Focus Friday: Third-Party Risk Insights Into Atlassian Jira, Ivanti Connect Secure, and Nostromo nhttpd Vulnerabilities With Black Kite’s FocusTags™
Written by: Ferdi Gül
Welcome to this week’s Focus Friday, where we delve into high-profile vulnerabilities impacting third-party software and explore their implications for Third-Party Risk Management (TPRM). This edition examines two notable vulnerabilities: the path traversal vulnerabilities in Atlassian Jira, Ivanti Connect Secure, and Nostromo nhttpd. With each vulnerability carrying the potential for severe exploitation, our insights aim to equip TPRM professionals with the knowledge and tools necessary to understand the impact of these risks on their organizations and address them proactively. By leveraging Black Kite’s FocusTagsTM, we enable TPRM teams to respond swiftly and strategically to evolving cyber threats, mitigating the cascading effects of third-party vulnerabilities on enterprise security.
CVE-2021-26086: Path Traversal Vulnerability in Atlassian Jira
What is the Path Traversal Vulnerability in Atlassian Jira (CVE-2021-26086)?
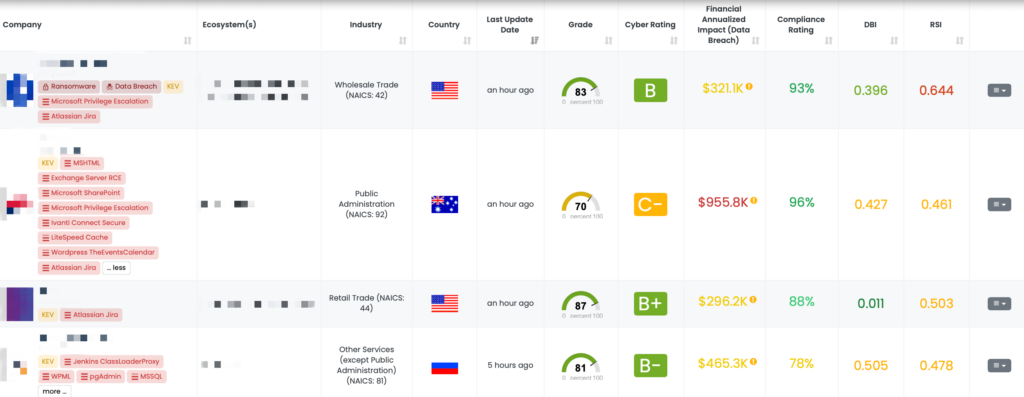
CVE-2021-26086 is a path traversal vulnerability in Atlassian Jira Server and Data Center versions prior to 8.5.14, between 8.6.0 and 8.13.6, and between 8.14.0 and 8.16.1. This vulnerability allows remote attackers to read specific files via a crafted request to the /WEB-INF/web.xml endpoint. The vulnerability has a CVSS score of 5.3, indicating a medium severity level, and an EPSS score of 97.11%, suggesting a high likelihood of exploitation.
PoC exploit code is available. It was first disclosed in August 2021 and has been actively exploited in the wild, with CISA adding it to their Known Exploited Vulnerabilities (KEV) catalog on November 12, 2024. The threat actor group Androxgh0st has been identified as exploiting this vulnerability.
You can access the workaround details shared on Atlassian’s official site here. However, upgrading to the latest version will help enhance your resilience against current and future vulnerabilities.
Why Should TPRM Professionals Be Concerned About CVE-2021-26086?
Third-Party Risk Management (TPRM) professionals should be concerned about CVE-2021-26086 because it allows unauthorized access to sensitive files on vulnerable Jira instances. If a vendor’s Jira system is compromised, attackers could gain access to internal project information, user data, and other confidential materials, potentially leading to data breaches and further exploitation within the organization’s network.
What Questions Should TPRM Professionals Ask Vendors Regarding CVE-2021-26086?
- Have you identified any instances of Atlassian Jira Server or Data Center within your infrastructure?
- If so, have these instances been updated to versions 8.5.14, 8.13.6, 8.16.1, or later to address CVE-2021-26086?
- What measures have you implemented to detect and prevent unauthorized access attempts exploiting this vulnerability?
- Can you provide details on any monitoring or logging mechanisms in place to identify potential exploitation of this vulnerability?
