Downfall of a Digital Titan: The Global Sting That Toppled LockBit
In the shadowy corners of the internet, a cyber titan fell. Operation Cronos wasn’t just a sting—it was a spectacle. Here’s the inside scoop on how a global posse of law enforcers has turned the tables on LockBit, the ransomware behemoth. This takedown reads like a spy thriller, but for the cyber world, it’s real life, and the consequences are even more gripping.
LockBit, notorious for its ransomware rampage, has long been the digital boogeyman for businesses worldwide. With precision, they’ve struck at the heart of our digital reliance, leaving a trail of disrupted lives and businesses. But in a digital David versus Goliath moment, Operation Cronos has shown that no one is untouchable.
As the dust settles, we’re left to dissect the aftermath: the strategy, the downfall, and the seismic shift in the cybercrime landscape. This is the story of how LockBit’s cybercrime domino fell, and what it means for the future of digital security. Buckle up; this is where it begins.

Lockbit’s dark web blog after it was seized
Operation Cronos: The LockBit Timeline of Takedown
The takedown of LockBit, the ransomware colossus, wasn’t an overnight exploit—it was a meticulously plotted siege that crescendoed with Operation Cronos, a testament to cyber resilience and international collaboration. Here’s how the operation unfurled, step by cyber-step.
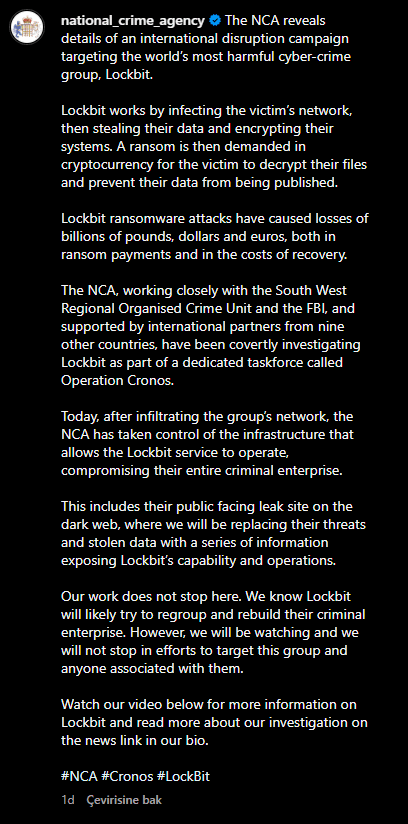
NCA announcement
Before the public spectacle, there was the silent gathering of intel. Throughout 2023, the National Crime Agency (NCA) of the UK, the FBI, and their international partners, including Europol, conducted covert operations, mapping the digital footprint of LockBit and laying the groundwork for their eventual strike. Cybersecurity companies such as Trend Micro and Prodaft also provided intel to agencies for the success of the information by pinpointing over 28 affiliates and prying open the trove of decryption keys and mapping out the crafty TTPs (tactics, techniques, and procedures) of LockBit’s affiliates.
The operation hit daylight when agencies from across the globe, including Europol, struck simultaneously. It was a multi-pronged digital assault that saw 34 servers across countries like the Netherlands, Germany, and the United States fall like dominoes. This cyber blitz was the product of an international taskforce, all hands on deck, targeting every node of LockBit’s dark web presence.
On February 20, 2024, the world woke up to the new face of LockBit’s dark websites. Instead of ransom demands and stolen data, banners from the NCA and partners heralded the success of Operation Cronos. LockBit’s infrastructure was now a digital trophy case for law enforcement.
If rumors of a PHP vulnerability leading to LockBit’s undoing hold true, it would be a twist of cyber karma — the exploiters becoming the exploited, caught in a web of their own overlooked weaknesses.
In a poetic twist, LockBit’s own platforms were turned against them. Their seized dark web sites, once a showcase of conquests, now displayed badges of law enforcement. And the data—meticulously gathered intelligence on the syndicate’s activities—was laid bare for the world to see.

Lockbit’s website is used to publish leaked data of the group itself.
Diving into the LockBit Labyrinth
LockBit’s digital fingerprints are smeared across the cyber realm, with their handiwork impacting a staggering range of victims. With a focus on entities below $100 million in annual revenue, LockBit has been indiscriminate yet tactical, striking over a thousand victims in just the past year.
From exploiting vulnerabilities like Citrixbleed to deploying ransomware, their tactics are as varied as their targets. Yet, they’ve shown an odd sense of ethics, as seen in their response to an affiliate’s attack on a German hospital, where they offered a free decryptor—a move that hints at their complex image management.
Their alliance with AlphV, when they came to their aid after a shutdown, underscores a symbiotic underworld, where even rivals band together against common threats. This underworld camaraderie, however, does little to shield them from the concerted might of international law enforcement, as evidenced by the recent crackdown.
LockBit, a behemoth in the ransomware space, has now been dissected under the public’s microscope. The leaked data from Operation Cronos reveals a sophisticated and compartmentalized operation—a cybercrime enterprise with a customer service veneer. This information offers invaluable insights into their expansive and, until recently, shadowy operations.
LockBit Under the Lens: A Data-Driven Perspective
At Black Kite Research and Intelligence Team (BRITE), we cast a wide net over the ransomware landscape, meticulously tracking over 130 groups. In 2023 alone, our vigilance covered the activities of 67 active ransomware groups, compiling data on over 4,700 victims. Our focus on LockBit’s reach and impact paints a detailed picture of its operational scope and victim profile.
