Patched your network recently? The growing risk on IT Vendors
Published
Nov 17, 2020
Updated
Jan 27, 2026
Authors
Black Kite
The onset of the pandemic has led to a massive surge in hacking activities. With much of the work still being done on personal laptops and residential internet connections, hackers saw a goldmine to take advantage of this new working model and inflict greater damage to organizations through vulnerable devices and software. CISA’s recent advisory is particularly pointing to state-sponsored malicious activity, targeting U.S. national security systems, U.S. Defense Industrial Base (DIB), and Department of Defense (DoD) information networks exploiting known vulnerabilities. Whether they are national systems, defense industry, or any other critical sector, it is of paramount importance that network defenders prioritize patching and mitigation efforts.
The US Cybersecurity and Infrastructure Protection Agency (CISA) recently published a list of vulnerabilities in which Chinese state-sponsored hackers have either been searching for or leveraging in attacks. CISA declared the Chinese Ministry of State Security (MSS)-affiliated cyber threat actors use publicly available information sources and common, well-known tactics, techniques, and procedures (TTPs) to target U.S. Government agencies.
The same tools and techniques for any sophisticated cyber actor to organize the exploitation of a computer system is used by these state-sponsored hackers. They first identify a target, collect technical data, vulnerabilities on the target, create or reuse an exploit for those vulnerabilities, and then launch their exploits.
Some of the vulnerabilities from CISA’s list are as follows:
- CVE-2019-11510 – affects Pulse Secure VPNs
- CVE-2020-5902 – affects F5 BIG-IP proxy/load balancer devices
- CVE-2019-0708- affects Microsoft Windows 11 XP – 7, Microsoft Windows Server 12 2003 – 2008
- CVE-2019-19781 – affects Citrix Application Delivery Controller (ADC) and Gateway
- CVE-2020-8193, CVE-2020-8195, CVE-2020-8196 – affect Citrix ADC & Citrix Gateway & Citrix SDWAN WAN-OP
- CVE-2019-0708 – affects Microsoft Windows and Microsoft Windows Server Remote Desktop Services
- CVE-2020-15505 – affects MobileIron mobile device management (MDM)
- CVE-2020-1350 – affects Windows (Domain Name System) Server
- CVE-2020-1472 – affects Microsoft Windows Server
- CVE-2019-1040 – affects Microsoft Windows and Microsoft Windows Server
- CVE-2018-6789 – affects Exim mail transfer agent
- CVE-2020-0688 – affects Microsoft Exchange Server
- CVE-2018-4939 – affects Adobe ColdFusion
- CVE-2015-4852 – affects Oracle WebLogic Server
- CVE-2019-3396 – affects Atlassian Confluence
In a recent report [1], CISA claims that hackers leverage open source platforms as an initial vector in crafting their attacks, such as Shodan, NIST Vulnerability Database, and other CVE sources. Tools like Mimikatz and Cobalt Strike are also often utilized to exfiltrate sensitive information from the attacked systems.
“Cyber threat actors also continue to identify large repositories of credentials that are available on the internet to enable brute-force attacks,” the agency said. “While this sort of activity is not a direct result of the exploitation of emergent vulnerabilities, it demonstrates that cyber threat actors can effectively use available open-source information to accomplish their goals.”
With this rising trend of CVEs on third-party IT vendors, let’s now take a look at some of the most exploited vulnerabilities:
CVE-2019-11510: Pulse Secure VPN
VPNs have been critical for controlling access to critical organizational assets and have increased in importance with the onset of the pandemic. Pulse Secure VPN disclosed the CVE-2019-11510 vulnerability and provided software patches for the various affected products in April of 2019. Wide exploitation of CVE-2019-11510 is still observed in 2020 and even today. As of August 2020, Bad Packets identifies over 14,500 vulnerable VPN servers globally still unpatched and in need of an upgrade. [2]
Today, a Shodan search revealed 491 vulnerable Pulse Secure devices worldwide.
