FOCUS FRIDAY: TPRM INSIGHTS ON CRITICAL CITRIX BLEED 2 AND WING FTP SERVER VULNERABILITIES
Welcome to this week’s Focus Friday, where we examine two high-priority vulnerabilities from a Third-Party Risk Management (TPRM) standpoint. Today, we’ll dive into CVE-2025-5777—better known as Citrix Bleed 2—and the devastating RCE flaw CVE-2025-47812 in Wing FTP Server. Both issues carry extreme severity and real-world exploit potential, making it imperative for TPRM teams to quickly identify which suppliers are exposed, understand the operational impact, and ask the right questions to drive swift remediation.
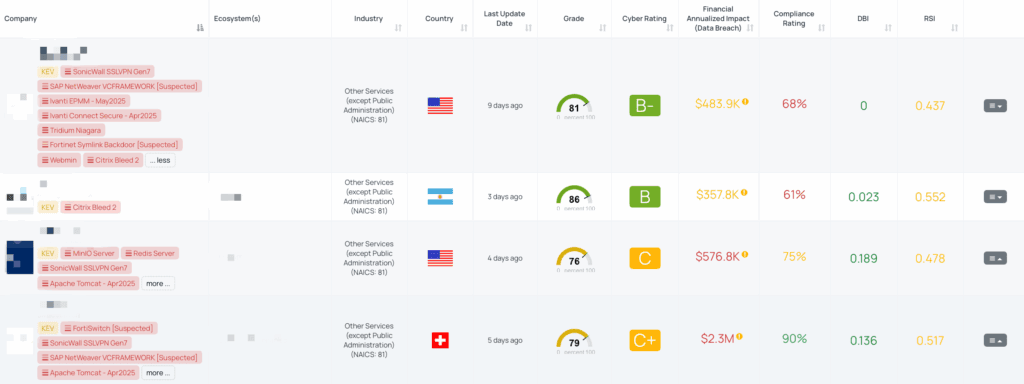
Filtered view of companies with Citrix Bleed 2 FocusTag™ on the Black Kite platform.
CVE-2025-5777 IN CITRIX NETSCALER ADC & GATEWAY
What is the Citrix Bleed 2 Out-of-Bounds Read Vulnerability?
CVE-2025-5777, dubbed Citrix Bleed 2, is a critical insufficient-input-validation flaw in NetScaler ADC and Gateway appliances when configured as VPN/ICA/CVPN/RDP proxies or AAA servers. A maliciously crafted request can trigger an out-of-bounds memory read, leaking session tokens and other sensitive data from device memory. It carries a CVSS 4.0 base score of 9.3 and an EPSS probability of 0.06%, and was publicly disclosed on June 17, 2025.
Beyond simple memory leakage, this flaw specifically targets session tokens—often used for APIs and persistent authentication—enabling attackers to bypass MFA and maintain access even after valid users log off reliaquest.com.
Why the name “Citrix Bleed 2”?
Security researcher Kevin Beaumont likened CVE-2025-5777 to the original “Citrix Bleed” (CVE-2023-4966) because both vulnerabilities expose session data from memory, facilitating session hijacking and MFA bypass.
Evidence of active exploitation
- ReliaQuest reported “indications of exploitation” with medium confidence as of June 26, 2025 reliaquest.com.
- A CSO Online article on June 30, 2025 confirmed in-the-wild use, warning of session hijacking and MFA bypass and urging immediate mitigation csoonline.com.
CVE-2025-5777 is not currently listed in CISA’s KEV catalog. However, its sibling memory-overflow flaw (CVE-2025-6543) was added on June 30, 2025—underscoring the rapid weaponization of NetScaler vulnerabilities.
What about the related memory-overflow and improper-access-control flaws?
- CVE-2025-6543 is a buffer-overflow in the packet parser that can cause Denial of Service or arbitrary code execution. Rated CRITICAL with a CVSS 3.1 score of 9.8 and an EPSS of 16.13%, it was published on June 25, 2025, and has confirmed in-the-wild exploitation.
- CVE-2025-5349 is an improper-access-control issue in the NetScaler Management Interface, allowing network-accessible attackers to invoke privileged operations without authorization. Rated HIGH with a CVSS 4.0 score of 8.7 and an EPSS of 0.04%, it was published on June 17, 2025, with no known public exploitation.
Why should TPRM professionals care?
NetScaler ADC & Gateway appliances often serve as the front door to corporate networks. CVE-2025-5777 can:
- Hijack authenticated sessions by stealing session tokens and bypassing MFA.
