FBI Issues Ransomware Warning for Mergers and Acquisitions
Written by: Black Kite
The more a company has at stake, the more attractive it becomes to cyber criminals. The FBI recently issued a Private Industry Notification (PIN) warning companies of the malicious intent to diminish company value if ransom demands are not met. Mergers and acquisitions that are under time-sensitive financial pressure seem to have become the latest goldmine for ransomware operators.
Significant Financial Events Become the Common Denominator Among Top Ransomware Targets
Ransomware gangs intend to put pressure on firms by threatening to expose information. Their overall goal is to have a negative impact on their stock price, allowing traders to profit from the stock price decline. This technique is a novel strategy in the world of cybercrime, as it presents an indirect threat to hacked organizations that fail to pay the ransom demand. Negative press severe enough to affect stock exchange listings may persuade some victims to pay the demanded payment.
The foundations of this ransomware extortion technique were initially laid by REVil last year, who made the call for its affiliates to copy all information before encryption. According to the FBI, “ransomware actors are targeting companies involved in significant, time-sensitive financial events to incentivize ransom payment by these victims.”
Evidence of ransomware groups leveraging significant financial events to extort its victims include:
- Early 2020: A cyber criminal with an “unknown” moniker encouraged the hacker community to leverage the stock exchange during extortion. Then, in March, threatened to exploit stock information if the company did not pay its ransom.
- March – July 2020: Three companies involved in mergers and acquisitions became ransomware victims during the negotiation period.
- November 2020: Technical analysis of Pyxie RA remote trojan revealed concerning research. Hackers were searching for keywords such as “NASDAQ”, “Marketwired” and “newswire” during an attack
- April 2021: Darkside ransomware actors issued a statement on their blog indicating the intent to adversely affect stock price.
One of the most infamous examples of this extortion method, however, dates back to 2014 with the attack against Starwood Hotels. The breach went unnoticed until it was officially acquired by Mariott in 2016. It wasn’t until 2018 that the aftermath finally came to light—four years after the initial breach.
500 million people were affected by the Marriot breach. Financially, the company was fined over $25 million by the Information Commissioner’s Office (ICO) 2020. Marriott’s stock price immediately fell 5%.
Why its security systems failed to detect a breach until four years after it started still remains unanswered. More importantly, why did an acquisition like this miss such a compromise? Were the due diligence efforts on cybersecurity insufficient?
Time is Money: Why Nasdaq Cybersecurity Due Diligence is Critical During M&As
Today, cybersecurity plays a larger part in mergers and acquisitions. Several acquiring firms have experienced significant losses as a result of discovering the target company’s previous data breaches only after the final deal activities were completed. As a result, they’ve faced hefty financial sanctions and a decrease in the target company’s total purchase value.
The cybersecurity due diligence process should be at the forefront of any M&A decision. Because a technical cyber rating does not necessarily reflect the posture of the company, cybersecurity due diligence for M&As should always be a priority. The goal is for the purchaser to uncover the target organization’s cybersecurity controls and potential risk areas.
The purpose here is to gather information about potential security flaws in networks and supply chains so that they can be corrected before being exploited by cyber criminals. Cyber due diligence can also assist businesses in better managing third-party partnerships by allowing them to evaluate their providers’ cybersecurity posture, avoid fines, and develop more thorough compliance strategies.
The cybersecurity community is now used to new threats and extortion models of these gangs. Luckily, as information about these criminal groups emerges, it’s shared by law enforcement and immediately circulated via news channels and on social media.
With all this information and new intelligence, the Black Kite Research Team especially urges companies traded on NASDAQ to take necessary actions to be proactive and understand their current cybersecurity posture from a hacker’s perspective.
The Current Cybersecurity Posture of NASDAQ 100 Companies
The Black Kite Research Team completed a thorough risk assessment to get a pulse on the NASDAQ community and discover key security vulnerabilities. On the surface, the technical grade of the top 100 NASDAQ companies is a C+, or “average”.
