2018 Guide to Select 3rd Party Cyber-Risk Assessment Tool
Written by: Black Kite
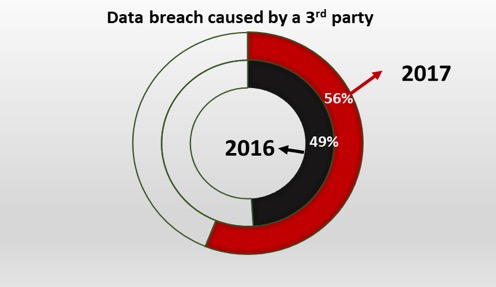
A recent survey conducted by Ponemon Institute reveals that 56% of companies have experienced a 3rd-party breach in 2017, which is an increase of 7% compared to previous year. Another survey conducted by Deloitte in 2016 was more depressive, reporting that 87% of organizations have experienced a disruptive incident with third-parties in the last 2-3 years. Another research in 2016, sourced by Soha Systems, reports that 63% of all breaches were related to third parties. The findings in these studies confirm that third-party cyber risk assessment is a must. The goal of this paper is to provide a review on third-party cyber risk assessment/scoring tools that automatically gather and analyze open source data and provide a risk score/security rating.
What is Third-Party
Third-parties include broad range of companies you directly worked with such as data management companies, law firms, e-mail providers, web hosting companies, subsidiaries, vendors, sub-contractors, basically any company whose employees or systems have access to your systems or your data. However, third-party cyber risk is not limited to these companies. Any external software or hardware that you use for your business also poses a cyber risk. Even the JavaScript that is added to your website for analytics may cause a breach by exposing the information of people that visit your website. Recent hacks (like CCleaner in 2017) exposed backdoors to well-known software have confirmed that the definition of third-party should not be limited to only the companies that you directly work with. Even IoT devices can be considered as a third-party and can be source of a breach. Very recently a casino was hacked through its Internet-connected thermometer in an aquarium in the lobby of the casino. For more info on third-party cyber risk, check out our 2018 third-party cyber risk report here.
Breaches Caused by Third-Parties
The figure below shows recent breaches/incidents caused by third-parties, varying from law, accounting, HVAC firms to companies that provide web hosting, data management, e-mail services, etc.
How to Assess Third-Party Risk?
Many companies either do not conduct any assessment of the cyber risk of third-parties or use old-school questionnaire methodology (they send a list of questions for third-parties to answer). First of all, questionnaire-based assessment is very time consuming (even though there are some online tools that simplify the process) and answers are not reliable. Even if we assume that answers are correct and we gather the results quickly, there might be some cyber risks that are invisible to third-party. This type of “hidden” risks can only be detected by gathering cyber threat intelligence and evaluating the risk.
Fortunately, there are several platforms that gather third-party cyber risk data and provide a risk score or security rating for companies. The information gathering is done by a method called “passive scan” where non-intrusive methods are used and company assets remain untouched. It is basically a hacker’s view of the third-parties external cyber risk. The open-source intelligence data is collected from many feeds such as reputation services, hacker sites/forums, vulnerability databases, Internet-wide scanners, social media, paste sites, black markets, underground forums, etc. Information gathering should be done for the company of interest and any related third-party company.
Key Players
The top players that provide such cyber risk scoring through passive scanning are BitSight, Black Kite, Security Scorecard, UpGuard, and Riskrecon. They all provide risk scores or security ratings for any company. This type of cyber risk assessment can be used for suppliers, joint-ventures, target acquisitions, franchisees, cyber insurance customers, etc.
There are also some new players like iTrust and Paris-based company Cyrating. Also few 10+ year-old cybersecurity companies such as RiskIQ, RiskSense, Tenable have been working on cyber risk scoring products and their contribution to this niche market will make it more competitive.
Comparison
In this study, we compare the key players’ cyber risk scoring products with Black Kite’s Cyber Risk Scorecard. Herein after, we will use notations Company A, B, C, and D for competitors.
Methodology
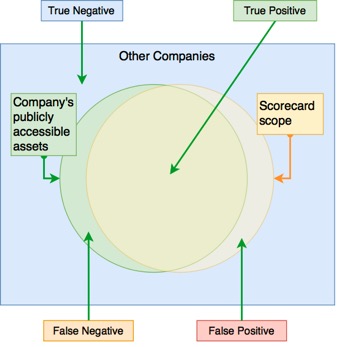
Since the methodology and data resources are similar, the differentiating factors are data quality, technical depth, reliability (true positive), coverage (true negative), usability and reporting capabilities. The ideal scorecard should sufficiently cover the target company’s and related third-parties’ assets and must exclude any findings that belong to other companies. In other words, the scoring system should be highly reliable (high true positive rate) and consistent (less false negative).
Threat Vectors Considered
We first look at the threat vectors covered. The number of threat vectors indicates the scorecard scope. As seen in the figure below, Black Kite provides a large scope for risk scoring. There are some threat vectors, such as DDoS resiliency that other products do not cover. The ability to keep the scope large comes from the broad digital footprint information gathered. Black Kite scorecard collects all domains, subdomains, IP addresses, DNS records, services, emails, ASNs, social media accounts, and company information with its proprietary algorithms. A large digital footprint intel with sensitive false-positive elimination (by computer and human analysts) gives a jump start to Black Kite compared to others. Because it increases visibility and reliability.
The below figure shows that Company C’s product has the narrowest scope. Even though they provide a quick scoring, the information they gather is not sufficient to give a reliable score. They also provide breach information if an add-on feature is separately purchased. Company D has a larger but limited scope that covers some essential threat vectors. Company A and B have both large scopes and provide additional information such as Endpoint Security or Software Security, but they miss threat vectors such as DDoS Resiliency, CDN Security, etc. Another downside of Company A is that it does not monitor fraudulent domains, which are the main source of phishing attacks that target the customers and/or employees of a company.
Scoring
There are no standards on scoring methodologies (yet) for risk scoring products. An easy-to-understand and consistent scoring is very important when assessing the cyber risk posture of your own company and your third-parties.
Some companies used numeric scoring (0 to 900 scoring) and some use letter grades ( A to F scoring). Black Kite uses both A to F letter grades and percentage (0 to 100 percent) for overall score and all risk categories. Company A has a similar scoring/grading system. Company B, on the other hand, provide a 0 to 1000 overall score and A to F letter grades for subcategories. Company C shows only one score (0 to 1000) and does not provide scores for risk vectors. Finally, Company D provide 0 to 10 score for both overall and subcategories.
Reporting and Alerting
An ideal third-party cyber risk scoring tool should provide useful reports for risk remediation and mitigation and also provide alerts for important risk factors (such as leaked info) via e-mail or SMS.
Black Kite Cyber Risk Scorecard provides very rich reports for each risk factor discovered with suggestions for mitigating the risk and also generates alerts via e-mail to notify IT security personnel about critical issues. Company A has similar features for reporting and alerting. Company D goes one step forward and creates a priority matrix based on severity of expected damage and importance of the asset that can be affected. Though, it is questionable how they determine importance of an asset.
While Company B does not provide an easy-to-generate report for remediation of risks, Company C does not give any suggestion at all.
Conclusion
In this paper, we provide a review of third-party cyber risk scoring tools that automatically gather information and provide a risk assessment. We evaluated top players in the market and compared their scorecard scope (number of threat vectors considered), digital footprint, scoring methodology, and reporting/alerting systems. We see that the Black Kite Cyber Risk Scorecard provides a larger scope with the discovery of a larger digital footprint, has a consistent and easy-to-understand scoring, and generates rich reports and alerts.