FOCUS FRIDAY: TPRM INSIGHTS INTO CRITICAL VULNERABILITIES IN MICROSOFT WINDOWS, SOLARWINDS WHD, ZIMBRA, AND EXCHANGE SERVER
Welcome to this week’s edition of Focus Friday, where we delve into high-profile incidents from a Third-Party Risk Management (TPRM) perspective. In today’s rapidly evolving cyber threat landscape, organizations must remain vigilant, particularly when dealing with critical vulnerabilities that could significantly impact their operations. This week, we spotlight four significant vulnerabilities affecting widely-used platforms: Microsoft Windows, SolarWinds Web Help Desk (WHD), Zimbra Collaboration Suite, and Microsoft Exchange Server. We will explore the risks these vulnerabilities pose, how they could impact your vendors, and how you can leverage Black Kite’s FocusTags™ to mitigate these threats effectively.
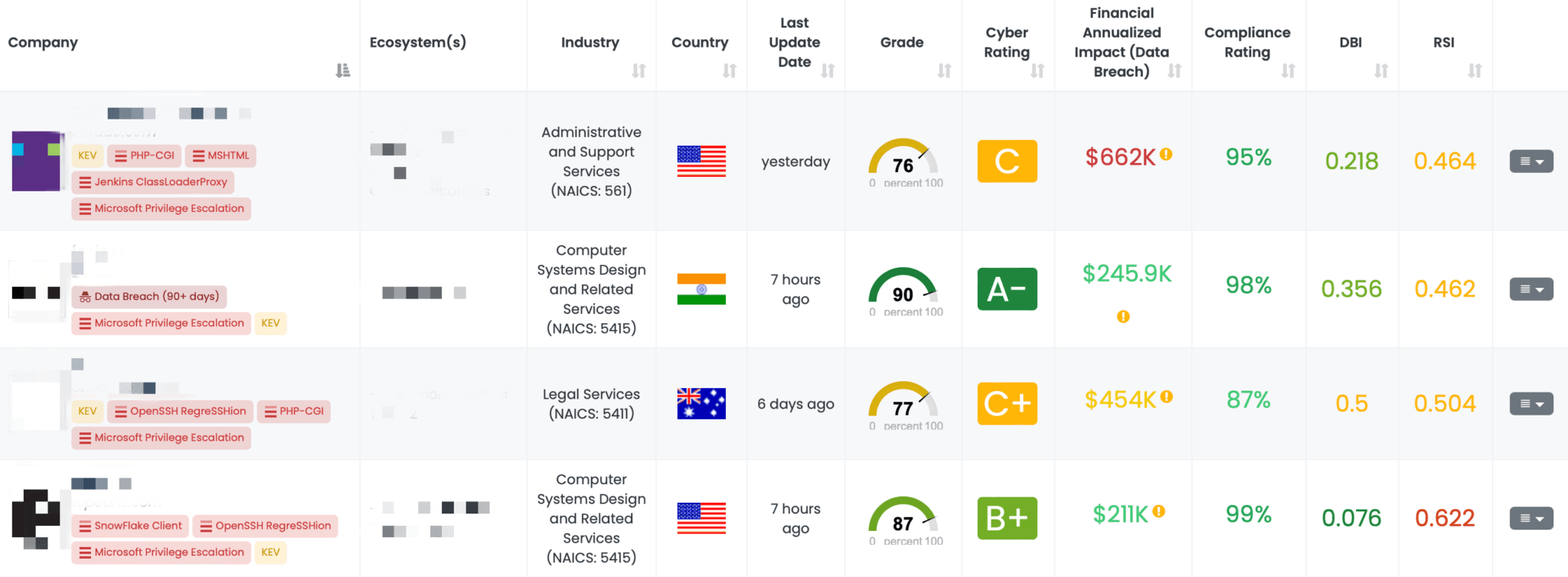
Filtered view of companies with a Microsoft Windows Privilege Escalation FocusTag™ on the Black Kite platform.
CVE-2024-38193, CVE-2024-38106, CVE-2024-38107: Critical Privilege Escalation Vulnerabilities in Microsoft Windows
What is the Microsoft Privilege Escalation Vulnerability?
CVE-2024-38193, CVE-2024-38106, and CVE-2024-38107 are critical vulnerabilities affecting various versions of Microsoft Windows, including Windows 10, Windows 11, and Windows Server. These vulnerabilities comprise a remote code execution vulnerability (CVE-2024-38193) in the Windows Ancillary Function Driver for WinSock, a privilege escalation vulnerability (CVE-2024-38106) in the Windows Kernel, and a security feature bypass vulnerability (CVE-2024-38107) in the Windows Power Dependency Coordinator. All three vulnerabilities have been classified as high-severity, with CVSS scores of 7.8 for CVE-2024-38193 and CVE-2024-38107, and 7.0 for CVE-2024-38106.