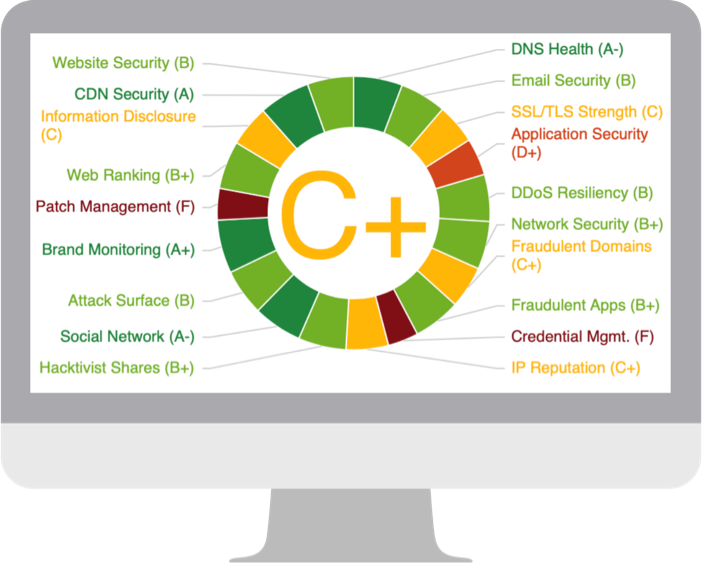
The cybersecurity posture is like a showcase of the company to the outside world. The more problematic it gets, the more luring it becomes to hackers. Despite the surface rating, serious weaknesses in Application Security (D+), Patch Management (F), and Credential Management (F) become even more critical as phishing emails and leaked credentials are among the preferred ransomware entry points. Other key ransomware indicators found among NASDAQ companies include:
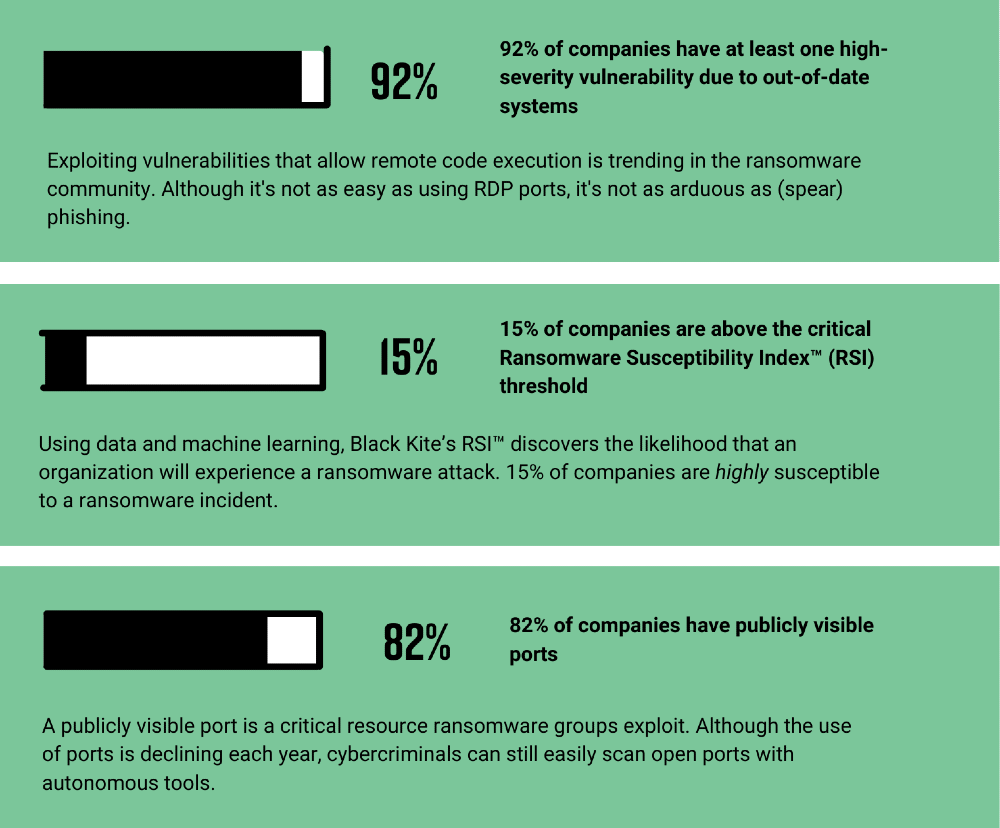
The Ransomware Susceptibility Index® collects data from various open-source intelligence (OSINT) sources including internet-wide scanners, hacker forums, the deep/dark web, and more to determine how susceptible a company and its third parties are to a ransomware attack.
Free RSITM RatingFBI Recommendations for Ransomware Protection
Although the sensitivity of the data at risk may pressure organizations to pay the ransom, the FBI strongly urges companies to avoid meeting criminals’ demands. Instead, companies are urged to take proactive steps to protects itself against ransomware:
- Back-up sensitive and confidential data offline on the Cloud, on an external hard drive, or another storage device. Make sure these backups are secure and data on the system is not available for change or deletion.
- Regularly update anti-virus and anti-malware software on all hosts. Out-of-date systems are a prime gateway for malicious activity.
- Use two-factor authentication for user login credentials and replace email with authenticator apps. Actors may have access to victim email accounts, and don’t open unsolicited attachments or click on links in emails.
- Enable least privilege for file, directory, and network sharing permissions.
Stay up to date on the latest ransomware attacks and news with our news feed powered by RansomwareReport.com.

