Cisco Confirms Attack by Ransomware Gang: How Is the Supply Chain Affected?
Written by: ceren
Written by Ferhat Dikbiyik
Additional Contributors Ekrem Celik and Gizem Toprak
Edited by Haley Williams
Cisco disclosed a security breach on August 10, 2022, an attack executed by the Yanluowang ransomware gang. Cisco confirmed that the infamous threat actor breached its corporate network in late May and that the actor tried to extort them under the threat of leaking 2.8GB of stolen files online. While the company also stated that the attackers could only harvest and steal non-sensitive data, the threat actor published NDA files allegedly stolen from the company. Since Cisco products are widely used by many organizations worldwide, there are concerns about this breach’s impact on the global supply chain.

What Happened?
The investigation conducted by Cisco Security Incident Response (CSIRT) and Cisco Talos revealed that threat actors compromised a Cisco employee’s credentials after they gained control of a personal Google account. Within that account, credentials had been saved in the victim’s browser and synchronized. Threat actors may have invested time and money to link a personal account to the victim’s company.
Threat actors used voice phishing (vishing) attacks to bypass the MFA protection to obtain access to the VPN with stolen credentials.
The Yanluowang ransomware group then attempted to extort the company. The gang published a list of files stolen from the company threatening to leak all stolen data if Cisco would not pay the ransom. While the group is famous for its triple extortion (data encryption, leaking data, and DDoS attacks), they only threatened the victim by leaking the data. Cisco’s security operations teams could have noticed the abnormal behavior before the group took any further action from their usual process.
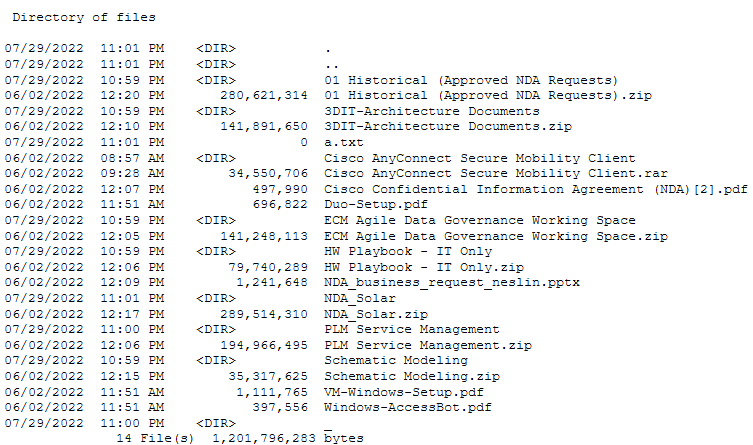
While the Yanluowang gang took credit for the attack, Cisco said it had moderate/high confidence that an initial access broker launched the initial attack with ties to other groups, including the UNC2447 cyber crime gang and the Lapsus$ threat actor group.
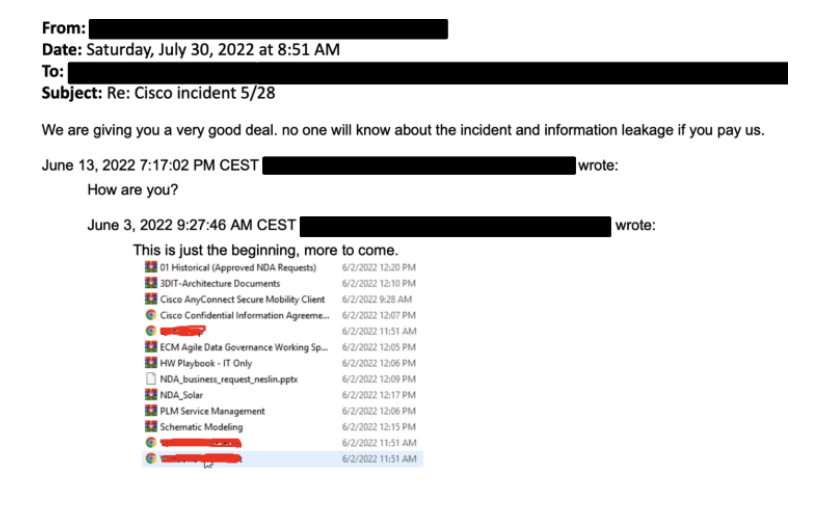
Cisco noted that after kicking the threat actors out of the network, the bad actors emailed Cisco executives. They did not make threats or extortion demands but instead shared a screenshot showing the directory listing of the Box data that was previously exfiltrated.
Cisco Talos published the results of their investigation with TTPs of the attack and MITRE ATT&CK mapping.
