What should cyber security’s role in sourcing and procurement be?
Written by: Black Kite
By Haley Williams, from the perspective of Jeffrey Wheatman, Cyber Risk Evangelist
There seems to be a split opinion on this question, from both cybersecurity teams and vendor procurement teams.
The general consensus is that the interaction between the two teams should be bidirectional: Security teams should be informing sourcing, procurement and vendor management (SPVM) teams, and sending data to build procurement processes.
In sourcing and procurement, SPVM teams are looking at a multitude of factors that do not always prioritize or include security. Interaction with security teams guarantees that they are informed of these issues before decision-making begins.
The past of procurement
Historically, it had been a very questionnaire-based process. IT and security professionals created the questionnaires, leaving them simpler and less involved for the vendor. Parsing the questionnaires allowed for a manual process of discovering where potential risks could fall and what implications there could be.
However – these processes are not just one after another, and call it a day. It should be an ongoing process. A cyclical flow that has review sessions cycled back in creates a more proactive environment to catch particularly risky issues with vendors, especially in today’s digital supply chain environment.
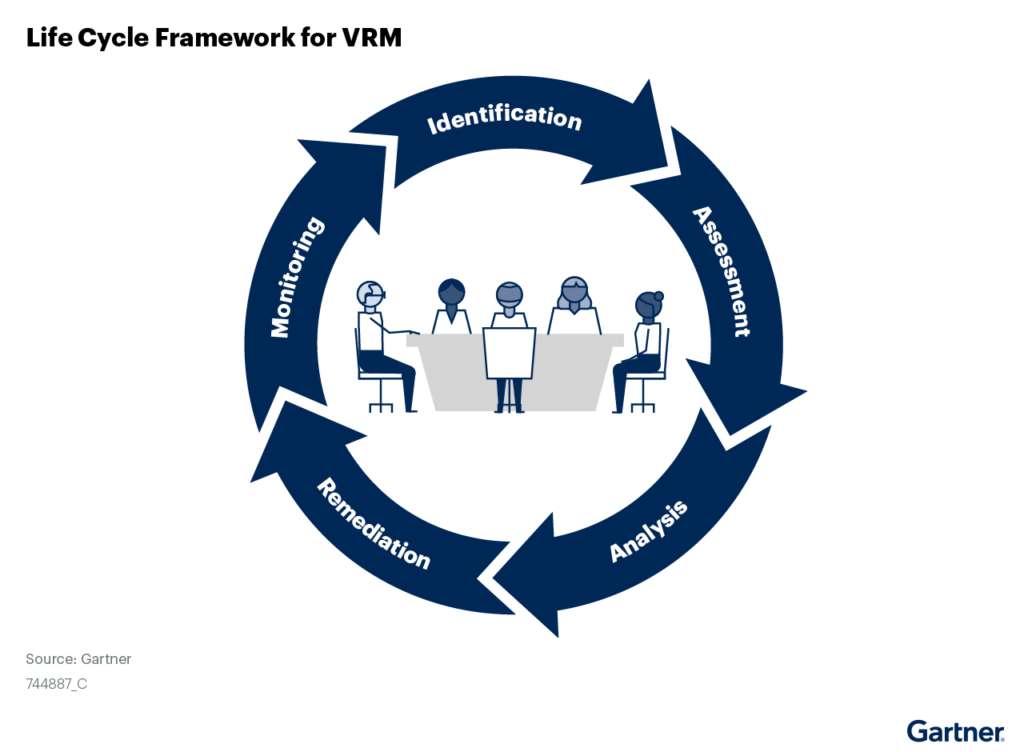
SVPM should be engaging security professionals earlier in the process
What often happens (and this is what not to do) – Vendor procurement goes out and acquires a company or vendor and then comes to their security team after the fact and asks “What do you think?” But the deal has already been written – the contract has already been signed. While they are still asking, the vendor is already being thrown into the supply chain, whether or not they are secure enough to be accessing data.
Who owns the risk?
The business owns the risk, but the accountability is not sure where to rest. Does it lie with those making the business decisions? When speaking to our customer advisory board, only 5 out of 8 said they had the power to stop a deal, and only if they felt that the security risks were too high for the company. (Which is actually pretty good.)
But the flip side is, they’re some of the best security professionals we know. Not everyone has that experience working as a security team trying to have a voice in the decision-making.
So how can security professionals work with the business to help reveal what the cyber exposures are from a cyber security perspective?
The risks of forgoing a security-forward approach
Forfeiting shared company data is one of the main things to focus on when prioritizing security in vendor procurement. However, supply chain cyber risk (and cascading business downtime) is a much bigger liability to endure and, ultimately, accept. What happens when a breach in the supply chain causes your business to halt operations due to a key partner having to suspending their own operations?
When speaking with an old Gartner colleague, it was shared that procurement teams are often looking for input and insight from the security teams to help them to understand what questions to ask, what red flags to look for, and what risks they should focus on.
Procurement teams might not have the perspective and knowledge to assess those risks, so security is brought in again. It creates a high-effort, high-investment process, sometimes involving questionnaires with hundreds of line items, being received from hundreds of vendors in one supply chain (time to do some math!)
On the flip side, everyone is trying to speed up their procurement and onboarding process for new vendors. Procurement may have a tool they want to begin using, but they have to gain the trust of the security teams on using said tool (hopefully Black Kite.)
How can Black Kite help?
We work with a multitude of industries, and each industry has its own supply chain to worry about, whether that is physical/operational or digital.
We work with companies that not only have records and data to protect, but also have process dependencies. Black Kite can provide insight into the likelihood that a critical vendor in the supply chain will get hit with ransomware, halt deliverance on goals and objectives, and in turn have a direct effect on the company at hand.
With automation that is quick, efficient, and more powerful than manually handling hundreds of questionnaires, Black Kite brings a unique and lucrative value proposition to procurement and security teams alike.
See it for yourself
