Check Whether Your IP Assets Are Blacklisted Or Not For Free
Written by: Black Kite
Employees may download applications that compromise computers and networks. As a result, the IP addresses can become part of a hacker’s network and hosting malware. Hackers can leverage IP addresses for Advanced Persistent Attacks, a situation that can compromise the company’s brand reputation and lead to a breach.
IP Reputation tells something about your company
Black Kite conducted a survey, which reviews trends and insights from Cyber Risk Scorecard key data points that include detailed external security risk data from cyber risk scoring for 5,217 organizations across multiple industries and over one million active assets on the Internet, including web and network devices. Black Kite cyber risk scorecard checks if an organization’s IP addresses have been associated with any blacklists.
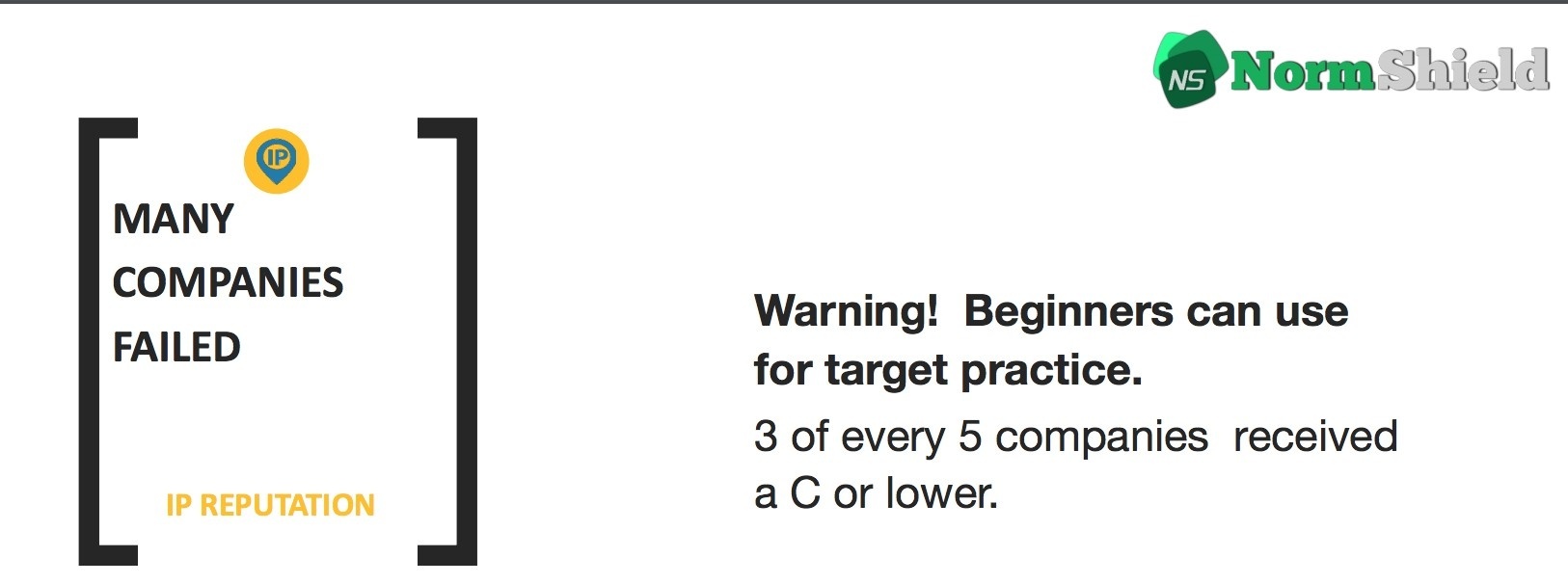
According to the survey, 60% of the companies fail and receive C or lower grade on IP Reputation. This result reveals a bitter truth, which is a simple fact that even the beginner-level hackers (aka script kiddies) can use your IP addresses for practice. Your IP assets can be exploited for malicious actions and, since you are not aware of this exploitation, your IP addresses may appear in blacklists. Thus C or lower grade poses a significant cyber risk. The complete version of this survey can be reached here.
5 things to do to mitigate cyber risk due to low IP Reputation!
- Monitor cyber reputation.
- Ask reputation and content filtering sites to properly categorize your website.
- Block unexpected/malicious traffic on the firewall.
- Change the default resolving IP address of all domains to a whitelisted IP or a loopback IP.
- If possible, avoid using shared servers (IP addresses used by other domains).
Check whether your IP assets are blacklisted or not with Black Kite’s Free IP Blacklist Search
To learn whether your company’s IP addresses are blacklisted, check Black Kite’s free IP Blacklist Search service. Black Kite’s blacklisted IP data is collected from various resources on the net plus Black Kite’s own honeypot systems spread all over the world.
