FOCUS FRIDAY: THIRD-PARTY RISKS FROM ADOBE COLDFUSION AND BEEGO XSS VULNERABILITIES
Welcome to this week’s Focus Friday, where we examine three high‑profile vulnerabilities through a Third‑Party Risk Management (TPRM) lens. Today, we’ll dive into the critical remote code execution flaw in Ivanti Connect Secure As cyber threats continue to evolve in scope and complexity, Third-Party Risk Management (TPRM) teams are increasingly challenged to respond to emerging vulnerabilities with speed and precision. In this week’s Focus Friday, we examine two critical security issues—one affecting Adobe ColdFusion and the other targeting the Beego framework for Go. Both vulnerabilities expose organizations to serious risks, including remote code execution (RCE), access control bypass, and session hijacking.
We break down each incident from a TPRM perspective, highlighting the specific technical risks, vendor remediation recommendations, and key questions TPRM professionals should ask. Additionally, we demonstrate how Black Kite’s FocusTags™ help organizations identify affected vendors quickly and take meaningful action without wasting time on broad-based questionnaires or assumptions.
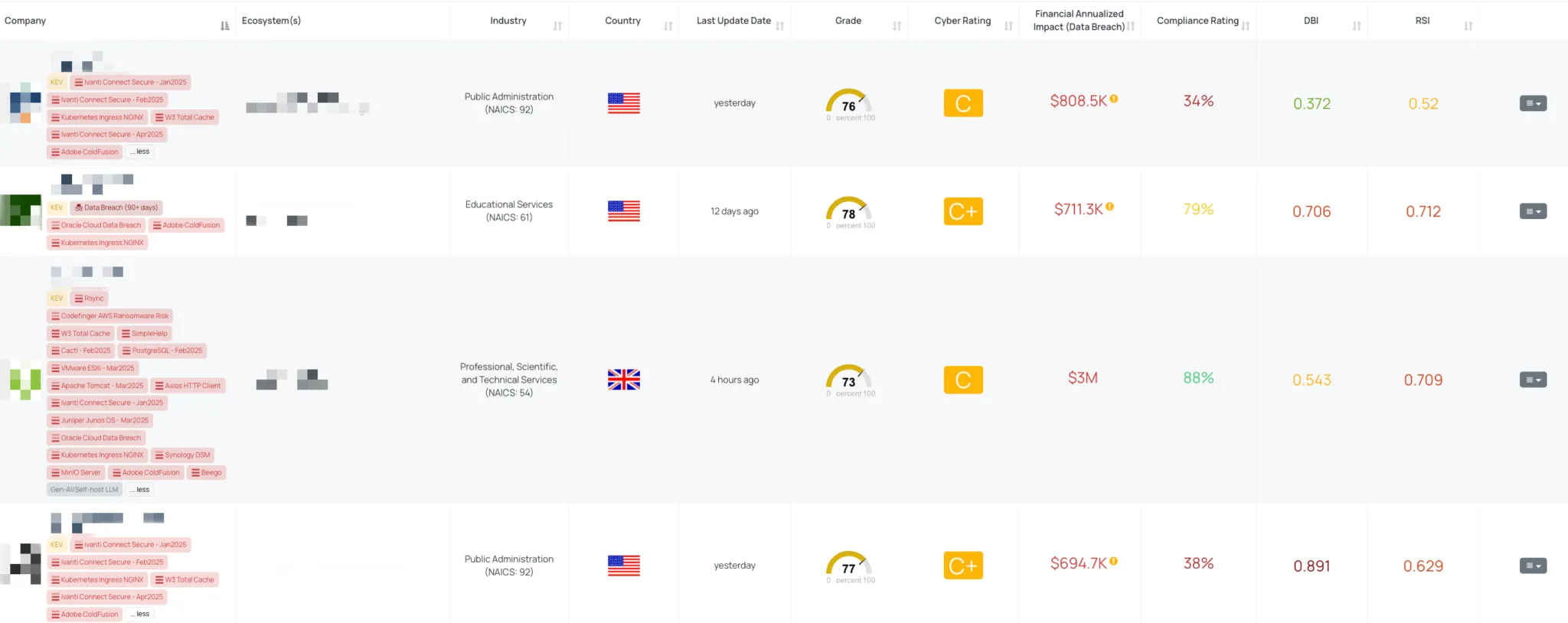
Filtered view of companies with Adobe ColdFusion FocusTag™ on the Black Kite platform.