These vulnerabilities were disclosed on August 13, 2024, and have since been confirmed and exploited in the wild, although they were not publicly disclosed prior to this announcement. They were subsequently added to CISA’s Known Exploited Vulnerabilities (KEV) catalog on the same day. The impacted products include various versions of Windows 10 (versions 1507, 1607, 1809, 21H2, 22H2), Windows 11 (versions 21H2, 22H2, 23H2, 24H2), and multiple versions of Windows Server (2008, 2008 R2, 2012, 2012 R2, 2016, 2019, 2022, 2022_23H2).
Why Should TPRM Professionals Care About the Microsoft Windows Vulnerabilities?
The vulnerabilities CVE-2024-38193, CVE-2024-38106, and CVE-2024-38107 pose significant risks to organizations utilizing affected Microsoft products, including Windows 10, Windows 11, and Windows Server. Successful exploitation of these vulnerabilities could allow attackers to gain SYSTEM privileges, leading to a complete system compromise. The potential for unauthorized access to sensitive information, disruption of critical services, and severe operational impacts is heightened, particularly in environments where these Microsoft systems are integral to business operations.
The urgency of addressing these vulnerabilities is further amplified by the introduction of Windows 11, version 24H2, which is pre-installed on the new Copilot+ devices. Although this version of Windows 11 is not yet generally available, the presence of these vulnerabilities on devices already in use underscores the importance of immediate action. Users must be aware of these risks and ensure that necessary updates are promptly applied to mitigate potential threats.
What Questions Should TPRM Professionals Ask Vendors About These Microsoft Windows Vulnerabilities?
To assess their risk exposure related to these vulnerabilities, TPRM professionals should ask vendors the following specific questions:
- Have you deployed the specific security updates released in August 2024 for Windows 10, 11, and Windows Server versions to address CVE-2024-38193, CVE-2024-38106, and CVE-2024-38107?
- Have you implemented any specific Group Policy settings or registry modifications to address this vulnerability, especially regarding race conditions in the Windows Kernel?
- What specific logging configurations and monitoring tools are you using to detect and respond to potential exploitation attempts of CVE-2024-38193 in the Windows Ancillary Function Driver for WinSock?
- How have you configured the Windows Power Dependency Coordinator to prevent exploitation of CVE-2024-38107?
Remediation Recommendations for Vendors Subject to This Risk
To mitigate the risks associated with CVE-2024-38193, CVE-2024-38106, and CVE-2024-38107, vendors should take the following actions:
- Apply Security Patches: Ensure that all affected systems are updated with the latest security patches provided by Microsoft to address these vulnerabilities.
- Monitor for IoCs: Implement enhanced monitoring for unusual activity that may indicate an attempt to exploit these vulnerabilities, particularly focusing on logs and security events.
- Implement Least Privilege: Restrict user permissions to minimize the potential impact of a successful exploit, ensuring that only essential users have administrative privileges.
- Review and Harden Configurations: Secure system configurations to reduce potential attack vectors. For CVE-2024-38106, which involves a race condition, ensure that system configurations are optimized to minimize the risk of exploitation.
How TPRM Professionals Can Leverage Black Kite for These Vulnerabilities
Black Kite’s FocusTags™ provide TPRM professionals with a streamlined and efficient method for identifying vendors at risk due to these vulnerabilities. The Microsoft Privilege Escalation tag, published shortly after these vulnerabilities were disclosed, allows customers to quickly determine which vendors are exposed. By providing detailed asset information, such as IP addresses and subdomains associated with the vulnerabilities, Black Kite enables TPRM teams to focus their efforts on the most critical areas, significantly reducing time and resource expenditure.
Moreover, the FocusTag™ includes updates related to the new Windows 11, version 24H2, as installed on Copilot+ devices. This ensures that TPRM professionals are informed of potential risks even before the general availability of this Windows version, allowing them to take preemptive measures to safeguard their organization’s assets.