LockBit, in a class of its own, led the ransomware pack with a staggering 1,005 victims announced in 2023, as shown in our charts. Notably, our analysis of over 400 LockBit victims revealed a striking insight: 75% boasted annual revenues below $100 million, with 43% under the $20 million mark. This data challenges the perception that ransomware only targets the largest corporations; in truth, LockBit’s tentacles reached deep into the fabric of small and medium-sized businesses.
Industries across the board felt LockBit’s grasp, with manufacturing and professional services bearing the brunt, as our industry-focused chart demonstrates. Geographically, their strategy was no less comprehensive, with the United States, the United Kingdom, and France emerging as top targets.
As we look ahead, the data serves as both a record of LockBit’s former stronghold and a guidepost for future defenses. With the LockBit operation now disrupted by international law enforcement, the question remains: who will fill the void they’ve left, and how can organizations prepare? BRITE remains at the forefront, deciphering trends and providing actionable intelligence to navigate the evolving ransomware threat landscape.
The LockBit Paradox: Image vs. Affiliate Relation
LockBit’s ascent in the ransomware realm was as rapid as it was reckless towards the end. With growth came a treacherous balancing act: upholding a veneer of a hacktivist group while managing a network of affiliates with less scrupulous agendas. This cybercriminal powerhouse, which once set its own rules to avoid healthcare or nonprofit sectors, increasingly saw these boundaries crossed, not by their enemies, but from within.
The group’s public image, carefully curated to portray a certain – twisted- ethical stance, began to crumble under the weight of its own contradictions. As LockBit expanded, the control over its affiliates—those crucial cogs in their ransomware-as-a-service machine—started to slip. This was a group straining against the leash of its own making, with justifications for rule-breaking becoming a routine chorus following each high-profile attack.
The group faced a constant tug-of-war. On one end, LockBit sought to maintain a facade of principled criminals, selectively releasing decryption keys as a gesture of goodwill, as in the incident with the German hospital network. On the other, their affiliates, driven by profit, frequently breached these rules, dragging the group’s name through the mud with attacks on vulnerable sectors.
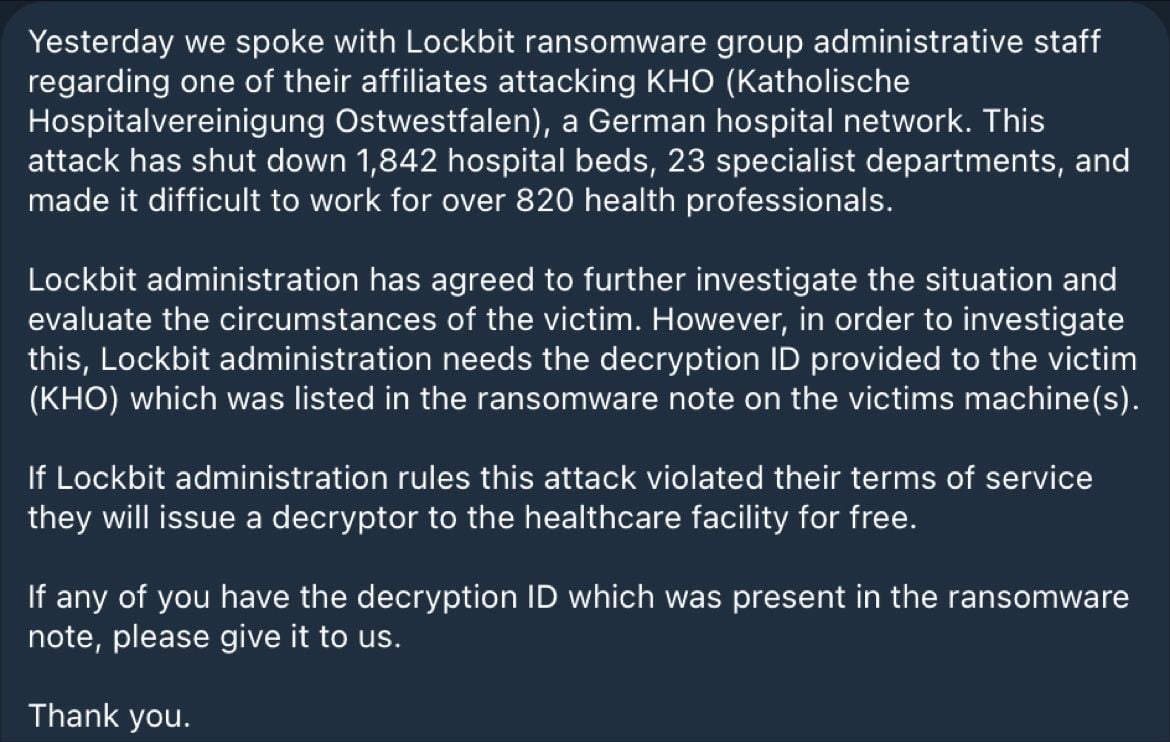
Lockbit’s statement given to vx-underground about the attack on a hospital
In this high-stakes environment, speed was a double-edged sword. LockBit’s quick moves and bold targets grabbed headlines, but also painted a bullseye on its back. It wasn’t just about breaking rules; it was about breaking them too loudly, too visibly. As the saying goes, the candle that burns twice as bright burns half as long. LockBit’s flame drew too many eyes, and in the end, their meteoric rise set the stage for an equally swift downfall. The wall they hit was one of their own construction, and it halted their charge with unyielding finality.
