Focus Friday: Grafana Vulnerability and Cisco ClamAV Risks From a TPRM Perspective
Written by: Ferdi Gül
This week’s Focus Friday highlights two critical areas of concern for Third-Party Risk Management (TPRM) professionals: a high-severity vulnerability in Grafana and multiple security flaws in Cisco’s ClamAV antivirus engine. As organizations continue to rely heavily on monitoring tools and embedded antivirus components provided by third parties, vulnerabilities in these platforms can open the door to exploitation, data compromise, and service disruptions.
In this edition, we examine CVE-2025-4123 in Grafana, which enables attackers to perform cross-site scripting (XSS) and server-side request forgery (SSRF) using malicious plugin injection. We also break down CVE-2025-20260 and CVE-2025-20234 in ClamAV, which threaten availability and potentially allow code execution under specific configurations. Both Grafana and Cisco ClamAV have FocusTags™ now available in Black Kite’s platform to help security teams quickly pinpoint third-party exposure and prioritize vendor outreach. The Black Kite research group issues FocusTags™ on the most critical vulnerabilities impacting third-party cyber ecosystems from the full CVE Database.
CVE‑2025‑4123 – Grafana XSS, Open Redirect, and SSRF Vulnerabilities
Grafana is an open-source analytics and interactive data visualization platform. It is widely used for monitoring and observability across IT systems, often in combination with time-series databases like Prometheus, InfluxDB, or Graphite.
What is CVE‑2025‑4123?
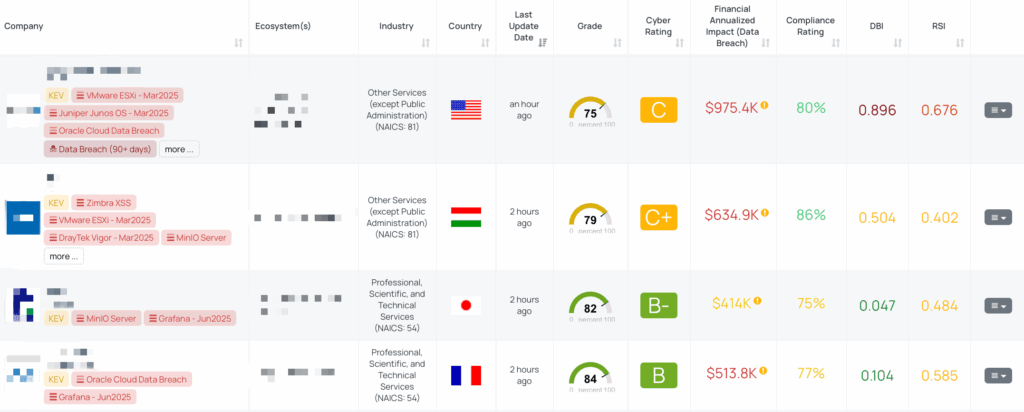
CVE‑2025‑4123 is a high-severity vulnerability (CVSS: 7.6 / EPSS: 1.61%) affecting Grafana’s plugin loading logic. It combines a client-side path traversal with an open redirect flaw to allow attackers to inject and load malicious frontend plugins. These plugins can execute arbitrary JavaScript in a user’s session, leading to a cross-site scripting (XSS) attack. If the optional Grafana Image Renderer plugin is installed, attackers can also exploit this redirect mechanism to conduct full-read server-side request forgery (SSRF) against internal services.
The vulnerability was reported through a bug bounty program on April 26, 2025, publicly disclosed on May 21, and patched shortly thereafter. The PoC exploit for CVE‑2025‑4123 is publicly available, yet this flaw is not listed in CISA’s Known Exploited Vulnerabilities catalog. Its high severity, the ease of exploitation—even users with only Viewer permissions can trigger it—and the fact that patches are already released make it a top priority for immediate remediation. Successful attacks can inject a malicious plugin to execute arbitrary JavaScript in the user’s session and, if the Image Renderer plugin is present, perform full-read SSRF to internal services—potentially exposing sensitive data across the network. In the European Union’s Vulnerability Database, the corresponding entry for this vulnerability is EUVD-2025-16107.
Why should TPRM professionals care?
Grafana is a widely adopted platform for data visualization and monitoring. If a vendor uses Grafana in their environment, a successful exploit could result in session hijacking, dashboard tampering, or even internal data exfiltration via SSRF. The exploit can be triggered without elevated privileges and even works with anonymous access enabled—making it particularly risky in exposed internet-facing deployments.