Remediation Recommendations for Vendors
- Upgrade Jira Instances: Update all Atlassian Jira Server and Data Center instances to the latest fixed versions (8.5.14, 8.13.6, 8.16.1, or later) to mitigate the vulnerability. Atlassian provides the latest versions (9.12.15) on their support site, ensuring protection against this and other known vulnerabilities.
- Implement Access Controls: Restrict access to Jira instances through secure methods such as VPNs and enforce strong authentication mechanisms.
- Apply Workarounds if Immediate Upgrade Isn’t Possible:
- Reverse Proxy/Load Balancer Configuration: Configure reverse proxies or load balancers to block path traversal attempts by denying requests containing traversal sequences.
- URL Rewrite Rules: Modify Jira’s urlrewrite.xml to redirect suspicious requests containing path traversal characters to safe URLs.
- Monitor Systems: Regularly review access logs and network traffic for unusual activities that may indicate exploitation attempts.
How Can TPRM Professionals Leverage Black Kite for CVE-2021-26086?
Black Kite’s FocusTag™ for Atlassian Jira, published on November 13, 2024, enables TPRM professionals to identify vendors potentially affected by CVE-2021-26086. By providing detailed information on vulnerable assets, such as specific IP addresses and subdomains, Black Kite allows organizations to prioritize assessments and remediation efforts effectively. This targeted approach helps reduce the scope of vendor inquiries, minimizing questionnaire fatigue and streamlining the risk management process.
Critical Ivanti Connect Secure Vulnerabilities
What Are the RCE and Privilege Escalation Vulnerabilities in Ivanti Connect Secure?
After creating our FocusTag™ for Ivanti Connect Secure, specifically for CVE-2024-37404 on October 9, 2024, we mentioned this FocusTag™ in our Focus Friday post on October 11, 2024. This week, Ivanti’s Security Advisory page published an update with 25 CVEs, and 14 of these, selected based on their criticality, are discussed below. You can find the other vulnerabilities here.
The vulnerabilities identified in Ivanti Connect Secure and Policy Secure include a total of 14 critical issues, such as use-after-free (CVE-2024-9420, CVE-2024-47906), stack-based buffer overflow (CVE-2024-47907), argument injection (CVE-2024-38655, CVE-2024-38656, CVE-2024-39710), command injection (CVE-2024-11007, CVE-2024-11006, CVE-2024-11005), and reflected XSS (CVE-2024-11004). These vulnerabilities enable attackers to escalate privileges, execute arbitrary commands, and in some cases, cause denial of service. Specifically:
- CVE-2024-9420: A use-after-free vulnerability in Ivanti Connect Secure versions prior to 22.7R2.3, allowing remote authenticated attackers to achieve remote code execution.
- CVE-2024-47906: Another use-after-free issue that allows local attackers to escalate privileges.
- CVE-2024-47907: A stack-based buffer overflow in the IPsec module of Ivanti Connect Secure, potentially causing a denial of service attack by unauthenticated remote attackers.
- CVE-2024-37400: An out-of-bounds read vulnerability leading to infinite loop and potential denial of service.
- CVE-2024-38655, CVE-2024-38656: Argument injection vulnerabilities that allow remote code execution with admin privileges.
- CVE-2024-39709: Incorrect file permissions, which could allow local attackers to escalate their privileges.
- CVE-2024-39710, CVE-2024-39711, CVE-2024-39712: Argument injection vulnerabilities enabling remote code execution.
- CVE-2024-11007, CVE-2024-11006, CVE-2024-11005: Command injection vulnerabilities allowing admin-level code execution.
- CVE-2024-11004: A reflected XSS vulnerability allowing privilege escalation through user interaction.
While these vulnerabilities are not yet reported to be exploited in the wild, the widespread use of Ivanti products in enterprise environments increases the potential risk. The Ivanti Connect Secure tag was updated on November 14, 2024, to reflect the latest risk assessment.
Why Should TPRM Professionals Be Concerned About These Vulnerabilities?
These vulnerabilities could enable unauthorized actors to access Ivanti systems, move laterally within a network, access sensitive information, or disrupt critical services. Given Ivanti Connect Secure’s role in VPN and access management, the exploitation of these vulnerabilities could lead to significant security and operational impacts for enterprises.
What Questions Should TPRM Professionals Ask Vendors About These Vulnerabilities?
- Have you applied the latest patches (e.g., Ivanti Connect Secure 22.7R2.3) to mitigate these vulnerabilities?
- Can you confirm if you have implemented the recommended mitigation steps provided by Ivanti, such as restricting admin access to the management interface, strengthening password policies and MFA protections, and disabling remote access where possible?