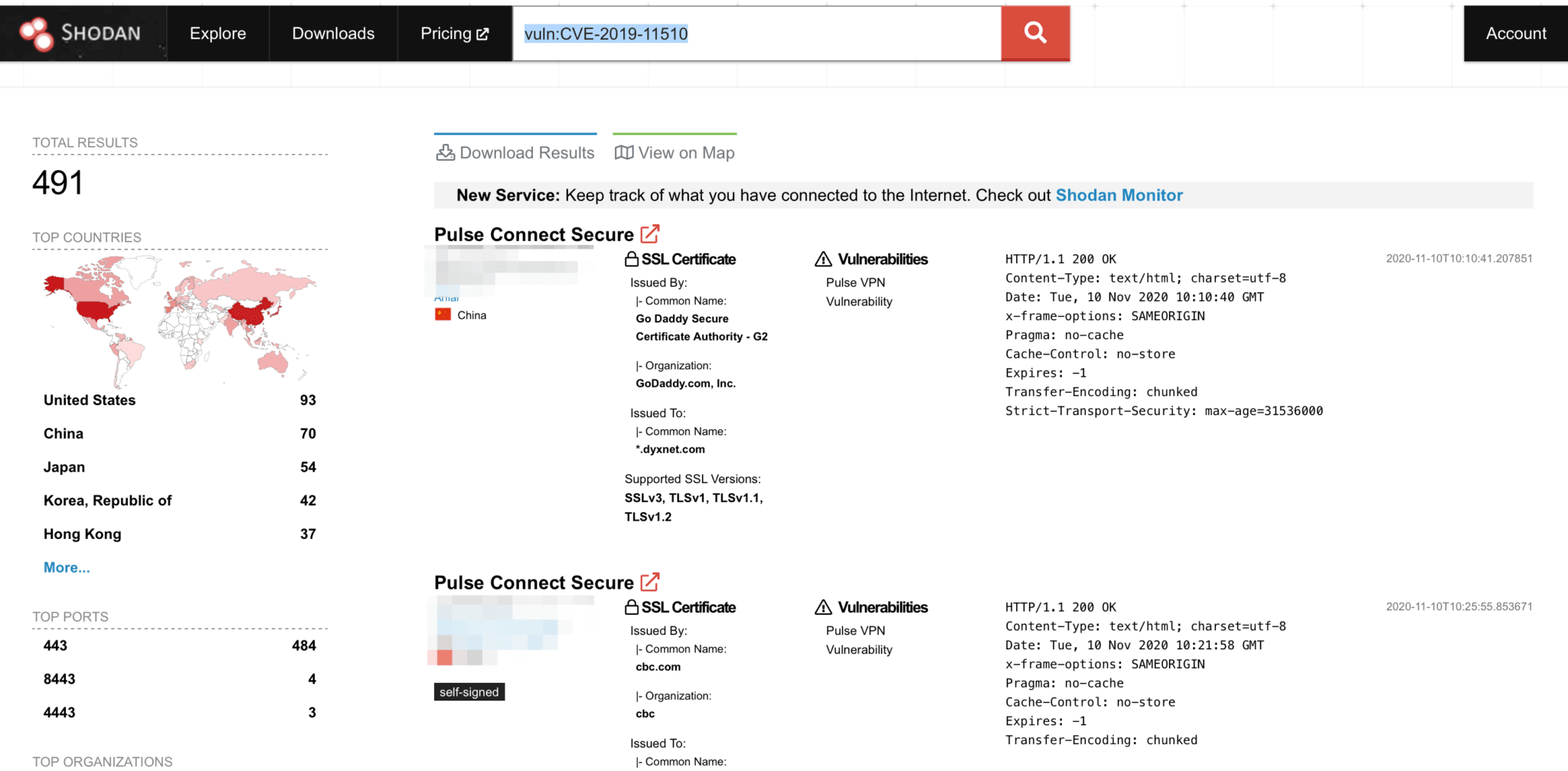
Shodan offers many filters to perform a selective search. For example, you can perform a search with custom filters such as IP, Netblock, Server type, Service type, Ports, Banner, and even vulnerability codes.
Having a CVSS score of 10, this CVE allows an unauthenticated remote attacker to send a specially crafted URI to perform an arbitrary file reading vulnerability. Using this method, the attacker can obtain usernames and plaintext passwords from vulnerable endpoints.
