How do you breach a company as big as SpaceX? Explore LockBit’s latest third-party attack
Written by Ferhat Dikbiyik
Edited by Haley Williams
On March 13, 2023, LockBit Ransomware group claimed to have breached a third party in the SpaceX supply chain, a manufacturing contractor in Texas. Through this gained access to this vendor, LockBit successfully (allegedly) seized 3,000 drawings/schematics certified by SpaceX engineers.
In the words of LockBit, they spoke directly to Elon Musk through this breach announcement, saying, "I would say we were lucky if SpaceX contractors were more talkative. But I think this material will find its buyer as soon as possible. Elon Musk, we will help you sell your drawings to other manufacturers – build the ship faster and fly away."
LockBit gave the vendor a week to pay the ransom, though it is typically recommended that companies refuse to pay any such ransom. This behavior aims to discourage ransomware actors from continuing in their quest to attack. However, the threat of leaking Musk and SpaceX proprietary blueprints and drawings to the general public in their best bet at receiving payment.
Why was LockBit so successful?
Currently, it is hard to assess how critical these drawings are for SpaceX, but it does communicate one blatant message: large organizations have gaps and weaknesses in their supply chain, allowing for groups such as this to target small, under-the-radar third parties as a means to attack and gain data on said companies.
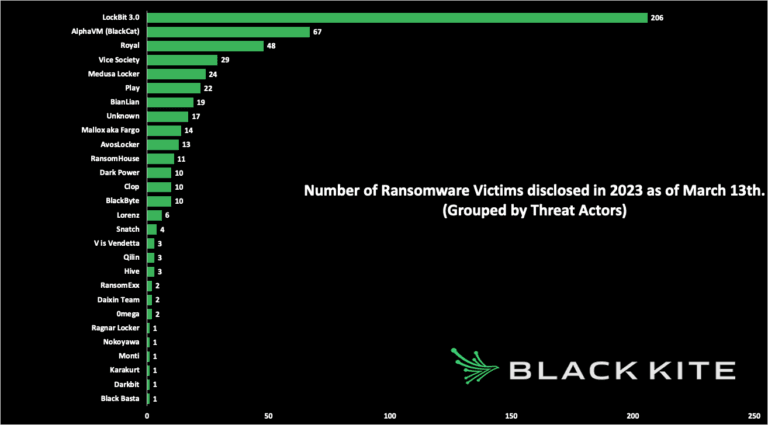
The Russia-based group (with some leaders claimed to be in the United States), LockBit is the current most prolific ransomware group in the world, accounting for 30% of ransomware attacks last year. They are notorious for their confidence, lofty targets, and high ransoms. And so far, LockBit is well ahead of all other ransomware groups in 2023. Almost 40% of ransomware victims announced so far were allegedly attacked by LockBit.
Manufacturing leads as a ransomware target
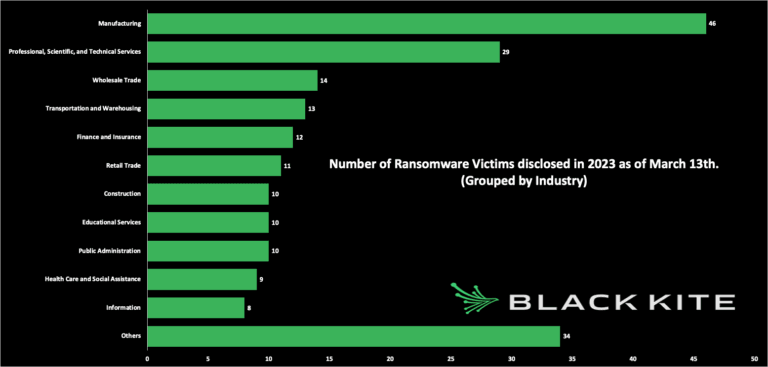
41% of LockBit’s victims are in the United States, and 22% are in the manufacturing industry. Lockbit, like some other ransomware groups, targets manufacturing companies to extort the company and gain any intellectual property information that the company possesses on behalf of its clients.
Often, ransomware groups target manufacturing knowing they have little to no capacity for downtime. These companies are more likely to quickly pay a ransom than suffer the effects of diminished reputation, business downtime, and lost revenue from halted production.
Additionally, many of the systems they rely on are outdated, older and unpatched, leaving seemingly unthreatening vulnerabilities out in the open for threat actors to exploit.
What should SpaceX expect going forward?
As a result of this attack, it is likely that an increase in related cyber scenarios could occur. LockBit may find new ways to exploit discovered vulnerabilities on outdated products that have not been patched.
Lockbit claims that the contractor has about 3,000 drawings certified by SpaceX engineers. Currently, it is hard to assess how critical these drawings are for SpaceX if they were to be sold or leaked.
Can we learn more about the breached vendor?
The vendor is a waterjet cutting, laser cutting & CNC machining service contractor in Irving, Texas.
According to their website, they are a full service, piece-part production and contract manufacturing facility, founded a little over 25 years ago. Their facility is equipped with the latest technology in CNC horizontal and vertical mills, multi-axis lathes, 5-axis waterjet, and laser systems.
The company’s digital presence is extremely small. They have a single website, with only three IP addresses. Linkedin shows only 12 employees work at the company (though some blue-collar workers might not be present on Linkedin) —most likely no dedicated security team.
Attacks of this nature reiterate the importance of monitoring third party risk
In any situation unfolding like this, it is easy for large companies like SpaceX to assume their supply chain and attack surface are good to go. But third parties, 4th parties, and nth parties along a vast digital supply chain add compounding threats to a seemingly secure company. You are only as safe as your weakest link.
Threat actors like LockBit will never spend their time trying to break into a fortress. They will target the small companies with unlocked doors and unpatched vulnerabilities. This is why monitoring your entire vendor ecosystem - not just the technology vendors or most critical vendors is so important.