New Ransomware Group Triples Extortion Campaign with DDoS Threats
Written by: ceren
Written by Gokcen Tapkan
Edited by Haley Williams
Threat actors evolve their techniques every day, especially their attack vectors. Their extortion models already have “data theft” and an “encrypted-unavailable system” under their toolbelt. A recent attack reveals the Distributed-Denial-of-Service (DDoS) threat is the latest addition to the extortion list, and threat actors now threaten their victims with a DDoS threat if they do not fulfill their demands.
The New DDoS Ransomware Threat: Yanluowang
According to the latest discovery by the Symantec Threat Hunter Team, a new ransomware strain is on the block. “Yanluowang”, a malware named after the extension it adds to the encrypted files, is still in the development process.
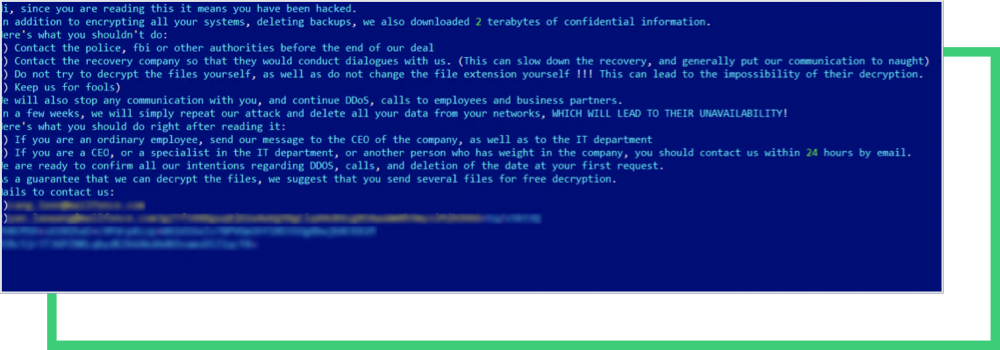
The above note was captured from a recent attack on a high-profile company. In the note, the Yanluowang ransomware operators threatened to conduct DDoS attacks if the victim contacted law enforcement, or did not not otherwise adhere to their “rules.”
The attack was initially uncovered through a suspicious activity of AdFind on a computer, an Active Directory search tool. Although the tool is legitimate, it’s in the “usual suspects” list for ransomware operators, often leveraged in reconnaissance activities.
After a detailed code analysis, the ransomware strain was still found to be under development. Threat actors then deployed the ransomware that:
- Shut down all hypervisor virtual machines
- Stopped all the running processes, including backup solutions and SQL
- Encrypted the files with the extension .yanluowang
- Left a ransom note on the compromised computer
What is a DDoS Attack?
A DDoS attack is an attempt to overwhelm an organization’s network by flooding it from a multitude of sources; mainly from the attacker’s bot army (i.e., botnet). DDoS attacks targets’ various resources, from banks to news websites, preventing people, users, etc from accessing information or critical financial operations.
DDoS attacks provoked a global security crisis after reaching 5.4 million total incidents in the first half of 2021, up 11% from the year prior. Data forecasts expect that to remain consistent throughout the year, indicating 11 million global DDoS attacks are expected this year. The attacker innovation is projected to persist, generating a growing cybersecurity issue that will affect both public and private sector companies.
How Protected are Today’s Companies Against DDoS Attacks?
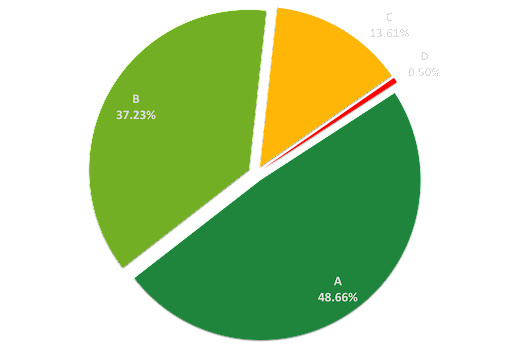
The Black Kite research team selected a sample of 50,000 companies in order to better understand the DDoS Resiliency of organizations across different industries. Of the over 600 companies that have been hit by ransomware in 2021, just over 20% have “C” and “D” grades, indicating bad and poor cyber posture regarding DDoS resiliency.
