MalasLocker Ransomware: Exploiting Zimbra Servers for Charity and its Global Impact
Written by Ferhat Dikbiyik
Additional Contributors Yavuz Han and Ekrem Celik
Edited by Haley Williams
In an alarming new development in the cyber threat landscape, a ransomware group dubbed MalasLocker has emerged with a unique modus operandi. This group is exploiting vulnerabilities in Zimbra Collaboration Suite (ZCS), a popular enterprise cloud-hosted collaboration software and email platform, and is demanding an unconventional "ransom" - donations to charity.
Instead of demanding payment directly to them, MalasLocker hackers are asking victims to donate to an approved non-profit charity. Despite their unusual philanthropic request, the hackers' actions remain malicious and harmful, as they steal sensitive data and encrypt files, causing significant disruption and potential data leakage.
While the notion of cybercrime with a 'charitable' facade may seem paradoxical, it adds another layer of complexity to the growing threat of ransomware attacks. In the following sections, we will delve into the intricacies of how MalasLocker exploits Zimbra vulnerabilities, the global impact of these attacks, and how Black Kite can help organizations manage the third-party cyber risk related to these issues.
How MalasLocker Operates
Unlike traditional ransomware groups who demand ransoms in cryptocurrency, MalasLocker operates on a unique and unconventional model. Once they successfully infiltrate a system, they encrypt the victim's data and demand a "donation" instead of a ransom. The donation must be given to a charity of the group's choice, a peculiar twist that has led some to dub them the "Robin Hood" of the cyber world.
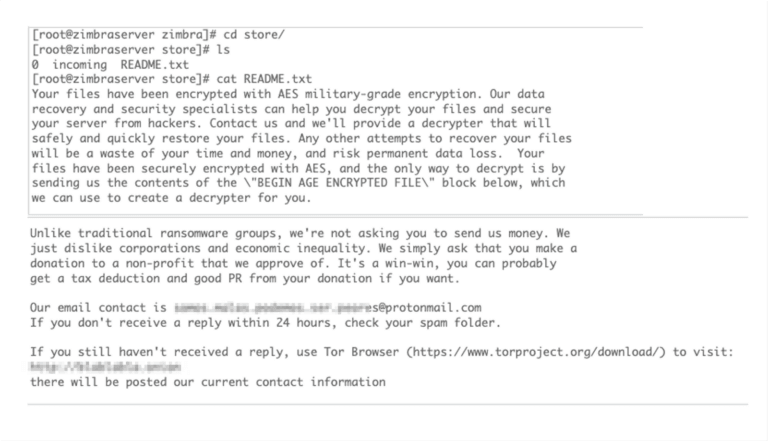
Upon successful infiltration and data encryption, the group leaves a ransom note on the victim's computer. This note contains detailed instructions on how to make the "donation" and provide the receipt to the group. The group assures victims that upon receipt of the donation proof, they will provide the decryption key to restore the locked files and not leak any stolen data. They also threaten that failing to make the donation within the stipulated time will result in data leakage and permanent loss of data access.
However, as an added complexity, the group does not directly specify a donation amount. Instead, they state that the donation amount is determined by the victim's financial capabilities and the sensitivity of the stolen data. This leaves victims in a state of uncertainty and potential negotiation with the group.
Despite their seemingly altruistic approach, MalasLocker's operations are still illegal. They intrude into private systems, encrypt data, and demand donations under duress. Furthermore, their actions put charities in difficult positions as they might unknowingly receive funds obtained through illicit activities.
Notably, by demanding "donations" rather than direct ransom payments, MalasLocker cleverly circumvents the typical complexities associated with cryptocurrency transactions. They avoid the process of laundering cryptocurrency, and there's less chance of law enforcement tracking them through crypto wallet connections. This modus operandi not only makes their operations more covert but also potentially more efficient.
Additionally, their choice of targeting certain countries and exempting others, as well as the act of demanding donations to certain charities, suggests a political motivation behind their activities. Although the group portrays themselves as cyber "Robin Hoods", their actions are illegal, unethical, and potentially politically charged. This unique approach raises many ethical and legal questions, underlining that MalasLocker is a significant cyber threat that organizations need to be vigilant about.