- Expose credentials/tokens, enabling lateral movement and persistent access.
- Disrupt service availability, undermining business continuity and SLAs.
Overlooking vendor exposure to Citrix Bleed 2 puts data flows, operational uptime, and regulatory compliance at risk.
What questions should TPRM professionals ask vendors about CVE-2025-5777, CVE-2025-6543, CVE-2025-5349?
To assess the risk posed by CVE-2025-4981 in your supply chain, consider asking vendors the following questions:
- Have you updated all instances of NetScaler ADC & Gateway to versions 14.1-47.46, 13.1-59.19, or 13.1-37.236-FIPS/NDcPP to mitigate the risk of CVE-2025-6543, CVE-2025-5777, and CVE-2025-5349?
- Can you confirm if you have implemented monitoring for anomalous buffer-overflow signatures, unexpected read errors, or unauthorized API calls to management endpoints as recommended in the advisory for CVE-2025-6543, CVE-2025-5777, and CVE-2025-5349?
- Have you restricted network exposure by limiting access to VPN, AAA, and management interfaces to trusted IPs only as a measure to prevent exploitation of CVE-2025-6543, CVE-2025-5777, and CVE-2025-5349?
- Can you confirm if you have applied BOD 22-01 guidance for any cloud-hosted NetScaler instances to mitigate the risk of CVE-2025-6543, CVE-2025-5777, and CVE-2025-5349?
Remediation recommendations for vendors subject to this risk
To address all three Citrix NetScaler ADC & Gateway flaws (CVE-2025-5777, CVE-2025-6543, CVE-2025-5349), vendors should implement the following controls:
- Apply all vendor patches immediately:
CVE-2025-5777 (Citrix Bleed 2): Install the June 17 2025 releases (14.1-47.46+, 13.1-59.19+, or 13.1-37.236-FIPS/NDcPP+).
CVE-2025-6543 (buffer overflow DoS/RCE): Install the June 25 2025 releases (same build numbers as above for each line).
CVE-2025-5349 (improper access control): Install the June 17 2025 Management Interface fixes. - Restrict network exposure:
Limit access to VPN/ICA/CVPN proxy and AAA endpoints to trusted management networks or jump-box hosts only.
Enforce IP-whitelisting or VPN-only access for NSIP, Cluster IP, GSLB site IP and the management interface. - Terminate and rotate active sessions:
After patching, terminate all active ICA, PCoIP, and AAA sessions to purge any hijacked tokens.
Force session re-authentication and consider rotating any shared credentials or API tokens used by NetScaler scripts. - Enable and fine-tune logging & alerting:
Monitor for anomalous buffer-overflow or memory-read signatures (e.g. unexpected packet parser errors).
Alert on unauthorized or unusually timed management API calls and privileged-operation invocations. - Audit and harden configurations:
Conduct an external exposure scan (e.g. Shodan) to identify any publicly reachable NetScaler endpoints.
Apply strict ACLs and disable any unused virtual servers or services (e.g. unused AAA or Gateway vservers). - Follow federal/cloud guidance:
For cloud-hosted NetScaler instances, implement CISA BOD 22-01 requirements or equivalent cloud-provider security controls.
Ensure that any automation or orchestration workflows also reference the updated firmware/API endpoints. - Ongoing verification & validation:
Periodically re-fingerprint deployed builds (using the vhash MD5 method) to confirm that no outdated or vulnerable build remains in service.
Incorporate these checks into regular vulnerability scanning or patch-compliance reports.
How TPRM professionals can leverage Black Kite for Citrix Bleed 2
Black Kite’s “Citrix Bleed 2” FocusTagTM streamlines vendor risk workflows by:
- Filtering your vendor portfolio to those hosting vulnerable NetScaler builds.
- Providing asset-level intelligence (specific IP addresses and subdomains) for rapid impact analysis.
- Version fingerprinting via the embedded vhash JavaScript variable on /vpn/index.html or /vpn/logout.html.
As Black Kite, when detecting this data we leveraged the embedded JavaScript variable vhash on the HTTP login pages (/vpn/index.html or /vpn/logout.html) to obtain version-based hash information. This vhash corresponds to the MD5 digest of the compressed configuration file (rdx_en.json.gz), allowing us to accurately identify which specific builds are vulnerable.