Where do we get the data
Black Kite has a number of servers spread around the world to collect threat data with honeypot system. We are collecting, consolidating and grouping hundreds of suspicious IP addresses every day from 400+ open source threat intelligence feeds.
How to do it
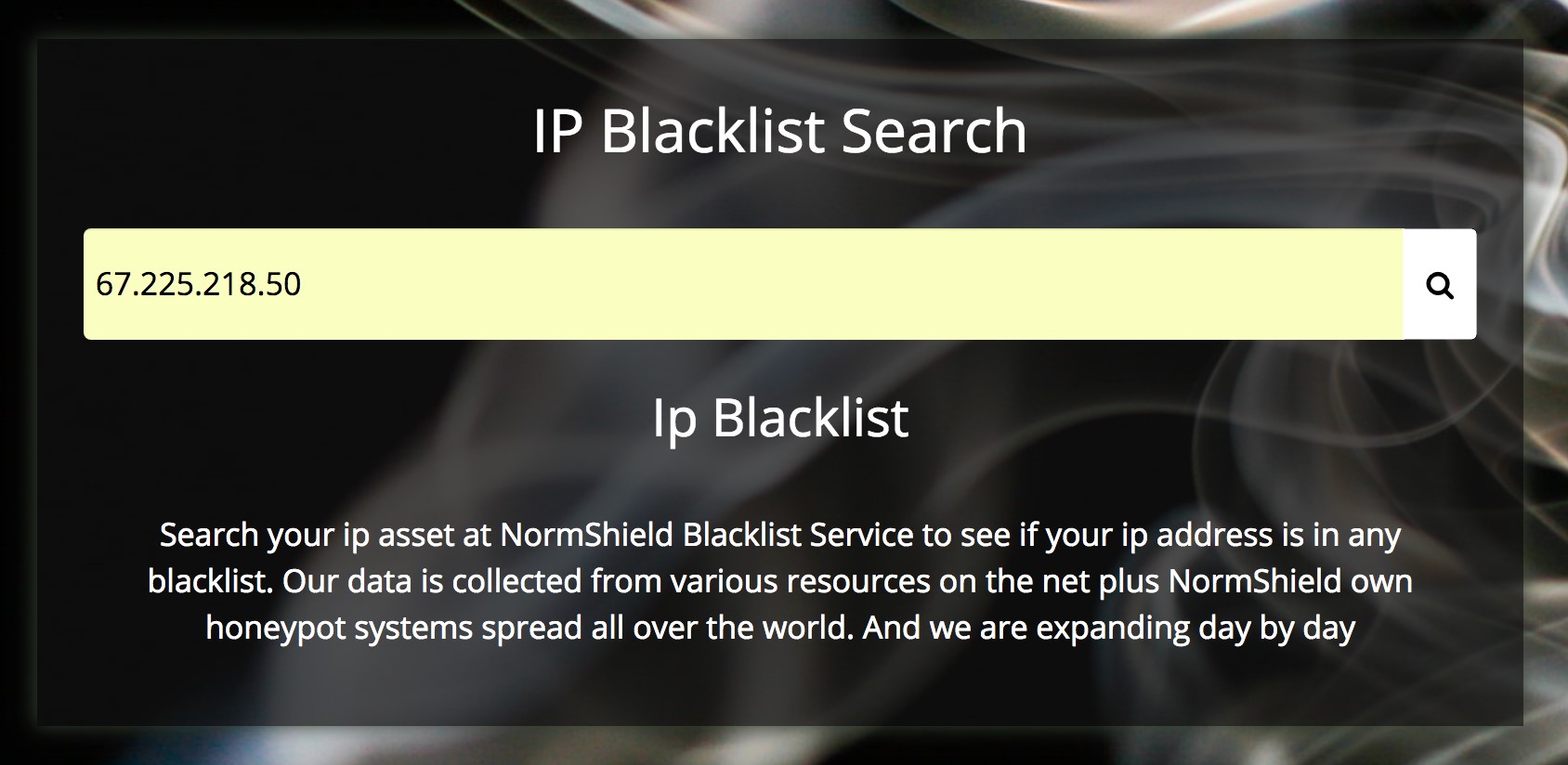
Step 1. Enter any of asset’s IP address that you want to check. Press Enter/Return and scroll down to see the results.
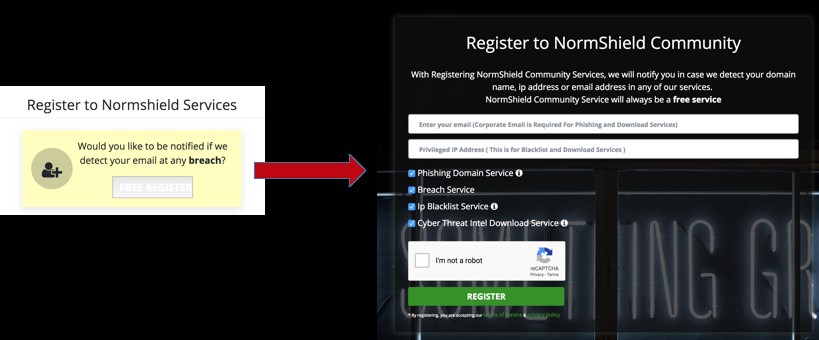
Step 2. If you would like to receive a notification when one of your company accounts is breached, click on the Free Register button to join Black Kite Community and fill out the form (note that you can see the results by simply scrolling down without registration). Black Kite only needs your corporate e-mail address and privileged IP address for IP Blacklist search (that will be shown automatically). Just check the free services about which you want to receive notification and click on the Register button.
