CLOP Ransomware Gang Reemerges to Claim 21 New Victims
Written by: ceren
Written by Gokcen Tapkan
Additional Contributor Yavuz Han
Edited by Haley Williams
In the last few months, the Clop ransomware gang resurfaced after a four-month silence between November 2021 and February 2022. This hiatus followed a take down of their entire organization in November. Clop posted 21 new victims to their data leak website in just the month of April, signaling an unexpected uptick in activity.
Black Kite Research analyzed 20 of the 21 victims and found that the vulnerabilities (still) present within their cyber ecosystems, allowed Clop to gain initial access.
Key Findings in the Research
- 20 of the 21 victims have been analyzed in depth
- 40% of the Clop victims are in the IT/Tech industry
- 30% of the Clop victims are in the Manufacturing industry, aligning with Black Kite’s generalized ransomware study
- 80% of the victims are U.S. based
- The victims have an average RSI™ of 0.45
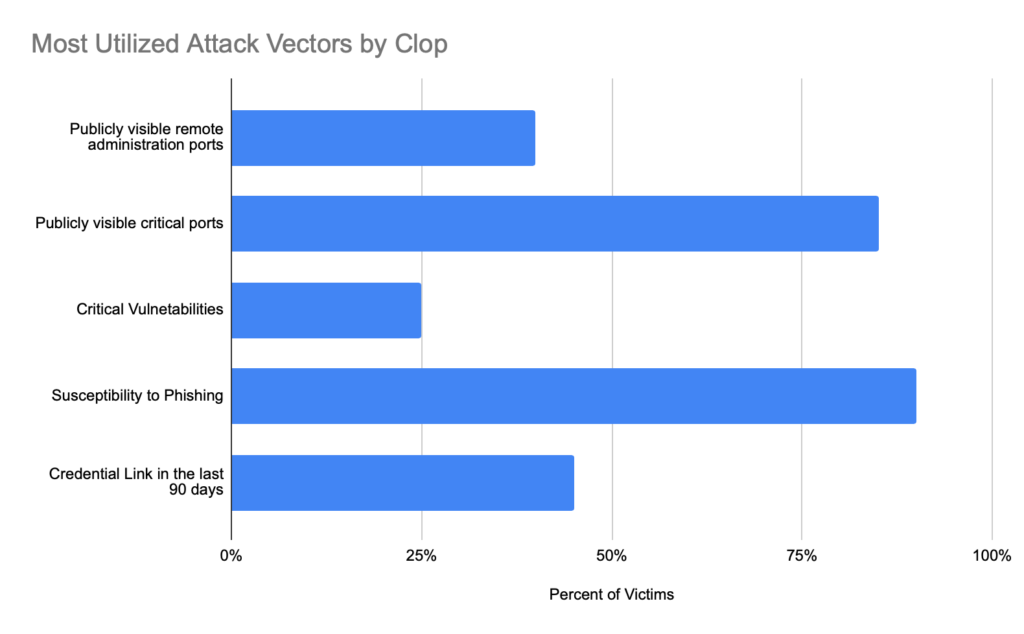
- 90% of the Clop victims have susceptibility to phishing, a vulnerability Clop utilizes often as an initial attack vector
- 80% of the Clop victims have open critical ports and 40% have open remote admin ports – another common Clop attack vector
- 45% of the victims have leaked credentials in the last 90 days
- 25% of the victims have critical vulnerabilities due to out-of-date systems
Research and Intelligence On Clop Victims
Clop posted the 21 victims on their site, and Black Kite instantly scanned each of them. This analysis, by Black Kite Research, is an in-depth look into the 20 victims by country and industry.
Clop Victims by Industry
Although we are aware that Clop operations are not representative of the entire ransomware landscape, there are some common patterns that tell a larger story – industry being one of them.
Our study reveals that 40% of the victims are in the technology domain, with almost half of them providing IT support services to other firms. This setup allows for easier access for supply chain attacks.