LockBit’s Twisted Self-Perception in the Ransomware Realm
In the ecosystem of cybercrime, LockBit’s rise to prominence was not just about the code; it was about the culture they cultivated. They considered themselves the kings of ransomware, providing what they framed as a ‘service’ to the digital world. This self-perception was not merely delusional but strategic, a way to rationalize their actions and elevate their status among peers and victims alike.
They approached the ransomware game with a business-first mentality, seeing their exploits as a ‘post-paid service’—a term that thinly veiled the disruption and fear they sold. This mindset was evident in their cavalier response to the takedown of AlphV, another prominent group in the ransomware scene. Where others might see a cautionary tale, LockBit perceived an opportunity, a chance to consolidate power and reinforce their position at the top.
In the clandestine forums where cybercriminals converge, LockBit fashioned an image not just of dominance, but of professionalism and camaraderie. This was a group that understood the value of relationships—even with those who might be considered rivals. Their support of AlphV amidst its takedown wasn’t just an act of opportunism, but a display of solidarity, reinforcing a culture where even competitors could find mutual respect and common ground.
This duality of LockBit’s nature—ruthless in their attacks, yet respectful in their criminal alliances—paints a picture of a group that navigated the dark waters of cybercrime with a certain code of conduct. It’s a reminder that beneath the disruptive exterior lay a network of individuals bound by shared goals and an understanding of their ecosystem’s fragility.
LockBit’s support of AlphV, as revealed in the forum exchanges, was a calculated move to uphold their standing as leaders who could extend a lifeline to a rival, all while underlining their own stature as the pinnacle of ransomware sophistication.”
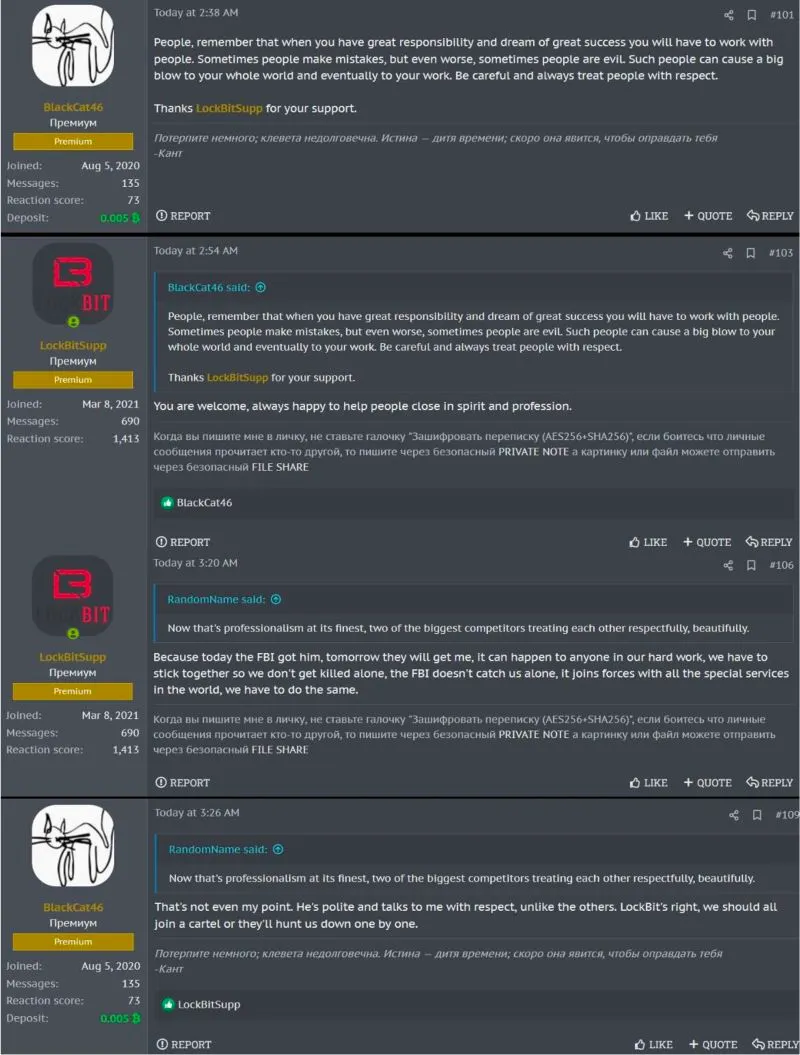
However, the very speed of their growth and the boldness of their operations set them on a collision course with reality. As LockBit expanded, they increasingly found themselves in a precarious position, justifying breaches of their own ethical guidelines. These rationalizations and excuses for rule-breaking were a sign of the strain between their public image and the rogue actions of their affiliates.
As LockBit’s narrative unfolded, it became clear that their rapid ascent was powered by more than just technical prowess; it was fueled by a distorted view of their role in the cyber world—a view that ultimately led to their undoing. They rode fast, grew bold, and as they bent their own rules, they hit the wall they had built around themselves.
