an information disclosure vulnerability in Check Point Security Gateways. This allows an attacker to attain certain sensitive information on internet-connected gateways that have some particular features configured:
- IPSec VPN
- Remote Access VPN
- Mobile Access Software Blade (includes Capsule Workspace)
This is considered a critical vulnerability, as it may be exploited remotely without user interaction, making it easy to compromise vulnerable systems.
Technical Details
CVE-2024-24919 is a vulnerability for information disclosure in Check Point Security Gateways. An attacker can exploit this vulnerability by accessing confidential information on gateways connected to the internet with Remote Access VPN or Mobile Access Software Blades enabled. This includes local account credentials, passwords, and other sensitive information. The hacker may capture user credentials from local gateway users to unauthorized access to other network systems. The vulnerability further allows the attacker to monitor network traffic flowing through the gateway, probably capturing sensitive information, such as passwords or credit card numbers.
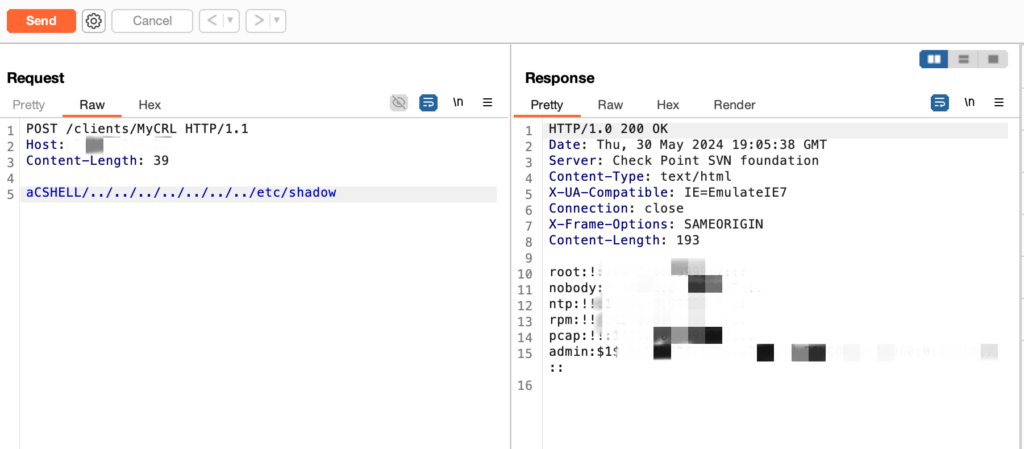
A payload for this vulnerability is available. The vulnerability was added to CISA’s Known Exploited Vulnerabilities catalog on May 30, 2024, indicating that threat actors can exploit the vulnerability to this day.In a PoC study by the Black Kite Research & Intelligence Team (BRITE), unauthorized remote access to critical directories like ‘etc/shadow,’ which contain user password-related information, was identified.
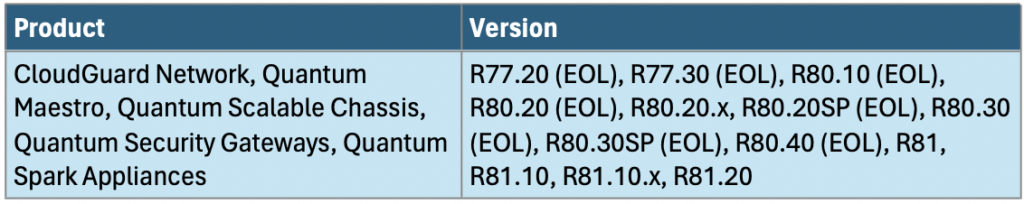
What is the scope of CVE-2024-24919?
Below is the products and their versions impacted by this vulnerability.
