FOCUS FRIDAY: THIRD-PARTY RISKS IN SHAREPOINT TOOLSHELL AND GRAFANA VULNERABILITIES
This week’s Focus Friday highlights two high-profile vulnerability disclosures that pose significant third-party risks for organizations using Microsoft SharePoint and Grafana. These platforms, widely adopted for collaboration and observability, have been targeted by sophisticated exploit chains and misconfiguration-dependent attacks that could lead to full system compromise or session hijacking.
In this post, we break down the SharePoint ToolShell remote code execution chain actively exploited by Storm-2603 and the recent XSS and open redirect flaws in Grafana affecting versions across multiple release lines. Each section offers vendor-facing questions, remediation guidance, and insight into how Black Kite’s FocusTags™ help streamline and operationalize Third-Party Risk Management (TPRM) in the face of such threats.
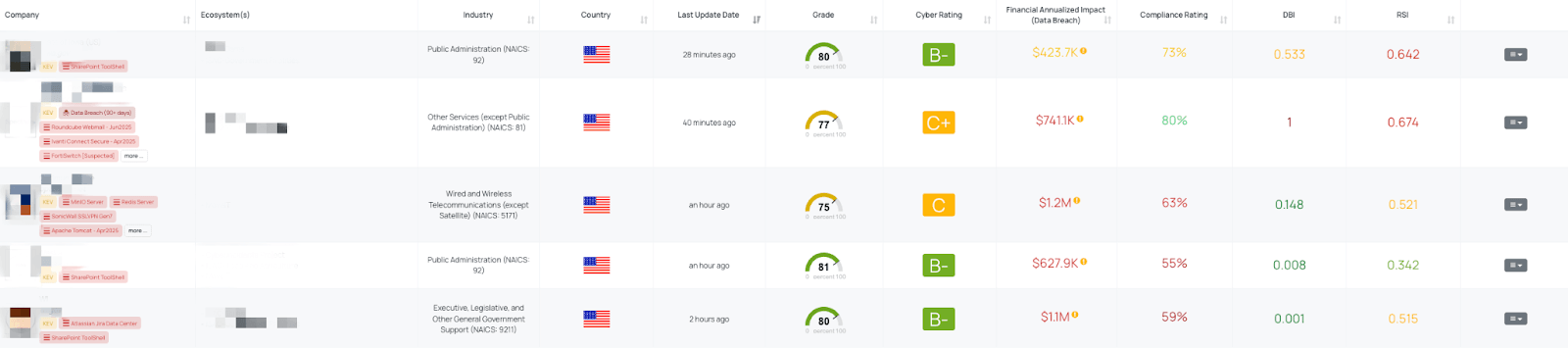
Filtered view of companies with SharePoint ToolShell FocusTag™ on the Black Kite platform.
CVE-2025-53770 – MICROSOFT SHAREPOINT TOOLSHELL EXPLOIT CHAIN
The cybersecurity community is facing a rapidly unfolding threat as Microsoft SharePoint is targeted by one of the most devastating and technically advanced exploit chains observed in recent times.
📌 You can read our in-depth technical breakdown of this widespread vulnerability in our blog post: Microsoft SharePoint Under Siege: CVE-2025-53770 Exploited via ToolShell RCE Chain.
What is the SharePoint ToolShell Exploit Chain?
ToolShell is a sophisticated unauthenticated exploit chain targeting Microsoft SharePoint Server through a combination of vulnerabilities:
- CVE-2025-49704: Code Injection – CVSS: 8.8, EPSS: 13.20%
- CVE-2025-49706: Improper Authentication – CVSS: 6.5, EPSS: 0.64%
- CVE-2025-53770: Remote Code Execution – CVSS: 9.8, EPSS: 2.48%
- CVE-2025-53771: Path Traversal – CVSS: 7.1, EPSS: 0.07%
This chain allows attackers to bypass authentication, upload a malicious ASPX web shell (e.g., spinstall0.aspx), steal cryptographic MachineKey values, and then craft signed __VIEWSTATE payloads to execute arbitrary commands via insecure deserialization.