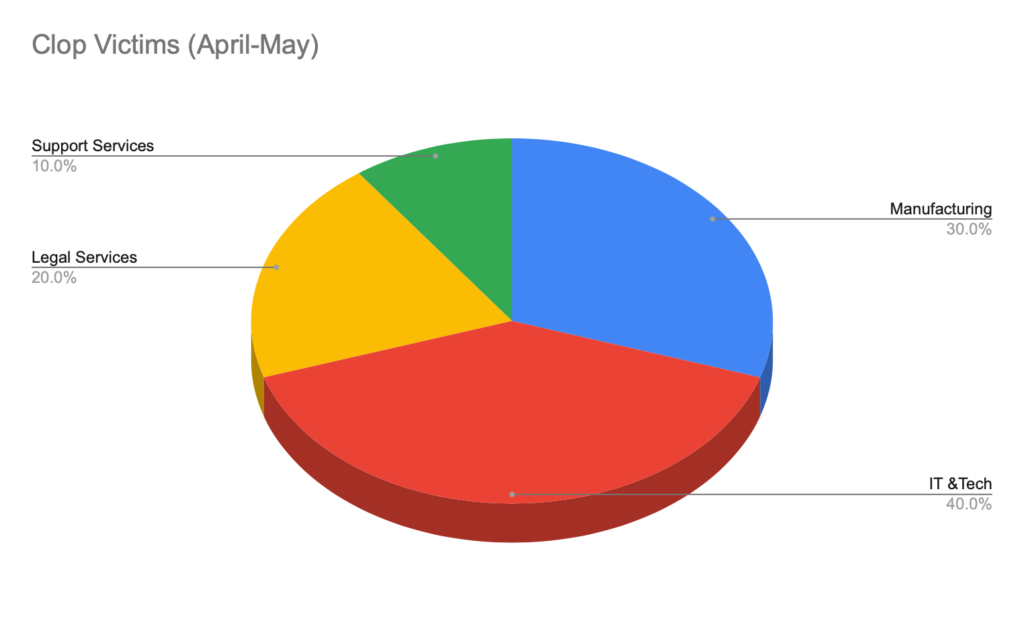
The remaining breakdown includes 30% in the manufacturing industry, 20% in legal services and 10% in support services – Mostly small businesses with newer cyber security programs.
The top two industries of Clop victims, Manufacturing and IT/Tech, are in line with the findings in our generalized ransomware study.
Clop Victims by Country
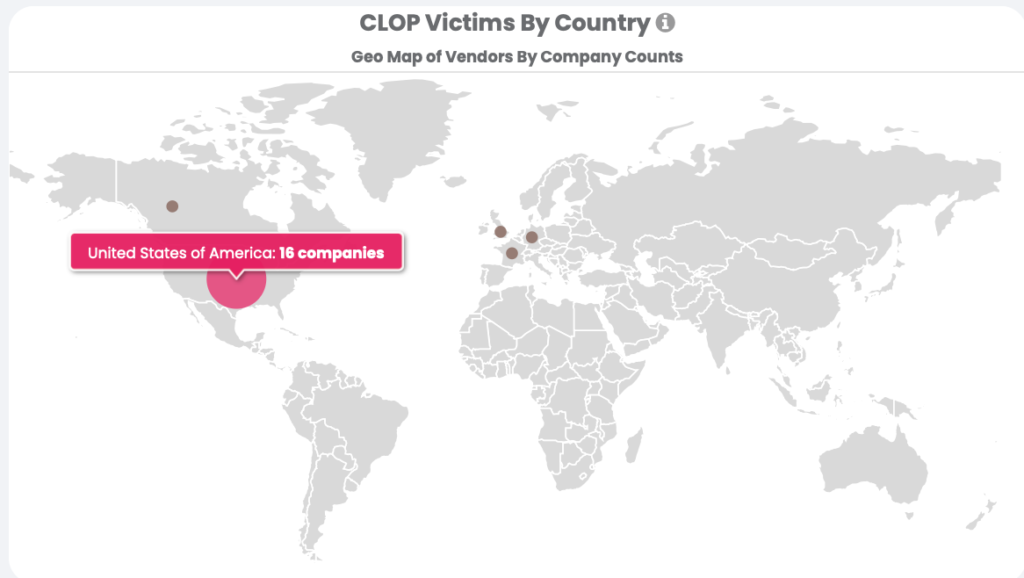
Again, 80% of their victims are based in the U.S., perfectly aligning with the findings in our RSI™ report.