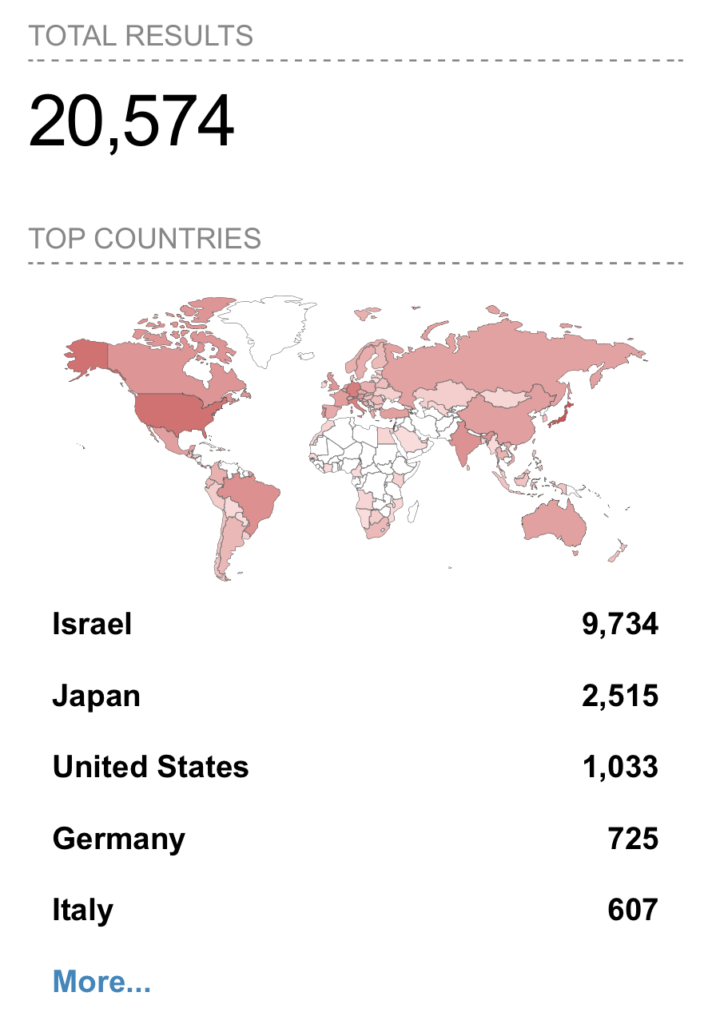
How many endpoints can be accessed through Check Point Quantum Gateway?
Recent research indicates that over 20,000 endpoints may be accessible externally.
Timeline for CVE-2024-24919:
May 27, 2024 (Monday)
- Check Point’s dedicated task force continued investigating unauthorized access attempts to customer VPN products.
May 28, 2024 (Tuesday)
- Check Point discovered a vulnerability in Security Gateways with IPsec VPN and the Mobile Access software blade.
- Public sources start reporting CVE-2024-24919. Details such as CVE assignment, CVSS score estimation, and security researchers’ initial analysis appear around this date.
- The vulnerability is publicly published on NVD and assigned the CVE-ID CVE-2024-24919.
May 30, 2024 (Thursday)
- The vulnerability was analyzed, and the FocusTagTM processing was completed by Black Kite’s Research Team.
- PoC details were shared publicly.
- The vulnerability was listed on CISA’s KEV catalog.
TPRM Implications
Considering that the vulnerability allows attackers to access sensitive data, any Tier 1 vendor with access to such data susceptible to CVE-2024-24919 poses a significant risk.
To mitigate the risk associated with CVE-2024-24919, TPRM professionals should follow these steps:
- Conduct an immediate review of your Third-Party Risk Management (TPRM) program to identify all vendors using Check Point Security Gateways with Remote Access VPN or Mobile Access enabled.
- Reach out to these vendors and inquire about their:
- Awareness of CVE-2024-24919.
- Patching status for their Check Point Security Gateways.
- Security measures are in place to mitigate the vulnerability.
- Don’t solely rely on vendor responses. If possible, verify they have patched their gateways by requesting confirmation or conducting your scans (with proper authorization).
- Expand your monitoring programs to detect suspicious network activity that might indicate exploitation attempts targeting Check Point Security Gateways.