Behind the Curtain: LockBit’s Leaked Backend Data
The unveiling of LockBit’s backend data provided a rare glimpse into the inner workings of a top-tier ransomware syndicate. The leak, a direct result of Operation Cronos, revealed intricate details of LockBit’s operations, showcasing how they orchestrated their ransomware campaigns with chilling efficiency.
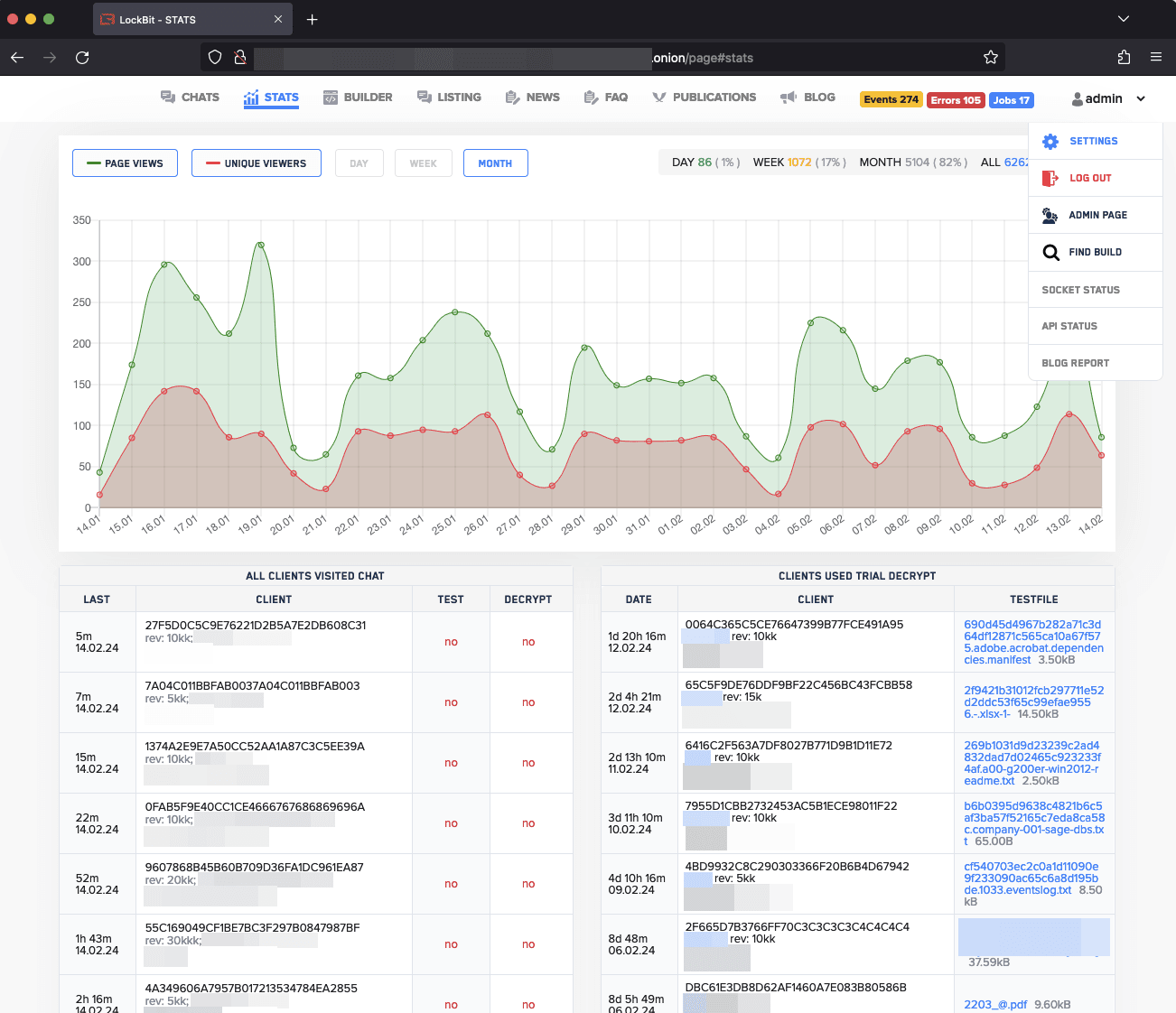
Leaked screenshots from their system reveal a sophisticated tracking dashboard, complete with stats on page views, chat interactions, and a breakdown of victim negotiations. It’s a window into a perverse kind of customer service, where victims are managed with the same attention to detail as a corporate sales team would monitor leads.
