What is “Third Party” in Third-Party Risk Management?
Published
Feb 19, 2020
Updated
Jan 27, 2026
Authors
Black Kite
Businesses rely on third parties to deliver a service or product to their customers. In a tightly-linked digital world, third-parties are indispensable and inherently risky elements of a digital ecosystem.
Before going deep into the risks they pose to the business, we need to understand the definition and be able to identify the ones critical to the organization. Here are the definitions you need to know and how Black Kite can help with monitoring third-parties continuously.
What does the “third party” mean?
A third party is a company or entity with whom you have an agreement to provide a product or service to you or to your customers on behalf of your organization. A more general term for a third party is a vendor or a supplier. Nowadays, it’s almost impossible to find a company that doesn’t leverage third-party suppliers or vendors.
In a tightly-linked digital world, third-parties usually access companies’ systems and resources. These links are so inherent and part of everyday use that most of them are hardly accounted as third-parties in the inventory. Take jquery libraries on content delivery networks (CDN) as an example. Numerous 2018 and 2019 breaches have been caused by this specific use of third-party. Or Trello and Jira boards holding both company-specific and employee-specific data.
As a result, companies end up sharing sensitive data with these third parties beyond their knowledge most of the time.
Examples of Third Parties

Here are a few examples of who can be considered as a “third party” in third-party risk management
- Call center
- Marketing Agency
- Law Firm
- Office supplies provider
- Telephone company
- Courier services
- Software Development Service Provider
- Security Service Provider
- Hosting Provider
- Education company
What are my (critical) third parties?
Companies not only should understand the meaning of a third party but also “know their third-parties”. How does this apply to the business? It means that if a company is bound to certain laws, regulations, contracts, and even working out an enterprise risk management and keep the risk within a certain threshold, etc, then its third-party service providers and vendors automatically need to meet these requirements. At the end of the day, it comes to the fact that third parties need to be assessed and even be continuously monitored with regards to their commitment to business’ risk tolerance, regulatory compliance and contractual requirements. By doing this, you make sure that they don’t pose an unnecessary risk to the organization. But let’s not be that quick, we will leave these issues to the upcoming blog posts.
Follow these steps to identify critical third-parties linked to your business that might pose a risk:
If a third-party vendor
- receives or has access to personal or sensitive data,
- has persistent access to your network,
- or is critical/material to your company,
then it is in scope for risk assessment and continuous monitoring.
How Black Kite Can Help?
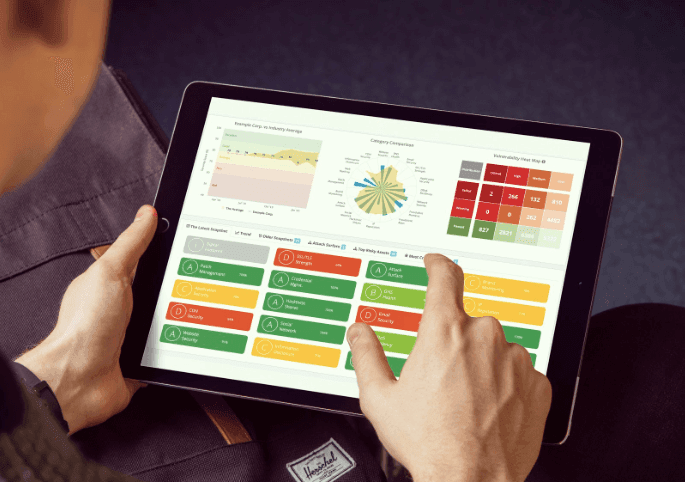
Monitoring and continuous oversight on your third-party vendors and supply-chain are critical. That goes beyond your organization including anywhere your data is handled during the process.
Black Kite Third-Party Risk Assessment continuously assesses an organization, captures critical information in the cyber risk dashboard and provides detailed drill-down capabilities to fully understand each risk. Ongoing monitoring surfaces priority risks and measures cyber risk posture improvement over time. By providing Cyber Rating (technical), Compliance Estimations (policies and processes) and Open FAIR™ results (the probable impact in financial numbers), Black Kite’s vision is to give a complete risk picture of a third party.