The Top Five Third-Party Data Breaches in June 2021, Revealed
Written by: Black Kite
Automotive manufacturers have stepped up into the passenger’s seat of the cybercrime hit list. Digital transformation, supply chain complexities and a “physical safety comes first” mindset have enabled cybercriminals to get ahead of the curve. In contrast to the age-old idiom, “slow and steady” will not win the race toward supply chain security.
Despite the majority (71%) of automotive CIOs indicating plans to increase their cyber and information security investments in 2021, major industry manufacturers were involved in the top two third-party data breaches that closed out the first half of the year.
1. Millions of personal records for Volkswagen and Audi customers were exposed through a vendor database.
Volkswagen announced that a significant data breach exposed the personal information of over 3.3 million customers after one of its vendors, Shift Digital, left a cache of unencrypted consumer data on the internet. According to the carmaker, leaked data included the personal information used for marketing to both Volkswagen/ Audi customers and interested buyers.
Although the breach is believed to have occurred between August 2019 and May 2021, the exposed information was collected between 2014 and 2019. The data included driver’s license numbers, names, mailing addresses, email addresses, numbers and, in some instances, information surrounding the vehicle that was purchased.
Unsecured databases by vendors continue to be a top issue in supply-chain breaches. Accounting for at least 13% of third-party related breaches, misconfigured servers are almost an open invitation to hackers. For more information on keeping your servers protected, check out our full list of common misconfigurations and steps to prevent them.
2. Another cybersecurity breach impacted over 1 million Mercedes-Benz customers.
Mercedes-Benz is the second German carmaker to disclose a data breach in June 2021. Although the disclosure had many similarities, the automotive manufacturer did not name the third-party vendor responsible for the leak that may have impacted 1.6 million customers and prospects. Still, it was reported that very few sensitive records were stolen.
Vendor-caused vulnerabilities are a major concern for the automotive sector, especially as supply chains continue to increase in complexity. The Black Kite Research Team recently uncovered that more than 17% of automotive suppliers are likely to incur a ransomware attack, further emphasizing the need for third-party risk management programs.
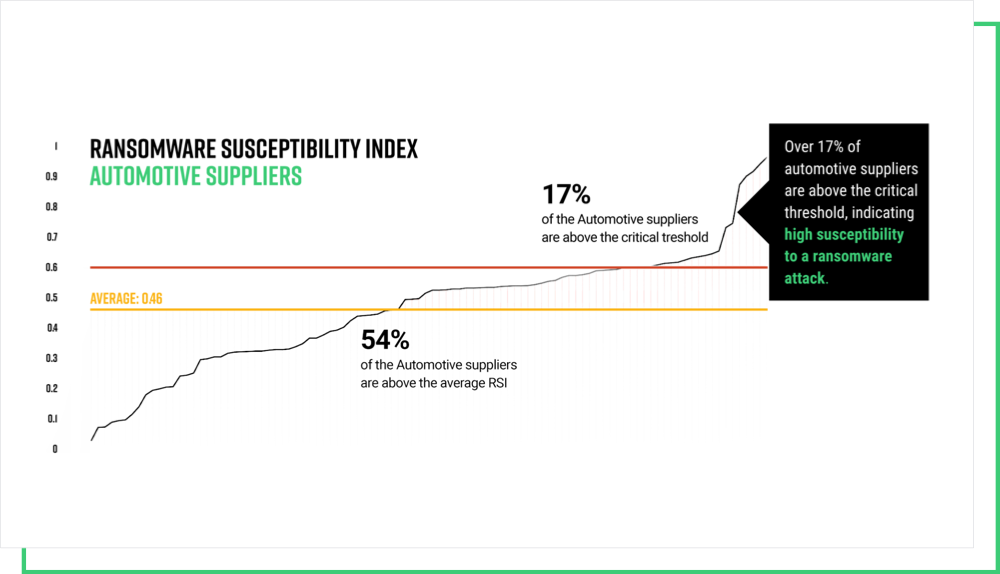
Download our report for a detailed analysis of the state of cybersecurity across automotive supply chains.
3. Patient data records were accessed through a cloud-based storage vendor.
A major compromise of protected health information (PHI) surfaced after Elekta, a cloud server, exposed data belonging to numerous healthcare organizations including Cancer Centers of Southwest Oklahoma, St. Charles Health System, Renown Health , Northwestern Memorial HealthCare, Carle Health, Lifespan Southcoast Health and Yale New Haven. Third-party vendor Elekta was responsible for the attacks.
4. Nearly 50,000 PHI records were accessed through an attack against a risk and compliance vendor.
Continuing to dominate the third-party breach headlines in June, another major healthcare breach potentially exposed the PHI of 47,034 BlueCross BlueShield of Kansas City patients. The breach that exposed names, birthdates, social security numbers and related medical information turned eyes to the compliance and risk vendor, LogicGate.
According to the statement issued by the vendor, an unauthorized party accessed Logic Gates Amazon Web Services-hosted cloud storage servers that stored customer backup files for its platform ‘Risk Cloud’. While it’s still unclear as to how it was compromised, the cyber criminals leveraged stolen credentials to infiltrate the database.
5. An eight-second breach impacted over 100 Amerigas employees.
AmeriGas reported a data breach that impacted 123 employees in mid June. The breach stemmed from J. Keller, a Department of Transportation (DoT) compliance vendor, was discovered after suspicious activity was detected regarding an email account belonging to its network.
The incident was then traced back to a phishing attack that an employee had fallen victim to. During the short breach window, the attacker was able to access emails with spreadsheet attachments containing AmeriGas’ employee information, which included Lab IDs, social security numbers, driver’s license numbers, and dates of birth.
Even before we had the chance to reflect on the lessons learned from supply chain attacks in June 2021, the largest ransomware attack ever recorded shook up the world as we knew it. On July 2nd, Kesaya servers were leveraged to distribute malicious software to thousands of servers across the globe. Discover more here.