New Year’s Resolutions for 2022: Cyber Risk Learnings
Written by: Black Kite
New headlines reached the papers and urgent updates were pushed for software across the globe, but in 2021, the overarching theme was consistency.
While the cyber risk landscape changes, the risks themselves remain similar to those from previous years, while of course, increasing exponentially. In 2021, the reported number of compromising events increased by 17%, which made it a record breaking year.
Takeaways here? Threats aren’t slowing down. It is better to be aware and take precautions than ride your luck and be forced to work backwards in worst case scenarios.
Ransomware remains at the top
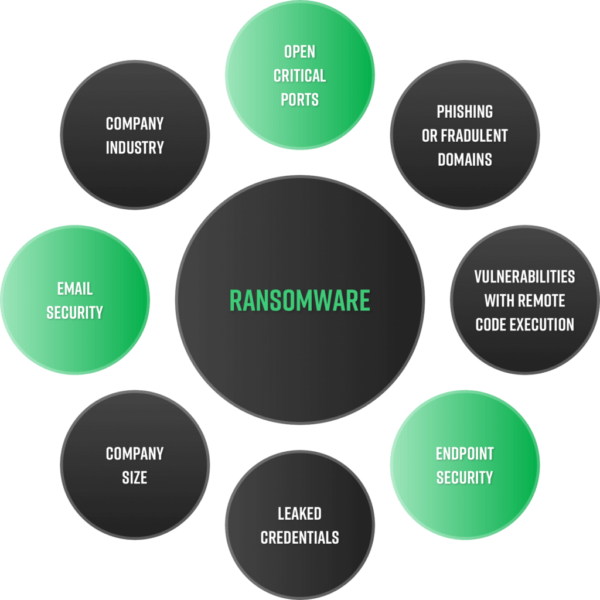
Of the record-breaking number of compromises throughout the year, ransomware is the main culprit and reason for those incidents. With the rise of RaaS and seasoned threat actors gaining intelligence, it has become successfully evolutionary as an operation. The US Treasury ties $5.2 billion in BitCoin transactions to ransomware payments and the average payment has gone up 82% to over $500,000 per transaction.
Though ransomware is not a new threat to the cybersecurity community, RaaS has introduced multifaceted extortion models, creating an extremely lucrative business model.
In a recent Black Kite research article, the team outlined steps you can take to address RaaS and ransomware for your own company, putting proactivity at the forefront of the focus.
There are three questions about RaaS that all CISOs must ask their internal team:
- Do we have a clear strategy for ransomware? If so, are we more likely to be proactive or reactive, given the current maturity level?
- Are we aware of the legal repercussions of a ransomware attack? Does my team have legal respondents in case of ransomware?
- Do we have the capacity/bandwidth to deal with a ransomware attack?
Taking into account the Kronos attack in December 2021, it is evident that ransomware creates a damaging domino effect for the community. Businesses are impacted at the core, but so are the people relying on those companies to get a paycheck into their hands. Having a lenient compliance checklist ultimately causes more work in the end.
Risk management guidelines have not changed
While it may seem daunting to prepare for a world where ransomware is part of our common language, the guidelines have actually been consistent through decades of risk management. In July of this year, CISA launched StopRansomware.gov to bring reports, alerts, and other resources all to one easy place.
The website is a great response to help educate the general public, however much of the information has been already circulating for more than a decade. Most cyber security professionals should already know these guidelines as well. The campaign provides guidance for addressing common ransomware attack vectors, but the compliance checklists aren’t built for the evolving cyber world we live in.
Cybersecurity does not end with you
Cybercriminals recognize the opportunity to target organizations with poor cyber posture to make their way into larger, more secure companies that hold confidential information and are willing to pay higher ransom amounts. If you solely monitor your own company without paying attention to everyone in your ecosystem, you are opening up hundreds of doors to gain access.
To make this a reality, consider every vendor as part of your core organization when going about vendor risk management.
“This year showed us that our perimeter is not only limited with our infrastructure but also includes our vendors’ environment. Cloud made vendors should not be viewed as an external supplier but be made a part of your business like an organizational unit,” commented Candan Bolukbas, CTO at Black Kite, “It emphasizes the shared responsibility model. We expect our vendors to be secure but we also need to verify with a non-intrusive scan or security rating like Black Kite. Trust but verify.”
48% of small and midsize businesses still rely on unsupported or approaching-end-of-support operating systems for their security needs. In most cases, once a system reaches end-of-life status, there are no more patches available, vastly increasing the threat landscape and leaving the organization wide open for an attack. Technically under most compliance frameworks, that organization can say they are patch compliant. So again, trust but verify.
Act now
Remember, compliance doesn’t equal security, and book smart doesn’t equal street smart. You must constantly monitor and adapt your security procedures to maintain the proper protection and start off strong for 2022.
This year, remember that managing third party risk matters. Be aware of your vast vendor ecosystem and use automated RSI your advantage as you determine the risk of each vendor.