Defend Cybersecurity Investment Amidst an Economic Downturn
Written by: Black Kite
By Haley Williams, from the perspective of Jeffrey Wheatman, Cyber Risk Evangelist
In economic moments similar to what we are experiencing right now, defending investment is imperative for remaining cyber secure and prioritizing risk level maintenance. This is the defense of investment, not budget.
Business Objectives May Be Shifting
During an economic downturn, with limiting budgets and inflation at an all-time high, it is natural for business objectives to shift and change to match the environment.
However, the last thing a company should do is cut cybersecurity budget. Why? Opening up the company to vendor risk and ransomware risk by halting programs increases the likelihood of an attack; a ripple effect resulting in lost business and financial burden.
Justify the Value of a Security Program
In order to keep security programs active, it is important to connect the actions and investments by the security team back to the business objectives and goals of the company.
For example, if you are told to cut 20% of the security budget, you can present to management a report that details the change in risk level. This could be an avenue for setting up an evaluation schedule on a quarterly cadence rather than a monthly cadence, adding a level of exposure there. Keeping some level of active monitoring and risk management is key to ensure cyber health does not drastically shift to the negative.
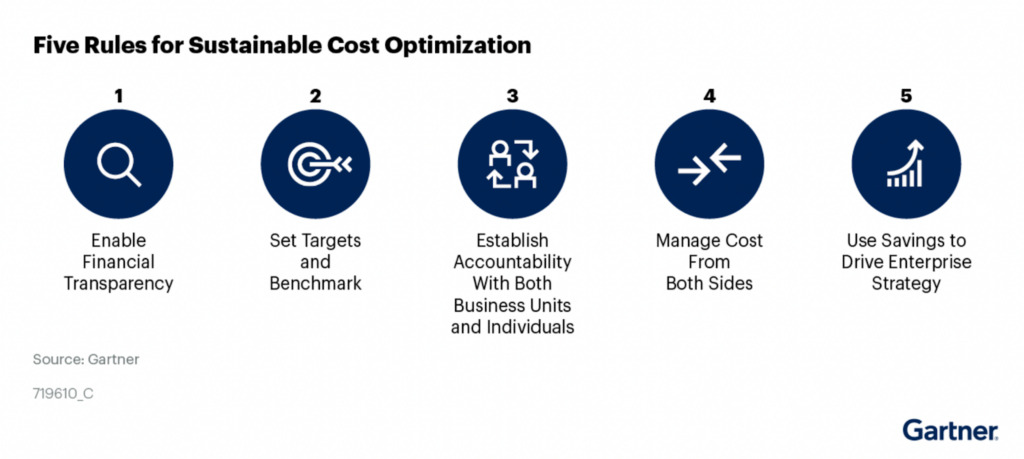
Another method of communication is to build out stories around control implementations directly connected back to business goals.
For example, if an organization has intellectual property, quantifying the business impact of losing that property to industrial espionage can contextualize the risk. This contextualization may come in the form of quantified risk, using Open FAIR™ with Black Kite, or business lost if one week was sacrificed to retrieve the intellectual property.
Presenting a thorough explanation to management displays that while the economy is tough, cutting budget creates additional exposure from a business impact perspective. This allows management to weigh the risks of cutting budget before actually doing so, and be comfortable with the additional exposure they are taking on.
Allowing management to move forward (or not) based on metrics and risk levels keeps the fear tactic to a minimum, and helps contextualize the data at hand. While of course we know that saying “bad things could happen!” as an explanation is true, it is not always the most effective tactic.
Is it worse to risk losing intellectual property and competitive advantage in the market, while cutting 10% out of the budget? Present the data and let management make the call.
Common Budget-Cutting Compromises
More often than not after the presentation of data, budget-cutting will still happen. This may lead to compromised security measures.
For instance, a company cannot fully halt patching practices. However, a 14-day patching cadence may be transitioned into a 30-day patching cadence, saving XX amount of budget, while increasing incremental risk by a small amount.
To create these compromises, you must build narratives that connect controls to business goals or metrics. One example of a narrative sequence might look something like this: Implementation of Control -> Keeps XX Data Secure -> Allows for Zero Business Interruption -> Prevents Reputation Loss
This is a much stronger argument than approaching management with: “this data has to be encrypted because the data needs to be encrypted.”
New Regulations Encourage Retainment of Budget
New rules proposed by the U.S. Securities and Exchange Commission (SEC) would force an immediate disclosure of major cyberattacks. This could drive a dramatic improvement in security posture for U.S. based companies, according to cyber industry executives in conjunction with VentureBeat.
“The proposed SEC rules include a requirement for publicly traded companies to disclose details on a ‘material cybersecurity incident’ — such as a serious data breach, ransomware attack, data theft or accidental exposure of sensitive data — in a public filing. And under the proposed rule, the disclosure would need to be made within just four business days of the company determining that the incident was ‘material,’” according to the SEC and VentureBeat.
You Will Never Have All the Budget in the World
While in an ideal world you could throw millions of dollars at cyber security controls and practices, that will never be realistic and would not be a good business decision, even in the best of boom times. There will always be decisions your company makes while sacrificing a good measure in exchange.
But being able to quantify and determine how each control meets (or doesn’t meet) a business goal allows these decisions to be made in good conscience, and with informed, educated perspectives.

The first step is making sure you have a system in place that allows you to see and conceptualize the data into something presentable, as well as monitor the full scope of vendors in your ecosystem. The Black Kite team would love to show you how we can be your partner in third-party risk intelligence.
With our model, you can monitor every vendor in your supply chain, continuously with no added cost to do so. We are built to scale with you, easily and simply.
Set Up A Free Demo