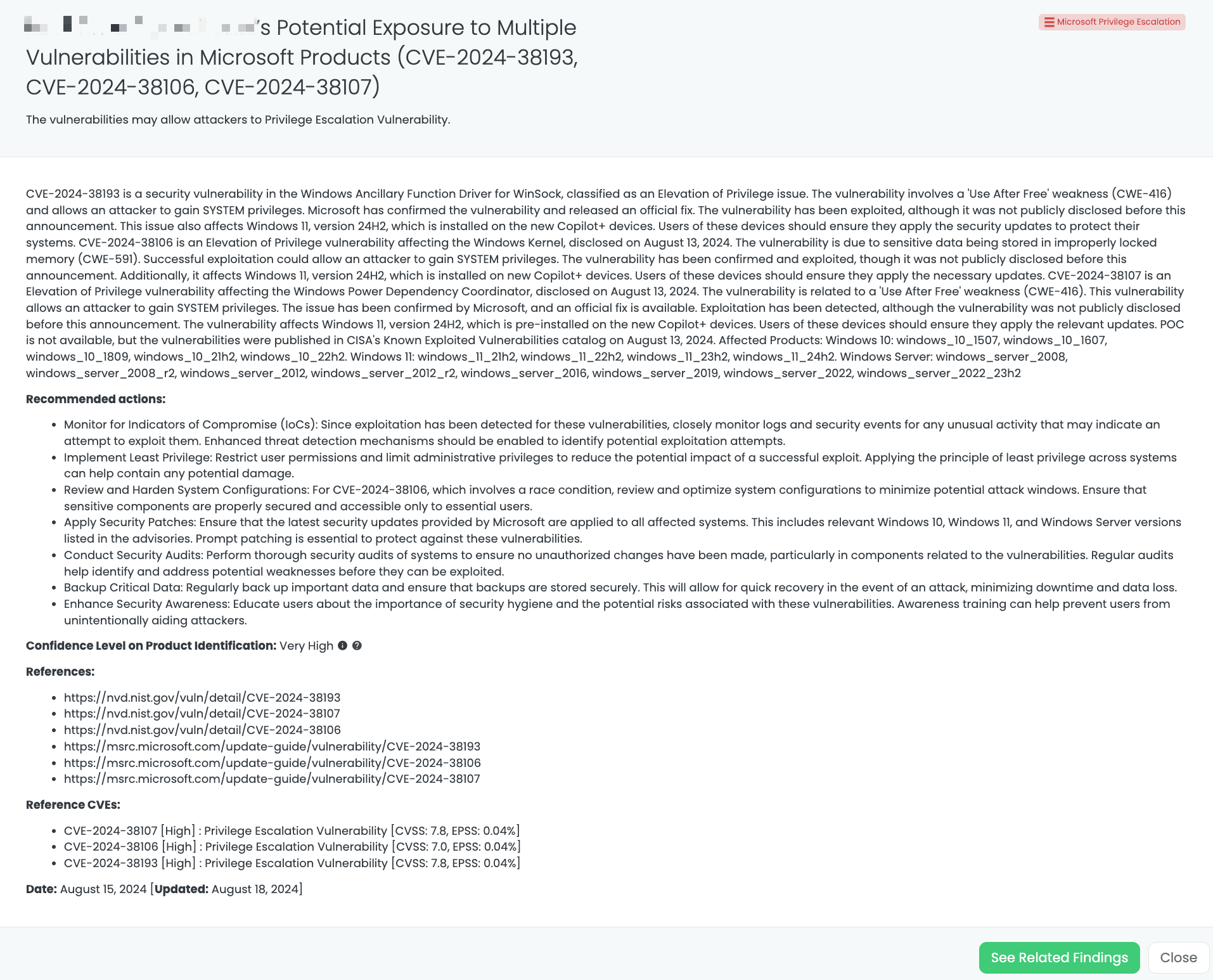
Black Kite’s Microsoft Privilege Escalation FocusTagTM details critical insights on the event for TPRM professionals.
CVE-2024-28986: Critical RCE Vulnerability in SolarWinds Web Help Desk
What is the SolarWinds WHD RCE Vulnerability?
CVE-2024-28986 is a critical remote code execution (RCE) vulnerability affecting all versions of SolarWinds Web Help Desk (WHD) prior to version 12.8.3. This vulnerability is a result of improper deserialization of untrusted data, which allows attackers to execute arbitrary commands on the host system. With a CVSS score of 9.8, this vulnerability is extremely severe, as successful exploitation can lead to full control over the affected system.
The vulnerability was publicly disclosed on August 15, 2024, and has been actively exploited in the wild. CISA added this vulnerability to its Known Exploited Vulnerabilities (KEV) catalog on the same day, indicating the seriousness of the threat. Although initially reported as potentially exploitable without authentication, SolarWinds has been able to reproduce the issue only after authentication. Despite this, the vulnerability’s critical nature and the fact that it is being actively exploited in attacks have made it a top priority for remediation.
Why Should TPRM Professionals Be Concerned?
TPRM professionals should be particularly vigilant about this vulnerability because SolarWinds WHD is widely used across various industries, including government, healthcare, and education. Exploitation of this vulnerability could lead to significant operational disruptions, data exfiltration, and further attacks on other systems within a network. Given the software’s role in managing IT assets and service tickets, a compromised WHD system could expose sensitive information and be used to launch broader, more damaging attacks.
What Questions Should TPRM Professionals Ask Vendors?
To assess the risk posed by CVE-2024-28986, TPRM professionals should ask vendors the following questions:
- Have you successfully applied the SolarWinds Web Help Desk 12.8.3 HF1 hotfix to mitigate CVE-2024-28986?
- How have you configured access control lists (ACLs) or firewall rules to restrict access to the SolarWinds WHD interface, ensuring that only trusted IP addresses can reach the application?
- What specific logging and monitoring mechanisms have you implemented to detect and respond to potential exploitation attempts of CVE-2024-28986?
- Have you reviewed and tested your backup and recovery procedures to ensure they are robust in case of an attack exploiting this vulnerability?