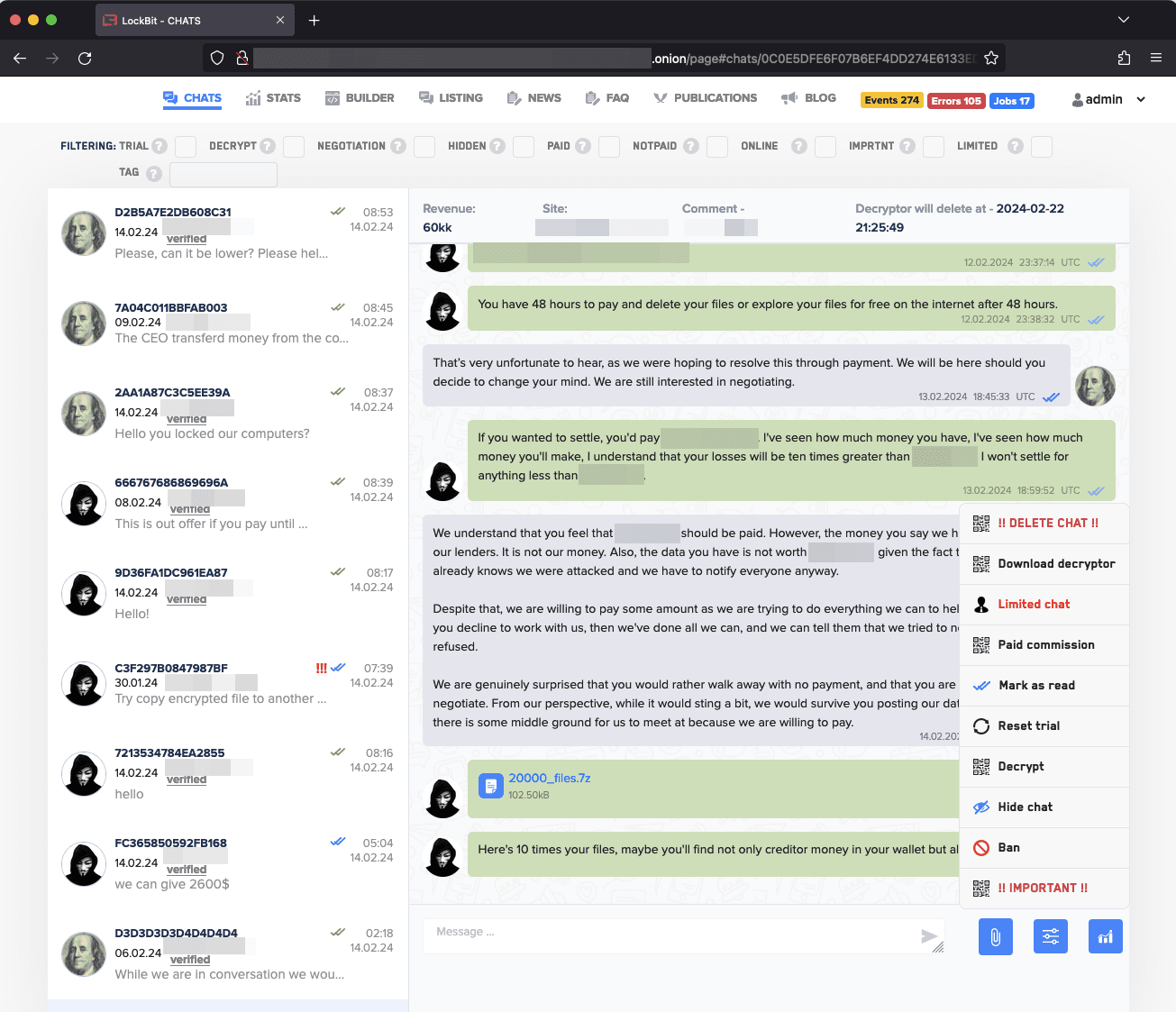
These insights into LockBit’s backend are revelatory, exposing the extent of their operational reach. From stats that chart the growth of their campaigns to chat logs that betray their negotiation tactics, we see a group that had monetized every aspect of the ransomware process. They commodified fear and weaponized vulnerabilities, turning network intrusions into a transactional art.
The leak also uncovered a builder tool, evidence of the ransomware-as-a-service model that LockBit leveraged. With options for customization and deployment, it’s clear that LockBit provided a one-stop-shop for affiliates to tailor their attacks, underscoring the syndicate’s role as a facilitator of widespread cyber disruption.
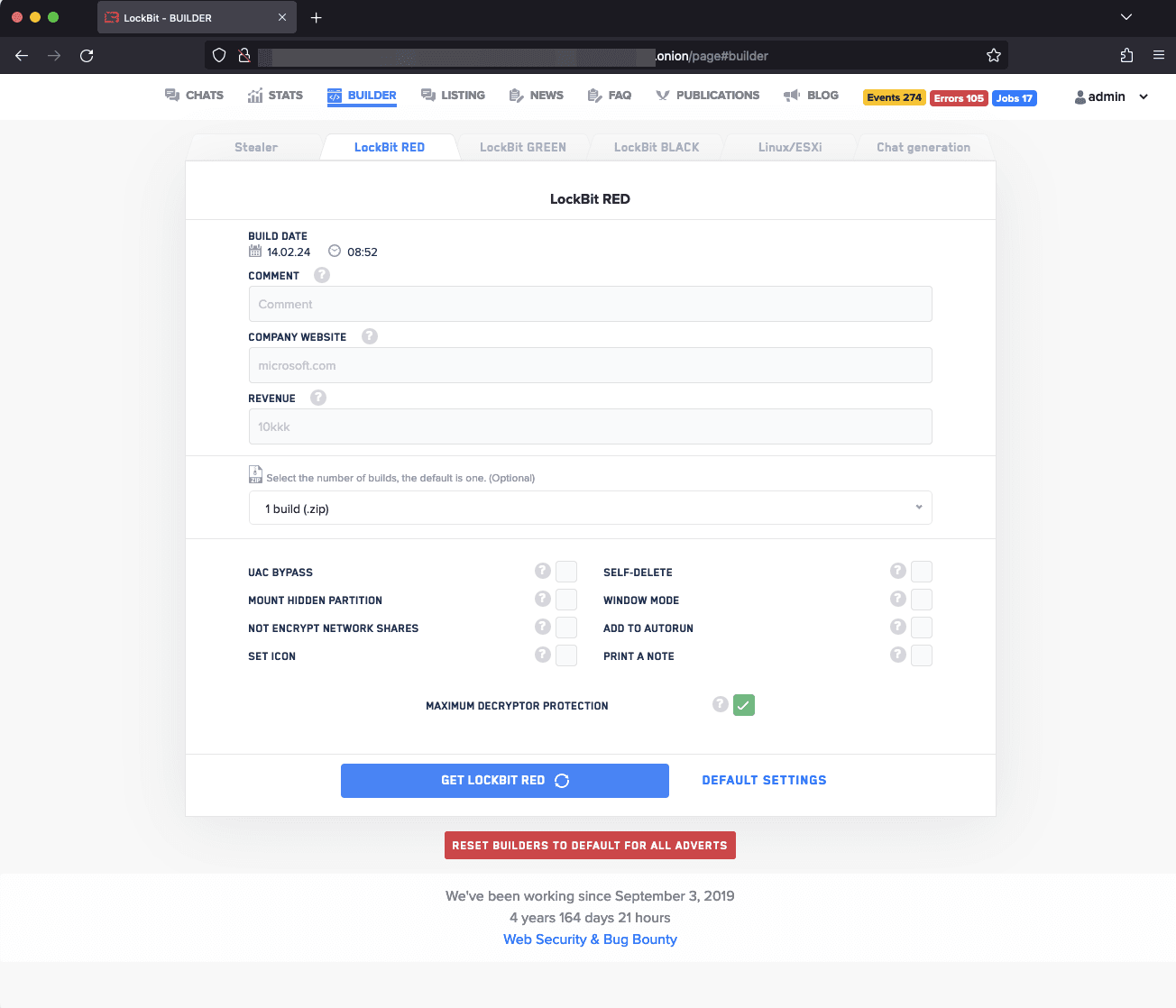
This treasure trove of leaked data doesn’t just illuminate the past; it provides a roadmap for preventing future attacks. By understanding the strategies and tools used by