Critical Adobe ColdFusion Vulnerabilities
What are the Critical Vulnerabilities Recently Discovered in Adobe ColdFusion?
A large set of critical vulnerabilities was recently identified in Adobe ColdFusion, affecting versions 2021, 2023, and 2025. These flaws, including CVE-2025-24446, CVE-2025-24447, CVE-2025-30281 through CVE-2025-30290, span multiple attack categories such as arbitrary file system read, remote code execution (RCE), OS command injection, access control bypass, and improper authentication. The CVSS scores for these vulnerabilities range from 7.5 to 9.8, and their EPSS scores indicate active risk, with some as high as 1.44%.
These vulnerabilities stem from insecure deserialization, improper input validation, access control weaknesses, and failure to sanitize user-supplied input.
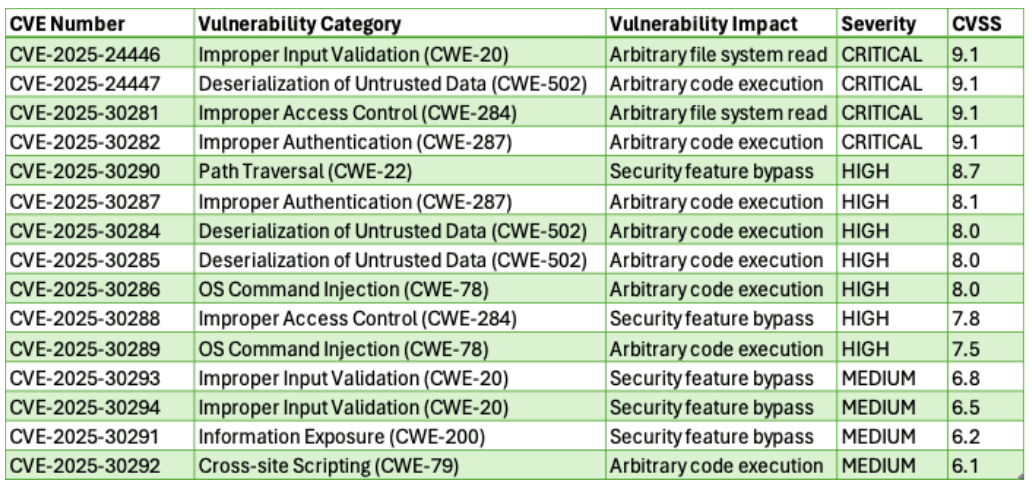
Adobe ColdFusion Critical Vulnerabilities Details Table
While no exploitation has been observed in the wild yet, and these CVEs are not currently listed in CISA’s Known Exploited Vulnerabilities (KEV) catalog, the public disclosure on April 8, 2025, along with multiple critical CVSS scores and high EPSS predictions, raises serious concerns.
Why Should TPRM Professionals Care About These Vulnerabilities?
TPRM professionals must be particularly cautious when it comes to ColdFusion deployments, as these vulnerabilities directly impact critical business applications hosted on ColdFusion platforms. Exploitation could lead to unauthorized file access, arbitrary code execution, or full system compromise—potentially exposing sensitive client data or internal business logic.
Adobe ColdFusion is frequently used in enterprise and government environments. The presence of deserialization vulnerabilities and OS-level command injection significantly increases the risk of lateral movement, persistent access, and data exfiltration within third-party ecosystems. Additionally, since these issues affect all ColdFusion versions prior to the latest updates, unpatched systems are common in unmanaged or aging vendor environments.
What Questions Should TPRM Professionals Ask Vendors About These Vulnerabilities?
To assess vendor exposure, TPRM professionals should consider asking:
- Have you updated all instances of Adobe ColdFusion to the latest versions (ColdFusion 2021 Update 19, ColdFusion 2023 Update 13, ColdFusion 2025 Update 1) to mitigate the risk of the mentioned CVEs?