Ransomware Susceptibility Index® and Common Clop Attack Vectors
Black Kite’s Ransomware Susceptibility Index® (RSI™), a tool that uses data and machine learning to provide the likelihood an organization will experience a ransomware attack, is consistently updated with ransomware incident data, drawn from our database, to further enhance the accuracy of our findings.
Black Kite scanned Clop victims the moment disclosures were made on the gang’s site. Given the instant scanning of the victims and the tight window between the attack date and disclosure date, we believe that the RSI™ ratings have a high confidence level with respect to timeliness. With that being said, Clop victims have an average RSI™ rating of 0.45, which is much higher than our control groups.
The companies in our control group had a high cyber security posture and had not experienced a ransomware attack in the past (as far as disclosures are concerned).
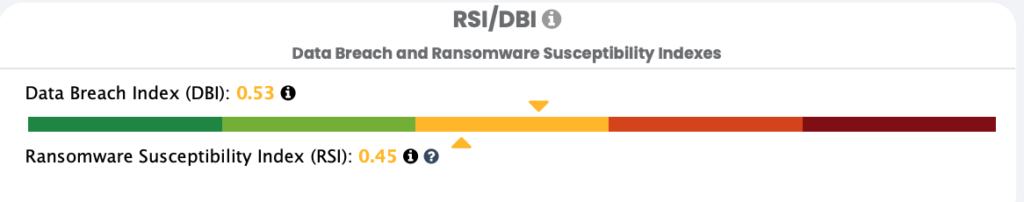
60% of Clop victims are above an RSI™ of 0.40, getting close to the critical RSI™ threshold level of 0.60, a significant indicator of being prone to a ransomware attack.