The first exploitation in the wild was confirmed on July 18, 2025, with mass campaigns surfacing shortly thereafter. Microsoft published security updates for Subscription Edition and SharePoint 2019 on July 19, and CISA added CVE-2025-49704 and CVE-2025-49706 to its KEV catalog on July 22, and CVE-2025-53770 on July 20, indicating confirmed exploitation. An official CISA advisory was also published the same day.
Recent research from Microsoft, Eye Security, and Black Kite confirms that the exploit chain has been adopted by multiple threat actors, including Storm-2603, APT27, and APT31. Storm-2603, in particular, has been seen deploying Warlock ransomware via GPO after achieving system-level persistence on SharePoint servers.
📌 Affected Versions:
- SharePoint Server Subscription Edition
- SharePoint Server 2019
- SharePoint Server 2016
- SharePoint Online (Microsoft 365) is not impacted.
Why Should TPRM Professionals Be Concerned?
SharePoint servers often store sensitive business-critical content and are widely integrated into internal and external workflows. This attack chain provides unauthenticated, persistent, full-system compromise, allowing attackers to:
- Exfiltrate documents, credentials, tokens, and secrets
- Establish web shell persistence and deploy ransomware (e.g., Warlock)
- Move laterally across environments (via PsExec and Impacket)
- Disable security controls like Defender AV using registry edits
- Masquerade as legitimate processes (w3wp.exe) to evade detection
If a vendor’s on-premises SharePoint server is compromised, the fallout extends to customers via exposed data, impersonated communication, and ransomware propagation.
🧱 Storm-2603’s Attack Chain
The diagram below outlines how the threat actor Storm-2603 weaponizes the ToolShell exploit chain from initial access to ransomware deployment. This step-by-step operational flow highlights how a single unpatched SharePoint server can become an entry point for a full-domain compromise:
- Exploitation of Internet-Facing SharePoint Server
The attack begins with unauthenticated exploitation of vulnerable SharePoint endpoints (ToolPane.aspx, ToolShell.aspx) via crafted requests. This grants remote command execution without needing credentials. - Discovery Phase
Immediately after gaining a foothold, Storm-2603 executes basic reconnaissance commands like whoami to identify user context and privilege level, verifying whether SYSTEM-level access was achieved. - Command Execution and Script Deployment
Using cmd.exe, batch scripts, and PsExec, the attacker launches broader execution across the compromised system. PsExec enables lateral command execution between hosts. - Disabling Defender Protections
The group leverages services.exe and registry edits to disable Microsoft Defender. This creates a stealthy environment where subsequent payloads can run undetected. - Establishing Persistence
Multiple persistence mechanisms are implemented—including scheduled tasks, malicious .NET assemblies injected into IIS processes, and backdoor shells—to ensure the attacker retains access even after system reboots or partial remediation. - Credential Harvesting
With persistence secured, the attacker runs Mimikatz to dump credentials from LSASS memory, gaining access to cached or active domain credentials. - Lateral Movement
Using the stolen credentials, Storm-2603 moves laterally within the network via PsExec and Impacket, accessing additional hosts and expanding control. - Ransomware Deployment
Finally, Warlock ransomware is pushed via Group Policy Objects (GPO) to all reachable endpoints. This step weaponizes the compromised infrastructure against the victim’s broader environment.
What questions should TPRM professionals ask vendors about ToolShell?
- Have you applied the latest security updates for Microsoft SharePoint Server Subscription Edition and SharePoint Server 2019 to mitigate the risk of CVE-2025-53770, CVE-2025-49704, CVE-2025-49706, and CVE-2025-53771?
- Have you rotated SharePoint Server ASP.NET machine keys and restarted IIS on all SharePoint servers to invalidate any cryptographic material that may have been leaked by the attacker’s ‘spinstall0.aspx’ payload?
- Have you enabled Antimalware Scan Interface (AMSI) integration in Full Mode for your SharePoint Server farm(s) and configured it with a robust antivirus solution like Microsoft Defender Antivirus to protect against the exploit?