From a third-party risk management perspective, vendors running unpatched Grafana instances may unintentionally expand your organization’s attack surface. This is especially critical if the affected vendors handle internal dashboards, service metrics, or manage infrastructure components with access to sensitive resources.
What questions should TPRM professionals ask vendors?
To evaluate a vendor’s exposure and response, consider asking:
- Have you upgraded your Grafana instances to one of the patched versions (v11.0.5+security-01, v11.1.6+security-01, v11.2.1+security-01, v11.0.6+security-01, v11.1.7+security-01, v11.2.2+security-01) to mitigate the risk of CVE-2024-9264?
- Can you confirm if the DuckDB binary has been removed from your system’s PATH or uninstalled entirely to prevent exploitation of the CVE-2024-9264 vulnerability?
- Have you implemented measures to regularly review system logs for suspicious activity, specifically related to potential exploitation of the ‘SQL Expressions’ feature in Grafana?
- Can you confirm if you have implemented proper access controls for users with Viewer permissions or higher to prevent unauthorized exploitation of the CVE-2024-9264 vulnerability?
Remediation recommendations for affected vendors
To mitigate the risk of CVE‑2025‑4123, vendors should:
- Apply security patches immediately for all affected versions.
- Disable anonymous access unless strictly required.
- Restrict or disable open redirect endpoints (e.g., /redirect) via web server or reverse proxy rules.
- Implement plugin whitelisting to only allow known, trusted sources.
- Strengthen Content Security Policy (CSP) by disallowing connections to untrusted origins.
- Monitor Grafana logs for access patterns involving path traversal or attempts to load external plugins.
How Black Kite helps with this vulnerability
Black Kite released the Grafana – Jun 2025 FocusTag on June 17, 2025, identifying which vendors are running vulnerable versions of Grafana. The FocusTag includes precise asset information such as IP addresses and subdomains where the risk is present—empowering TPRM teams to take immediate and focused action.
Rather than sending mass questionnaires, customers can use the FocusTag to zero in on vendors with actual exposure, drastically reducing manual overhead. If a vendor previously patched and later reverts to a vulnerable version, Black Kite’s continuous monitoring ensures timely alerts—adding both speed and consistency to the remediation process.
CVE‑2025‑20260 & CVE‑2025‑20234 – Cisco ClamAV
ClamAV (Clam AntiVirus) is an open-source antivirus engine designed for detecting malware, trojans, viruses, and other malicious threats—particularly in email and file scanning environments.
What are these ClamAV vulnerabilities?
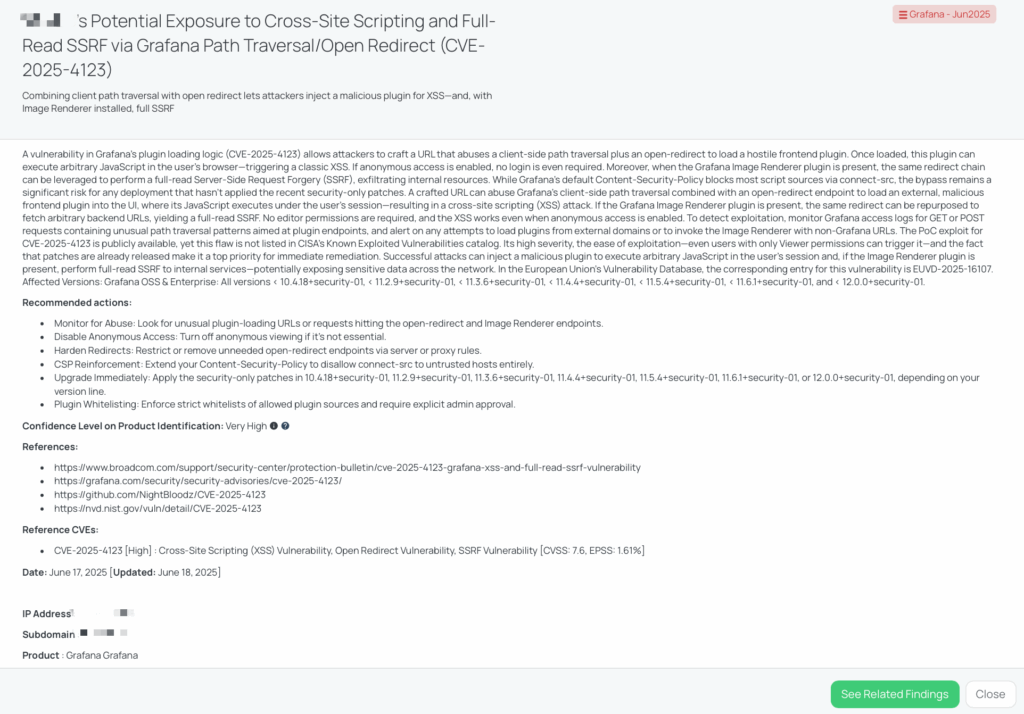
Two new vulnerabilities—CVE‑2025‑20260 (critical) and CVE‑2025‑20234 (medium)—were found in Cisco’s ClamAV antivirus:
- CVE‑2025‑20260: A heap-based buffer overflow in ClamAV’s PDF parser (CVSS 9.8 / EPSS 0.11%). This flaw becomes exploitable under non-default configurations where max-filesize ≥ 1024 MB and max-scan-size ≥ 1025 MB, potentially leading to denial-of-service or remote code execution. High confidence in the configuration dependency reduces overall exploit probability.
