Ransomware is Easy, And That's the Problem
Introduction
Ransomware attacks are on the rise—not due to more advanced malware, but because launching an attack has never been easier. Today, the real threat isn’t sophistication. It’s accessibility.
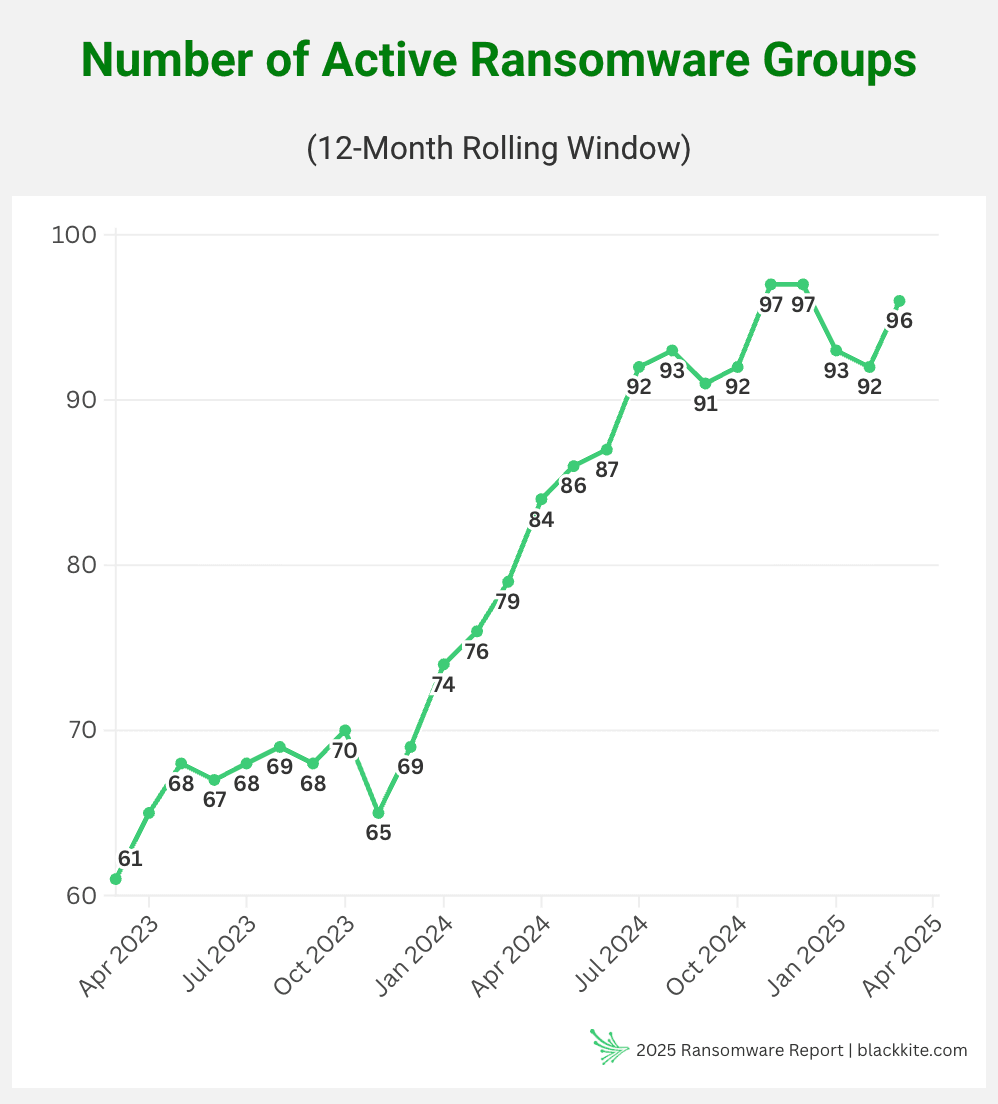
Over the past year, more than 6,000 ransomware victims were publicly reported—a 24% year-over-year increase. This surge came even as law enforcement took down some of the most well-known groups, including LockBit and AlphV. But their disappearance didn’t slow things down.
In their place, 52 new ransomware groups emerged between April 2024 and March 2025, bringing the total number of active groups to a record 96:
And these aren’t just rebranded versions of traditional ransomware groups. Our 2025 Ransomware Report shows these actors operate with looser structures, little discipline, and inconsistent tactics. With so many groups now active—most working independently—ransomware has become less strategic and far more opportunistic.
Ransomware is no longer a high-skill operation. It’s a low-barrier criminal business. And Ransomware-as-a-Service (RaaS) is what’s made that shift possible. These subscription-based platforms have turned cyber extortion into a scalable business model—one that opens the door to anyone with a motive, a little money, and no scruples.
RaaS 101: The Business Behind the Boom
Ransomware-as-a-Service has completely changed the economics of ransomware. What once required deep technical expertise, underground connections, and costly infrastructure can now be done with a few hundred dollars and an internet connection.