A popular exploiter for Pulse Secure VPNs on GitHub traverses the target’s directories for vulnerable Pulse Secure devices and downloads etc/password file as seen below.
![The screenshot of Pulse Secure VPN exploit from Github. [3]](/_next/image?url=%2Fapi%2Fmedia%2Ffile%2Fpatched%2520iamge%25202-1642x1076.png&w=3840&q=85)
The screenshot of Pulse Secure VPN exploit from Github. [3]
CISA carried out several incident response engagements at Federal Government and commercial entities, where CVE-2019-11510 was exploited. Although Pulse Secure released patches for CVE-2019-11510 in April 2019, CISA observed incidents where compromised Active Directory credentials were used months after the victim organization patched their VPN appliance.
Per the provider, they are deployed across 80 percent of the Fortune 500 and used by 20 million endpoints, as Pulse Secure is one of the industry leaders in providing secure access.
CVE-2020-5902: F5 BigIP
This is a vulnerability In F5’s Big-IP Traffic Management User Interface (TMUI). The BIG-IP Local Traffic Manager allows controlling the network traffic by selecting the correct destination based on server performance, security, and accessibility.
F5 released a critical Remote Code Execution vulnerability (CVE-2020-5902) on June 30th, 2020 that affects several versions of F5. With this vulnerability, cyber threat actors can execute arbitrary commands, build or delete files, disable services, and/or run Java code. The vulnerability received a CVSSv3 rating of 10.0, the highest possible score.
When network access to the TMUI is exposed through the BIG-IP management port or Self IPs, the vulnerability is easy to exploit. Successful exploitation of this flaw would provide a variety of advantages to an attacker, including the ability to execute arbitrary system commands or Java code, create or delete files, as well as disable vulnerable host services. The advisory states that the vulnerability could “result in full system compromise” as well.
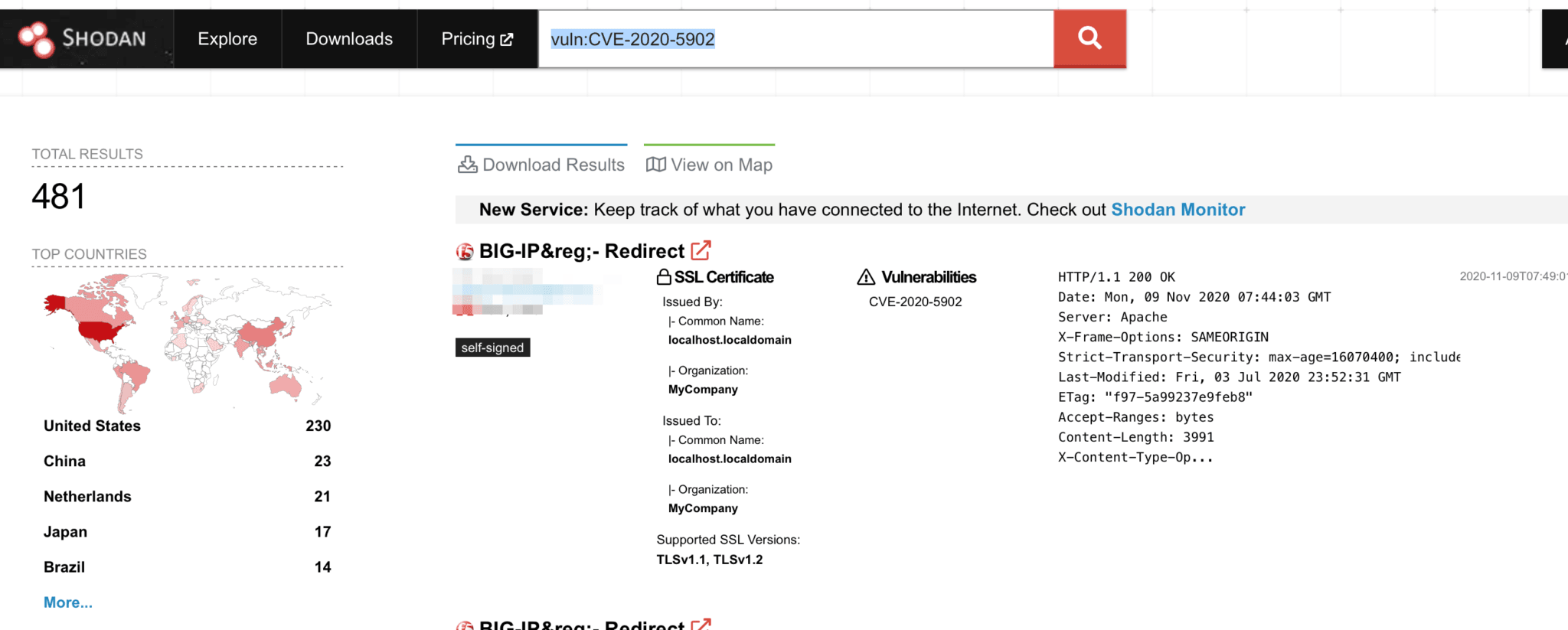
A Shodan search reveals 481 vulnerable F5 BigIP devices today, still.