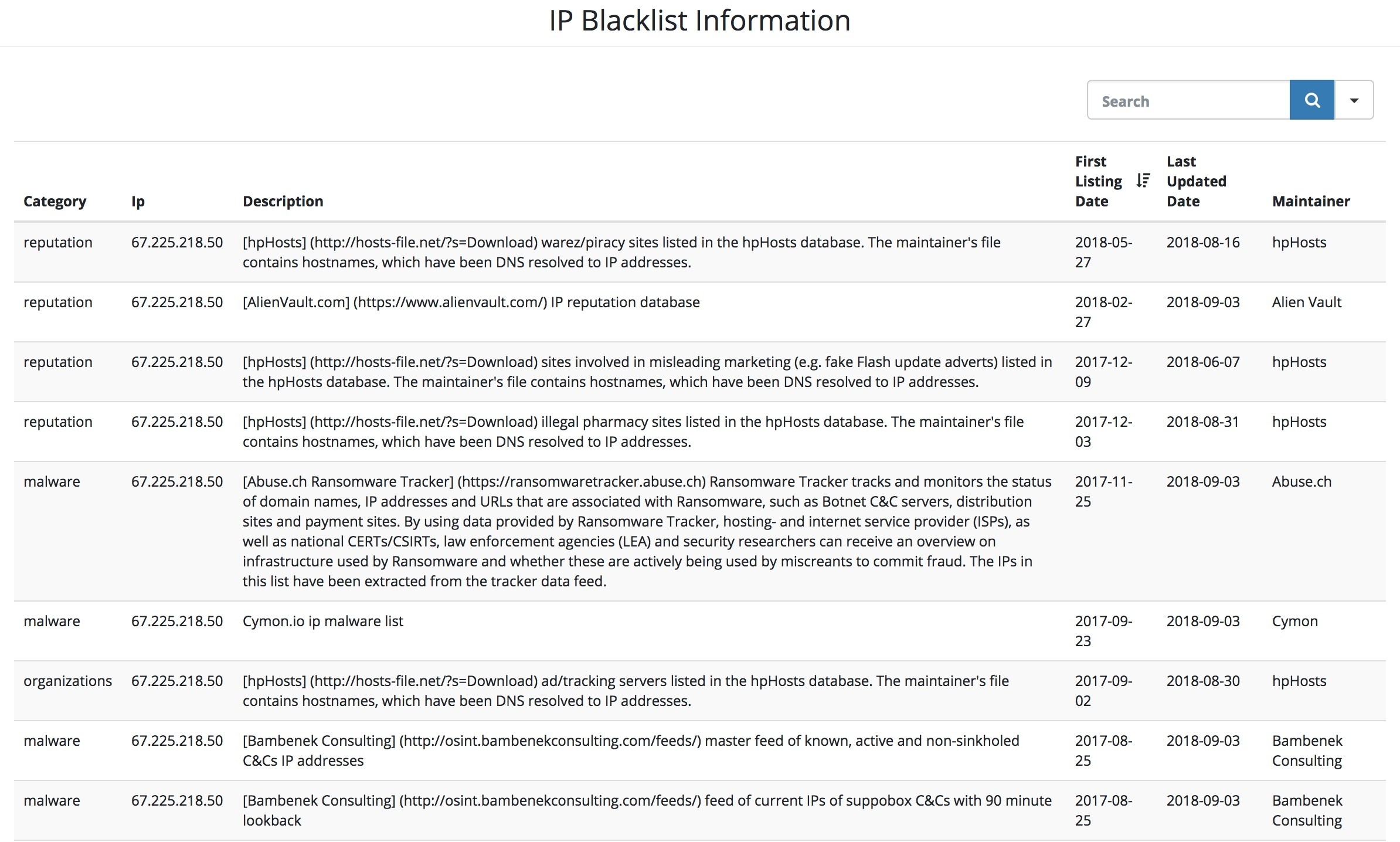
Step 3. See the IP Blacklist information. The information fives category of the database (reputation, malware, etc.), the description of the database, the date of the first time the IP address is listed in this database and the date when it is updated last time, and who maintains the database.
You can filter the results by using the Search box on the top right, sort the results with respect to any field, and even check/uncheck the fields that you want to be shown.