Remediation Recommendations for Vendors
Vendors using SolarWinds WHD should take immediate action to mitigate the risk posed by CVE-2024-28986:
- Apply the Hotfix: Upgrade to SolarWinds Web Help Desk 12.8.3 HF1 immediately.
- Restrict Access: Limit access to the WHD interface to trusted IP addresses only and avoid exposing the application directly to the internet.
- Continuous Monitoring: Implement continuous monitoring of network traffic and system logs for any unusual activities.
- Backup and Recovery: Ensure that backup and recovery plans are in place and regularly tested to prevent data loss in the event of an attack.
How TPRM Professionals Can Leverage Black Kite for This Vulnerability
Black Kite has provided a FocusTag for CVE-2024-28986, which helps identify vendors potentially affected by this vulnerability. This tag, published on August 15, 2024, allows TPRM professionals to quickly determine which vendors in their supply chain may be at risk. By providing asset information, such as IP addresses or subdomains associated with vulnerable systems, Black Kite enables organizations to prioritize their remediation efforts effectively, saving time and resources. For organizations already using this tag, the updated information highlights the importance of swift action due to active exploitation in the wild.
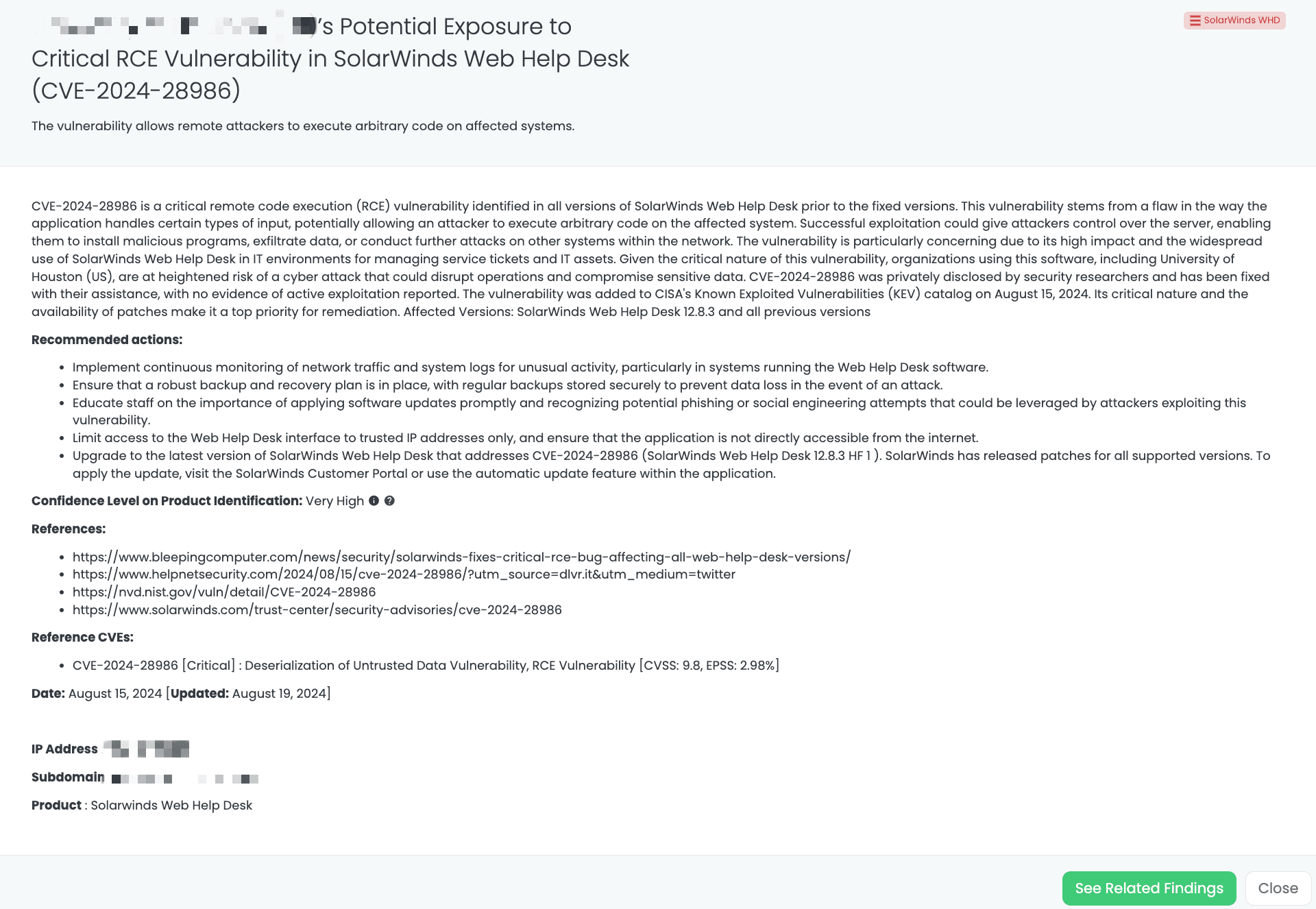
Black Kite’s SolarWinds WHD FocusTagTM details critical insights on the event for TPRM professionals.