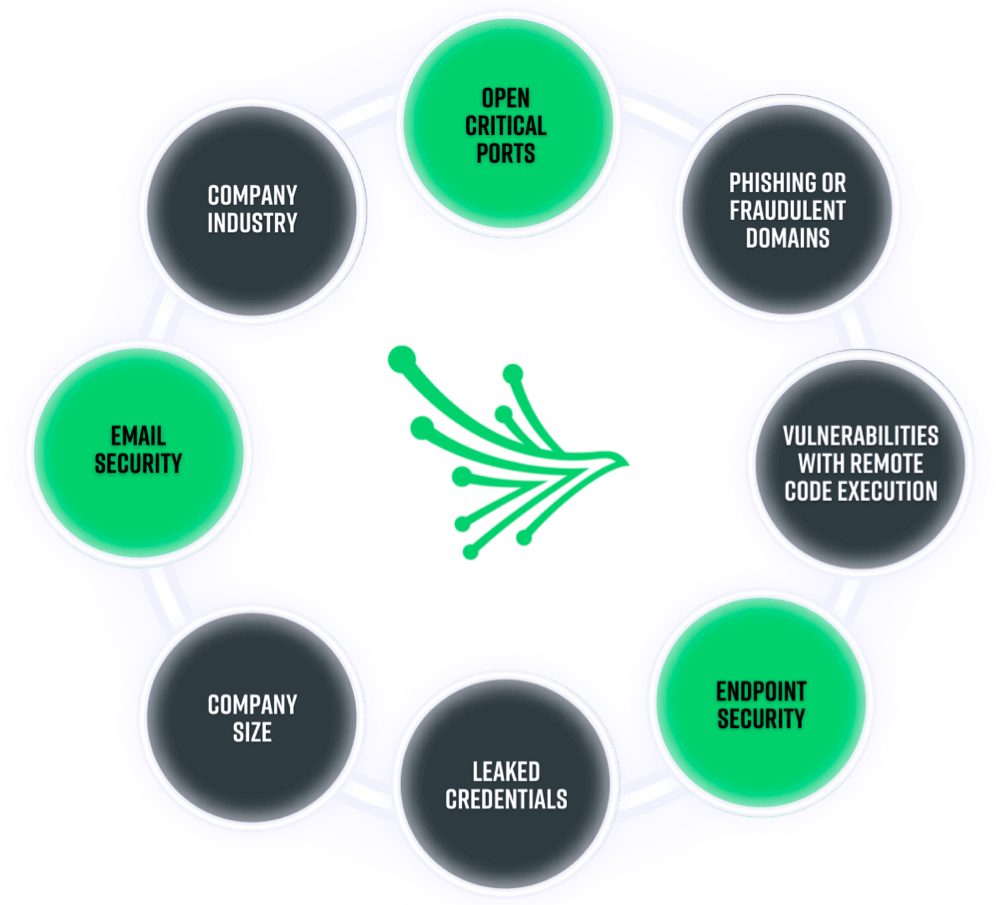
As we analyzed specific attack vectors that Clop presumably relies on, we discovered that the victims are highly (about 90%) susceptible to phishing. Clop often utilizes phishing scams as an initial attack vector along with leaked credentials. 45% of victims have leaked credentials on the dark web. 80% of the victims have open critical ports and 40% have open remote admin ports. 25% of the victims have vulnerabilities that are of critical severity.
Other Cybersecurity Indicators
Along with the ransomware indicators, the victims have other major issues with regards to their cybersecurity posture. Although these are not as frequently used by threat actors as the ransomware indicators above, they are often linked to “low cybersecurity posture” and hence make organizations fall to the attack of cybercriminals.
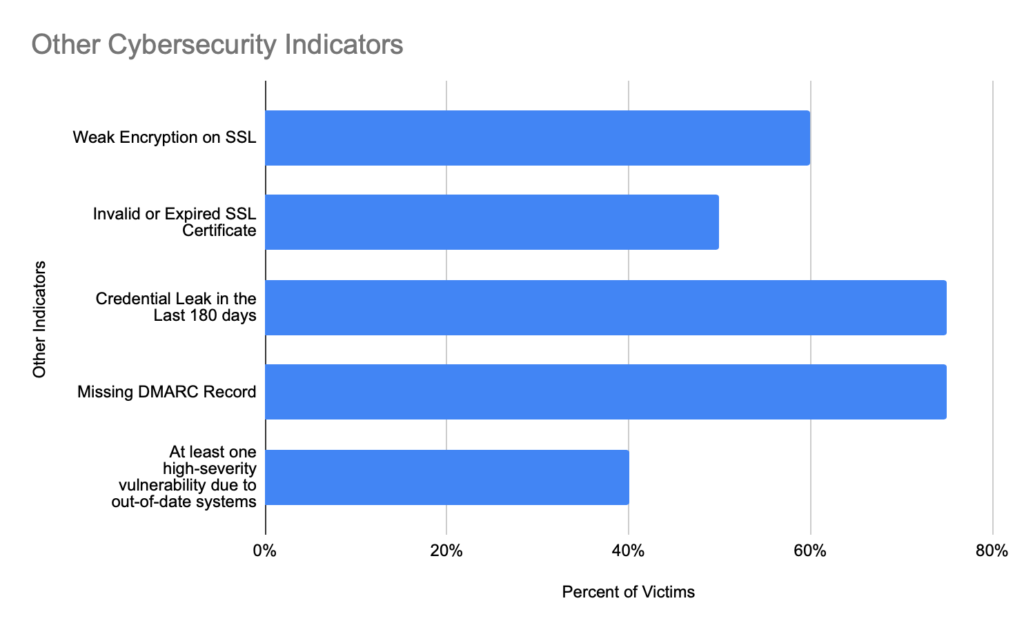
These indicators of a vulnerable organization include: Credential leaks either on the dark web or surface web in the last 180 days, weak encryption on SSL, missing DMARC records and unpatched high-severity vulnerabilities.
