Do You Monitor Your Suppliers? ISO/IEC 27001 Regulations Say You Should
Written by: Black Kite
Suppliers, in general third parties, have become one of the weaker links in the system. Recent TicketMaster data breach show how third parties may carry too much risk to your organization. Thus, they should be constantly monitored as ISO 27001 standard suggests.
What is ISO/IEC 27001?
ISO/IEC 27001 (some only write ISO 27001) is an information security standard created by ISO and IEC jointly to standardize cyber security practices. It provides certain control items in 18 categories to improve cyber security of an organization. Compliance to ISO 27001 standard provides benefit to an organization to better manage their IT systems with those control items. Besides, organizations that meet ISO 27001 requirements can be certified after an audit. Even though, it is not updated since 2013, the regulations are well-put and still respected.
What is 3rd-party cyber risk?
A recent survey conducted by Ponemon Institute reveals that 56% of companies have experienced a 3rd-party breach in 2017, which is an increase of 7% compared to previous year. Data breaches caused by third parties cost millions of dollars to large companies.
Third-parties include broad range of companies a company directly worked with such as data management companies, law firms, e-mail providers, web hosting companies, subsidiaries, vendors, sub-contractors, basically any company whose employees or systems have access to your systems or your data. However, third-party cyber risk is not limited to these companies. Any external software or hardware that you use for your business also poses a cyber risk. For instance, very recently UK-based TicketMaster experienced a data breach of potentially 40 thousand customer information because of a chatbot software. For more info on third-party cyber risk, check out our 2018 third-party cyber risk report here.
Do third parties/suppliers have to comply ISO 27001 standards?
Yes. ISO/IEC 27001, Section A15, defines five controls for Supplier Relationships. Based on these control, third party compliance can be checked in 5 steps.
5 steps to check supplier ISO/IEC 27001 compliance
- Create an information security policy for supplier relationships that address the processes and procedures to be implemented by the organization to mitigate the risks associated with the vendor.
- Make the supplier sign a contractual agreements to ensure that there will not be any misconceptions in future. For example, the organization may include legal and regulatory requirements, ‘right to audit’ clause, Terms & Conditions etc., in the contractual agreement
- Be clear about the agreements that include requirements to address information security risks associated with Information and communication technology services such as monitoring process, defining rules for sharing information etc.
- Monitor and review supplier services. The organization should monitor, review and conduct audits on supplier services at regular intervals to ensure that supplier is adhere to the terms and conditions as per the agreement.
- Manage change to supplier services such as updation of information security policy, use of new technologies/tools, changes to physical location, improvised services etc.
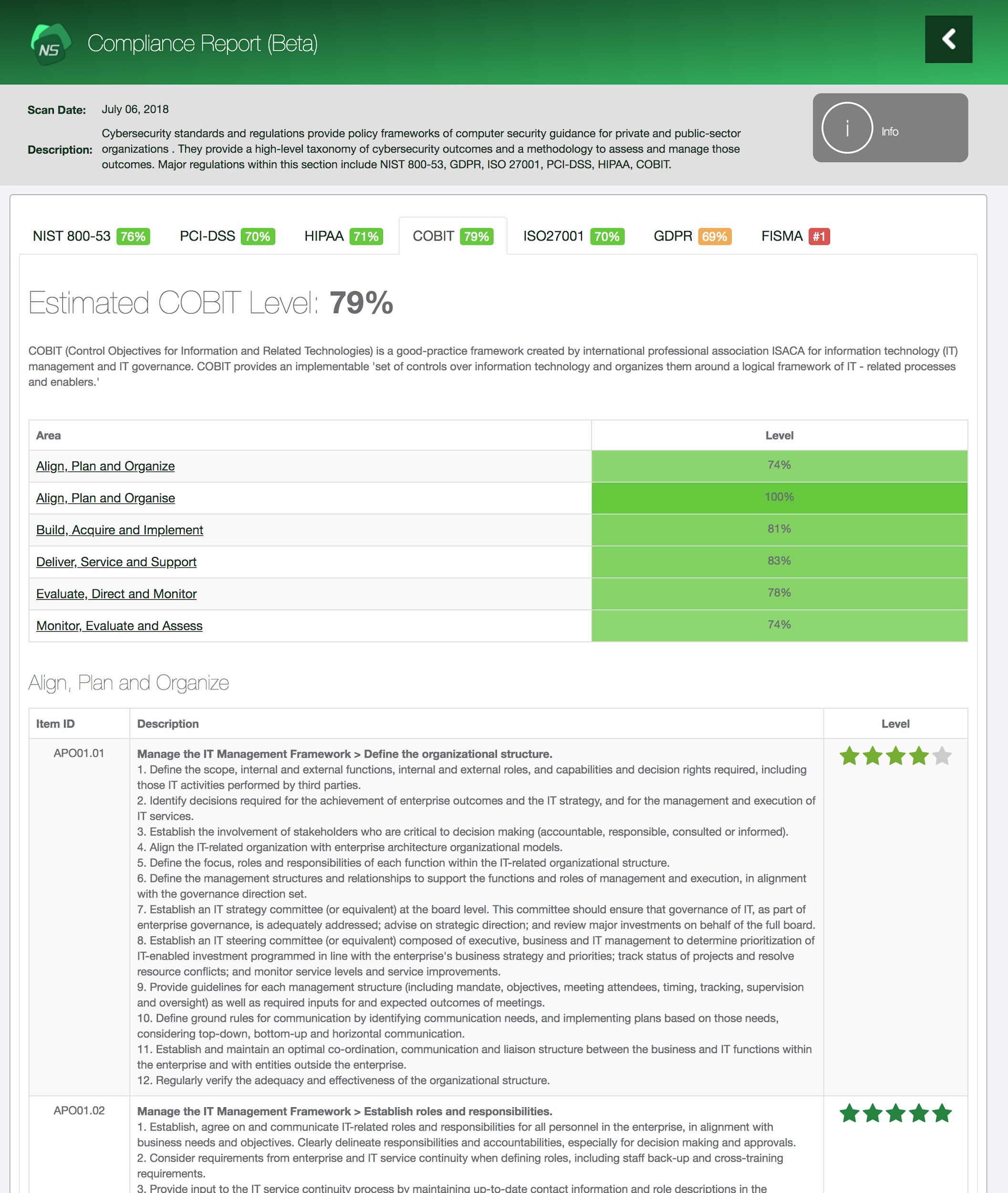
How to use Black Kite for third party for ISO/IEC 27001 compliance
ISO 27001 recommends to monitor suppliers for ISO 27001 compliance and provide risk assessment them. The risk assessment can be done in an old-school fashion questionnaire method. Unfortunately, some third-parties are not so eager to respond, questions might not cover all the risks, and the answers will be only depend on what the third-party knows about it IT structure.
Thus, Black Kite Cyber Risk Scorecard, with its benchmarking reports, provides risk scoring and ranking for companies and their third parties. Besides, it also check compliance to well-known cybersecurity frameworks including ISO 27001. Even prior to work with a third party, its ISO 27001-compliance can easily be checked with Black Kite Cyber Risk Scorecard. Act now and learn your company and related third parties here.