CVE-2024-33535: Zimbra Collaboration Suite Local File Inclusion Vulnerability
What is the Zimbra LFI Vulnerability?
CVE-2024-33535 is a Local File Inclusion (LFI) vulnerability affecting Zimbra Collaboration Suite (ZCS) versions 9.0.0 and 10.0.0 through 10.0.7. This vulnerability stems from insufficient input validation, allowing an attacker to manipulate input parameters to include arbitrary files from the local server into the application’s output stream. As a result, sensitive files such as configuration files and user credentials could be exposed, potentially leading to unauthorized access and data leakage. The vulnerability was first disclosed in August 2024, and while it has not been added to CISA’s Known Exploited Vulnerabilities (KEV) catalog, the lack of a public PoC suggests it might still be exploitable by attackers with the necessary expertise.
Why Should TPRM Professionals Care About This Vulnerability?
TPRM professionals should be concerned about this vulnerability due to its potential impact on the security and integrity of email communications and sensitive data handled by vendors using Zimbra Collaboration Suite. If exploited, this vulnerability could allow threat actors to gain unauthorized access to critical information, which could be used for further attacks, including compromising the vendor’s network or launching phishing campaigns using legitimate email accounts. Given that Zimbra is widely used for email and collaboration, the risk of data breaches and subsequent reputational damage is significant.
What Questions Should TPRM Professionals Ask Vendors About This Vulnerability?
When assessing vendors’ exposure to CVE-2024-33535, TPRM professionals should consider the following questions:
- Have you updated all instances of Zimbra Collaboration Suite to versions 9.0.0/P40 or 10.0.8 to address CVE-2024-33535?
- What specific input validation mechanisms have you implemented to ensure that file-related parameters within Zimbra Collaboration Suite cannot be manipulated to include arbitrary files?
- Have you reviewed and updated file permissions within the Zimbra environment to restrict access to sensitive files, such as configuration files and user credentials?
- What logging and monitoring strategies are you using to detect potential exploitation attempts of CVE-2024-33535?
Remediation Recommendations for Vendors Subject to This Risk
Vendors should take the following actions to mitigate the risk associated with CVE-2024-33535:
- Update all Zimbra installations to the latest version that addresses this vulnerability.
- Implement strict input validation on all file-related requests to prevent unauthorized file inclusion.
- Restrict access to sensitive files by ensuring proper permissions and limiting exposure.
- Regularly monitor server logs for any signs of attempted exploitation.
- Consider deploying a Web Application Firewall (WAF) to detect and block malicious requests targeting LFI vulnerabilities.
How TPRM Professionals Can Leverage Black Kite for This Vulnerability
Black Kite’s FocusTags™ provide invaluable insights by identifying vendors potentially exposed to this LFI vulnerability in Zimbra Collaboration Suite. The FocusTag for CVE-2024-33535 was published on August 15, 2024, and offers detailed information on affected assets, including IP addresses and subdomains. This intelligence enables TPRM professionals to prioritize risk assessments and remediation efforts, reducing the time spent on evaluating unaffected vendors. Additionally, Black Kite’s ability to provide real-time updates and refined vulnerability data allows for more proactive and informed decision-making.