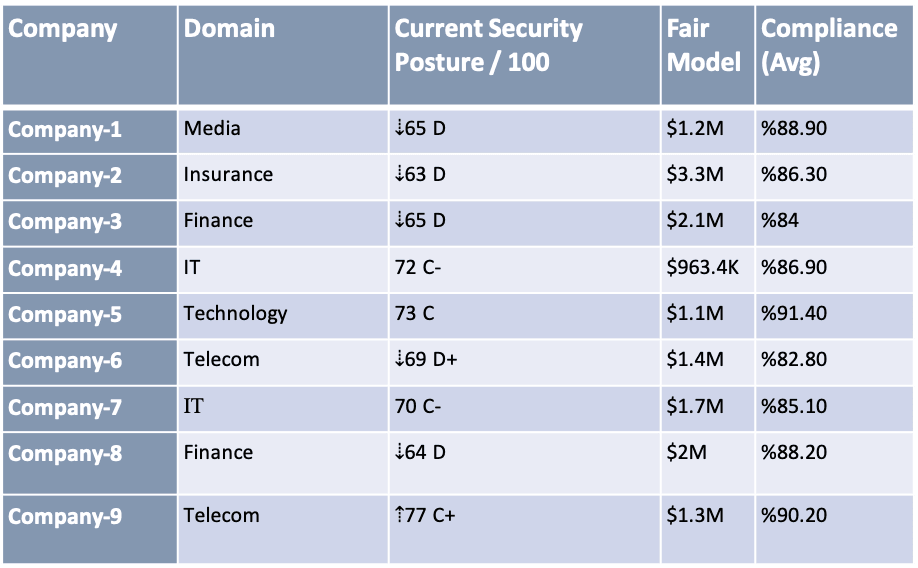
Black Kite also identified this particular vulnerability on numerous entities on its platform. The vulnerability spans different sectors including some large companies in Telecom, Finance, Insurance, and Technology. The vulnerable entities are listed with their overall Cyber Rating, Financial Impact Rating, and Compliance Estimation scores.
The advisory states [1], the best practice to mitigate the attack is to disable the external interface of the management port and configure an out-of-band management network.
CVE-2019-0708: Microsoft Remote Desktop Services
Although this CVE was released in May 2019 by Microsoft, vulnerable devices still exist and are among the commonly exploited vulnerabilities by state-sponsored hackers.
Using this vulnerability, an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests. It can be leveraged in pre-authentication, and thus requires no user interaction. An attacker who successfully exploited this vulnerability could execute arbitrary code on the target system, for example, install programs; view, change, or delete data; or create new accounts with full user rights.