Engaging with Vendors Regarding CVE-2024-24919
Attackers could exploit the issue to extract information from exposed Gateways if certain VPN features are enabled. Proactive communication with your vendors is necessary to ensure you are covered. The key questions to ask are:
- Has Check Point released a security patch for your Check Point Security Gateway model on the CVE-2024-24919?
- Do you have a managed service provider responsible for your Check Point Security Gateway?
- How does your vendor ensure their infrastructure is not exposed to CVE-2024-24919 exploits?
- Beyond patching, what other mitigation actions are your vendors taking regarding CVE-2024-24919?
Open communication with your vendors will give you an exact picture of how they address this vulnerability. Armed with this information, you’ll be more empowered to make informed decisions about the security of your Check Point Security Gateways.
How can vendors detect and remediate CVE-2024-24919?
- Apply the security hotfix: Check Point released the last modified security hotfix on May 30, 2024, specifically for CVE-2024-24919. The hotfix details are on the Check Point support page.
- Enable IPS and SSL Inspection: Check Point recommends enabling IPS and SSL Inspection on the Security Gateway to block attempts to exploit this vulnerability.
- Apply to Security Gateways with IPsec VPN Blade or Mobile Access Software Blade enabled.
- For online Security Gateways, find the Hotfix in CPUSE. Install via Gaia Portal: Software Updates > Available Updates > Hotfix Updates, then click Install. A confirmation window will display. Reboot the Security Gateway.
- Manual download is available from the official Check Point site.
- Disable Remote Access VPN or Mobile Access to reduce the attack surface if not needed.
- Strengthen local account security: remove local users and rotate passwords for LDAP accounts.
- Monitor network traffic for unusual activities.
Mitigating Vendor Risk of CVE-2024-24919 with Black Kite’s FocusTags™
On May 30, 2024, the Black Kite platform applied a FocusTag for CVE-2024-24919. Black Kite customers can filter by this FocusTag to identify their Tier 1 vendors susceptible to this vulnerability and communicate with them with risk intelligence (including the IT asset information) provided by Black Kite.

DNSBomb Attack in Dnsmasq, CoreDNS, Knot DNS, Simple DNS Plus, Technitium DNS, MaraDNS: A TPRM Perspective
What is the DNSBomb Attack?
DNSbomb is a cyber attack that disrupts internet infrastructure by creating large-scale fake DNS records, preventing users from accessing websites and online services.

Below is how it works, as explained in the image:
- Long-period query sending:
- Attacker: The attacker starts by sending a low rate of DNS queries over an extended period.
- Attacker’s low-rate traffic: The traffic accumulates over time, as depicted by the clock and the term “Accumulating.”
- Query aggregation:
- Recursive Resolver: Recursive resolvers, the middlemen who resolve domain names, collect such DNS queries.
- Amplifying: The resolver amplifies the queries received from the attacker, as depicted by the swirling amplification icons.
- Holding response until near the timeout:
- Authoritative Nameserver: The authoritative nameserver gets these aggregated DNS queries; it holds off sending back responses until the query’s timeout is almost reached.
- Query-timeout and Response-timeout: This is visualized with the DNS queries and responses piling up, with the query and response timeouts notated.
- 4. Short-period response returning:
- Authoritative Nameserver: When timeouts occur, the authoritative name server sends back a large number of DNS responses within a short period.
- Target Server: This sudden flow of DNS responses is directed toward the target server, creating a pulsing DoS pattern in traffic.
- Concentrating: The traffic pulses concentrate the attack’s impact, overwhelming the target server.
What is the scope of the DNSBomb Attack?
DNSBomb Attack targets two major components:
Authoritative Nameserver: It floods the nameserver with amplified DNS traffic, which simply brings down the domain online by prohibiting the response to legitimate queries.
Recursive Resolvers: These are leveraged to amplify attack traffic that can overwhelm it, causing a loss of DNS resolution to many users and websites.
The impact of such an attack may vary from transient disruption of a particular domain to large-scale outages affecting vast swaths of the Internet’s DNS infrastructure.