- Are you continuously monitoring your network and server logs for the Indicators of Compromise (IoCs) associated with active exploitation, such as Source IPs, User Agent, POST requests to ‘/_layouts/15/ToolPane.aspx?DisplayMode=Edit&a=/ToolPane.aspx’ with ‘Referer: /_layouts/SignOut.aspx’, and the presence of ‘spinstall0.aspx’ at ‘C:\\PROGRA~1\\COMMON~1\\MICROS~1\\WEBSER~1\\16\\TEMPLATE\\LAYOUTS\\spinstall0.aspx’?
Remediation Recommendations for Vendors Subject to This Risk
Vendors affected by the ToolShell exploit chain should implement a hardened, multi-layered remediation strategy aligned with Microsoft’s and the security community’s best practices. The following actions are essential to prevent initial compromise, detect post-exploitation behavior, and recover from potential breaches:
✅ Apply the July 2025 Security Updates
Install the official Microsoft patches for SharePoint Server Subscription Edition and SharePoint Server 2019, released on July 19, 2025. If you’re using SharePoint 2016, monitor for patch availability and apply it as soon as it’s released.
✅ Enable AMSI (Antimalware Scan Interface) in Full Mode
Ensure AMSI is configured for deep script analysis, especially for detecting obfuscated PowerShell payloads. Use a reputable antivirus solution like Microsoft Defender Antivirus to block threats such as:
- Exploit:Script/SuspSignoutReq.A
- Trojan:Win32/HijackSharePointServer.A
✅ Deploy Microsoft Defender for Endpoint or equivalent EDR/XDR
Leverage threat detection platforms to monitor for post-compromise activity:
- Suspicious IIS worker process behavior (w3wp.exe)
- PowerShell encoded command execution
- Web shell installation indicators
✅ Rotate ASP.NET Machine Keys and Restart IIS
After patching or enabling AMSI, rotate the SharePoint Server machine keys (ValidationKey and DecryptionKey) using:
Set-SPMachineKey -WebApplication “<YourWebAppUrl>”
Update-SPMachineKey -WebApplication “<YourWebAppUrl>”
iisreset.exe
This step invalidates any leaked cryptographic material used in ViewState forgery.
✅ Restrict or Disable Public Access to SharePoint Servers
Immediately disconnect affected servers from the internet if you cannot patch or enable AMSI. Use VPNs, reverse proxies, and strict IP whitelisting to reduce exposure.
✅ Harden WAF Rules and Filter Suspicious Payloads
Set custom Web Application Firewall (WAF) rules to detect or block:
- Untrusted or anomalous __VIEWSTATE payloads
- POST requests with unusually long or base64-encoded data
- Direct access to /ToolShell.aspx, /ToolPane.aspx, or known web shells like spinstall0.aspx
✅ Monitor Logs and Detect IoCs
Regularly review logs and implement detection rules for the following indicators:
- Malicious file: spinstall0.aspx
- SHA256: 92bb4ddb98eeaf11fc15bb32e71d0a63256a0ed826a03ba293ce3a8bf057a514
- Suspicious user agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0
- POST to /ToolPane.aspx with referer /SignOut.aspx
- Known attacker IPs:
- 107.191.58[.]76
- 104.238.159[.]149
- 96.9.125[.]147
- 103.186.30[.]186
💡 Note on AMSI:
AMSI (Antimalware Scan Interface) helps detect malicious scripts like PowerShell and JScript. Its impact on exploitation likelihood is significant:
Condition | Exploit Likelihood |
AMSI enabled | High chance of detection; low success rate |
AMSI disabled | Exploit highly likely to succeed |
Defender AV disabled | Payload runs silently |
Server is internet-facing | Remote access easily achievable |
How TPRM Professionals Can Leverage Black Kite for This Vulnerability
Black Kite released the SharePoint ToolShell FocusTag™ on July 20, 2025, immediately after Microsoft’s patch and CISA’s KEV update. This tag identifies vendors with internet-facing, on-prem SharePoint servers potentially exposed to ToolShell vulnerabilities.