RaaS operators function like criminal SaaS vendors, selling plug-and-play ransomware kits to aspiring attackers for as little as $500. These kits often include everything an attacker needs: encryption tools, leak site hosting, payment processing, and even customer support.
What makes RaaS particularly dangerous isn’t just how easy it is to access—it’s how widely it scales. Affiliates can run high-volume campaigns without much experience. The result is a flood of low-skill attacks that are faster, sloppier, and harder to predict. Ransomware groups are no longer going after volume—they’ve going after value.
Many affiliates switch between RaaS platforms, bringing stolen data and access credentials with them—leading to repeated attacks on the same organization, often within days. Our data shows that 14 organizations over the past year were hit by two separate ransomware groups within a single week. Once a victim appears on a leak site, they become a target for opportunistic affiliates looking for their next mark.
With near-zero barriers to entry and a growing pool of affiliates, defenders aren’t up against one consistent threat model. They’re facing a chaotic ecosystem where tactics vary widely and almost anyone can get involved.
From Organized Crime to RaaS-Fueled Chaos
This fragmentation has given rise to what we call “ransomware-as-a-chaos”—a landscape where ransomware has become so accessible and disorganized that control has completely unraveled. It’s a natural consequence of the democratization of ransomware.
In the past, groups like LockBit ran like criminal enterprises with structure. There was consistency, predictability, and even a strange sort of professionalism in how they operated. That’s gone. Today’s attackers are erratic, often lacking the infrastructure or experience to run sophisticated campaigns. Some skip the negotiation phase entirely, demanding flat fees or dumping stolen data without warning. Others mimic legacy tactics but fail to execute them effectively.
With low-cost, ready-made ransomware kits, the threat has shifted from a few major actors to a chaotic mass of attackers with no rules. That’s what makes it so difficult to defend against: there’s no pattern, no consistency, and no central force driving the attacks.
We’re not dealing with 20 or 30 known players anymore. The Black Kite Research Group is now tracking over 100 groups—half of which didn’t even exist a year ago. And most of them don’t follow any recognizable playbook. The result is that attacks feel less like coordinated campaigns and more like street fights: loud, messy, and completely out of control. That’s the chaos we’re facing—and it’s only accelerating.
SMBs: The Path of Least Ransomware Resistance
All this chaos isn’t just changing how attacks happen—it’s also changing who gets hit. With less emphasis on large payouts and more on quick wins, small and mid-sized businesses (SMBs) have become primary targets.
Just 11% of publicly disclosed victims in the past year had annual revenue exceeding $100 million. The most frequently hit companies were those earning under $20 million per year, with a clear concentration in the $4 to $6 million range—a segment that presents a tempting target for attackers.
For threat actors looking to move quickly and avoid scrutiny, SMBs strike the right balance: small enough to slip under the radar, but big enough to pay. Many lack dedicated cybersecurity teams and incident response plans, making them easier to breach—and more likely to pay to make the problem go away.
Many SMBs manage data, infrastructure, or services for much larger organizations. So when one gets hit, the blast radius extends far beyond its own size. If your vendor goes down, so do you. For ransomware groups, targeting an SMB often isn’t the endgame—it’s just the first domino. Case in point: CDK Global. The 2024 ransomware attack on this mid-sized automotive software provider disrupted over 3,000 car dealerships across the U.S., stalling inventory systems, delaying customer deliveries, and freezing CRM platforms.
As ransomware groups prioritize speed and volume, more SMBs are getting caught in the crosshairs. And as CDK Global’s case illustrates, the damage can extend far beyond the initial breach—not just for the victim, but for everyone downstream.
Ransomware Isn’t Random—RSI™ Proves It
In a threat landscape this messy, traditional third-party risk management (TPRM) methods—like static point-in-time assessments—aren’t enough. That’s why we created the Ransomware Susceptibility Index® (RSI™).
