WHY YOU WANT HUMAN EXPERTS BEHIND YOUR TPRM DATA: BLACK KITE RESEARCH & INTELLIGENCE TEAM (BRITE)
Raw data, even from powerful sources, lacks the contextual intelligence needed for effective third-party cyber risk management (TPCRM). It’s this human element, the ability to connect the dots and discern patterns, that transforms data into actionable intelligence. The Black Kite Research & Intelligence Team (BRITE) conducts in-depth research to provide the critical context needed for Chief Information Security Officers (CISOs) and Third-Party Risk Managers to make informed decisions and proactively mitigate risks.
The team’s fingerprint can be found on Black Kite’s most impactful products and resources. That includes the Ransomware Susceptibility Index®(RSI™), FocusTags™, the artificial intelligence (AI) engines that power our products, and our many in-depth research reports.
As our own Chief Security Officer, Bob Maley says:
“What truly sets Black Kite apart is the BRITE team. They’re not just running scans; they’re researchers digging into the data, revealing the critical connections that automated tools miss. That’s the real game-changer.”
WHAT EXACTLY IS BRITE?
BRITE is a team within Black Kite that provides research led by Black Kite’s Chief Research and Intelligence Officer, Ferhat Dikbiyik. Ferhat has 15 years of experience as a researcher in the risk-centered studies space, which he now applies to studying threat actors, the hacker mindset, cyber risk, and cyber attacks.
BRITE is made up of a few dozen people who work in the following verticals:
- Data engineering: This team processes and maintains terabytes of data every day. Their mission is to make sure data in our products is accurate, transparent, and fast.
- Data research: This team manages Black Kite’s machine-learning algorithms and projects that help generate the tailored intelligence Black Kite provides.
- Cybersecurity research: This team is on 24/7, scouring hacker forums, Telegram channels, the dark web, and more to identify vulnerabilities and threats.
HOW DOES BRITE’S WORK IMPACT BLACK KITE CUSTOMERS?
We’ve seen the forum chatter out there where security professionals complain about security rating service providers being slow, inaccurate, and opaque with its ratings methodology. It can take up to a month for a vendor to see their security rating score change from these providers, even on the simplest of issues.
We don’t want to be in that camp. Do you know how long they have to wait on Black Kite? One day at most.
At Black Kite, we take pride in providing our customers with accurate, transparent, and fast risk intelligence, so teams can easily make informed risk decisions and bring cyber resilience into their supply chains. In other words, our goal is to provide teams with targeted, tailored risk intelligence they can easily act on that stays updated in near real-time. The work that BRITE does makes this possible.
BRITE POWERS BLACK KITE’S BIGGEST DIFFERENTIATORS
The Ransomware Susceptibility Index®
Black Kite’s RSI™ helps teams understand the likelihood that an organization in their ecosystem will experience a ransomware attack. Rather than looking at indicators of compromise after an event, the RSI is a proactive measurement of near-future incidents.
RSI follows a process of inspecting, transforming, and modeling data collected from a variety of OSINT sources, such as internet-wide scanners, hacker forums, the deep/dark web, and more. Using machine learning (ML), RSI then identifies critical indicators correlated with an attack. Companies then receive a score that reflects their susceptibility to an attack.
BRITE collects and analyzes data that goes into RSI, and frequently verifies that the RSI is accurate.
FocusTags™
Black Kite FocusTags™ automatically flag vendors impacted by cyber events, such as data breaches, ransomware attacks, known exploitable vulnerabilities, and security incident disclosures/filings.
Many threat intelligence vendors struggle to report on critical events in a timely way. For example, some security rating providers may take weeks to months to log a new mass event. Comparatively, Black Kite applied a FocusTag to 82.4% of OSINT-discoverable vulnerabilities before or within 24 hours of being added to CISA’s Known Exploited Vulnerability (KEV) catalog last year. One of our customers told us they waiting two months for intelligence on a vulnerability from another provider. By that time, any exploitation can wreak havoc.
How can Black Kite act so quickly?
In short, BRITE focuses on relevant data, rather than all available information. Consider this: In 2024, more than 40,000 CVEs were published (as shown by the light gray circle in the diagram below). No team has the bandwidth to investigate every single one of these vulnerabilities. Even if you investigate vulnerabilities with a CVSS score of 7.0 or higher, that’s 20,000 CVEs (as shown by the dark gray circle in the diagram below), or if you just look at vulnerabilities with a CVSS score of 9.0 or higher, that’s still 4,000 CVEs (as shown by the blue circle in the diagram below). Still too many.
But what really matters are the CVEs that will be exploited. Last year, 768 CVEs were exploited in the wild (as shown by the purple oval in the diagram below). A proactive approach to TPCRM will address that subsest of vulnerabilities. And last year. BRITE identified and analyzed 780 high-priority CVEs (as shown by the green oval in the diagram below).