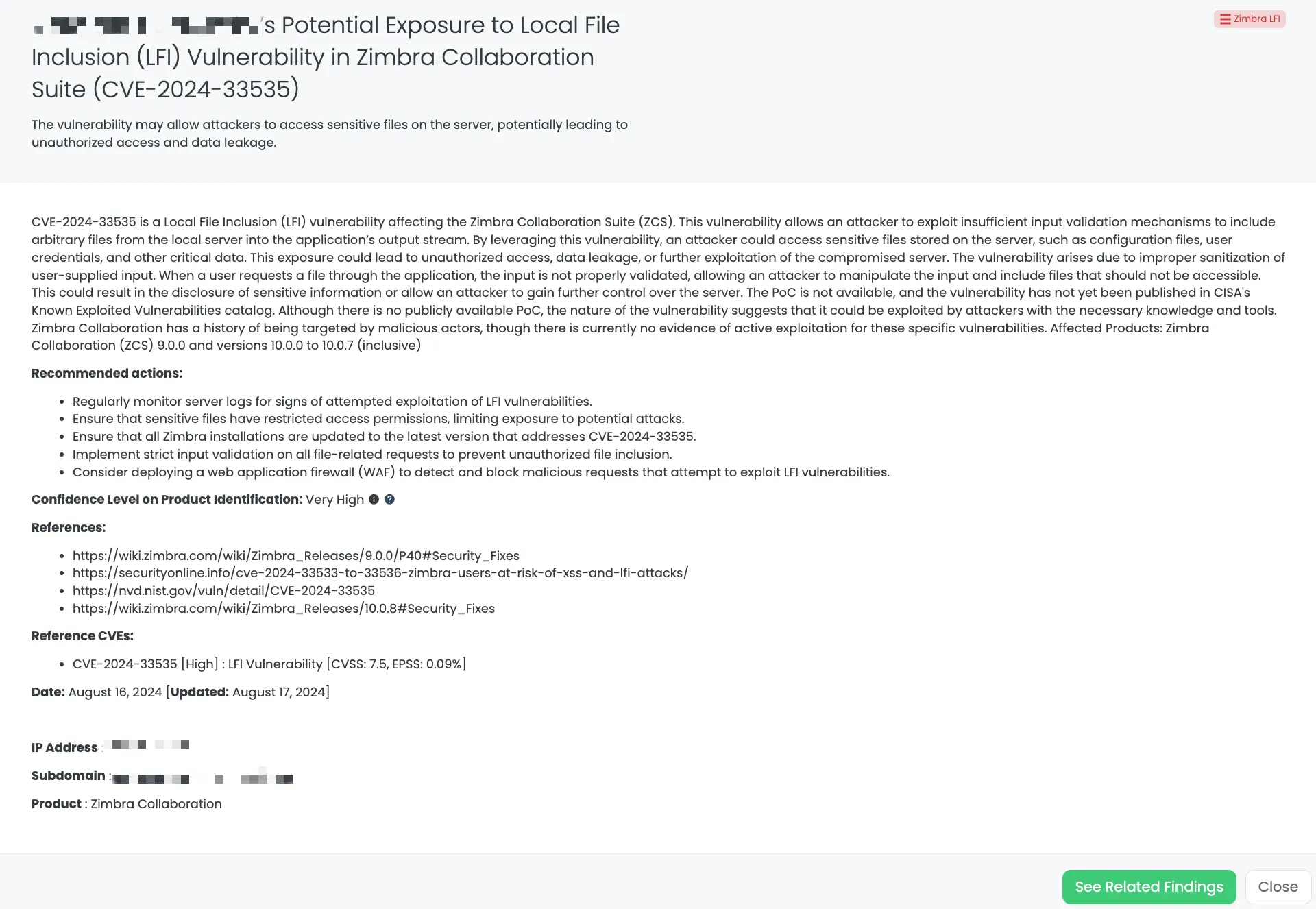
Black Kite’s Zimbra LFI FocusTagTM details critical insights on the event for TPRM professionals.
CVE-2021-31196 and CVE-2021-34473 in Microsoft Exchange Server
What are the Remote Code Execution Vulnerabilities in Microsoft Exchange Server?
CVE-2021-31196 and CVE-2021-34473 are both critical Remote Code Execution (RCE) vulnerabilities affecting multiple versions of Microsoft Exchange Server. These vulnerabilities allow attackers to execute arbitrary code on a server, potentially leading to a full system compromise.
- CVE-2021-31196: This vulnerability exists due to improper validation of certain requests made to the Exchange Server. An attacker can exploit this flaw by sending specially crafted requests, resulting in the execution of malicious code. The CVSS score for this vulnerability is 7.2, with an EPSS score of 6.17%.
- CVE-2021-34473: A part of the notorious ProxyShell exploit chain, this vulnerability is especially dangerous, allowing unauthenticated attackers to execute arbitrary code by exploiting improper validation of client requests. The CVSS score is 9.8, with an EPSS score of 97.30%, indicating a high likelihood of exploitation.
Both vulnerabilities were added to CISA’s KEV catalog on August 21, 2024, reflecting their criticality and widespread impact. CVE-2021-34473 has been extensively exploited in the wild, leading to numerous unauthorized access incidents and data breaches.
Why Should TPRM Professionals Care About These Vulnerabilities?
These vulnerabilities pose a significant risk to organizations, particularly those relying on Microsoft Exchange Server as a core component of their IT infrastructure. Successful exploitation can lead to the complete compromise of sensitive data, including emails and internal communications. This can result in unauthorized data access, manipulation of communication channels, and further network intrusions.
Given the critical role of email servers in an organization’s operations, the potential consequences of an exploited Exchange Server vulnerability include severe data breaches, operational disruption, and reputational damage.
What Questions Should TPRM Professionals Ask Vendors About These Vulnerabilities?
When engaging with vendors, TPRM professionals should ask specific questions to assess the risk related to these vulnerabilities:
- Have you applied the latest cumulative updates from Microsoft that address CVE-2021-31196 and CVE-2021-34473 on all Exchange Server installations?
- Have you configured access controls to limit exposure to CVE-2021-34473, particularly in relation to the ProxyShell exploit chain?
- What specific threat detection measures are in place to identify potential exploitation of CVE-2021-31196 and CVE-2021-34473?
- Are you auditing and monitoring logs on your Exchange Server to detect potential signs of exploitation related to these vulnerabilities?
Remediation Recommendations for Vendors Subject to This Risk
Vendors should take the following actions to mitigate the risks associated with these vulnerabilities:
- Apply the Latest Security Updates: Ensure that all affected Exchange Server installations are updated to the latest cumulative updates as provided by Microsoft.
