COLLABORATION TO WIN THE WAR ON CYBER THREATS
In every part of the world, security teams are at war. And they’re on the losing side. Cyber attackers are becoming increasingly sophisticated, working together to amplify their efforts. Adversaries are actively collaborating — sharing intelligence and tactics to optimize their attacks.
On the other side of the trenches — despite doing business with hundreds or even thousands of third parties — companies are fighting their security battles alone. Corporations tend to defend their assets like lone wolves, with security and threat intelligence siloed within each link of the supply chain. While some know how to shore up their defenses, others are left open to attack. This lack of unity often leads to infighting and companies clashing with their own third parties — all while attackers coordinate their attacks to exploit weaknesses.
We know ransomware groups and bad actors are working together because the data shows an increasing prevalence of repeat victims — often in rapid succession. According to the Black Kite State of Ransomware 2024 report, in 2023, 104 companies fell victim to two attacks by different ransomware groups, with a clear downward trend in the amount of time between each attack. This indicates that ransomware groups are communicating and strategizing together, monitoring other attacks so they can strike while a victim is still unprotected.
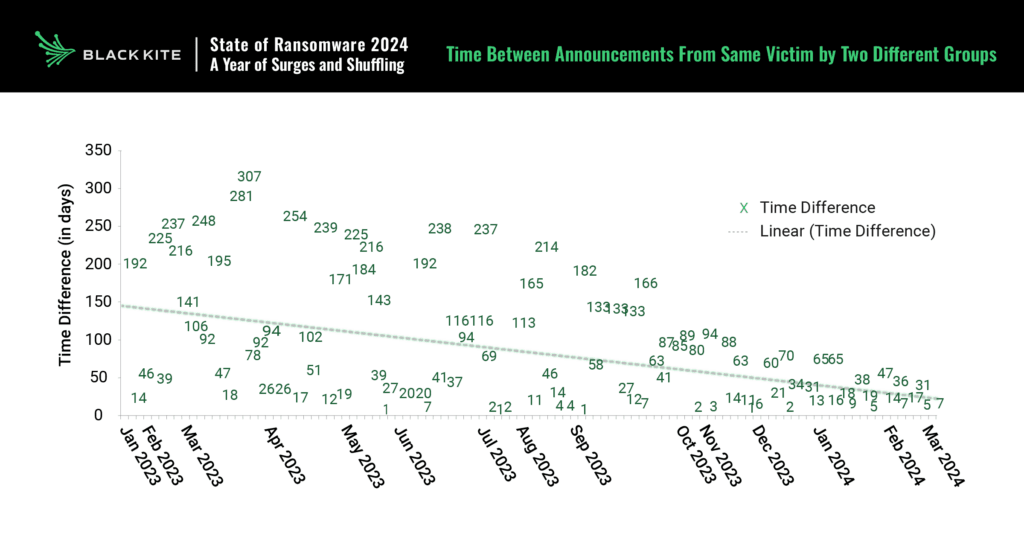
While attackers benefit from shared intelligence, organizations fail to collaborate on defense strategies, opening themselves — and their supply chains — to significant security risks. Going alone is a losing strategy.
This lack of coordination heightens exposures and the likelihood of successful attacks, as even the most robust cybersecurity defenses have their limits. After all, each company only has so many resources.
But there is a better way.
STRENGTHENING DEFENSES WITH COLLABORATIVE CYBER THREAT INTELLIGENCE
To paraphrase my industry colleague Richard Stiennon, Chief Research Analyst at IT-Harvest, who was featured in an episode of our Risk & Reels podcast, companies are currently defending themselves as best they can. Those that know how to strengthen their defenses are faring better, while the rest are engaged in a losing battle. It’s time for us to be proactive, reach out, and work together.
Consider the impact of just 10 companies pooling their resources and working together to combat cyber threats. This means companies can gain access to the kinds of best practices and tools that others are already using to successfully defend themselves against cyber attacks. Now imagine 100 or even 1,000 companies coming together to share tactics, best practices, and practical defense strategies.
While this may seem like an ambitious goal, intelligence-sharing entities like ISACs (Information Sharing and Analysis Centers) and the NSA Cybersecurity Collaboration Center
are already turning this vision into a reality — and proving the power of collective action.
A prime example is the Northeast Ohio CyberConsortium (NEOCC), established in 2018. This ISAC actively promotes collaborative cyber threat intelligence across the region through industry-led efforts and public-private partnerships. By fostering an environment of shared knowledge and practices, NEOCC members have built a culture of collaborative defense, achieving significant improvements in cybersecurity resilience and incident response.
IF COLLABORATION IS SO GREAT, WHY ISN’T IT HAPPENING?
There’s a strong case for collaboration, but to get there, there are a few issues with the current approach to vendor risk assessment and remediation to resolve first:
- Lack of clear ownership for risk assessment: When everyone thinks risk assessment is another team’s priority, nothing gets done. By making it clear who’s in charge, everyone knows which team is responsible for taking action.