LockBit, cybersecurity professionals can better anticipate and mitigate the methods employed by ransomware groups. The LockBit leak is a sobering reminder of the cyber threat landscape’s complexity and the need for continued vigilance.
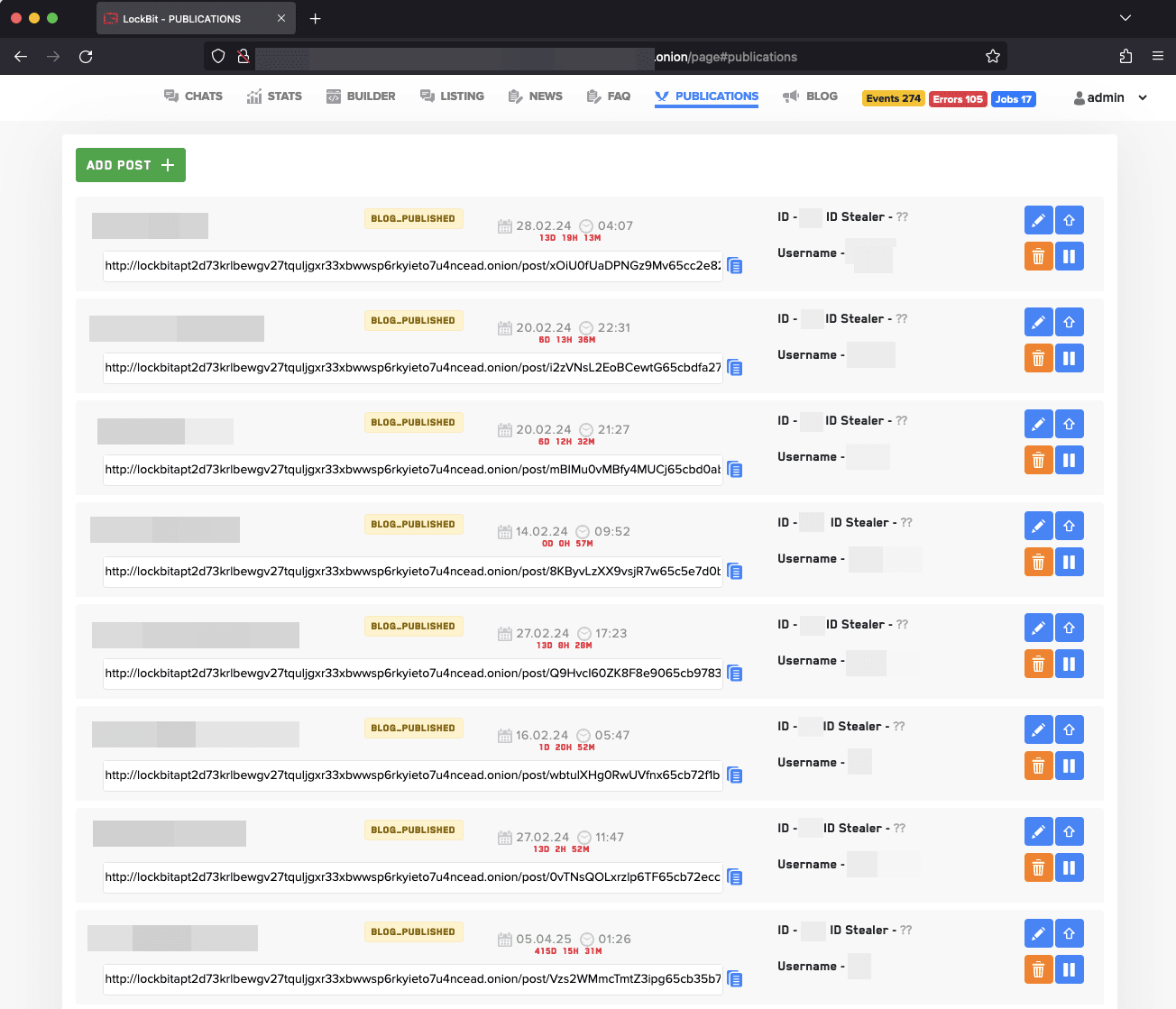
In a sweeping move that ratchets up the pressure on the ransomware cybercrime ecosystem, law enforcement agencies have laid bare the sprawling network of LockBit’s operation by publishing the names of 187 affiliates. This unprecedented reveal not only spotlights LockBit’s vast reach but is poised to send shockwaves through the underbelly of cybercrime. Unmasking these affiliates, integral cogs in LockBit’s formidable operation, serves as a warning: anonymity in the digital age is a fragile veil. As this list circulates, it’s not just a roster but a harbinger of heightened risk for those involved, significantly upping the ante for anyone daring to fill the void left by LockBit’s dramatic takedown.