- Implement Strong Security Practices: Configure Exchange Server with robust security measures, including limiting server access, enabling multi-factor authentication, and regularly auditing access logs.
- Conduct Proactive Threat Hunting: Given the critical nature of Exchange Server, proactive threat hunting to identify potential indicators of compromise is essential.
- Monitor Network Traffic: Regularly monitor network traffic to and from Exchange Server for any unusual activity that may indicate exploitation attempts.
How TPRM Professionals Can Leverage Black Kite for These Vulnerabilities
Black Kite’s FocusTags™ provide crucial insights for TPRM professionals, enabling them to identify vendors potentially exposed to these vulnerabilities. The FocusTag™ for Exchange Server RCE, published on August 22, 2024, highlights vendors at risk, including details such as IP addresses and subdomains associated with vulnerable assets.
By leveraging this information, TPRM professionals can prioritize their outreach and remediation efforts, focusing on vendors that pose the greatest risk to their organization. The updated FocusTag also reflects new intelligence on the exploitation of these vulnerabilities, ensuring that organizations can respond swiftly to emerging threats.
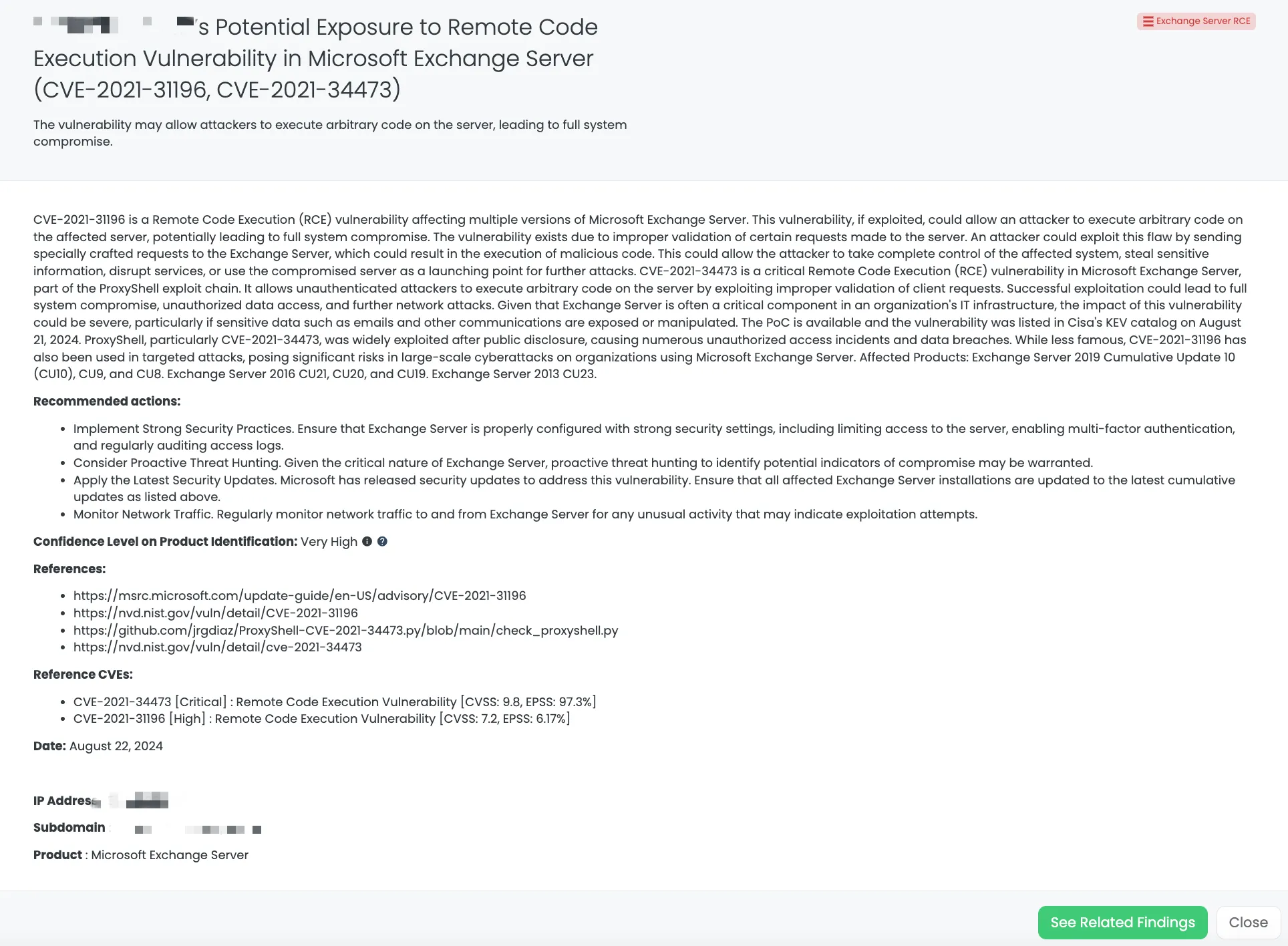
Black Kite’s Exchange Server RCE FocusTagTM details critical insights on the event for TPRM professionals.