Exploiting Zimbra Server Vulnerabilities
The primary attack vector of the MalasLocker group is the exploitation of a significant vulnerability in Zimbra Collaboration Suite (ZCS), a widely-used enterprise cloud-hosted collaboration software and email platform. The primary vulnerability exploited by the group is CVE-2022-24682 [1], a flaw discovered in the Calendar feature of Zimbra Collaboration Suite. Versions 8.8.x before 8.8.15 patch 30 (update 1) are affected by this vulnerability [1].
This particular vulnerability allows an attacker to place HTML containing executable JavaScript inside element attributes, resulting in arbitrary markup being injected into the document. This flaw can be exploited to enable remote code execution, meaning a malicious actor can remotely control the ZCS server without having any authorized access. This vulnerability, first exploited in the wild in December 2021, was assigned a CVSS 3.x severity score of 6.1 (medium) [1].
Volexity, a cybersecurity firm, highlighted an operation titled "Operation EmailThief" in which this zero-day Cross-Site Scripting (XSS) vulnerability in Zimbra was actively exploited. The operation began with a series of targeted spear-phishing campaigns against organizations, eventually leading to the exploitation of the vulnerability in the Zimbra email platform. The attacker in these cases attempted to load JavaScript to steal user mail data and attachments, again emphasizing the potential damage such vulnerabilities can cause [2].
While CVE-2022-24682 is a focal point for MalasLocker, it's important to note that other vulnerabilities associated with ZCS have also been exploited by various threat actors [3]:
- CVE-2022-27924
- CVE-2022-27925 chained with CVE-2022-37042
- CVE-2022-30333
- CVE-2022-27926
CVE-2022-27926, for example, was notably exploited in attacks against NATO-aligned countries by the Russian hacking group Winter Vivern [4]. They used the flaw to launch a Cross-Site Request Forgery (CSRF) attack to steal Zimbra users' credentials and CSRF tokens.
Given these potential threats, CISA has issued a warning and a subsequent advisory regarding these vulnerabilities, urging all organizations to take the necessary measures to protect their systems [3]. With these vulnerabilities known and being actively exploited, organizations must ensure they are aware of the latest patches and security advisories from Zimbra and cybersecurity authorities.
Victims of MalasLocker Attacks and Companies at Risk
Since its emergence, MalasLocker has executed numerous successful attacks. Our research, conducted by Black Kite, has revealed the existence of this group and been tracking it since May 16th, 2023. As of our analysis, there are a total of 173 victims announced on the group's website. The geographic distribution and sectors of these victims provide us with valuable insights about the group's targeting preferences.
- Geographic Distribution: A large proportion of MalasLocker's victims are located in Europe, accounting for 43% of the total number. This includes 41 victims in Italy, 6 in Germany, 6 in Spain, 4 in Austria, 4 in the UK, and 3 in France. The rest are scattered across other European countries, with one or two victims per country. Unusually, this ransomware group has also targeted Russian companies, which account for 30% of the victims. Meanwhile, 11% of the victims are US companies.
- Industry Distribution: In terms of industry sectors, the majority of victims fall within Professional, Scientific, and Technical Services (41 victims), followed by Manufacturing (20 victims), Retail Trade (13 victims), and Information (13 victims). The industry sectors of the remaining 49 victims are currently being identified.
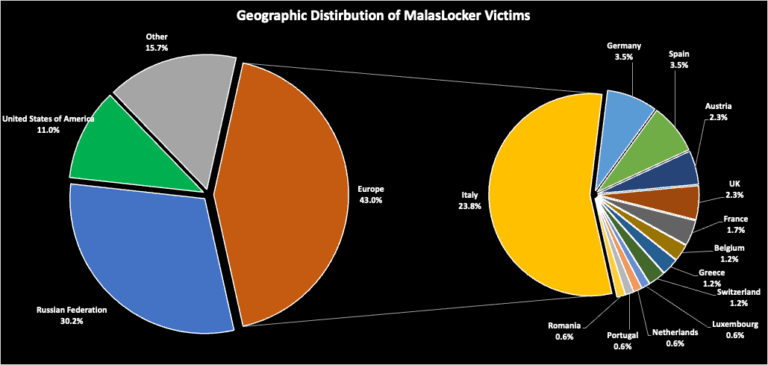
MalasLocker's unusual targeting of Russian companies, its large number of European victims, and its spread across multiple industry sectors suggest a varied and potentially politically-motivated attack strategy.