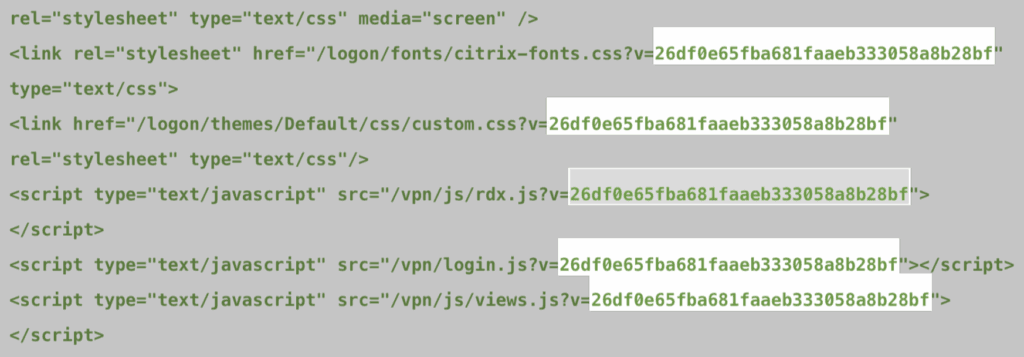
The vhash shown in the screenshot, 26df0e65fba681faaeb333058a8b28bf, corresponds to Citrix NetScaler build 12.1-50.28.
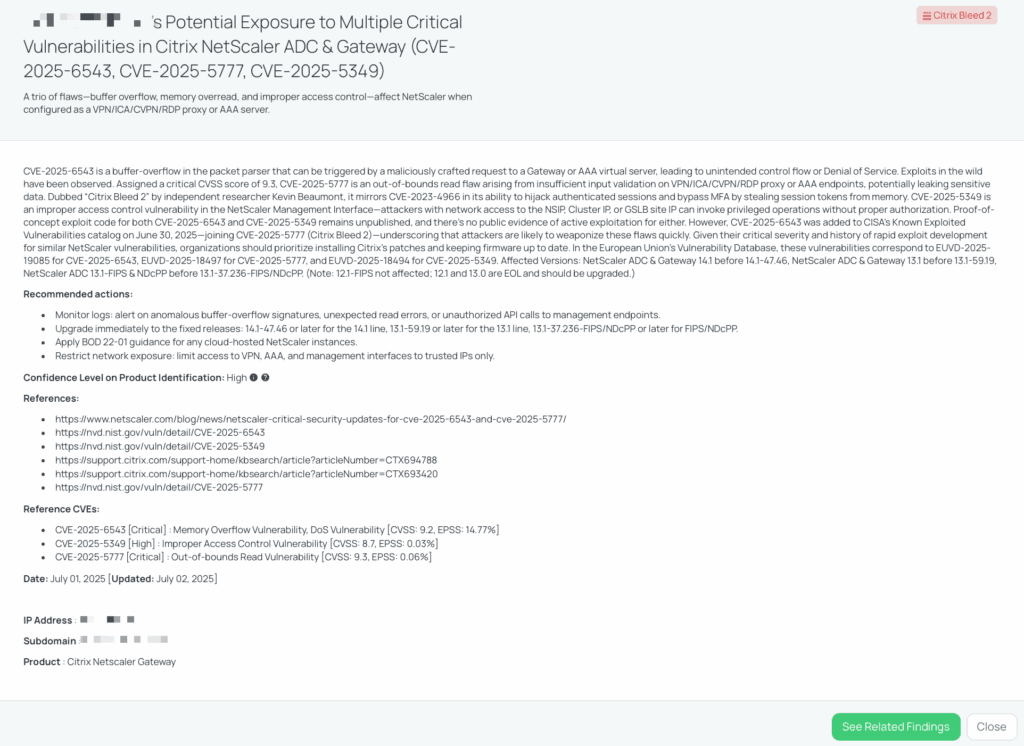
Black Kite’s Citrix Bleed 2 FocusTagTM details critical insights on the event for TPRM professionals.
CVE-2025-47812 IN WING FTP SERVER
Wing FTP Server is a highly featured, cross-platform Windows, Linux and macOS file transfer solution. It supports FTP, FTPS, HTTP, HTTPS and SFTP so clients can pick the protocol most suitable for their requirements. Administrators remotely manage users and domains, view performance and active sessions, set up event-driven notifications (e.g., email notifications on upload or download), and automate workflows with integrated Lua.
What is the Wing FTP Server remote code execution vulnerability?
CVE-2025-47812 is an unauthenticated remote code execution flaw in Wing FTP Server versions ≤ 7.4.3. It arises from improper handling of NULL bytes in the username parameter on the /loginok.html endpoint—an attacker can truncate the authentication check and inject arbitrary Lua into session files, which the server then executes with root (Linux) or SYSTEM (Windows) privileges. This vulnerability scores 10.0 (CRITICAL) under CVSS 4.0; EPSS data is not available. On June 30, 2025, public proof-of-concept exploit code and a Metasploit module were released to the Exploit Database, dramatically lowering the barrier to compromise.