- Can you confirm if you have implemented the recommended actions such as auditing access controls and logs, reviewing file upload and deserialization controls, and limiting application exposure to mitigate the risk of these vulnerabilities?
- Have you applied the security configuration settings included in the ColdFusion Security documentation and reviewed the respective Lockdown guides as recommended by Adobe?
- Have you updated your ColdFusion JDK/JRE LTS version to the latest update release and set the recommended JVM flags on a JEE installation of ColdFusion as a secure practice?
Remediation Recommendations for Vendors Subject to This Risk
Vendors using ColdFusion should take the following technical steps to address these vulnerabilities:
- Patch Immediately: Upgrade ColdFusion to the latest versions—2025 Update 1, 2023 Update 13, or 2021 Update 19.
- Secure Deserialization and Upload Paths: Review all serialization-related functions and restrict unsafe classes using Adobe’s serial filter documentation.
- Apply JVM Flags for JEE Installations: Set -Djdk.serialFilter values as recommended by Adobe to block dangerous object types during deserialization.
- Isolate ColdFusion Services: Place ColdFusion services behind firewalls or WAFs and restrict access to only required IP ranges.
- Audit Access Logs: Review logs for unauthorized access attempts or security feature misuse, especially around the setAdminPassword, upload handlers, or URL routing logic.
- Follow Adobe’s Lockdown Guide: Apply recommended security configurations from Adobe’s official lockdown and JVM guidance for your ColdFusion version.
How TPRM Professionals Can Leverage Black Kite for This Vulnerability
Black Kite published the Adobe ColdFusion FocusTag™ on April 11, 2025, to help organizations identify at-risk vendors rapidly. Using internet-wide scanning, subdomain fingerprinting, and exposed asset detection, Black Kite identifies vendors that host ColdFusion installations vulnerable to the disclosed CVEs.
TPRM teams can use this FocusTag™ to immediately narrow down the list of potentially impacted vendors, enabling fast risk prioritization, informed questioning, and effective outreach. By providing visibility into external-facing infrastructure and the likelihood of exposure, Black Kite simplifies complex supply chain risk monitoring in real time.
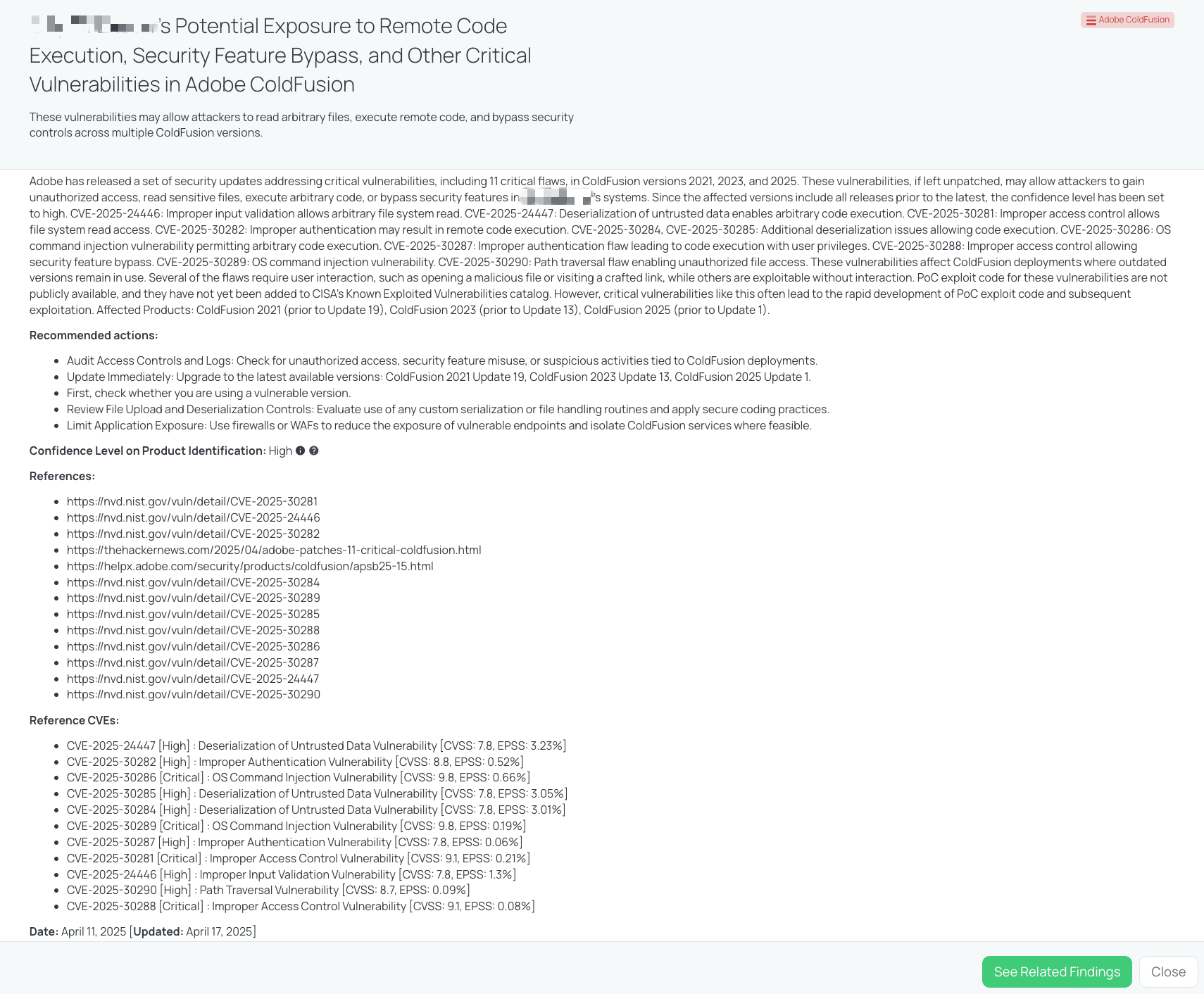