Adding to the tangible concern, several victims have reported encrypted emails on Zimbra Forums, underlining the real-world impact of this ransomware activity. However, the actual number of victims might be higher than reported due to a potential underreporting of incidents.
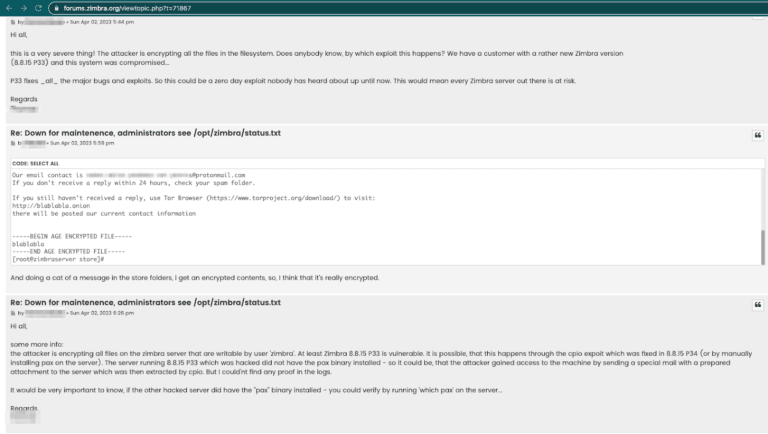
The data extracted from the Shodan search suggests that over 32,000 Zimbra Collaboration Suite servers could be vulnerable to the group's exploits. These servers are publicly discoverable and distributed among several countries: over 3,000 in the US, almost 3,000 in Germany, 2,600 in Russia, and 2.3K in France.
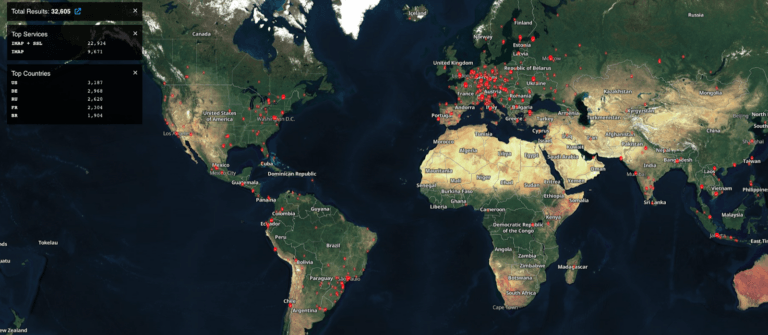
Interestingly, the distribution of these potentially vulnerable ZCS servers coincides with both the geographic distribution of MalasLocker's victims and the group's stated target countries in its manifesto. This alignment further highlights the potential risk to these companies and supports the need for urgent action to secure their systems.
The group's targeting choices and the potential risk to many other companies worldwide are indicative of its broader aims and should be considered when developing defensive strategies against this new threat. Black Kite is the first to make this analysis public, and we will continue to monitor MalasLocker's activities and targets.
Protecting Your Organization from MalasLocker
Given the potential for expansion of MalasLocker's activities and targets, it is crucial for organizations, particularly those using Zimbra Collaboration Suite, to take proactive steps to secure their systems. The following subsections provide recommended strategies to achieve this.
Importance of Upgrading Zimbra and Patching Vulnerabilities
As the group exploits known vulnerabilities in Zimbra Collaboration Suite, particularly CVE-2022-24682, the importance of keeping your software updated cannot be overstated.
- Ensure your Zimbra Collaboration Suite version is updated, and all available patches have been applied. Particularly if you are using a version prior to 8.8.15P30 Update 2, upgrading should be an immediate priority, as these versions contain the vulnerabilities MalasLocker exploits.