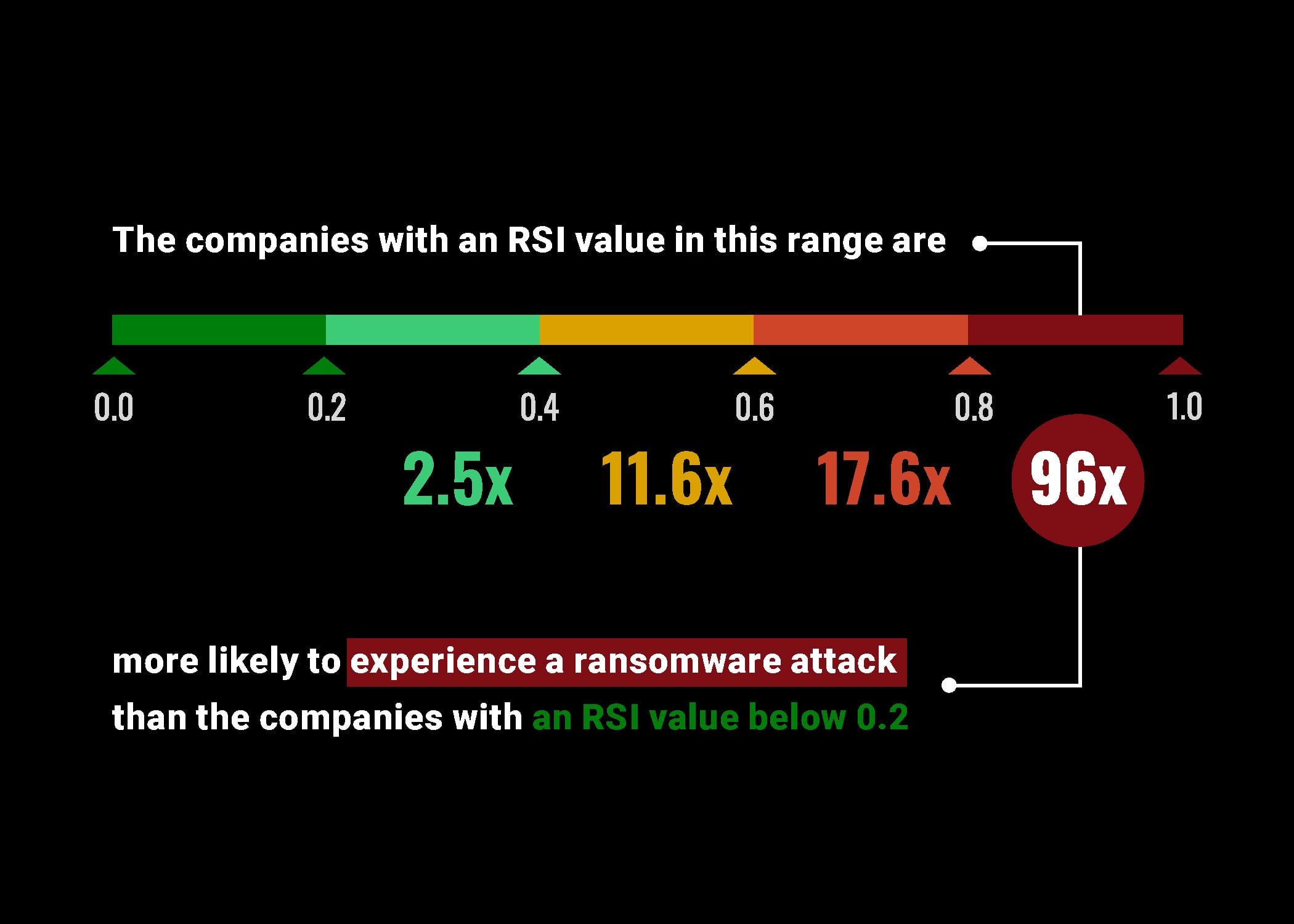
RSI is a predictive signal that identifies which organizations are most likely to be targeted by ransomware. It generates a dynamic score between 0.0 and 1.0, with higher scores indicating greater susceptibility. Since ransomware groups don’t pick targets randomly—they choose victims who are exposed, accessible, and profitable—RSI reflects that logic.
Here’s what the data tells us about RSI and real-world risk:
- Companies with an RSI above 0.8 were 96x more likely to be attacked than those with a score below 0.2.
- While just 0.82% of companies fall into this high-risk tier (RSI > 0.8), nearly half (46%) of them experienced ransomware attacks within the year.
- In 88% of those cases, RSI spiked more than 10% in the six months leading up to the breach.
RSI isn’t rooted in theoretical modeling—it’s based on data from more than 5,700 ransomware victims and hundreds of thousands of non-victims. More than just a risk score, RSI provides a continuous early warning system, allowing organizations to shift from reactive defense to proactive third-party risk management.
The Easier Ransomware Gets, the More Dangerous It Becomes
The explosion in ransomware activity over the past year wasn’t driven by new vulnerabilities—it was driven by access. RaaS has dramatically lowered the entry bar, unleashing a wave of new attackers—many with little experience but plenty of impact. Ironically, cheap attack kits have led to some of the most expensive consequences we’ve ever seen—shutting down systems, compromising sensitive data, and causing major reputational damage.
Organizations need to stop viewing ransomware as a technical issue. It’s not just about malware anymore—it’s a full-fledged business model that’s been optimized, monetized, and industrialized. You don’t fight that with checklists or point-in-time audits. You fight it by recognizing it for what it is: an operational threat that demands continuous visibility and proactive defense.
At the end of the day, ransomware isn’t just a risk on paper—it’s a business interruption waiting to happen. It might sound like a distant, abstract problem—until it’s your company locked out of every system, with a ransom note blinking back at you from every screen. That’s when it gets real. And if you’re not taking it seriously today, there’s a good chance you’ll be paying for it tomorrow—literally.
Read the full 2025 Ransomware Report for a closer look at how ransomware threats are shifting—and what it takes to stay ahead.