- Identifying issues is time-consuming: Following a high-profile incident, companies often struggle to pinpoint issues and respond effectively across their entire third-party ecosystem. Without visibility into vendors’ platforms, organizations often resort to sending shotgun blast emails, which isn’t effective or scalable.
- Security is on the sidelines: Business goals and objectives often overshadow security requirements — until a breach occurs. Security is frequently sidelined compared to focusing on delivering products to market or meeting revenue targets, leaving critical risks unaddressed until it’s too late.
- Inadequate security-to-security communication: When security teams identify a vulnerability in a partner or vendor, they often face challenges in finding the right point of contact. Instead of directly interfacing with the vendor’s security team, they’re passed through account managers, customer success teams, and other intermediaries, resulting in a slow and inefficient game of telephone. Sometimes, the message never even reaches the security team, leading to no action being taken at all.
- Fear of reputational damage or repercussions: Many organizations hesitate to share information about vulnerabilities or security gaps due to concerns about how it may reflect on their capabilities. They may feel embarrassed, fear being perceived as less competent, or worry about potential consequences if the shared intelligence reveals a significant oversight or weakness. This apprehension often discourages open collaboration and creates an environment where security teams remain isolated instead of leveraging collective intelligence to address threats.
Overcoming these challenges and working toward collaborative cyber threat intelligence might seem like a pipe dream — but it’s certainly possible. After all, the cyber attackers have already worked out how it’s done.
STRATEGIES TO IMPROVE VENDOR COLLABORATION
Organizations can improve vendor collaboration and security across the entire supply chain by adopting real-time risk assessments, providing clear remediation guidance, and closing communication gaps. Here’s how:
1. Continuously monitor supply chain risk and security vulnerabilities
Risk assessment must evolve from being an infrequent periodic task to an ongoing process. Some companies only reassess their vendors every three years — and that’s nowhere near enough. Point-in-time evaluations serve a limited purpose but must be augmented with real-time data collection and continuous monitoring. This shift allows organizations to identify and mitigate risks before they become crises.
This responsibility also needs to extend across the entire supply chain. Rather than considering security as the responsibility of the individual CISO at each company, it’s essential to work together to create a collaborative bubble of security that encompasses the entire ecosystem.
2. Provide vendors with accurate and trustworthy data — and specific, actionable remediation steps
When a vulnerability is identified, most companies still rely on outdated methods like manual surveys to gather information from vendors. But without knowing which company uses which software, you might need to ask hundreds or thousands of questions to uncover potential issues.
A better approach is to leverage real-time data-sharing platforms that allow vendors to receive actionable remediation steps based on actual risk exposure. Legacy tools often lack the necessary granularity, but newer solutions can fill this gap.
For example, Black Kite’s FocusTags™ can be used to uncover issues, automatically flagging vendors when they’re exposed to a data breach or attack — sometimes before they even realize it. Black Kite Bridge™ then helps automate and streamline the process of getting the issue addressed and sharing any relevant information with identified vendors, enabling risk collaboration across the entire supply chain.
3. Close the security communication gap
Effective collaboration relies on a direct connection between security teams across organizations. Too often, multiple calls and emails between departments waste critical time when addressing issues. Establishing direct communication channels between security teams ensures that the right people, those closest to the problem, can respond immediately.
This approach also helps solve the issue of false positives. Sending vendors irrelevant risk information can lead to vendor fatigue, creating a “boy/girl who cried wolf” scenario and diluting their response to actual threats. Black Kite Bridge helps by filtering out unnecessary alerts, ensuring only affected vendors are contacted. Compliance scores, risk indicators, and FocusTags allow security teams to communicate precisely and efficiently, reducing delays in remediation.
By closing these communication gaps and providing actionable intelligence directly to those who need to know, Black Kite Bridge helps improve response rates — with early customers already seeing response rates as high as 90%.
COLLABORATION: THE KEY TO SUCCESSFUL CYBER DEFENSE
Looking towards a future filled with increasingly frequent and sophisticated cyber attacks might feel bleak. But there is a path forward — one that hinges on collaboration.
To win the cybersecurity war, organizations must move away from isolated defense efforts toward a unified approach that prioritizes collective intelligence and collaboration at all levels. This shift requires enhanced transparency, open communication, and shared accountability throughout the supply chain.
Achieving this collaboration necessitates the adoption of the right technologies and frameworks. Historically, many organizations have struggled to establish robust cybersecurity practices, often focusing on reactive measures rather than addressing foundational issues. This oversight has left them exposed to threats, frequently entangled in longstanding vulnerabilities that should have been resolved years ago.
Now, Black Kite has a solution designed to address those fundamental issues. Enabling real-time risk assessments, actionable remediation intelligence, and enhanced communication between vendors and security teams, Black Kite BridgeTM gives organizations the tools they need to collaborate and effectively respond to threats.
For a deeper dive into how you can transform your third-party risk response and build a more collaborative, efficient approach to remediation, check out our eBook, Chaos to Collaboration: Transforming Third-Party Risk Response for Zero-Day Events. This guide takes you through a before-and-after journey of improving vendor collaboration, streamlining outreach, and ensuring risks are remediated faster and more effectively.