- CVE‑2025‑20234: An out-of-bounds read in the UDF file parser (CVSS 5.3 / EPSS 0.07%), potentially exposing data in temporary files or causing a crash/DoS.
Both vulnerabilities impact ClamAV versions prior to 1.4.3 (and pre-1.0.9 in the older series). No public exploit code exists yet, and neither entry appears in CISA’s KEV catalog. They were patched in ClamAV 1.4.3 and 1.0.9 on June 19, 2025. The EUVD identifier for the buffer overflow is EUVD‑2025‑18658.
Why should TPRM professionals care?
ClamAV is embedded in many Cisco products (e.g., Secure Endpoint Connector, mail gateways). A successful exploit—particularly the PDF-based overflow—could crash antivirus scanning or escalate to remote code execution. This undermines critical security mechanisms (antivirus, email/web filtering), exposing workflows and data to malware threats. From a third-party risk perspective, vendors using vulnerable ClamAV versions may unintentionally weaken layered defenses, increasing risk to your organization.
What questions should TPRM professionals ask vendors?
To clarify vendor exposure and response, ask:
- Have you updated all instances of ClamAV to versions 1.4.3 or 1.0.9 to mitigate the risk of CVE-2025-20260 and CVE-2025-20234?
- Can you confirm if your ClamAV configuration settings, specifically max-filesize and max-scan-size limits, have been adjusted to prevent excessive memory allocations that could be exploited in attack scenarios related to CVE-2025-20260?
- Have you implemented system-level controls such as cgroups, SELinux/AppArmor, or container resource limits to restrict memory and CPU usage of ClamAV processes and minimize the effect of possible denial-of-service conditions related to CVE-2025-20234?
- Can you confirm if you have isolated high-risk workloads by running ClamAV in sandboxed environments or containers with limited privileges, especially when processing untrusted files from external sources, to reduce the potential impact of exploitation of CVE-2025-20260 and CVE-2025-20234?
Remediation recommendations for affected vendors
To mitigate these vulnerabilities, vendors should:
- Upgrade to ClamAV 1.4.3 or 1.0.9 immediately.
- Audit configuration: Reset max-filesize and max-scan-size to conservative default values unless large-file scanning is essential.
- Sandbox scanning: Execute ClamAV in restricted containers or with limited privileges.
- Enforce resource limits: Use cgroups, SELinux/AppArmor, or container caps to constrain RAM and CPU usage.
- Monitor and log carefully: Watch for scan failures, crashes, or unusual file submissions—integrate logs into SIEM.
- Implement defense-in-depth: Use ClamAV results in concert with IDS/EDR and network segmentation.
- Restrict network exposure: Avoid exposing ClamAV daemons; enforce firewall or network segmentation.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite’s Cisco ClamAV FocusTag (published June 19, 2025) identifies vendors running vulnerable ClamAV builds across their environments. It provides asset-level data—specific IPs and subdomains—with risky ClamAV instances. TPRM teams can directly target remediation efforts by contacting only those vendors with confirmed exposure. As vendors apply patches or adjust configurations, Black Kite’s continuous monitoring verifies fixes and flags any regressions—ensuring efficient and precise third-party risk handling.
Enhancing TPRM Precision With Black Kite’s FocusTags™
Black Kite’s FocusTags™ empower organizations to streamline and fortify their Third-Party Risk Management (TPRM) workflows—especially when responding to critical vulnerabilities like those found in Grafana and ClamAV. These tags are engineered to provide:
- Immediate Vendor Visibility: Quickly identify which vendors are running affected versions of Grafana or ClamAV, enabling faster triage and prioritization.