- Stay aware of new patches and updates from Zimbra. They should be applied as soon as they are available, thereby reducing the window of opportunity for an attacker to exploit vulnerabilities.
- Also, it is crucial to educate your staff about the threat posed by MalasLocker and emphasize the importance of promptly reporting any suspicious activities, such as unusual email behavior or requests for credential details.
Recommended Security Measures
Besides patching and upgrading Zimbra, other security measures are critical in fortifying your defenses against MalasLocker.
- Implement stringent access controls and enforce multi-factor authentication. This aids in thwarting unauthorized access to sensitive systems and data.
- Continuously monitor your network for any signs of intrusion or unusual activity. This allows you to identify and respond to a potential attack before substantial damage occurs.
- Invest in cybersecurity awareness training. Most cyberattacks, including those deployed by MalasLocker, involve elements of social engineering. Staff training to recognize these tactics forms a potent line of defense.
- Leverage tools like Black Kite's Ransomware Susceptibility Index™ to understand your organization's risk profile concerning ransomware attacks. This tool uses data and machine learning to predict the likelihood of an attack and provides guidance for your organization's security strategy.
- Have a solid incident response plan in place. Prompt and structured response in the event of an attack minimizes the extent of damage and aids faster recovery.
The threat posed by MalasLocker, albeit new, is significant, but with the right strategies and tools in place, your organization can substantially mitigate its risk of falling prey to this group.
Securing the Vendor Ecosystem from MalasLocker
The rise of MalasLocker, being a new and unorthodox ransomware group, has placed an even greater emphasis on the importance of third-party cyber risk management. Cybersecurity is no longer an isolated concern but a shared responsibility that extends across an organization's entire vendor ecosystem. In order to navigate this interconnected landscape effectively and mitigate the risks posed by threats like MalasLocker, organizations must adopt tools and methodologies that allow for efficient, focused, and proactive management of their cyber risks.
Utilizing Black Kite to Identify Vendors Potentially Exposed to MalasLocker
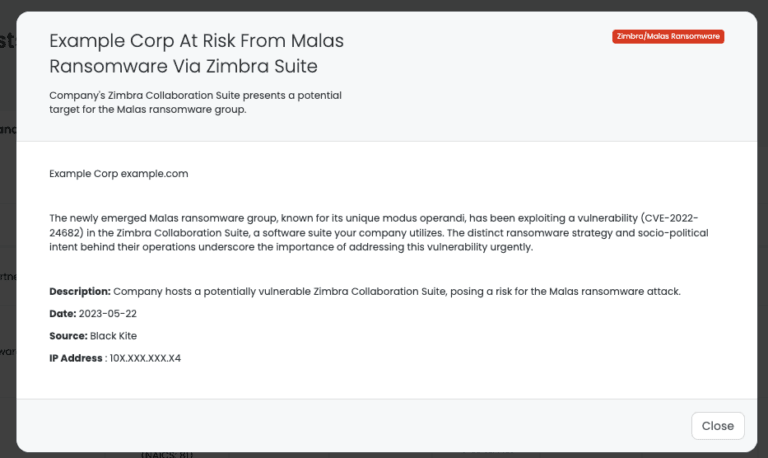
In response to the emergence of MalasLocker, Black Kite has proactively developed a unique solution, Focus Tags, to help organizations identify and manage their supply chain risks. These tags, created using Open Source Intelligence (OSINT) sources, automatically flag vendors that have publicly visible Zimbra Collaboration Suite (ZCS) servers, including those running versions susceptible to the CVE-2022-24682 vulnerability that MalasLocker exploits.
Identification of vendors utilizing ZCS is critical for assessing potential exposure to MalasLocker. With the Focus Tags feature, Black Kite provides organizations with a fast and efficient method of filtering and identifying such vendors within their vendor network.