There is no confirmed in-the-wild exploitation beyond those publicly released PoCs, but the ease of exploitation and default anonymous-login configuration make urgent patching imperative rcesecurity.com.
As of July 2, 2025, CVE-2025-47812 is not listed in CISA’s KEV catalog cisa.gov. No standalone CISA advisory has been published for this issue.
Why should TPRM professionals care about this vulnerability?
Wing FTP Server often sits at the edge of file-transfer workflows—exposure here can lead to:
- Full server takeover, compromising sensitive data and business processes.
- Lateral movement within the network using elevated privileges.
- Regulatory and contractual breaches, since FTP servers frequently handle PII or proprietary assets.
Unchecked vendor exposure could translate into data breaches, operational downtime, and significant remediation costs.
What questions should TPRM professionals ask vendors about CVE-2025-47812?
- Have you updated all instances of Wing FTP Server to version 7.4.4 or later to mitigate the risk of CVE-2025-47812?
- Can you confirm if the Wing FTP Server web session module (loginok.html) and its default Lua-based session file mechanism are active in your systems?
- Have you implemented network segmentation to limit HTTP(S) access to trusted management networks only as recommended for this vulnerability?
- Have you restricted anonymous access or tightly controlled anonymous/guest web logins to prevent unauthorized access and potential exploitation of CVE-2025-47812?
Remediation recommendations for vendors subject to this risk
To eliminate this flaw, vendors should:
- Upgrade immediately to Wing FTP Server v7.4.4 or later.
- Disable or tightly control anonymous/guest logins, allowing only authenticated or IP-restricted access.
- Segment the management interface and /loginok.html endpoint behind trusted networks or VPNs.
- Run the service under a least-privilege account rather than root/SYSTEM.
- Monitor file-system activity for unexpected creation or modification of Lua session files.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite’s “Wing FTP Server” FocusTagTM empowers you to:
- Filter vendor portfolios to pinpoint organizations running vulnerable Wing FTP builds.
- Retrieve asset-level intelligence (IP addresses, hostnames) for exposed FTP servers.
- Automate detection by scanning for the vulnerable /loginok.html behavior or parsing FTP-banner versions.
Operationalizing this tag ensures outreach is targeted only at vendors truly at risk—streamlining assessments and accelerating remediation.
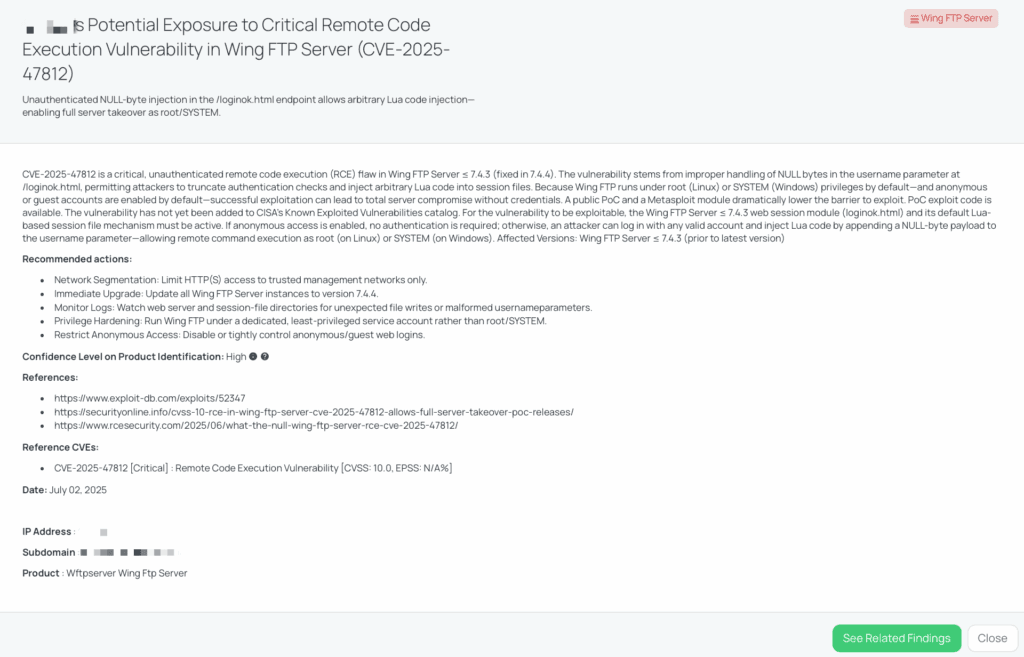
Black Kite’s Wing FTP Server FocusTagTM details critical insights on the event for TPRM professionals.