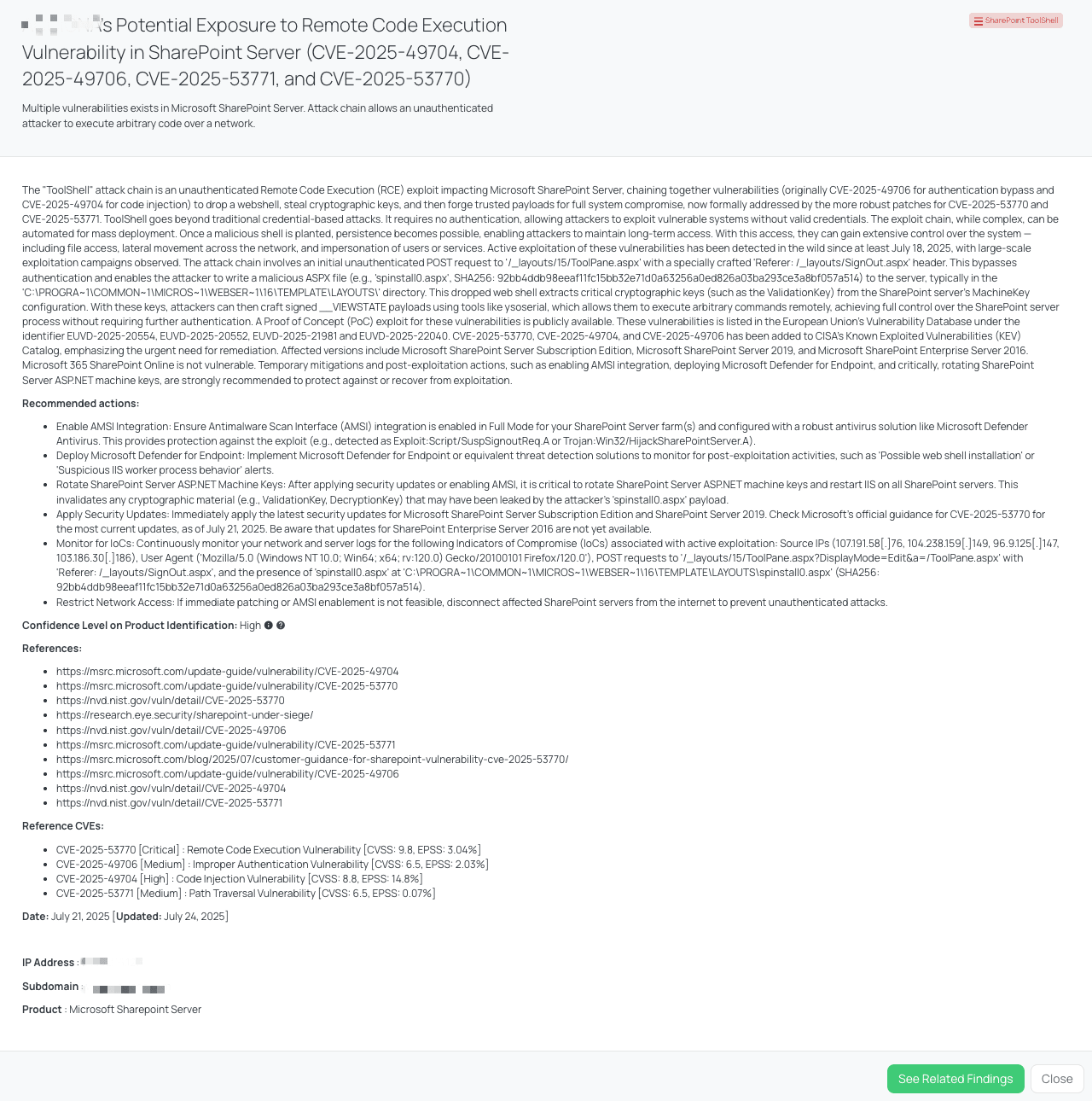
Black Kite’s SharePoint ToolShell FocusTagTM details critical insights on the event for TPRM professionals.
CVE‑2025‑6023 / CVE‑2025‑6197 – GRAFANA VULNERABILITIES
What is the Grafana XSS and Open Redirect issue?