High volume of leaked data and information
Clop ransomware gang published sensitive files online belonging to the victims. Due to this, these companies are labeled with “Data Breach” on the Black Kite platform using focus tags.
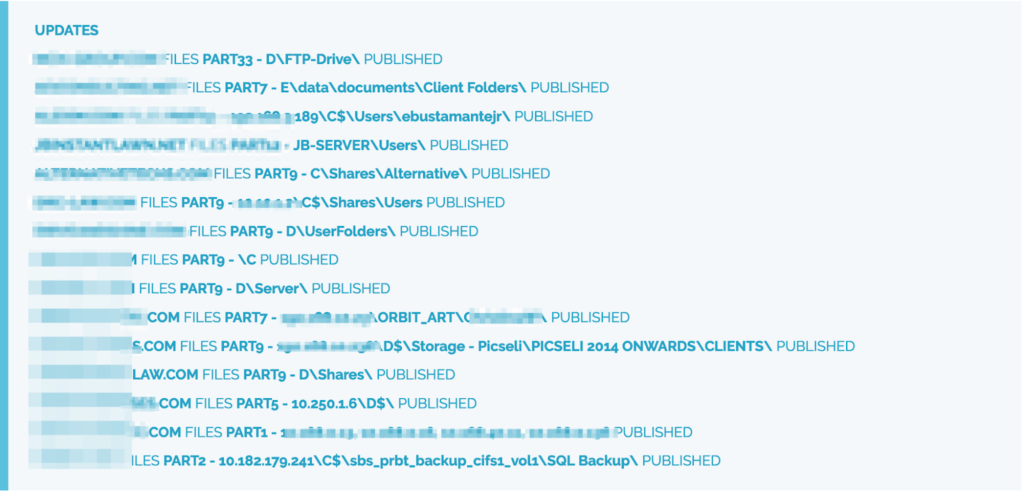

There are theories on such a high level of leaked data. One theory is that not all victims were the result of recent attacks, but actually older attacks that are only now being made public. This is a sign that threat actors could be halting operations altogether just like Clop. The gang has effectively ended its activity by destroying its infrastructure and notifying its team leaders that the group no longer exists.
History and Further Background on Clop Ransomware Itself
Clop Ransomware, a member of the popular Cryptomix ransomware family, is a dangerous file-encrypting virus. It deliberately avoids protection measures and encrypts saved files by planting an extension of the clop.
It also uses an AES cipher to encrypt images, videos, audio, databases, and papers, or attach .CLIP or .CLOP file extensions, preventing victims from accessing personal information. For example, “sample.jpg” gets renamed to “sample.jpg.Clop”. The victims are made to pay the ransom within a particular time limit in exchange for the supposed recovery of their data.
Clop ransomware is one of the most dangerous computer viruses because it creates entries in the Windows Registry and can start or stop processes in a Windows domain, keeping it hidden from antivirus software and users.
How Can You Be Proactive Against Ransomware?
While ransomware attacks appear overwhelming, organizations can take proactive steps to decrease their attack surface and minimize their susceptibility to attacks. Knowing your ransomware risk exposure is the first step in preparing for possible attacks.
Companies should always take advantage of the lessons learned from previous incidents, particularly that no vendor is flawless or without vulnerability, even the largest and most important. Continuous monitoring for vulnerabilities and timely patches are key to managing vendor risk and ransomware risk.
Companies need to arrive at a place of cyber resilience, where they can quickly adjust to tomorrow’s issues and today’s threats. Together we must adjust our posture and be prepared to respond to and recover from the unknown as threat actors’ moves become more difficult to foresee.
Embrace adaptability and continuous learning