Black Kite’s Adobe ColdFusion FocusTagTM details critical insights on the event for TPRM professionals.
CVE-2025-30223: Beego RenderForm() XSS Vulnerability
What is the Critical XSS Vulnerability in the Beego Framework?
CVE-2025-30223 is a critical Cross-Site Scripting (XSS) vulnerability discovered in the Beego web framework for Go, affecting all versions up to and including v2.3.5. The issue resides in the RenderForm() function, which dynamically generates HTML form fields. This function improperly handles user-supplied input and outputs it as raw HTML using template.HTML, bypassing Go’s built-in HTML escaping mechanisms.
The underlying problem originates from a helper function, renderFormField(), which uses fmt.Sprintf() to construct form input fields with values such as label, name, and value directly injected into the HTML structure. Since no HTML escaping is applied to these values, attackers can inject JavaScript payloads into form fields. This makes it possible to exploit the vulnerability through:
- Attribute Injection, such as injecting code into the DisplayName field (onmouseover=”alert(‘XSS’)”),
- Content Injection, such as inserting <script> tags into a textarea field.
With a CVSS score of 9.3, the vulnerability poses significant risk, especially in applications where user-generated content is displayed to others. Although this CVE is not listed in CISA’s KEV catalog as of now, a public proof-of-concept (PoC) was made available in early April 2025, demonstrating how JavaScript payloads can be rendered and executed in real-world browser sessions.
Why Should TPRM Professionals Care About This Vulnerability?
Beego is a widely adopted Go framework, popular among SaaS and platform providers due to its performance and simplicity. Applications that use RenderForm() with user-controlled inputs are highly susceptible to exploitation. This vulnerability is especially problematic for TPRM because:
- It allows client-side code execution in users’ browsers.
- It enables session hijacking, credential theft, and fake form injection.
- It can compromise administrative interfaces, resulting in account takeover of privileged users.
Vendors using Beego without proper patching or escaping mechanisms expose their customers to client-side threats that are difficult to detect from the backend. Moreover, XSS vulnerabilities often serve as an entry point for further attacks, including credential stuffing, business logic abuse, or malware injection.