These flaws impact self-hosted Grafana versions from 11.5.0 onward up to their respective security patches:
- CVE‑2025‑6023 (High, CVSS 7.6, EPSS 0.01%) is a reflected Cross-Site Scripting vulnerability rooted in path traversal and open redirect issues in scripted dashboards. It allows attackers to inject JavaScript in victims’ browsers without authentication—affecting both OSS and Grafana Cloud instances due to weak Content-Security-Policy (CSP) configuration.
- CVE‑2025‑6197 (Medium, CVSS 4.2, EPSS 0.01%) is an open redirect flaw in the organization-switching feature, exploitable if multiple organizations exist, the attacker knows the target org ID, and the victim belongs to more than one org. Grafana Cloud is unaffected.
Both were disclosed in mid-July 2025, and public CVE entries appeared respectively on June 11 and June 17. No public Proof-of-Concept exploits exist yet, nor are they listed in CISA’s Known Exploited Vulnerabilities (KEV) Catalog.
Why should TPRM professionals care?
Grafana is widely used for monitoring and observability. These vulnerabilities can lead to session hijacking or account takeover (CVE‑2025‑6023), enabling attackers to manipulate dashboards or query critical system data. The open redirect flaw (CVE‑2025‑6197) can facilitate phishing and may chain into additional exploit scenarios. From a TPRM standpoint, compromising a vendor’s Grafana instance might expose sensitive metrics, engineering dashboards, and internal infrastructure data—undermining trust, violating SLAs, and amplifying reputational risk.
What questions should TPRM professionals ask vendors?
To ensure adequate mitigation, risk teams can ask:
- Have you upgraded all instances of Grafana to versions 12.0.2+security-01, 11.6.3+security-01, 11.5.6+security-01, 11.4.6+security-01, or 11.3.8+security-01 to mitigate the risk of CVE-2025-6023 and CVE-2025-6197?
- Have you reviewed and disabled anonymous access in your Grafana configuration to reduce the risk of exploitation for CVE-2025-6023?
- Have you implemented a robust Content Security Policy (CSP) in your `grafana.ini` file to prevent the execution of untrusted external JavaScript and mitigate the XSS risk associated with CVE-2025-6023?
- Have you audited user accounts and sessions for any signs of suspicious activity that may have occurred prior to patching, considering that CVE-2025-6023 could potentially lead to session hijacking or account takeover?
Remediation Recommendations for Vendors Subject to This Risk
Ensure the following controls are in place without delay:
- Apply Security Updates: Patch Grafana to the recommended versions that address both vulnerabilities.
- Disable Anonymous Access: Set auth.anonymous: enabled = false in grafana.ini.
- Enforce Content Security Policy (CSP): If patching is delayed, enable a strong CSP with connect-src ‘self’ to limit script execution.
- Consolidate Organizations or Block Redirect Traffic: Simplify to single-org mode or use proxy rules to reject URLs containing %2F%5C..
- Audit Sessions and Logs: Monitor login events and dashboard requests for anomalies.
- Regularly Review Security Configurations: Validate anonymous access settings, CSP, version status, and redirect filters.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite released the Grafana – Jul2025 FocusTag™ on July 17, 2025, aligning with Grafana Labs’ public release of patches. This tag reveals which vendor systems are likely running vulnerable Grafana versions, enabling risk teams to:
- Identify Self-Hosted Exposure: Discover vendor IPs and subdomains with open Grafana panels.
- Prioritize Outreach: Focus on vendors whose telemetry indicates outdated versions or misconfigurations.
- Tailor Questions: Ask whether patches are applied, CSP is enforced, anonymous mode is off, and redirect mitigation is configured.
- Validate Configuration: Cross-check vendor claims with Black Kite insights about endpoint exposure and policy settings.