- Have you taken measures to monitor network traffic for any unusual activities, specifically in relation to the potential exploitation of the use-after-free, stack-based buffer overflow, argument injection, command injection, and reflected cross-site scripting (XSS) vulnerabilities identified in the Ivanti products?
- What additional precautions are in place to prevent privilege escalation or command injection attacks? Can you confirm if you have addressed the privilege escalation vulnerability (CVE-2024-39709) in Ivanti Connect Secure & Policy Secure by regularly auditing permissions, particularly for admin-level accounts?
Remediation Recommendations for Vendors
To mitigate these risks, vendors should:
- Upgrade to the latest versions—Ivanti Connect Secure 22.7R2.3, and Ivanti Policy Secure 22.7R1.2.
- Enable admin access only on the management interface, ensuring it is isolated from the internet by a firewall or jump-host.
- Implement strong passwords, regular password rotation, credential vaults, and multi-factor authentication (MFA) to further limit exposure.
- Regularly audit permissions, particularly for admin-level accounts, to prevent privilege escalation risks.
- For those unable to apply the update immediately, Ivanti provides mitigation steps, including restricting admin access to the management interface and strengthening password policies and MFA protections.
- Disable remote access where possible, and if remote access is essential, secure it via a VPN.
- Monitor network traffic for any unusual activities.
How Can TPRM Professionals Leverage Black Kite for These Vulnerabilities?
Black Kite’s updated FocusTag™ as of November 14, 2024, provides critical insights, including vulnerable IPs and subdomains, enabling TPRM professionals to focus on vendors directly impacted by these vulnerabilities. Black Kite’s detailed approach helps streamline the TPRM process by reducing questionnaire fatigue while enabling proactive risk management.

CVE-2019-16278 Nostromo nhttpd Path Traversal Vulnerability
What is the Nostromo nhttpd Path Traversal and Remote Code Execution Vulnerability?
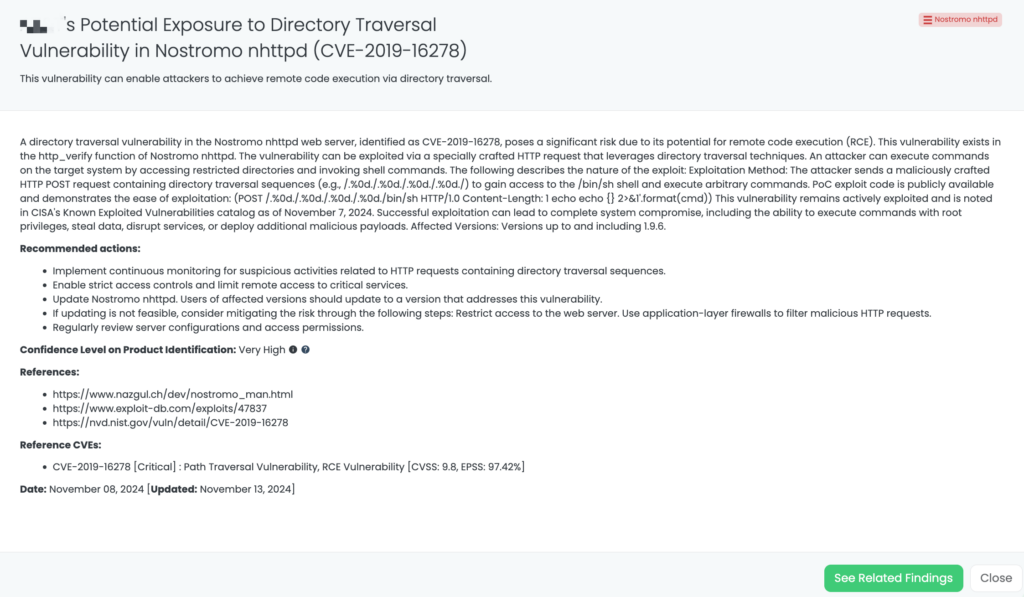
CVE-2019-16278 is a critical path traversal vulnerability in the Nostromo nhttpd web server, which can enable remote code execution (RCE). Rated with a CVSS score of 9.8 and an EPSS score of 97.46%, this vulnerability exists in the http_verify function of Nostromo nhttpd versions up to 1.9.6.