CVE-2023-28450 affects all Dnsmasq versions before 2.90, allowing malicious actors to overload DNS servers with large EDNS.0 UDP packets, leading to denial of service and potential data corruption. The POC exploit code for vulnerabilities has not yet been published, and the vulnerabilities have not yet been added to CISA’s Known Exploited Vulnerabilities catalog.
Our research has revealed that Dnsmasq is the most remarkable in terms of accessibility to endpoints. Based solely on the vulnerable versions in our study, this software is generally accessible to over 190,000 endpoints.
TPRM Implications
For TPRM professionals, action will need to be taken swiftly. This vulnerability in DNS server software Dnsmasq may enable attackers to interrupt services via third parties. For a vendor where the unavailability would cause a major disruption, TPRM professionals should start an outreach to understand and mitigate the risk.
Here’s how to mitigate the risks:
- Conduct a thorough inventory: Identify all Dnsmasq deployments within your organization, including those used by third-party vendors.
- Prioritize patching: Ensure all identified Dnsmasq instances are updated to a version that addresses CVE-2023-28450—those being version 2.90 or later. Patch the most critical systems first to shrink the exploitation window.
- Alert third-party vendors: Notify any vendors managing Dnsmasq on your behalf of CVE-2023-28450. Engage with them to ensure timely patching of their deployments.
- Elevate monitoring: Expand monitoring programs to detect unusual activity targeting DNS servers. Better vigilance will help the organization detect potential attempts to exploit the vulnerability CVE-2023-28450 and will take action timely.
Questions to ask Vendors for DNSBomb
- What cardinal signs indicate a DNSBomb Attack, and what distinguishes it from a conventional DDoS?
- What would be the effect on our organization if it was a successful hit on us by a DNSBomb Attack?
- Where are the weak points in our DNS infrastructure that could make us an easier target for such attacks?
- Do we have any tools or systems to detect or prevent DNSBomb Attacks?
- Is it worth considering purchasing specialized tools or monitoring services to improve our defense?
- How can the configuration of our DNS servers be made harder to prevent these kinds of attacks? Do we have a documented plan for responding effectively in case we ever experience a DNS bomb Attack?
- What immediate steps should be taken if we suspect or confirm an attack?
- How do we ensure continuity of business during and after a DNSBomb Attack?
- Will our security team’s discussion of these questions lead to a complete strategy for mitigating the risks arising from DNSBomb Attacks?
How can vendors detect and remediate CVE-2023-28450?
Here are some general code auditing practices:
- Patch Dnsmasq to version 2.90 or later.
- Temporary, lower max EDNS.0 UDP packet size in Dnsmasq config (might cause compatibility issues).
Mitigating Vendor Risk of CVE-2023-28450 with Black Kite’s FocusTags™
On May 28, 2024, the Black Kite platform provided the FocusTag for CVE-2023-28450. The vulnerability highlights the potential risks associated with unpatched DNS software and underscores the importance of proactive security measures to safeguard critical network infrastructure components.
the event for TPRM professionals.
Enhancing TPRM Capabilities with Black Kite’s FocusTags™
Effective Third-Party Risk Management (TPRM) is crucial in today’s dynamic cybersecurity landscape. Black Kite’s FocusTags™ for Check Point’s Quantum Security Gateways and DNSBomb attack vulnerabilities specifically address the unique challenges posed by these incidents. Here’s how these tags are critical in managing third-party risks:
- Immediate Threat Identification: Rapidly pinpoints vendors affected by the Check Point’s Quantum Security Gateways or the DNSBomb attack vulnerabilities, enabling swift mitigation actions.
- Risk Prioritization: Assists in categorizing vendor risks, focusing on those with the highest exposure due to these specific incidents.
- Strategic Vendor Interactions: Facilitates detailed discussions with vendors about their exposure to the Check Point’s Quantum Security Gateways or the DNSBomb Attack vulnerabilities, ensuring they understand the risks and mitigation strategies.
- Comprehensive Security Enhancement: Provides insights into the cascading impacts of the Check Point’s Quantum Security Gateways or the DNSBomb attack vulnerabilities, helping to bolster overall security posture and resilience.