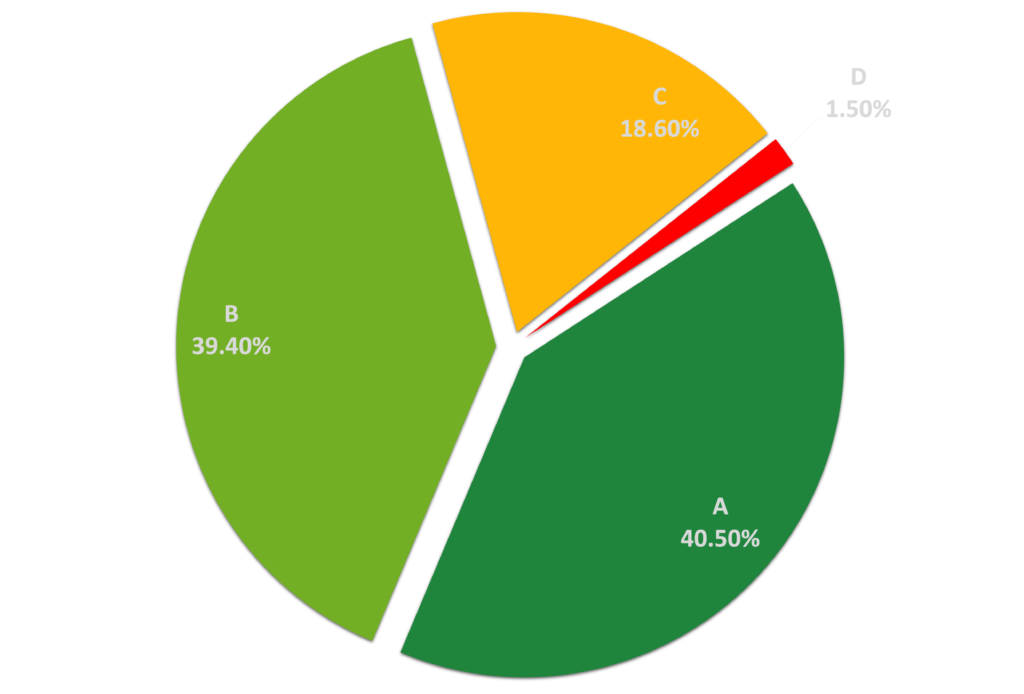
How it Works: Black Kite’s “DDoS Resiliency” category results from 15 different potential DDoS checks and detects any potential DDoS amplification endpoints. Black Kite gathers the data from non-intrusive scanners and other internet-wide scanners. The automated platform depicts DDoS Resiliency in letter grades on an A-F scale whereas A indicates very high resiliency, while F means very low.
A DDoS attack may come in many shapes and sizes. Some of the controls Black Kite tests in the “DDoS Resiliency” category include:
- UDP Flood: A UDP flood attack is a denial-of-service (DoS) attack using the User Datagram Protocol (UDP) while also spoofing the IP address of the UDP packets. It ensures that the excessive ICMP return packets do not reach them and anonymizes their network location(s).
- DNS Amplification: DNS amplification attacks are orchestrated when the attacker instructs bots or a botnet to send DNS queries with a forged source address to a legitimate server, which results in a large response sent back to the attacker’s victim
- DNS Flood: A DNS flood is a type of distributed denial of service attack (DDoS) where an attacker floods a particular domain’s Domain Name System (DNS) servers in an attempt to disrupt DNS resolution for that domain.
- WordPress XMLRPC: XML-RPC on WordPress is actually an API or “application program interface”. Attackers can launch brute force amplification attacks against WordPress XMLRPC.
How Do I Build DDoS Resiliency?
Organizations already targeted by ransomware groups should avoid cascaded extortions by improving their DDoS resiliency. Threat actors search for signals that help them to execute a successful and more severe DDoS attack. For instance, name or email servers under the same subnet without redundancy on other subnets indicate a target where a DDoS attack will prevent them from functioning correctly for a while.
Another example would be providing access to the WordPress XML-RPC file (xmlrpc.php). Attackers can launch brute force amplification attacks against WordPress XMLRPC as a part of the DDoS attacks. DDoS resiliency of a company can be measured by checking such indicators.
How Does Black Kite Help Defend Against Ransomware?
Ransomware is the most common cyber threat today, and the ransomware gangs have developed advanced techniques to ensure they’re paid successively. Double extortion techniques are becoming much more common, whereas a company’s data is stolen before encryption, and then the company is threatened with data leakage if the ransom is not paid. The DDoS threat is the third level of extortion for some groups.
Black Kite takes this all into account and continuously monitors the Ransomware Susceptibility Index® (RSI™) for all customers and their vendors.
Get Your Free RSI™
