
Cyber Risk Quantification
Translate Cyber Risk Into Financial Impact
Black Kite quantifies cyber risk in dollars—giving security, risk, and executive teams a shared language to prioritize smarter and act faster.

You Can’t Prioritize What You Can’t Price
Boards hear endless cyber briefings. What really resonates? "A breach with this vendor could cost us $30 million."
Without a common language to translate vendor exposures into business impact (the language of money), it’s nearly impossible to rally stakeholders around prioritizing actions.
Black Kite’s Cyber Risk Quantification (CRQ) solution changes the game. It turns abstract vendor risk into a clear business conversation.

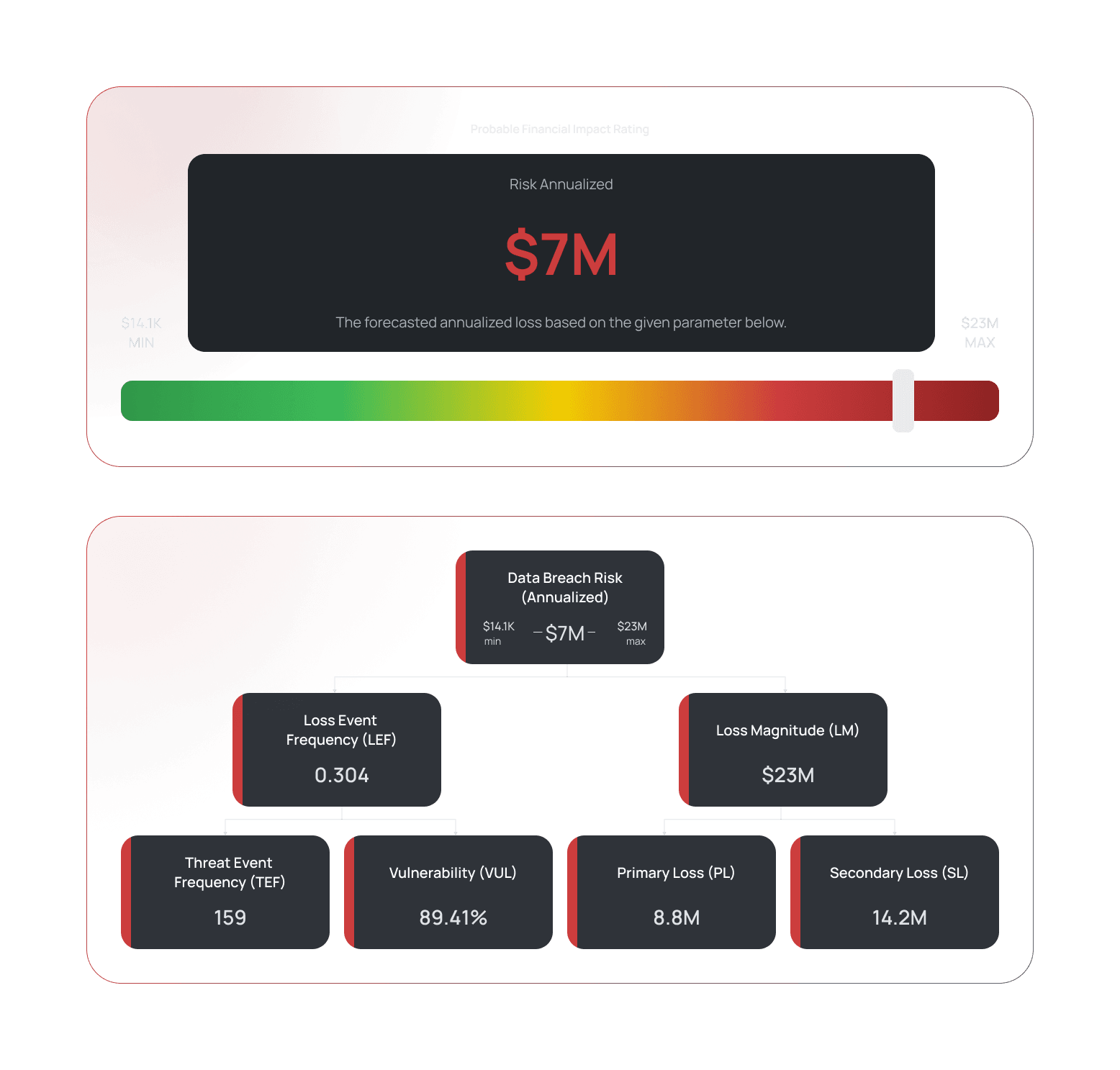
Measure Cyber Risk in Financial Terms
Black Kite was the first to give CISOs, CROs, and CFOs an automated tool that measures the probable financial impact of cyberattacks against your company, your vendors, your suppliers, or your trading partners to communicate risks in quantitative, easy-to-understand business terms.
Security understands the risk. Now finance and the board can too.
Based on Open FAIR™, the Gold Standard
Open FAIR™ (Factor Analysis of Information Risk) is the only international standard Value at Risk (VaR) model for cybersecurity and operational risk. Black Kite uses Open FAIR risk methodology to give you the real cost of a breach, adding business-critical context to a technical score. This means you see the impact on your bottom line.

What Can You Quantify? Real-World Scenarios.
Black Kite quantifies the dollars at stake for the scenarios that keep you up at night:

Why Financial Impact Changes the Conversation

Black Kite Welcomes Jack Jones, Originator of FAIR™, as Strategic Advisor to Deliver on its Strategic Vision to Improve the Health and Safety of the World’s Cyber Ecosystem

Black Kite Announces First Ever Automated Cyber Risk Quantification Capabilities for Ransomware and Business Interruption Scenarios

Think Like a Hacker for Successful Third-Party Risk Management (TPRM)
Show the True Cost of Cyber Risk
Posture scores aren’t enough. Quantify cyber risk in dollars, align your executive team, and defend security investments with board-ready data.