Enhancing TPRM Strategies with Black Kite’s FocusTags™
In the ever-evolving realm of cybersecurity, proactive risk management is essential, particularly when addressing critical vulnerabilities like those found in Microsoft Privilege Escalation, SolarWinds WHD, Zimbra LFI, Exchange Server RCE. Black Kite’s FocusTags™ are designed to provide unparalleled support in Third-Party Risk Management (TPRM) by offering real-time insights into potential threats, enabling swift and informed decision-making.
Real-Time Risk Identification: FocusTags™ enable organizations to instantly identify vendors affected by the latest vulnerabilities, ensuring a timely and focused response.
Targeted Risk Prioritization: By assessing both the importance of the vendor and the severity of the vulnerability, FocusTags™ help prioritize efforts where they matter most.
Informed Vendor Engagement: Engage in more productive conversations with your vendors, equipped with specific intelligence about their exposure to critical vulnerabilities.
Comprehensive Security Enhancement: With a broad perspective on the threat landscape, FocusTags™ facilitate the development of stronger, more adaptive cybersecurity strategies.
Black Kite’s FocusTags™ are essential for translating complex threat data into actionable intelligence, allowing TPRM professionals to manage risks efficiently and proactively. As these threats evolve, having the right tools in place to address them becomes increasingly vital for safeguarding your organization.
FocusTags™ in the Last 30 Days:
Microsoft Privilege Escalation Vulnerability: CVE-2024-38193, CVE-2024-38106, CVE-2024-38107, Critical Privilege Escalation Vulnerabilities in Microsoft Windows
SolarWinds WHD: CVE-2024-28986, Critical Remote Code Execution Vulnerability in SolarWinds Web Help Desk
Zimbra LFI: CVE-2024-33535, Local File Inclusion Vulnerability in Zimbra Collaboration Suite
Exchange Server RCE: CVE-2021-31196, CVE-2021-34473, Remote Code Execution Vulnerabilities in Microsoft Exchange Server
Zabbix: CVE-2024-22116, Critical Remote Code Execution Vulnerability in Zabbix Monitoring Solution
Jenkins ClassLoaderProxy: CVE-2024-43044, Arbitrary File Read and Remote Code Execution Vulnerability in Jenkins ClassLoaderProxy
Dahua NVR4: CVE-2024-39944, CVE-2024-39948, and CVE-2024-39949, Remote Code Execution, Authentication Bypass, and Improper Access Control Vulnerabilities in Dahua NVR4 devices
VMware ESXi: CVE-2024-37085, Authentication Bypass Vulnerability in VMware ESXi, VMware Cloud Foundation
Gogs: CVE-2024-39930, CVE-2024-39931, CVE-2024-39932, and CVE-2024-39933, Argument Injection Vulnerability in Gogs
Internet Explorer: CVE-2012-4792, Use-After-Free Vulnerability in Internet Explorer
Docker AuthZ: CVE-2024-41110, AuthZ Bypass and Privilege Escalation Vulnerability in Docker
JumpServer: CVE-2024-40628, CVE-2024-40629, Sensitive Information Disclosure and RCE Vulnerability in JumpServer
Serv-U FTP: CVE-2024-28995, Directory Traversal Vulnerability in SolarWinds Serv-U
Microsoft SharePoint: CVE-2024-38094, Remote Code Execution Vulnerability in Microsoft SharePoint
References
https://nvd.nist.gov/vuln/detail/CVE-2021-31196
https://nvd.nist.gov/vuln/detail/cve-2021-34473
https://msrc.microsoft.com/update-guide/en-US/advisory/CVE-2021-31196
https://github.com/jrgdiaz/ProxyShell-CVE-2021-34473.py/blob/main/check_proxyshell.py
https://nvd.nist.gov/vuln/detail/CVE-2024-33535
https://securityonline.info/cve-2024-33533-to-33536-zimbra-users-at-risk-of-xss-and-lfi-attacks
https://wiki.zimbra.com/wiki/Zimbra_Releases/9.0.0/P40#Security_Fixes
https://wiki.zimbra.com/wiki/Zimbra_Releases/10.0.8#Security_Fixes
https://nvd.nist.gov/vuln/detail/CVE-2024-28986
https://www.solarwinds.com/trust-center/security-advisories/cve-2024-28986
https://www.helpnetsecurity.com/2024/08/15/cve-2024-28986/?utm_source=dlvr.it&utm_medium=twitter
https://www.helpnetsecurity.com/2024/08/15/cve-2024-28986/?utm_source=dlvr.it&utm_medium=twitter
https://nvd.nist.gov/vuln/detail/CVE-2024-38193
https://nvd.nist.gov/vuln/detail/CVE-2024-38106
https://nvd.nist.gov/vuln/detail/CVE-2024-38107
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-38193
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-38106
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-38107