In a revealing development, a Twitter account has surfaced with purported communications from the cornered ransomware collective, LockBit. They’ve reportedly admitted to a lapse in their cyber defenses — specifically, an outdated PHP server. Despite the heavy hit from the FBI, they insist that their repository of stolen data remains untapped, suggesting plans to resurface and share details through a new blog. This candid admission from LockBit suggests they’re down but not out, hinting at their tenacious grip on the dark web’s undercurrents.
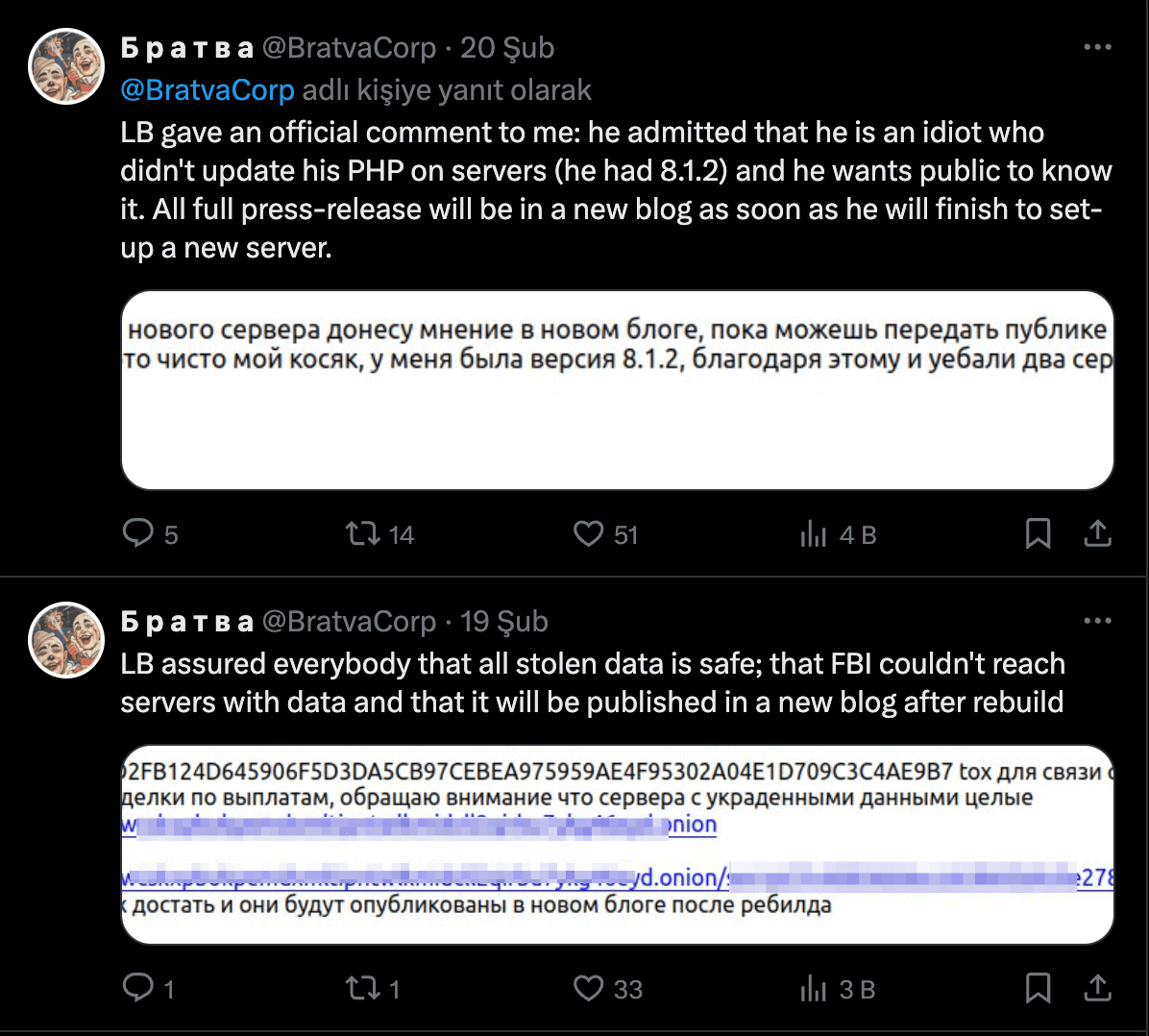
Amid the fallout from Operation Cronos, our team at BRITE has noted a curious anomaly: a handful of LockBit’s mirror servers are still online. Yet, they stand oddly silent — no new victims announced, no fresh proclamations from the group. This peculiar inactivity suggests that while the servers hum along, LockBit’s operators might be cut off from their own infrastructure or lack the necessary resources to wield it. It paints a picture of a once-formidable ransomware titan now potentially stranded from its tools of terror.