Black Kite Research on Cisco
Cisco, a continuously monitored vendor in the Black Kite platform, has a grade of C-, an average grade common in large global organizations. Cisco products are widely used across the digital supply chain, suggesting a potential cascading risk effect on their partners/customers. While there is no evidence that the threat actors have sensitive information on Cisco clients, the leaked data might be used to execute phishing attacks or credential stuffing attacks against their clients.
Yanluowang and its companions are capable of performing different forms of persistent phishing attacks. Even minimal information about a client within the leaked data gives threat actors enough material to devise a deliberate phishing attack on Cisco’s clients, allowing them to find their way up the supply chain.
Vulnerable Software Identifier
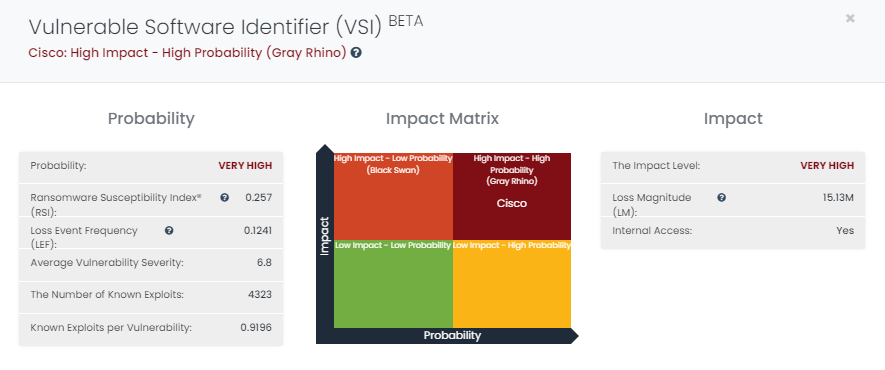
One prominent signal on the Black Kite Platform, which gives a quantified risk assessment of a vendor, is the Vulnerability Software Identifier, or VSI. Black Kite identifies the vulnerable software with the impact analysis of a software vendor by estimating the probability and impact of a cyber incident on your organization due to said vendor.
According to the Black Kite findings, Cisco is considered a High Impact – High Probability vendor. Here, both the probability of experiencing a cyber attack and the total impact are high. Any software vendors that fall into this category are critical to the organization.
How to determine vendors that use Cisco products
Any cyber risk professional working at an organization that invests heavily in third-party risk management asks the same question after a data breach incident like this: “How can I determine my vendors that use Cisco products?” Asking this question is crucial to prevent any cascading effect on the supply chain, even if the possibility of the impact on the vendor is low. Determination of vendors that use Cisco products helps the organizations warn the vendors about the incident and provides them TTPs and attack vectors.
Large organizations with hundreds of vendors cannot afford the time and cost of asking every vendor whether or not they use Cisco products. Cyber risk intelligence tools such as Black Kite can help organizations identify their vendors that use a specific product.
For instance, Black Kite customers can filter their monitored vendors by selecting the product types used by the vendors.
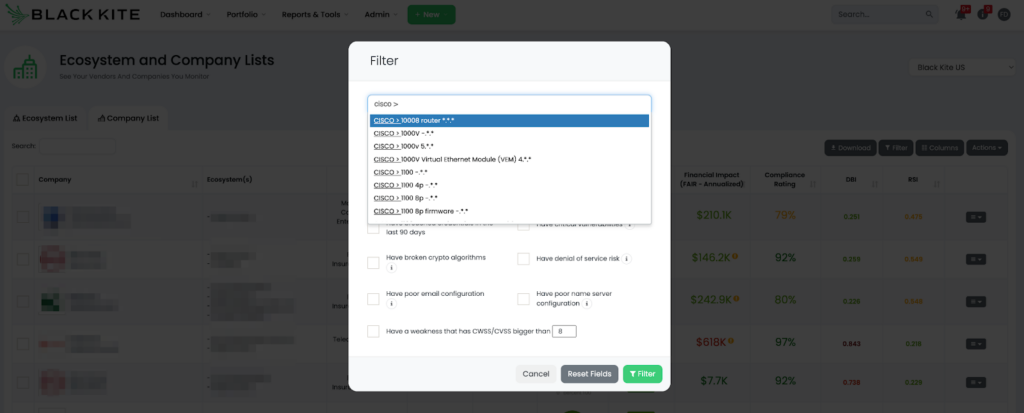
Black Kite additionally launched automatic focus tags that label Cisco clients. Black Kite users can use these tags to filter their vendors easily and see what Cisco products their vendors use.