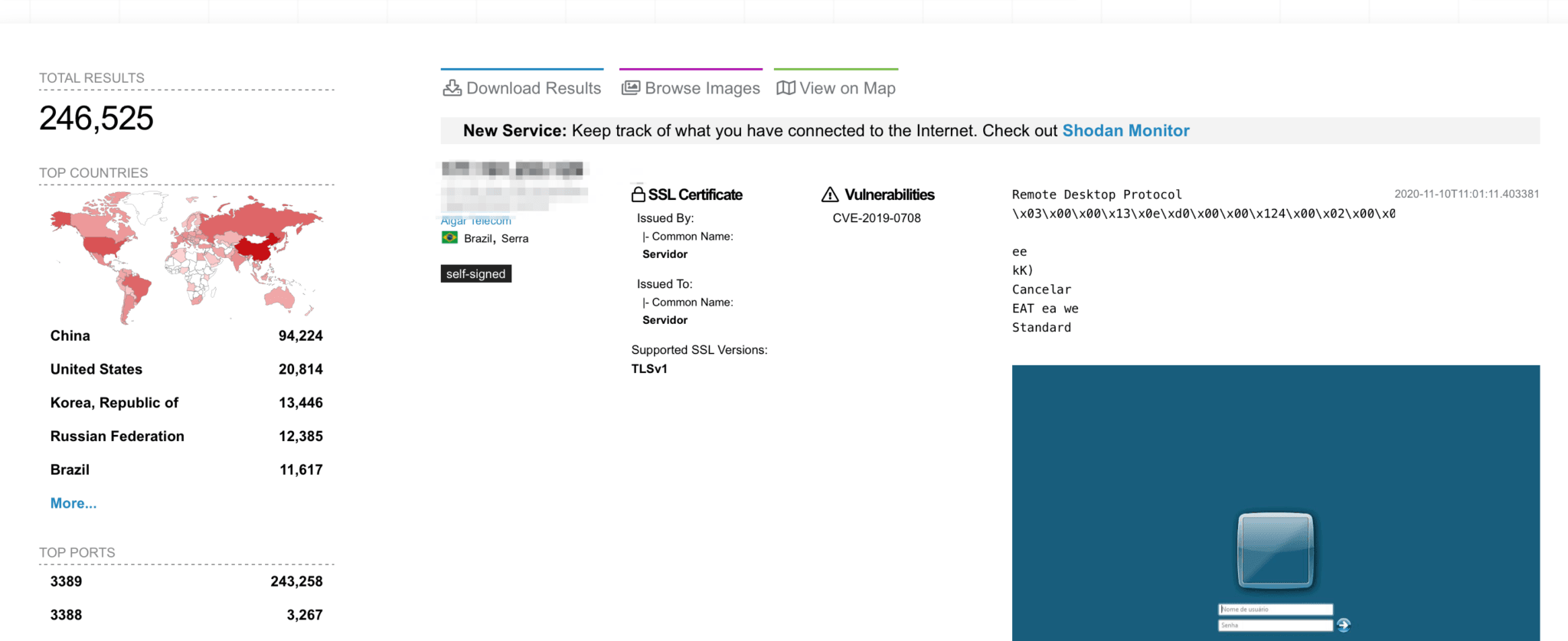
A Shodan search yields 246,525 CVE-2019-0708 vulnerable devices worldwide, with 20,814 of them deployed in the U.S.
The vulnerability affects Microsoft Windows®11 XP – 7, and unpatched versions of Microsoft Windows Server®12 2003 – 2008.