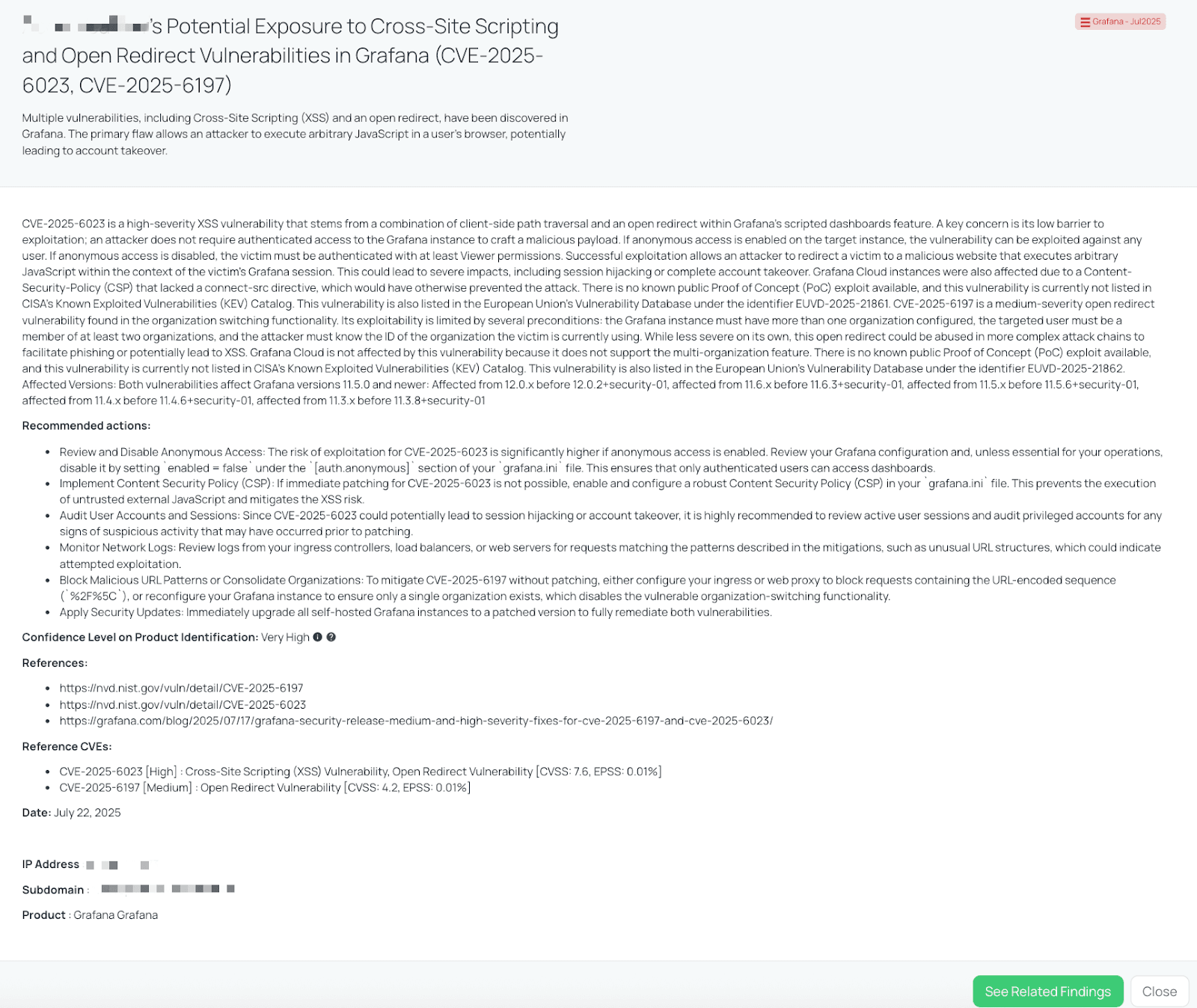
Black Kite’s Grafana – Jul2025 FocusTagTM details critical insights on the event for TPRM professionals.
ENHANCING TPRM RESILIENCE WITH BLACK KITE’S FOCUSTAGS™
Recent incidents like the unauthenticated RCE in SharePoint and cross-site scripting flaws in Grafana show how third-party software risks can escalate from isolated vulnerabilities to full-scale compromise. Black Kite’s FocusTags™ provide cybersecurity and TPRM teams with the critical visibility needed to manage this risk effectively.