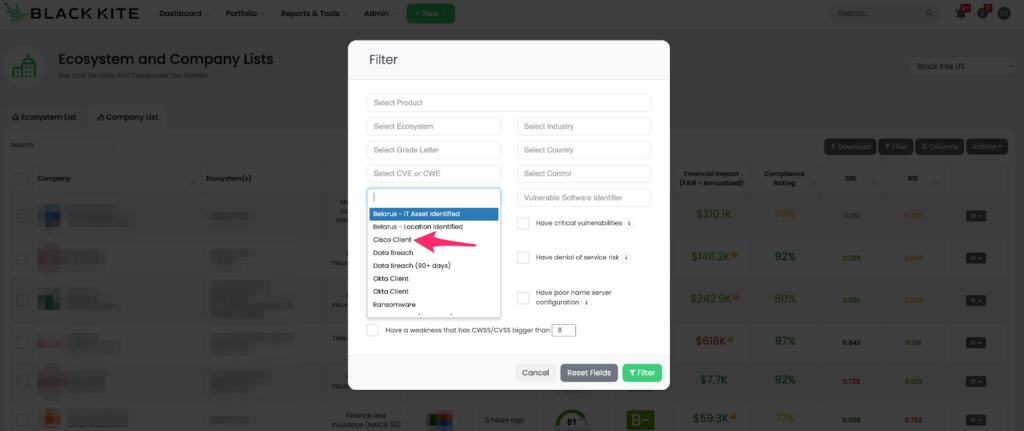
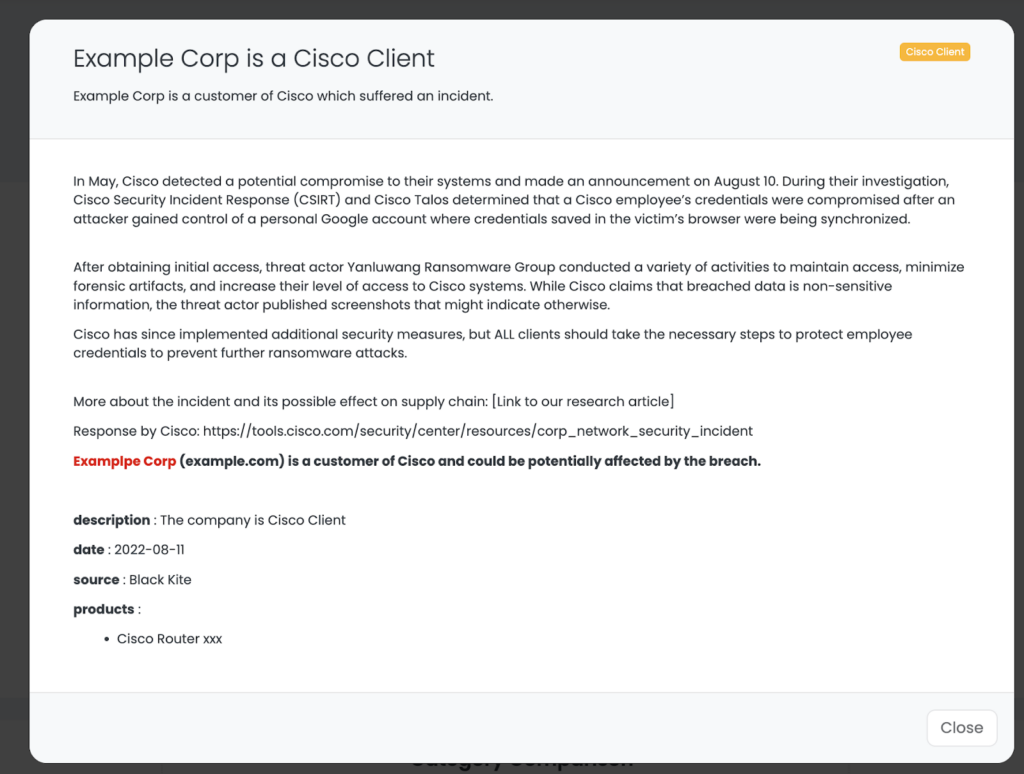
Remediation and recommendations to protect your supply chain
- List all the vendors that have access to your organization’s systems or store sensitive data that belongs to your organization
- Filter the vendors that use Cisco products
- Alert them with detailed information about the Cisco data breach
- Advise them to check the TTPs and IoCs of the threat actor
- Advise them to increase employee awareness of possible phishing attacks
- Continuously monitor your vendors’ cyber security posture and cyber hygiene against ransomware operations and all other threats