With these FocusTags™, Black Kite translates intricate threat data into actionable intelligence, empowering TPRM professionals to manage and mitigate risks associated with specific high-profile incidents proactively.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
About Focus Friday
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FocusTagsTM in the Last 30 Days:
- Checkpoint SNX: CVE-2024-24919, An Information Disclosure Vulnerability in Check Point’s CloudGuard Network, Quantum Maestro, Quantum Scalable Chassis, Quantum Security Gateways, Quantum Spark Appliances
- DNSBomb: CVE-2023-28450, DNSBomb Attack in Dnsmasq, CoreDNS, Knot DNS, Simple DNS Plus, Technitium DNS, MaraDNS, CoreDNS
- Veeam VBEM: CVE-2024-29849, Authentication Bypass Vulnerability in Veeam Backup Enterprise Manager.
- Multi Connect: CVE-2023-43208, Deserialization of Untrusted Data Vulnerability, RCE Vulnerability in NextGen Healthcare Mirth Connect.
- Cacti: CVE-2024-25641, Remote Code Execution Vulnerability in Cacti
- Veeam SPC: CVE-2024-29212, Remote Code Execution Vulnerability in Veeam Service Provider Console
- TinyProxy: CVE-2023-49606, Use-After-Free Vulnerability, RCE Vulnerability in Tinyproxy
- ArubaOS: CVE-2024-26304, Buffer Overflow Vulnerability, Remote Code Execution Vulnerability in ArubaOS
- CrushFTP VFS: CVE-2024-4040, a Server Side Template Injection Vulnerability in CrushFTP
- Sisense Client
- FortiClient EMS: CVE-2023-48788, SQL Injection Vulnerability in Fortinet’s FortiClient Endpoint Management Server
- FortiOS SSL VPN: CVE-2024-21762, A Out-of-Bounds Write Vulnerability in FortiOS [Tag updated]
- Outlook RCE: CVE-2023-36439, RCE Vulnerability in Microsoft Exchange Server
- Change Healthcare Client
- JetBrains TeamCity: CVE-2023-42793, Authentication Bypass in JetBrains TeamCity CI/CD Servers; CVE-2024-27198, Authentication Bypass Vulnerability [Tag Updated]
- ScreenConnect:CVE-2024-1709, Authentication Bypass Vulnerability
- Cisco ASA [Suspected]CVE-2020-3259, Information Disclosure Vulnerability
- Exchange Server:CVE-2024-21410,Privilege Elevation Vulnerability
- QNAP QTS:CVE-2023-47218, CVE-2023-50358, OS Command Injection Vulnerability
- Symantec MG [Suspected]:CVE-2024-23615, CVE-2024-23614, Buffer Overflow Vulnerability (Remote Code Execution)
- FortiOS SSL VPN [Suspected]:CVE-2024-22024, An Out-of-Bounds Write Vulnerability
- RoundCube [Suspected] :CVE-2023-43770, Stored-XSS Vulnerability [Updated]
- Citrix ADC/Gateway:CVE-2023-6549 [Updated], Buffer Overflow Vulnerability
- Ivanti EPMM:CVE-2023-35082 [Updated], Authentication Bypass Vulnerability
- GoAnywhere [Suspected]:CVE-2024-0204, Authentication Bypass Vulnerability
- Redis RCE: CVE-2023-41056, Remote Code Execution Vulnerability
- Ivanti ICS: CVE-2024-21887, Command Injection Vulnerability, CVE-2023-46805, Authentication Bypass Vulnerability
References:
https://nvd.nist.gov/vuln/detail/CVE-2024-24919
https://support.checkpoint.com/results/sk/sk182336
https://labs.watchtowr.com/check-point-wrong-check-point-cve-2024-24919/#
https://nvd.nist.gov/vuln/detail/CVE-2023-28450
https://cybersecuritynews.com/new-dos-attack-dnsbomb-exploiting
https://thehackernews.com/2024/05/researchers-warn-of-catddos-botnet-and.html