What Questions Should TPRM Professionals Ask Vendors About This Vulnerability?
To assess the exposure of vendors using the Beego framework, consider asking the following:
- Have you upgraded all instances of Beego Framework to version v2.3.6 or later to mitigate the risk of CVE-2025-30223?
- Can you confirm if you have reviewed all components using the RenderForm() function in your Beego application and ensured that no untrusted data is passed directly without escaping?
- Have you implemented a strong Content Security Policy (CSP) to restrict which scripts can be executed in the browser, as a measure to prevent the execution of malicious JavaScript injected via XSS?
- Have you audited stored data that might have been injected with XSS payloads before patching, especially in user-generated fields like DisplayName or Bio, to ensure no malicious scripts are present?
Remediation Recommendations for Vendors Subject to This Risk
Organizations using vulnerable Beego versions should take immediate actions:
- Upgrade Beego to v2.3.6 or later, which properly escapes all HTML input using template.HTMLEscapeString() inside RenderForm() and its helper methods.
- Sanitize All Inputs: Audit application code to ensure no unescaped user data is being passed to the UI layer.
- Implement CSP: Use Content Security Policy headers to prevent the execution of inline or unauthorized scripts.
- Review Cookies: Set HttpOnly and Secure flags on cookies to prevent session theft through JavaScript.
- Scan and Monitor: Use automated security scanners to detect residual or future XSS vulnerabilities and monitor for unusual activity within administrative dashboards.
- Audit Stored Data: Check stored fields like DisplayName and Bio for embedded scripts that may persist across sessions.
How TPRM Professionals Can Leverage Black Kite for This Vulnerability
Black Kite published the FocusTag™ for the Beego XSS vulnerability (CVE-2025-30223) on April 11, 2025. This tag identifies vendors whose exposed applications may be using vulnerable versions of the Beego framework. By analyzing HTML source code, script libraries, and domain-level fingerprints, Black Kite provides asset-specific intelligence such as affected subdomains or externally facing interfaces.