With tags like SharePoint ToolShell and Grafana – Jul2025, Black Kite enables:
- Real-Time Exploit Intelligence: Identify which vendors are exposed to specific vulnerabilities—before they respond.
- Targeted Outreach: Prioritize which vendors to contact based on evidence of unpatched systems, exposed endpoints, or public telemetry.
- Risk-Aligned Questioning: Ask the right questions—not if vendors have “seen the CVE,” but whether they’ve rotated machine keys, enabled CSP, or blocked anonymous access.
- Operational Efficiency: Replace scattershot risk questionnaires with intelligent, focused interactions.
By transforming complex threat data into actionable exposure insights, Black Kite FocusTags™ help TPRM teams act faster, reduce time-to-containment, and protect business continuity across the extended vendor ecosystem.
ABOUT FOCUS FRIDAY
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FOCUSTAGSTM IN THE LAST 30 DAYS:
- SharePoint ToolShell : CVE-2025-49704, CVE-2025-49706, CVE-2025-53770, and CVE-2025-53771, Code Injection Vulnerability, Improper Authentication Vulnerability, Remote Code Execution Vulnerability, Path Traversal Vulnerability in Microsoft SharePoint.
- Grafana – Jul2025 : CVE-2025-6023, CVE-2025-6197, Cross-site Scripting (XSS) Vulnerability and Open Redirect Vulnerability in Grafana.
- MSSQL – Jul2025 : CVE-2025-49719, CVE-2025-49718, CVE-2025-49717, Information Disclosure Vulnerability, Remote Code Execution Vulnerability in Microsoft SQL Server.
- Redis – Jul2025 : CVE-2025-32023, CVE-2025-48367, Buffer Overflow Vulnerability, Denial of Service Vulnerability in Redis.
- Zimbra – Jul2025 : CVE-2019-9621, Server-Side Request Forgery (SSRF) Vulnerability in Zimbra.
- Citrix Bleed 2 : CVE-2025-6543, CVE-2025-5777, CVE-2025-5349, Buffer Overflow Vulnerability, Out-of-Bounds Memory Read Vulnerability, RCE Vulnerability, and Improper Access Control Vulnerability in NetScaler ADC and NetScaler Gateway.
- Wing FTP Server : CVE-2025-47812, Remote Code Execution Vulnerability in Wing FTP Server.
- MongoDB – Jun2025 : CVE-2025-6709, CVE-2025-6710, DoS Vulnerabilities in MongoDB.
- Mattermost : CVE-2025-4981, Arbitrary File Write Vulnerability in Mattermost.
- Grafana – Jun2025 : CVE-2025-4123, Cross-Site Scripting (XSS) Vulnerability, Open Redirect Vulnerability, SSRF Vulnerability in Grafana.
- Cisco ClamAV : CVE-2025-20260, CVE-2025-20234, Heap-based Buffer Overflow Vulnerability, Out-of-bounds Read Vulnerability in Cisco ClamAV.
- Elastic Kibana : CVE-2024-43706, Improper Authorization Vulnerability in Elastic Kibana.
- Tridium Niagara : CVE-2025-3936, CVE-2025-3937, CVE-2025-3938, CVE-2025-3939, CVE-2025-3940, CVE-2025-3941, CVE-2025-3942, CVE-2025-3943, CVE-2025-3944, and CVE-2025-3945, Multiple Critical Vulnerabilities in Niagara Framework, Niagara Enterprise Security.
See Black Kite’s full CVE Database and the critical TPRM vulnerabilities that have an applied FocusTagTM at https://resources.blackkite.com/cve-database/.
References
https://nvd.nist.gov/vuln/detail/CVE-2025-53770
https://nvd.nist.gov/vuln/detail/CVE-2025-53771
https://nvd.nist.gov/vuln/detail/CVE-2025-49704
https://nvd.nist.gov/vuln/detail/CVE-2025-49706
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-53770
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-53771
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-49704
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-49706
https://research.eye.security/sharepoint-under-siege
https://nvd.nist.gov/vuln/detail/CVE-2025-6197