Attackers can exploit this flaw by sending a specially crafted HTTP POST request with directory traversal sequences to gain access to restricted directories and invoke commands on the target system. The vulnerability can lead to complete system compromise, allowing unauthorized code execution with root privileges, potentially stealing sensitive data, disrupting services, or deploying additional malicious software.
Discovered in 2019, this vulnerability remains actively exploited. Recently added to CISA’s Known Exploited Vulnerabilities (KEV) catalog on November 7, 2024, this vulnerability has been observed in real-world attack campaigns.
Why Should TPRM Professionals Care About Nostromo nhttpd Vulnerabilities?
For TPRM professionals, vulnerabilities in the Nostromo nhttpd web server present significant third-party risks due to the severity of potential impacts. An attacker exploiting this vulnerability can execute code with high-level privileges, enabling unauthorized access to critical data, systems, and even broader network infiltration. Organizations relying on third-party vendors using Nostromo nhttpd could face exposure to breaches involving sensitive information, service interruptions, and reputational damage. This vulnerability’s presence in publicly accessible servers magnifies the risk for organizations across various sectors.
What Questions Should TPRM Professionals Ask Vendors About Nostromo nhttpd Vulnerabilities?
To assess risk mitigation, TPRM professionals should ask vendors the following questions:
- Have you upgraded Nostromo nhttpd to a version beyond 1.9.6 that addresses CVE-2019-16278? If updating Nostromo nhttpd was not feasible, have you restricted access to the web server and used application-layer firewalls to filter malicious HTTP requests as recommended in the advisory?
- What measures are in place to restrict web server access and monitor HTTP requests for directory traversal patterns?
- How do you regularly assess server configurations and permissions for vulnerabilities?
- Are there any incident response procedures for detecting and responding to suspected exploits of this vulnerability?
Remediation Recommendations for Vendors Subject to this Risk
Vendors using Nostromo nhttpd should consider these recommended actions:
- Upgrade to a version of Nostromo nhttpd that addresses CVE-2019-16278 to eliminate the vulnerability.
- If immediate upgrade is not feasible, implement workarounds, such as:
- Restricting server access to trusted IP ranges.
- Using application-layer firewalls to block malicious HTTP requests targeting directory traversal sequences.
- Implement continuous monitoring for suspicious activities related to HTTP requests containing directory traversal sequences.
- Regularly review server configurations and access permissions.
- Enable strict access controls and limit remote access to critical services.
How TPRM Professionals Can Leverage Black Kite for This Vulnerability
Black Kite helps TPRM professionals identify vendors affected by CVE-2019-16278 through a comprehensive FocusTag™, released on November 8, 2024. With detailed asset information, including IP addresses and subdomains, Black Kite empowers TPRM professionals to operationalize the risk, enabling early intervention. For TPRM teams, this capability enhances monitoring and response to vendor security issues, adding a valuable layer of defense against potential exploitation.
Enhancing TPRM Strategies With Black Kite’s FocusTags™
In today’s fast-paced cyber threat landscape, staying ahead of vulnerabilities is essential for a robust Third-Party Risk Management (TPRM) approach. Black Kite’s FocusTags™ are designed to provide critical insights that enhance these strategies, transforming complex threat information into actionable intelligence. Here’s how these tags help TPRM professionals respond effectively to vulnerabilities like those recently highlighted in Atlassian Jira, Ivanti Connect Secure and Nostromo nhttpd:
- Real-Time Vulnerability Tracking: Black Kite’s FocusTags™ immediately identify vendors affected by emerging vulnerabilities, enabling TPRM teams to implement responses promptly and accurately.
- Strategic Risk Prioritization: FocusTags™ help prioritize risks by combining vendor criticality with vulnerability severity, allowing organizations to allocate resources to the most pressing risks.
- Enhanced Vendor Communication: By offering vendor-specific insights, FocusTags™ facilitate productive conversations with vendors about their exposure and response to particular vulnerabilities.
- Comprehensive Threat Landscape Overview: Black Kite’s FocusTags™ provide a broad view of the cybersecurity landscape, supporting the development of more resilient defenses against evolving threats.
Through Black Kite’s FocusTags™, TPRM professionals gain an invaluable tool for managing third-party cyber risks in a constantly changing environment, ensuring that vulnerabilities are managed proactively to protect enterprise security.