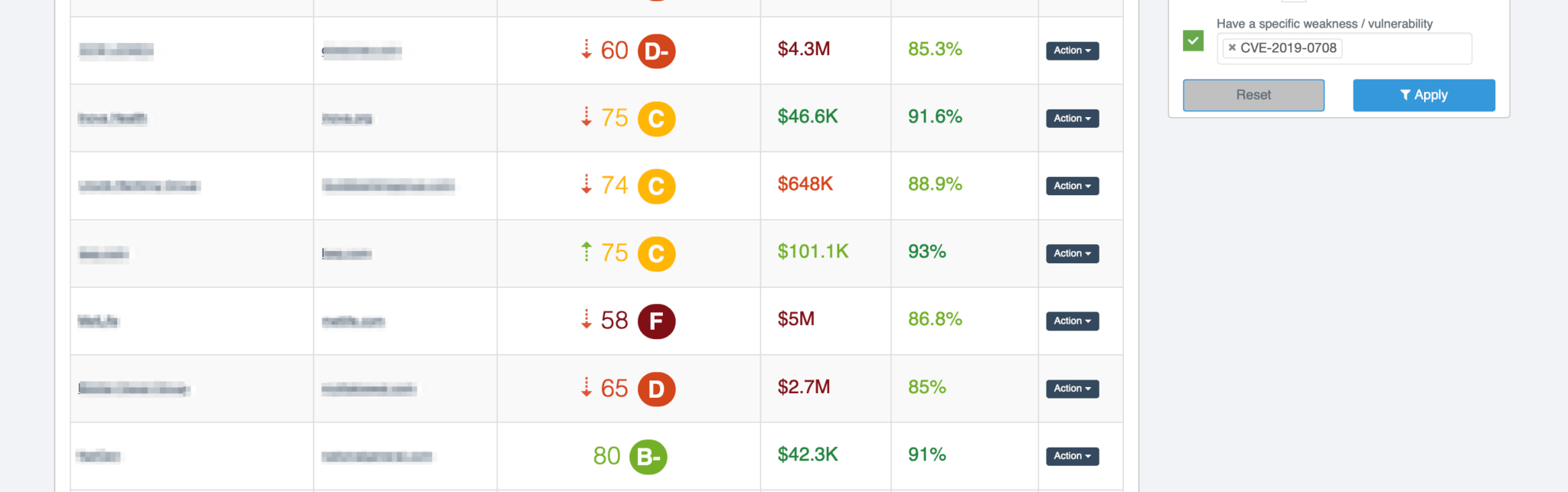
A Black Kite search would yield the CVE-2019-0708- vulnerable third parties in your ecosystem.
Mitigations
If patching is not possible, the risk of exploitation can be lowered by implementing mitigations provided by the vendors. Some of the mitigation options are:
- Disable external management ports and setting up an out-of-band management network.
- Disable unused and unneeded services as a best practice. Disabling will help reduce your exposure to security vulnerabilities.
- Enable Network Level Authentication (NLA) on systems running supported editions of Windows 7, Windows Server 2008, and Windows Server 2008 R2.
- Encapsulate Internet-facing services in a network DMZ. This will reduce the exposure of the internal network and eventually sensitive data.
- Increase employee-awareness to limit the damage or altogether prevent the attacks at preliminary stages.
How to practice effective patch management within your organization and with your third parties
Hundreds of vulnerabilities are published each month. Within this sea of bugs, CVE codes, severities, patches, and workarounds, IT teams become overwhelmed and miss critical updates.
Insufficient resource management as a result of a lack of risk prioritization also causes problems. As with any cyber risk-related issue, teams do not find themselves comfortable with risk prioritization and have difficulty in tying vulnerabilities/bugs to the risk management process.
However, an effective patch management process requires a combination of automation and best practices. Manual patch management can be inefficient for a secure system. Black Kite collects details related to the version number of your system and software from an internet-wide scanner.
The details are then converted into the corresponding common platform enumeration, and correlated with NIST NVD and MITRE CVSS databases to detect any unmitigated known vulnerabilities.
Black Kite ties each and every vulnerability inherent on a digital asset to cyber risk management using:
- Black Kite Technical report where each finding contributes to the overall risk score.
- Financial Impact Rating where each finding feeds the financial-cyber risk.
- Compliance Module where the findings correlate with the control items of regulations, standards, and best practices such as NIST 800-53, NIST CSF, HIPAA, GDPR, PCI-DSS, etc.
Whether it’s your organizational assets or third parties’ assets, you receive alerts and are informed about the most recent vulnerabilities in your ecosystem along with their level of severity. You can engage your third parties to the Black Kite platform or communicate through the Cyber Rating and Strategy Reports to help fix their vulnerabilities and eventually increase their security posture.
You can also use the filtering options to search for specific (and even old) vulnerabilities that your organization’s or third parties’ assets are prone to.
See our Automated Continuous Cyber Risk Monitoring tool to get more informed of what we can do for you.
References
[1] https://media.defense.gov/2020/Oct/20/2002519884/-1/-1/0/CSA_CHINESE_EXPLOIT_VULNERABILITIES_UOO179811.PDF
[2] https://us-cert.cisa.gov/ncas/alerts/aa20-010a
[3] https://github.com/projectzeroindia/CVE-2019-11510