Have you patched your holes? 6 Simple Things for Patch Management
Published
Jun 29, 2018
Updated
Jan 27, 2026
Authors
Black Kite
A vulnerability is a hole or a weakness in an application. It can be a design flaw or a bug. Attackers exploit vulnerabilities to harm the application owner, application users, and other entities that rely on the application. Patch management is the process of software updates to eliminate vulnerabilities or mitigate cyber risk caused by them. Sounds simple, but it is not the case, especially for large enterprises.
What is the cyber risk?
If the software and applications are not patched in a timely manner, malwares and ransomwares can create vital damage on a company’s system or data can be stolen for ransom. Spectre and Meltdown, worldwide attacks, exploited vulnerabilities in modern processors and leaked large amount of passwords and sensitive data in 2017. Similarly, ransomwares such as WannaCry and Petya in 2016 forced large enterprises to pay ransom by exploiting certain vulnerabilities in software that were not updated with available patches.
How can a hacker see your vulnerabilities?
A company’s digital footprint gives many information to outside world including what versions of web applications are in use in the company. Known vulnerabilities are listed in public databases and beginner to average hackers can combine these information to tailor a cyber attack by exploiting vulnerabilities.
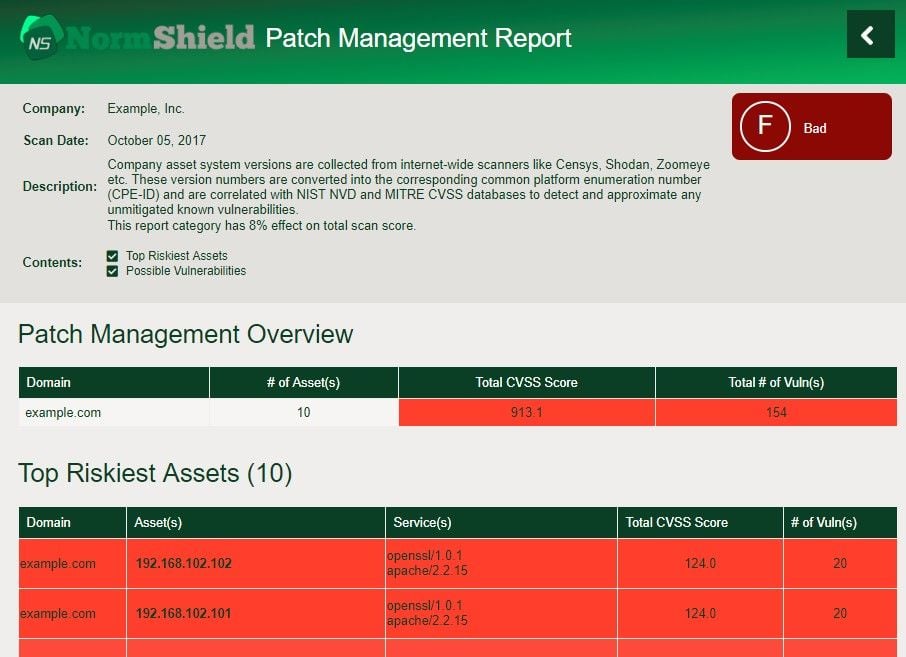
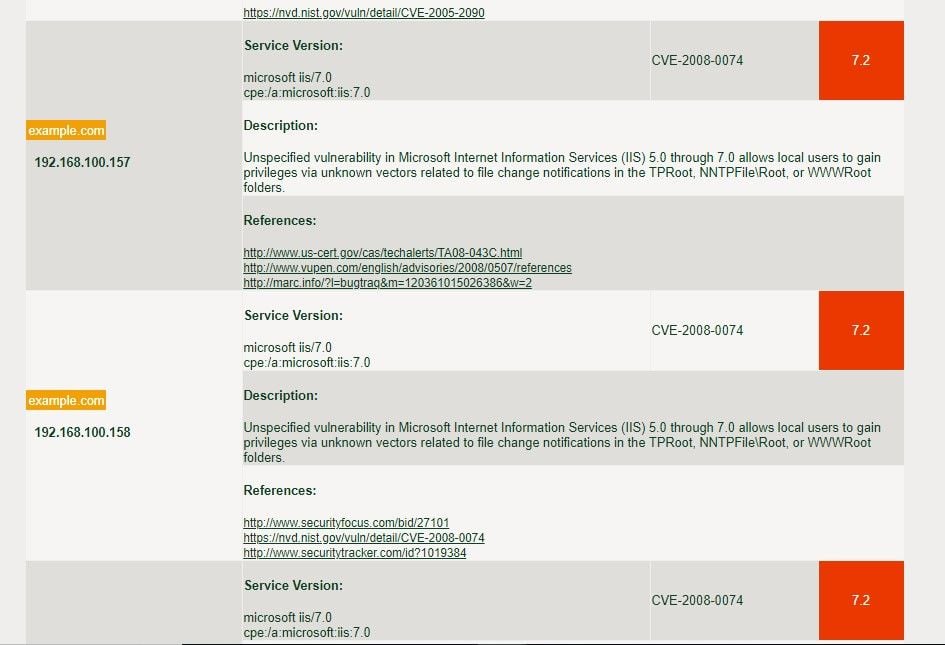
Black Kite scanned web applications and network systems against a database of thousands of known vulnerabilities and ranked them in order of severity. Black Kite recently conducted a survey, which reviews trends and insights from Cyber Risk Scorecard key data points that include detailed external security risk data from cyber risk scoring for 5,217 organizations across multiple industries and over one million active assets on the Internet, including web and network devices. The survey shows that most common & critical vulnerabilities found are;