But having these vulnerability insights is only one step in the process. You need to work with your vendors to remediate these risks effectively and efficiently. For a comprehensive guide on transforming vendor collaboration in times of urgency, check out our latest interactive guide, Chaos to Collaboration: Transforming Third-Party Risk Response for Zero-Day Events. Learn how to streamline communication, prioritize vendor actions, and implement scalable workflows that keep your third-party risk response strong when every second counts.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
About Focus Friday
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FocusTags™ in the Last 30 Days:
- Atlassian Jira: CVE-2021-26086, Path Traversal Vulnerability in Atlassian Jira Server and Data Center.
- Ivanti Connect Secure:
- Nostromo nhttpd: CVE-2019-16278, Path Traversal Vulnerability, RCE Vulnerability in Nostromo nhttpd.
- LiteSpeed Cache: CVE-2024-50550, Privilege Escalation Vulnerability iin LiteSpeed Cache plugin.
- RICOH Web Image Monitor: CVE-2024-47939, Buffer Overflow Vulnerability in RICOH Web Image Monitor.
- Squid Proxy: CVE-2024-45802, DoS Vulnerability in Squid Proxy Servers.
- XLight FTP: CVE-2024-46483, Integer Overflow and RCE Vulnerabilities in XLight FTP Servers.
- Exchange Server RCE: CVE-2021-26855, CVE-2021-27065, CVE-2021-26858, CVE-2021-26857, Remote Code Execution Vulnerability in Exchange Server.
- FortiManager: CVE-2024-47575, Missing Authentication Vulnerability in FortiManager.
- Grafana: CVE-2024-9264, Remote Code Execution Vulnerability in Grafana.
- Roundcube Webmail: CVE-2024-37383, Cross-Site Scripting (XSS) Vulnerability in Roundcube Webmail.
- Cisco FMC: CVE-2024-20424, Command Injection Vulnerability in Cisco Secure Firewall Management Center.
- Oracle WebLogic Server: CVE-2024-21216, Remote Code Execution Vulnerability in Oracle WebLogic Server.
- GitHub Enterprise: CVE-2024-9487, SAML SSO Authentication Bypass Vulnerability in GitHub Enterprise Server.
- Fortinet Core Products: CVE-2024-23113, Format String Vulnerability in FortiOS, FortiPAM, FortiProxy, and FortiWeb.
- Cisco RV Routers: CVE-2024-20393, CVE-2024-20470, Privilege Escalation and RCE Vulnerability in RV340, RV340W, RV345, and RV345P Dual WAN Gigabit VPN Routers.
- Ivanti Connect Secure: CVE-2024-37404, Remote Code Execution Vulnerability in Ivanti Connect Secure & Policy Secure.
- Zimbra: CVE-2024-45519, Remote Command Execution Vulnerability in Zimbra.
- DrayTek Routers: CVE-2020-15415, Remote Code Execution Vulnerability in DrayTek Vigor Routers.
- Authentik: CVE-2024-47070, Authentication Bypass Vulnerability in Authentik.
- Octopus Deploy: CVE-2024-9194, SQL Injection Vulnerability in Octopus Server.
References
https://nvd.nist.gov/vuln/detail/cve-2021-26086#range-13344932
https://packetstormsecurity.com/files/164405/Atlassian-Jira-Server-Data-Center-8.4.0-File-Read.html
https://jira.atlassian.com/browse/JRASERVER-72695
https://confluence.atlassian.com/jirakb/workaround-for-cve-2019-15004-979416164.html
https://nvd.nist.gov/vuln/detail/CVE-2024-11004
https://nvd.nist.gov/vuln/detail/CVE-2024-9420
https://nvd.nist.gov/vuln/detail/CVE-2024-47906
https://nvd.nist.gov/vuln/detail/CVE-2024-47907
https://nvd.nist.gov/vuln/detail/CVE-2024-37400
https://nvd.nist.gov/vuln/detail/CVE-2024-38655
https://nvd.nist.gov/vuln/detail/CVE-2024-38656
https://nvd.nist.gov/vuln/detail/CVE-2024-39709
https://nvd.nist.gov/vuln/detail/CVE-2024-39710
https://nvd.nist.gov/vuln/detail/CVE-2024-39711
https://nvd.nist.gov/vuln/detail/CVE-2024-39712
https://nvd.nist.gov/vuln/detail/CVE-2024-11007
https://nvd.nist.gov/vuln/detail/CVE-2024-11006
https://nvd.nist.gov/vuln/detail/CVE-2024-11005
https://nvd.nist.gov/vuln/detail/CVE-2019-16278#range-13412787