ENHANCING TPRM OUTCOMES WITH BLACK KITE’S FOCUSTAGS™
Black Kite’s FocusTags™ are purpose-built to turn complex vulnerability data into actionable TPRM intelligence. With tags tailored to Citrix Bleed 2 and the Wing FTP Server RCE, you can:
- Pinpoint at-risk vendors instantly: Automatically flag suppliers running vulnerable builds of NetScaler or Wing FTP Server.
- Streamline outreach: Focus questionnaires and verification efforts only on parties actually affected, reducing wasted effort.
- Gain asset-level visibility: Retrieve the exact IPs, hostnames, and endpoints tied to each vulnerability for rapid containment.
- Embed continuous monitoring: Leverage built-in fingerprinting (e.g., vhash for NetScaler, login behavior checks for Wing FTP) to maintain ongoing compliance checks.
By integrating these FocusTags™ into your risk workflows, you sharpen your ability to assess and mitigate third-party exposure—ensuring that critical fixes reach the right vendors without delay.
ABOUT FOCUS FRIDAY
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FocusTags™ in the Last 30 Days:
- Citrix Bleed 2 : CVE-2025-6543, CVE-2025-5777, CVE-2025-5349, Buffer Overflow Vulnerability, Out-of-Bounds Memory Read Vulnerability, RCE Vulnerability, and Improper Access Control Vulnerability in NetScaler ADC and NetScaler Gateway.
- Wing FTP Server : CVE-2025-47812, Remote Code Execution Vulnerability in Wing FTP Server.
- MongoDB – Jun2025 : CVE-2025-6709, CVE-2025-6710, DoS Vulnerabilities in MongoDB.
- Mattermost : CVE-2025-4981, Arbitrary File Write Vulnerability in Mattermost.
- Grafana – Jun2025 : CVE-2025-4123, Cross-Site Scripting (XSS) Vulnerability, Open Redirect Vulnerability, SSRF Vulnerability in Grafana.
- Cisco ClamAV : CVE-2025-20260, CVE-2025-20234, Heap-based Buffer Overflow Vulnerability, Out-of-bounds Read Vulnerability in Cisco ClamAV.
- Elastic Kibana : CVE-2024-43706, Improper Authorization Vulnerability in Elastic Kibana.
- Tridium Niagara : CVE-2025-3936, CVE-2025-3937, CVE-2025-3938, CVE-2025-3939, CVE-2025-3940, CVE-2025-3941, CVE-2025-3942, CVE-2025-3943, CVE-2025-3944, and CVE-2025-3945, Multiple Critical Vulnerabilities in Niagara Framework, Niagara Enterprise Security.
- Roundcube Webmail – Jun2025 : CVE-2025-49113, Remote Code Execution Vulnerability, Deserialization of Untrusted Data in Roundcube Webmail.
- ScreenConnect – May2025 : CVE-2025-3935, Improper Authentication Vulnerability in ConnectWise ScreenConnect.
- Zimbra – May2025 : CVE-2024-27443, Cross-Site Scripting (XSS) Vulnerability in Zimbra Collaboration (ZCS).
- DrayTek Vigor – May2025 : CVE-2024-12987, OS Command Injection Vulnerability in DrayTek Vigor Routers.
- Atlassian Jira Data Center : CVE-2025-22157, Privilege Escalation Vulnerability in Jira Core Data Center, Jira Core Server, Jira Service Management Data Center, Jira Service Management Server.
- Tornado Web Server : CVE-2025-47287, DoS Vulnerability in Tornado Web Server.
See Black Kite’s full CVE Database and the critical TPRM vulnerabilities that have an applied FocusTagTM at https://blackkite.com/cve-database/.
References
https://support.citrix.com/support-home/kbsearch/article?articleNumber=CTX694788
https://nvd.nist.gov/vuln/detail/CVE-2025-5777
https://nvd.nist.gov/vuln/detail/CVE-2025-5349
https://nvd.nist.gov/vuln/detail/CVE-2025-6543
https://support.citrix.com/support-home/kbsearch/article?articleNumber=CTX693420
https://www.exploit-db.com/exploits/52347
https://www.rcesecurity.com/2025/06/what-the-null-wing-ftp-server-rce-cve-2025-47812