With the tag’s VERY HIGH confidence level, TPRM professionals can quickly pinpoint which vendors require immediate outreach. The FocusTag™ streamlines due diligence by narrowing down the scope of concern, enabling organizations to conduct targeted assessments instead of issuing blanket questionnaires.
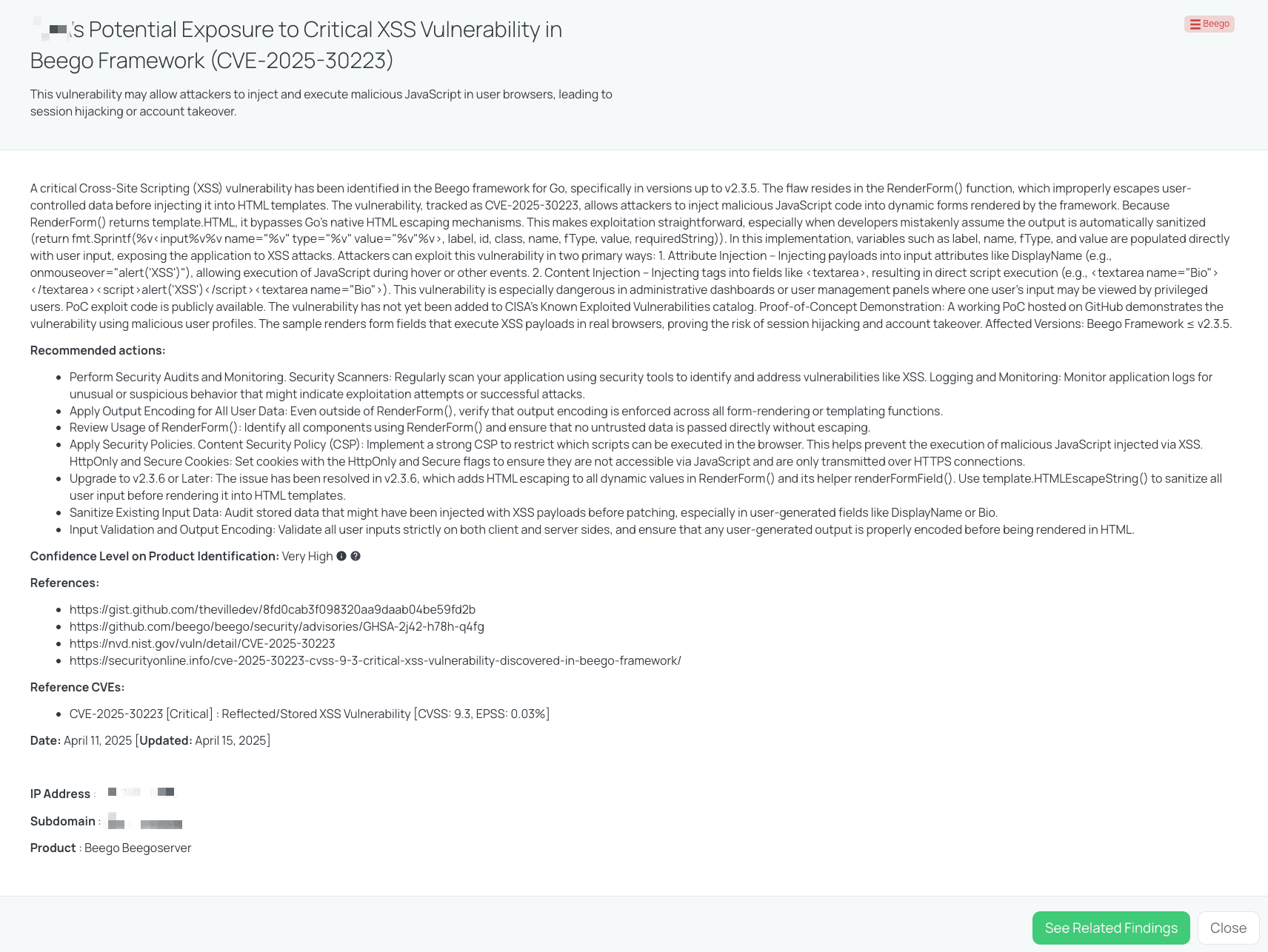
Black Kite’s Beego FocusTagTM details critical insights on the event for TPRM professionals.
Enhancing TPRM With Black Kite FocusTags™
The rise of exploitable software supply chain vulnerabilities—such as those in Adobe ColdFusion and Beego—demands a smarter, more targeted approach to Third-Party Risk Management. Black Kite’s FocusTags™ deliver that precision by equipping organizations with real-time, asset-level intelligence tied to the latest threats. Here’s how these tags empower TPRM teams:
- Threat-Centric Vendor Identification: Know exactly which vendors in your ecosystem are affected by vulnerabilities like CVE-2025-30223 or CVE-2025-24447—no guesswork, no overreach.
- Risk-Based Prioritization: Align vendor outreach efforts with the severity of each threat and the business criticality of the impacted third parties.
- Actionable Engagement: Conduct targeted conversations with vendors, backed by knowledge of exposed assets, vulnerable software versions, and available patches.
- Continuous Security Visibility: Access a constantly updated view of your third-party landscape, driven by internet-wide scanning, external intelligence, and contextual enrichment.
FocusTags™ are more than alerts—they are operational tools built to support agile, scalable risk management strategies. Whether responding to deserialization flaws in ColdFusion or XSS vectors in Beego, Black Kite’s platform ensures TPRM professionals are equipped with the right insights, right when they need them.
About Focus Friday
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FocusTagsTM in the Last 30 Days:
- Adobe ColdFusion : CVE-2025-24446 CVE-2025-24447 CVE-2025-30281 CVE-2025-30282 CVE-2025-30284 CVE-2025-30285 CVE-2025-30286 CVE-2025-30287 CVE-2025-30288 CVE-2025-30289 CVE-2025-30290, Deserialization of Untrusted Data, Improper Authentication, Improper Access Control, OS Command Injection, Improper Input Validation, Path Traversal Vulnerabilities in Adobe ColdFusion.