- Misconfiguration
- Denial of Service (DoS)
- Information Exposure
Another statistics that the survey serves us is that more than 10% of the companies had at least one critical issue in web or network assets and most had web servers and applications that were 5+ years old, with unpatched vulnerabilities (for more information download Black Kite Cyber Security Risk Brief 2018).
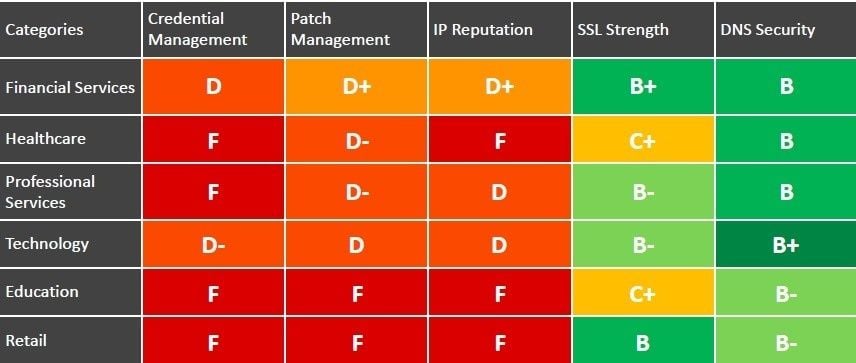
Which industry is the worst?
In general, most of industries perform very poorly in patch management. Black Kite Cyber Risk Scorecard provides easy-to-understand letter grades for 20 categories (including Patch Management) and the table below shows average grades for different industrial categories. In the sense of patch management, Companies in Education and Retail have the highest risk while companies in finance receive D+, a grade which shows that beginner-to-average hackers can practice their skills.
6 Simple Steps for Patch Management
- Tracked your assets. Most companies don’t know what they own.
- Identify the criticality of the assets in the organization and each system owner
- Make a list of all security controls and configurations – routers, firewalls, IDSes, AV…
- Establish the frequency of vulnerability scanning; compare your report against inventory/control list
- Classify risks based on the likelihood of an attack
- Monitor/scan public-facing systems for known vulnerabilities and patch them.
Black Kite’s non-intrusive Cyber Risk Scorecard can discover all the assets of a company by using only its domain name, determine the system versions run on your assets from internet-wide scanners, scan them against thousands of known vulnerabilities and rank them in order of severity.
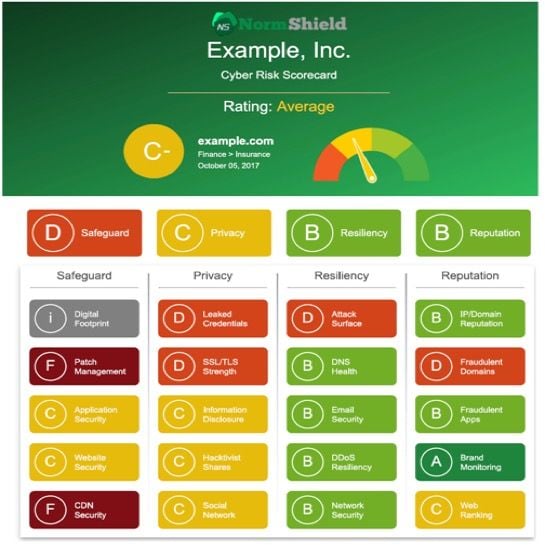
To act now and learn your cyber risk score on Patch Management among other categories, visit www.blackkite.com/resources