Ransomware Attacks Against the Fortune 500: Lessons Learned from Accenture
Written by: Black Kite
Global consulting firm Accenture was hit by a ransomware attack earlier this month. Disclosed on August 11, the infamous ransomware group LockBit 2.0 allegedly stole over 6 terabytes of data. While details continue to emerge, negotiations continue and the threat actors are demanding a substantial $50 million in ransom to prevent further information from being released.
It is not a surprise why a Fortune 500 company such as Accenture entered cybercriminals’ radar. The company generated $44 billion in revenue last year, now employs over half a million people across the globe, and services 91 of the Global Fortune 100, as well as over 75% of the Fortune 500. In other words, they have a wealth of client data at stake.
Download our report for more on the Fortune 100 cyber risk landscape.
1. What do we know about the LockBit 2.0 ransomware group?
Beginning its operations in September 2019, Lockbit is a relatively new ransomware family that takes advantage of widely used protocols and tools including SMB and PowerShell. It recruits victims through encrypted device networks.
The Evolution of LockBit
LockBit 2.0 shows influences from Ryuk and Egregor through its code similarities. According to TrendMicro, using Winspool APIs to enumerate and print a document on connected printers and using Wake-on-LAN features inspired by Ryuk ransomware are two significant markers that draw comparison with Ryuk and Egregor.
The novel version of LockBit (2.0) ransomware has some nuances to its legacy version. Version 2.0 uses Active Directory (AD) group settings to automatically encrypt devices across Windows domains, making it one of the fastest ransomware variations on the market today. It’s one of the fastest and most efficient encryption algorithms available today.
Initial Access
The LockBit gang recruits associates and helpers, as described, to get initial access to a targeted corporate network. These individuals then undertake the actual intrusion on targets, usually using authentic remote desktop protocol (RDP) account credentials. To aid in the cause, LockBit’s authors supply a useful StealBit trojan variant, which is a tool for gaining access and automatically exfiltrating data, to their partners.
Leveraging a scanner tool, hackers get a detailed structure of the network, identifying domain controllers, enabling RDP ports, clearing event logs and disabling some servers and services such as Microsoft Exchange and MySQL.
Lateral Movement
The malware produces new group policies and delivers them to every device on the network once it has gained access to the domain controller. These policies disable Windows Defender and send the ransomware malware to every Windows machine. Each file is then encrypted with its extension, and then it slips a ransom letter into each encrypted directory, threatening double extortion by warning victims that their files are encrypted and may be publicly revealed if they do not pay up.
Business Model
The group is supposedly linked to Maze, and many of its members are believed to have moved on after Maze halted operations. Like its counterparts, LockBit 2.0 today operates as a ransomware as a service (RaaS), which is today’s hackers business model.
Instead of the many individual hackers present in the early 2000s, today’s hackers work together as an enterprise with affiliate partnerships. They contain their own unique skill sets, interconnecting to close the gap in the ransomware “killchain”.
2. How can a ransomware attack be prevented in the first place?
Given that this was a ransomware attack, we immediately inspected the Ransomware Susceptibility Index®, which yielded 0.65– above the critical threshold of 0.60. Also raising concern is the fact that Accenture is 25% more susceptible to ransomware than the industry average.

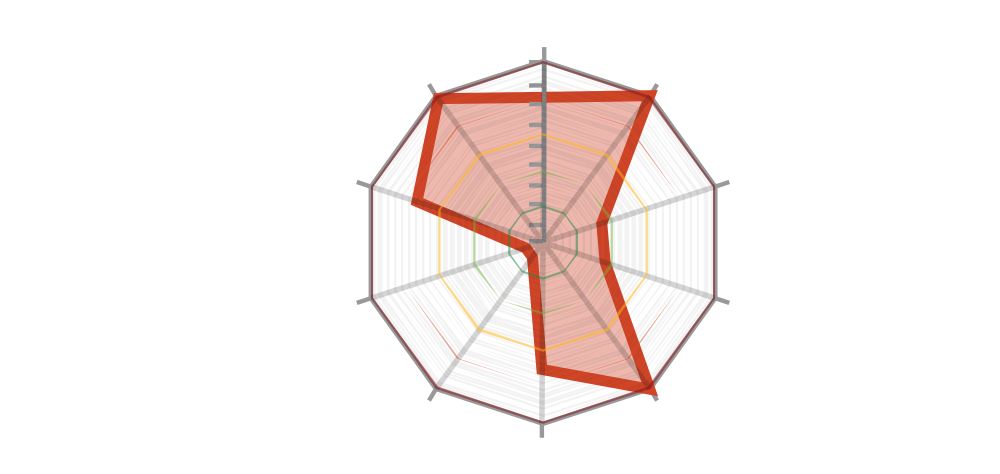
It’s important to note a low RSI™ score does not necessarily mean a company is immune to a ransomware attack. Cybercriminals, especially state-backed actors, may use zero-day vulnerabilities and craft sophisticated attacks, which a security automation tool may not detect or predict.