- Configuration-Aware Risk Context: FocusTags™ don’t just surface affected versions—they account for real-world exploitability factors, like ClamAV’s scanning thresholds or plugin exposure in Grafana.
- Targeted Vendor Dialogues: Equip TPRM teams with detailed, vulnerability-specific questions to uncover security gaps or mitigation delays among third parties.
- Operational Intelligence at the Asset Level: By surfacing IP addresses and subdomains hosting vulnerable services, FocusTags™ help organizations validate exposure and take decisive action.
As third-party ecosystems grow more complex, FocusTags™ offer security teams the clarity and agility needed to reduce uncertainty, limit overcommunication, and focus their efforts where it truly matters. With threats surfacing rapidly and remediation timelines tightening, FocusTags™ serve as a critical differentiator for proactive and data-driven TPRM.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
About Focus Friday
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FocusTagsTM in the Last 30 Days:
- Grafana – Jun2025 : CVE-2025-4123, Cross-Site Scripting (XSS) Vulnerability, Open Redirect Vulnerability, SSRF Vulnerability in Grafana.
- Cisco ClamAV : CVE-2025-20260, CVE-2025-20234, Heap-based Buffer Overflow Vulnerability, Out-of-bounds Read Vulnerability in Cisco ClamAV.
- Elastic Kibana : CVE-2024-43706, Improper Authorization Vulnerability in Elastic Kibana.
- Tridium Niagara : CVE-2025-3936, CVE-2025-3937, CVE-2025-3938, CVE-2025-3939, CVE-2025-3940, CVE-2025-3941, CVE-2025-3942, CVE-2025-3943, CVE-2025-3944, and CVE-2025-3945, Multiple Critical Vulnerabilities in Niagara Framework, Niagara Enterprise Security.
- Roundcube Webmail – Jun2025 : CVE-2025-49113, Remote Code Execution Vulnerability, Deserialization of Untrusted Data in Roundcube Webmail.
- ScreenConnect – May2025 : CVE-2025-3935, Improper Authentication Vulnerability in ConnectWise ScreenConnect.
- Zimbra – May2025 : CVE-2024-27443, Cross-Site Scripting (XSS) Vulnerability in Zimbra Collaboration (ZCS).
- DrayTek Vigor – May2025 : CVE-2024-12987, OS Command Injection Vulnerability in DrayTek Vigor Routers.
- Atlassian Jira Data Center : CVE-2025-22157, Privilege Escalation Vulnerability in Jira Core Data Center, Jira Core Server, Jira Service Management Data Center, Jira Service Management Server.
- Tornado Web Server : CVE-2025-47287, DoS Vulnerability in Tornado Web Server.
- MDaemon Email Server : CVE-2024-11182, Cross-Site Scripting (XSS) Vulnerability in MDaemon Email Server.
- Ivanti EPMM – May2025 : CVE-2025-4427, CVE-2025-4428, Authentication Bypass and Remote Code Execution Vulnerability in Ivanti Endpoint Manager Mobile (EPMM)
- SysAid On-Premises : CVE-2025-2775, CVE-2025-2776, CVE-2025-2777, XML External Entity (XXE) Injection Vulnerability in SysAid On-Premises.
- Apache ActiveMQ – May2025 : CVE-2025-27533, Memory Allocation with Excessive Size Value in Apache ActiveMQ.
- Webmin: CVE-2025-2774, CRLF Injection Privilege Escalation Vulnerability in Webmin.
- Couchbase Server: CVE-2025-46619, LFI Vulnerability in Couchbase Server.
See Black Kite’s full CVE Database and the critical TPRM vulnerabilities that have an applied FocusTag at https://blackkite.com/cve-database/.
References
- https://nvd.nist.gov/vuln/detail/CVE-2025-4123
- https://www.broadcom.com/support/security-center/protection-bulletin/cve-2025-4123-grafana-xss-and-full-read-ssrf-vulnerability
- https://grafana.com/security/security-advisories/cve-2025-4123/
- https://github.com/NightBloodz/CVE-2025-4123
- https://nvd.nist.gov/vuln/detail/CVE-2025-20260
- https://nvd.nist.gov/vuln/detail/CVE-2025-20234
- https://blog.clamav.net/2025/06/clamav-143-and-109-security-patch.html
- https://github.com/Cisco-Talos/clamav/releases
- https://github.com/advisories/GHSA-596c-w2jc-jmmx