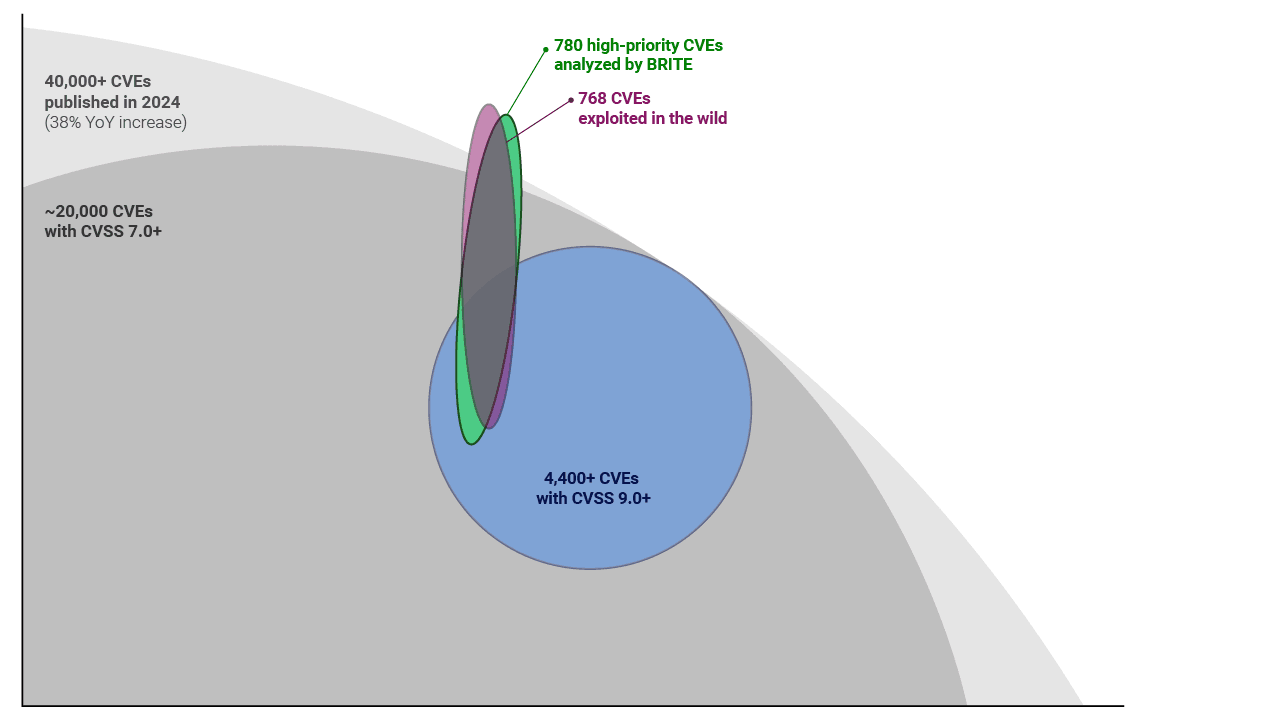
BRITE takes it a step further by looking at vulnerabilities that our customers need to focus on – those that are discoverable by open-source intelligence (OSINT), the same resources bad actors use to find vulnerabilities to exploit. So of the 780 high-priority CVEs analyzed by BRITE last year, 295 are discoverable by OSINT. In one customer’s supply chain, there may be about a dozen of these vulnerabilities present. This is a much more manageable number to manage. And with the research BRITE offers on each of these vulnerabilities, our customers can go to their vendors with actual intelligence – not questionnaires – for faster remediation.
First-Party Research Reports: Keeping a Pulse on Cyber Threats
BRITE publishes several reports each year that share our data and analysis on the cyber threat landscape and what those insights mean for customers and beyond.
These reports include:
Third-Party Breach Report:
Each spring, we publish a report that analyzes all third-party breaches from the previous year to explore trends in attack vectors, attack targets, and actionable tips to improve third-party security. Check out our sixth annual report, “2025 Third-Party Breach Report: The Silent Breach, How Third Parties Became the Biggest Cyber Threat in 2024.”
Ransomware Report:
BRITE’s annual State of Ransomware Report provides in-depth analysis of ransomware trends, dissecting attack patterns, vulnerable industries, and emerging threat actor tactics, empowering organizations to proactively strengthen their defenses. Check out our latest report, “State of Ransomware 2024: A Year of Surges and Shuffling.” (And keep an eye out for our 2025 Ransomware Report coming in May.)
Supply Chain Vulnerability Report:
New this year, the 2025 Supply Chain Vulnerability Report confronts the challenge of ‘vulnerability overload’ by revealing the shortcomings of applying traditional vulnerability management to third-party cyber risk management and introducing a framework that prioritizes vulnerabilities in the supply chain.
Vertical-Specific Reports:
In addition to broad landscape reports, we also publish industry-specific reports, such as “Healthcare Under Ransomware Attack: Why Healthcare Is Now the 3rd Most Targeted Industry in the Ransomware Cybercrime Ecosystem,” to provide TPRM leaders with more granular insights relevant to their specific industries.
We offer our reports with no registration required and strings attached to make sure our learnings are accessible to anyone who wants to learn more.
DELIVERING UNMATCHED, TAILORED INTELLIGENCE
When a cyber event occurs, time is of the essence. Black Kite customers can access accurate, transparent, and highly tailored intelligence at a remarkable speed.
If you’re interested in experiencing the impact of BRITE on your threat intelligence operations, request a free demo.