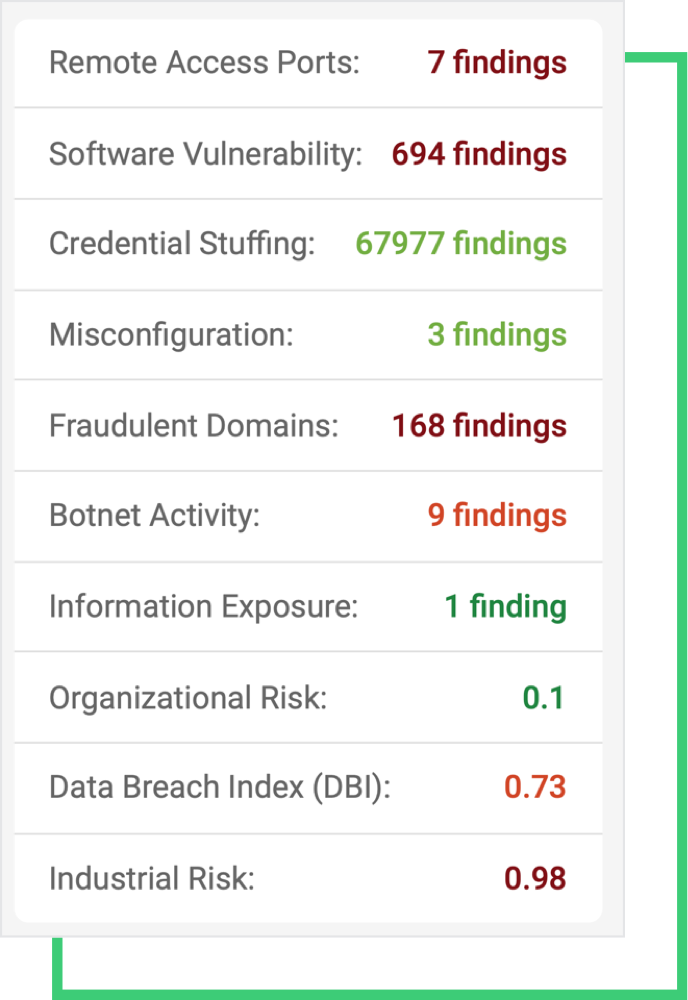
To combat this increasing complexity of related attacks, the platform also lists which indicators gave rise to the RSI™ are visible below. Some of the most critical findings come from Remote Access Ports, Software Vulnerabilities, and Fraudulent Domains parts.
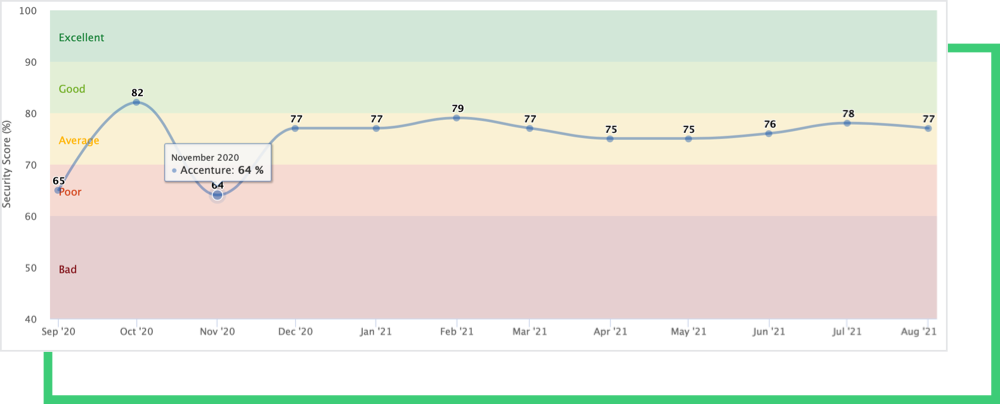
Missed Signals
The Black Kite platform has continuously monitored Accenture. Although the company consistently displayed an average cyber posture, the largest amount of security issues occurred towards the end of 2020.
Patch Management
Accenture received a “D” in patch management, which is a major problem among Fortune 100 companies. While the company is discrete about initial entry points, the breach window was probably wider than expected. It is of no surprise that a company with many out-of-date services can lure hackers, as they oftentimes indicate signs of flaws in risk and vulnerability management at an organization.

Application Security
The Black Kite platform discovered over 1,000 findings in Accenture’s Application Security category. Cross-site request forgery, cross-content mixing and plain-text transmission of sensitive information are among the alarming signals reflected in this category. Despite their low severity, the high number of findings should have constituted further investigation.
Credential Management
Whether leveraged as an initial entry point or used in lateral movement, leaked credentials play a major role in cyber attacks, and are the biggest concern among the Fortune 100. The majority of ransomware threat attactors use phishing or spear phishing as an initial entry to the target systems. Accenture received an “F” in credential management, with 373 leaks from the main domain alone.
3. How can we limit ransomware risk in the future?
According to an Accenture spokesperson, the attack was contained as soon as an irregular activity was detected on the network. Therefore, the affected set of servers remained limited. According to an internal memo released by CyberScoop:
“While the perpetrators were able to acquire certain documents that reference a small number of clients and certain work materials we had prepared for clients, none of the information is of a highly sensitive nature,” which makes the attack a third-party incident. The gang hacked into Accenture’s Industry X cloud platform to exfiltrate client data.
Although the initial entry point and several other details were kept from the public, there is one thing we are sure of: Human research and involvement remain absolutely critical to collecting preventive, detective intelligence and using it to support solid processes.
Understanding your risk landscape includes understanding the extent of your partner and supplier ecosystems, as well as their business and incident response capabilities. Addressing the entirety of your cyber risk posture from an n-th party standpoint is key to quickly identifying and reducing the potential impact of a cyberattack.
Additional Resources
- Download our Research: Fortune 100 Ransomware Risk, Revealed
- Read More: Growing Ransomware Risk on Third Parties
- Watch On-Demand: Reinventing the Ransomware Playbook