- Beego: CVE-2025-30223, Reflected/Stored XSS Vulnerabilities in Beego Web Framework.
- Ivanti Connect Secure : CVE‑2025‑22457, Stack‑based Buffer Overflow Vulnerability in Ivanti Connect Secure, Ivanti Policy Secure, and Ivanti ZTA Gateways.
- FortiSwitch : CVE‑2024‑48887, Unverified Password Change Vulnerability in Fortinet FortiSwitch web interface.
- MinIO : CVE‑2025‑31489, Improper Verification of Cryptographic Signature Vulnerability in MinIO Go module package.
- Kubernetes Ingress NGINX : CVE-2025-1097, CVE-2025-1098, CVE-2025-24514, CVE-2025-1974, Improper Isolation or Compartmentalization Vulnerability, Remote Code Execution Vulnerability in Kubernetes ingress-nginx controller.
- Synology DSM : CVE-2024-10441, Remote Code Execution Vulnerability in Synology BeeStation OS (BSM), Synology DiskStation Manager (DSM).
- Synapse Server : CVE-2025-30355, Improper Input Validation Vulnerability in Matrix Synapse Server.
- Juniper Junos OS – Mar2025 : CVE-2025-21590, Improper Isolation or Compartmentalization Vulnerability in Juniper Junos OS.
- SAP NetWeaver – Mar2025 : CVE-2017-12637, Directory Traversal Vulnerability in SAP NetWeaver Application Server.
- MongoDB – Mar2025 : CVE-2025-0755, Heap-based Buffer Overflow Vulnerability in MongoDB’s C driver library (libbson).
- DrayTek Vigor – Mar2025 : CVE-2024-41334, CVE-2024-41335, CVE-2024-41336, CVE-2024-41338, CVE-2024-41339, CVE-2024-41340, CVE-2024-51138, CVE-2024-51139, Code Injection Vulnerability, Arbitrary Code Execution Vulnerability Observable Discrepancy, Sensitive Information Disclosure Plaintext Storage of a Password, Sensitive Information Disclosure NULL Pointer Dereference, DoS Vulnerability Code Injection Vulnerability, Arbitrary Code Execution Vulnerability Unrestricted Upload of File with Dangerous Type, Arbitrary Code Execution Vulnerability Stack-based Buffer Overflow Vulnerability Buffer Overflow Vulnerability Cross-Site Request Forgery (CSRF) Vulnerability in DrayTek Vigor Routers.
- VMware ESXi – Mar2025 : CVE-2025-22224, CVE-2025-22225, CVE-2025-22226, Heap Overflow Vulnerability, TOCTOU Race Condition Vulnerability, Arbitrary Write Vulnerability, Information Disclosure Vulnerability in VMware ESXi.
- Apache Tomcat – Mar2025 : CVE-2025-24813, Remote Code Execution Vulnerability, Information Disclosure and Corruption Vulnerability in Apache Tomcat.
References
https://helpx.adobe.com/security/products/coldfusion/apsb25-15.html
https://thehackernews.com/2025/04/adobe-patches-11-critical-coldfusion.html
https://nvd.nist.gov/vuln/detail/CVE-2025-24446
https://nvd.nist.gov/vuln/detail/CVE-2025-24447
https://nvd.nist.gov/vuln/detail/CVE-2025-30281
https://nvd.nist.gov/vuln/detail/CVE-2025-30282
https://nvd.nist.gov/vuln/detail/CVE-2025-30284
https://nvd.nist.gov/vuln/detail/CVE-2025-30285
https://nvd.nist.gov/vuln/detail/CVE-2025-30286
https://nvd.nist.gov/vuln/detail/CVE-2025-30287
https://nvd.nist.gov/vuln/detail/CVE-2025-30288
https://nvd.nist.gov/vuln/detail/CVE-2025-30289
https://nvd.nist.gov/vuln/detail/CVE-2025-30290
https://nvd.nist.gov/vuln/detail/CVE-2025-30223
https://github.com/beego/beego/security/advisories/GHSA-2j42-h78h-q4fg
https://gist.github.com/thevilledev/8fd0cab3f098320aa9daab04be59fd2b