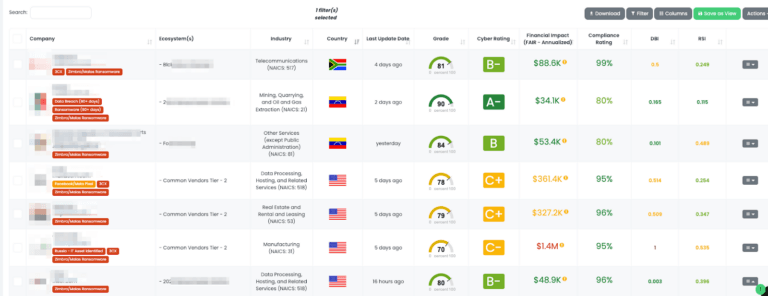
Within the Black Kite platform, organizations can conveniently filter their vendors based on these tags. This allows for quick identification of vendors that may be at risk from MalasLocker attacks. As these tags specifically highlight the use of vulnerable Zimbra versions, they provide valuable and actionable insights into an organization's vendor risk landscape in the context of this new and evolving ransomware threat.
With these unique insights, Black Kite is paving the way for organizations to proactively manage their supply chain risks. The platform allows them to concentrate their risk management efforts where they matter most, facilitating a swift and effective response to the rapidly evolving cyber threat landscape, particularly in relation to threats like MalasLocker.
Unveiling Black Kite’s Ransomware Susceptibility Index™ (RSI™)
In addition to its Focus Tags, Black Kite offers another unique tool for managing the risk of ransomware attacks: the Ransomware Susceptibility Index™ (RSI™). The RSI™ is the world's first and only tool of its kind, providing complete transparency into an organization's likelihood of experiencing a ransomware attack.
Understanding RSI™
The Black Kite RSI™ works by inspecting, transforming, and modeling data collected from a variety of OSINT sources, including internet wide scanners, hacker forums, and the deep/dark web. Through machine learning, it identifies correlations between control items to provide estimates of an organization's ransomware susceptibility. In other words, the RSI™ quantifies the risk of or susceptibility to a ransomware attack based on the organization's current cybersecurity controls and practices.
How RSI™ Helps Identify and Mitigate Ransomware Threats
By providing a quantitative measure of ransomware susceptibility, the Black Kite RSI™ allows organizations to prioritize their cybersecurity efforts and develop more informed risk management policies. This index can be particularly useful in the context of new and emerging threats like MalasLocker. Using the RSI™, an organization can quickly understand its likelihood of being targeted by MalasLocker and take appropriate remediation steps. Furthermore, the RSI™ can also guide an organization in managing its vendor risks, as it can identify which vendors are most prone to ransomware attacks.
Conclusion
The rise of MalasLocker highlights a new evolution in the world of ransomware, blending elements of hacktivist action with advanced techniques for exploiting Zimbra vulnerabilities. Its focus on publicizing stolen data, instead of traditional ransom demands, introduces an interesting twist to the threat landscape that organizations need to take seriously.
However, amidst this new and evolving threat, it's important for organizations to remember that they are not powerless. By keeping their systems patched and up-to-date, particularly Zimbra Collaboration Suite, they can significantly reduce their risk of falling victim to MalasLocker. Equally crucial is the role of third-party cyber risk management, which can help organizations identify and mitigate potential risks within their vendor network.
In this context, tools like Black Kite's Focus Tags and the Ransomware Susceptibility Index™ (RSI™) are invaluable assets for any organization. By providing actionable insights and quantifiable metrics, these tools enable organizations to understand their ransomware risks and prioritize their remediation efforts effectively.
The emergence of MalasLocker underlines the importance of vigilance and proactive risk management in today's dynamic threat landscape. By leveraging advanced tools and maintaining a focus on best-practice security measures, organizations can stay ahead of such threats and secure their operations against the evolving tactics of ransomware actors. In the face of an increasingly complex cyber landscape, knowledge remains our most powerful weapon.
Sources
- [1] https://nvd.nist.gov/vuln/detail/CVE-2022-24682
- [2] https://www.volexity.com/blog/2022/02/03/operation-emailthief-active-exploitation-of-zero-day-xss-vulnerability-in-zimbra/
- [3] https://www.cisa.gov/news-events/cybersecurity-advisories/aa22-228a
- [4] https://www.proofpoint.com/us/blog/threat-insight/exploitation-dish-best-served-cold-winter-vivern-uses-known-zimbra-vulnerability