Adding to the LockBit exposé, recent disclosures by law enforcement offer a counter-narrative to the group’s bold claims. Authorities have revealed their access to the supposedly secure stolen data, even for those who succumbed to paying ransoms. This new information challenges LockBit’s narrative of data security post-ransom and debunks a commonly held fallacy within ransomware circles — that payment ensures data safety. For victims and the cybersecurity community, this serves as a potent reminder of the unreliable nature of ransomware operators’ assurances.
The LockBit Aftermath: Repercussions in a Shaken Cybercrime Arena
The aftermath of Operation Cronos is a seismic shift in the cybercrime landscape. A colossal operation has led to the seizure of 34 critical servers that facilitated LockBit’s nefarious activities, two key actors behind bars, and a total of 200 cryptocurrency accounts frozen. Law enforcement didn’t stop there; they’ve closed down 14,000 rogue accounts connected to infrastructure or data exfiltration efforts, further crippling LockBit’s operational capabilities.
As for LockBit’s recovery, the odds seem stacked against it. They’ve suffered a substantial loss of resources and, perhaps more crucially, their reputation within the dark web ecosystem. Affiliates, already spooked by the crackdown, may likely scatter, wary of attracting the law’s gaze.
Reflecting on my earlier prediction, the disintegration or diminishment of a major ransomware entity like LockBit was anticipated, with the expectation that 2024 would see either significant takedowns or a dissolving into smaller factions. This fragmentation could result in more stealthy, low-key operations, aiming to fly under the radar of increasingly effective law enforcement.
For the victims, this operation isn’t just a crackdown—it’s a beacon of hope. Decryption tools released in the operation’s wake signal a turning tide, offering a lifeline for those ensnared by LockBit’s malicious campaigns. Agencies leveraging LockBit’s very own communication channels to reach out shows an innovative approach, bridging the gap between victims and the resources they desperately need.
Who will fill the void? It’s an open market now. Groups like AlphV, Cl0p, Play, Akira, Cactus, and Rhysida are climbing the ranks, but none exhibit LockBit’s dominance. AlpV is a wounded lion. Cl0p might adopt a more sporadic but impactful approach, striking fewer but more significant blows. The landscape is primed for a new leader, but with law enforcement’s aggressive stance, aspiring contenders are forewarned – the risks have never been higher.

As the landscape shifts, a new kind of cyber warfare unfolds—one where the agility of smaller groups could challenge the established hierarchies. This evolution will test the waters of cyber professionalism and technical prowess, as emerging groups vie for dominance and attempt to outpace giants like LockBit in both execution speed and technical sophistication.
Is ransomware still a threat? Absolutely. But this takedown is a spectacular lesson. It emphasizes that while the threat persists, so does the resolve of global law enforcement. As predicted in a previous article, a major ransomware group’s downfall was imminent. The dominoes have begun to fall, and it’s a reminder to all cybercriminals: their actions are not without consequences, and they could be next.
Final Words
As the dust settles on Operation Cronos, the LockBit saga shows a reality in the digital age: even the mightiest can fall. Law enforcement’s global collaboration and innovative tactics are proving to be effective deterrents, chipping away at the once-impenetrable veneer of ransomware syndicates.
For the cyber underworld, it’s a jarring wake-up call. The operation serves as a testament to the resilience and reach of global law enforcement, and a reminder that in the interconnected world of cybercrime, anonymity is no longer an impenetrable shield.
The victims of these attacks now have a glimmer of restitution and perhaps a slightly less treacherous digital landscape. With decryption tools made available and support systems in place, there is a path to recovery and a chance to bolster defenses against future threats.
Ransomware remains a formidable challenge, but the narrative is changing. The landscape is shifting away from the dominance of a few to a dispersed battleground, where the response of law enforcement will need to be as dynamic and adaptable as the threats they face.
The prediction of a ransomware group’s fall has come to pass, setting a precedent for the future. As we look ahead, it’s clear: adaptability, vigilance, and international cooperation are the new watchwords in the fight against cybercrime.
Updated [February 21, 2024]: List of affiliates, Lockbit’s statements after the operation, Lockbit’s operational websites.
THE BLACK KITE CYBER VILLAINS & THREAT ACTORS DOSSIER
Learn about the threat actors that are still out there. Learn More