Are Your Third Parties PCI-Compliant?
Published
Dec 28, 2021
Updated
Oct 31, 2025
Authors
Black Kite
Online shopping has quickly become one of the most popular online activities. While the pandemic sparked a significant uptick in global e-commerce activity, annual retail sales are expected to continue on a steady growth trajectory. The shift to e-commerce inherently poses its own set of cybersecurity risks–many of which pertain to investments retailers have made to satisfy demand, and the access those service providers have to consumer data.
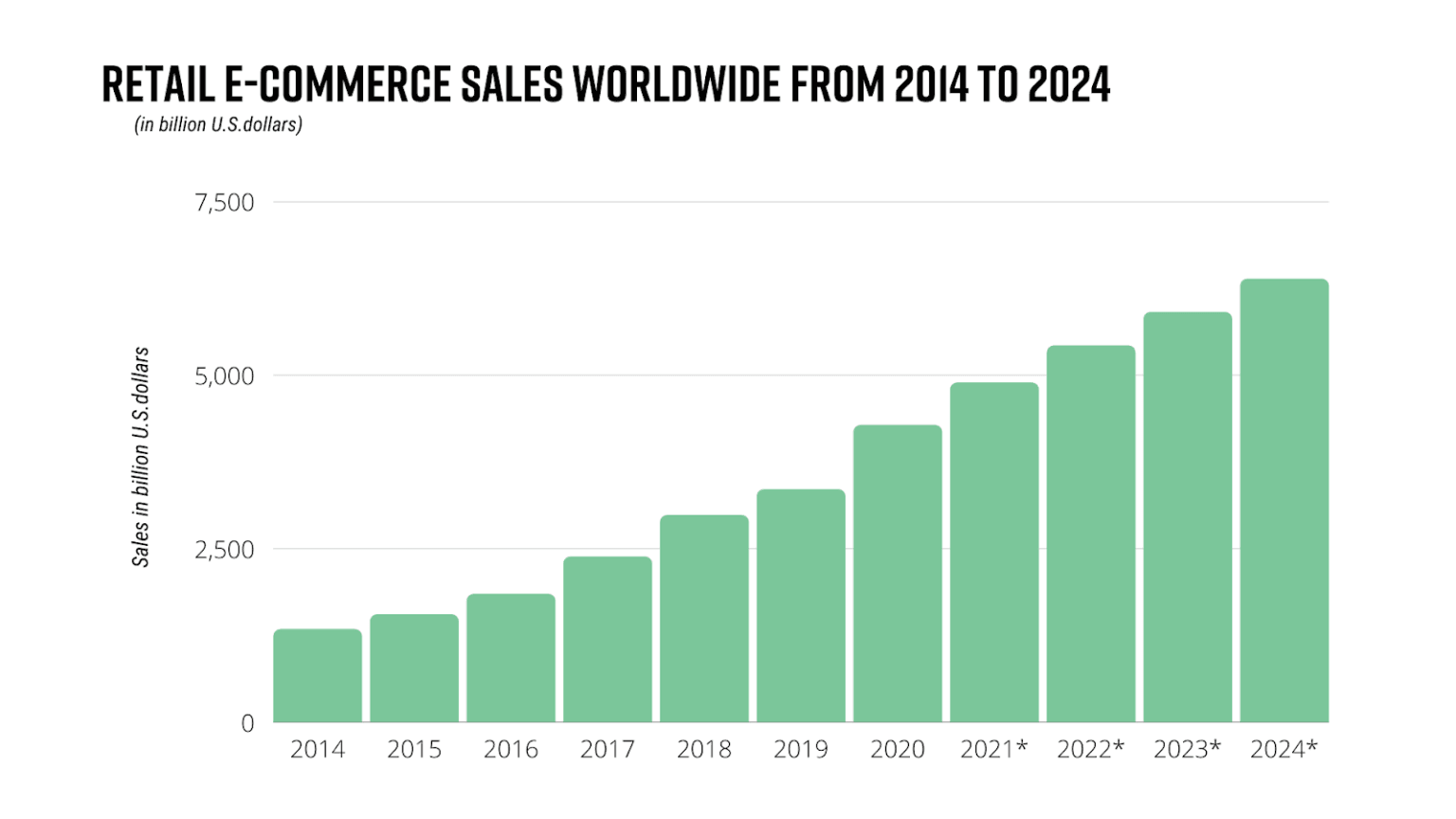
Source: Statista
A Guide to Your Third Parties and PCI-DSS Compliance
Cybercriminals are working smarter, not harder–and they know that they don’t need to attack retailers or financial institutions directly to gain access to customer and credit card data. Although all businesses that collect credit card data for online purchases must achieve compliance with PCI Data Security Standards (PCI-DSS)–not everyone with access to sensitive information falls under that umbrella.
First off, what is the PCI Data Security Standard (PCI-DSS)?
The PCI Data Security Standard (PCI-DSS) provides a mandatory and actionable 12-step framework to secure and refine payment card industry data security processes. Originally released in 2004 by American Express, Discover, MasterCard, JCB International and Visa, PCI-DSS has since established the PCI Security Standards Council (PCI SSC)—an international institution that sets the global standards for protecting cardholder data.
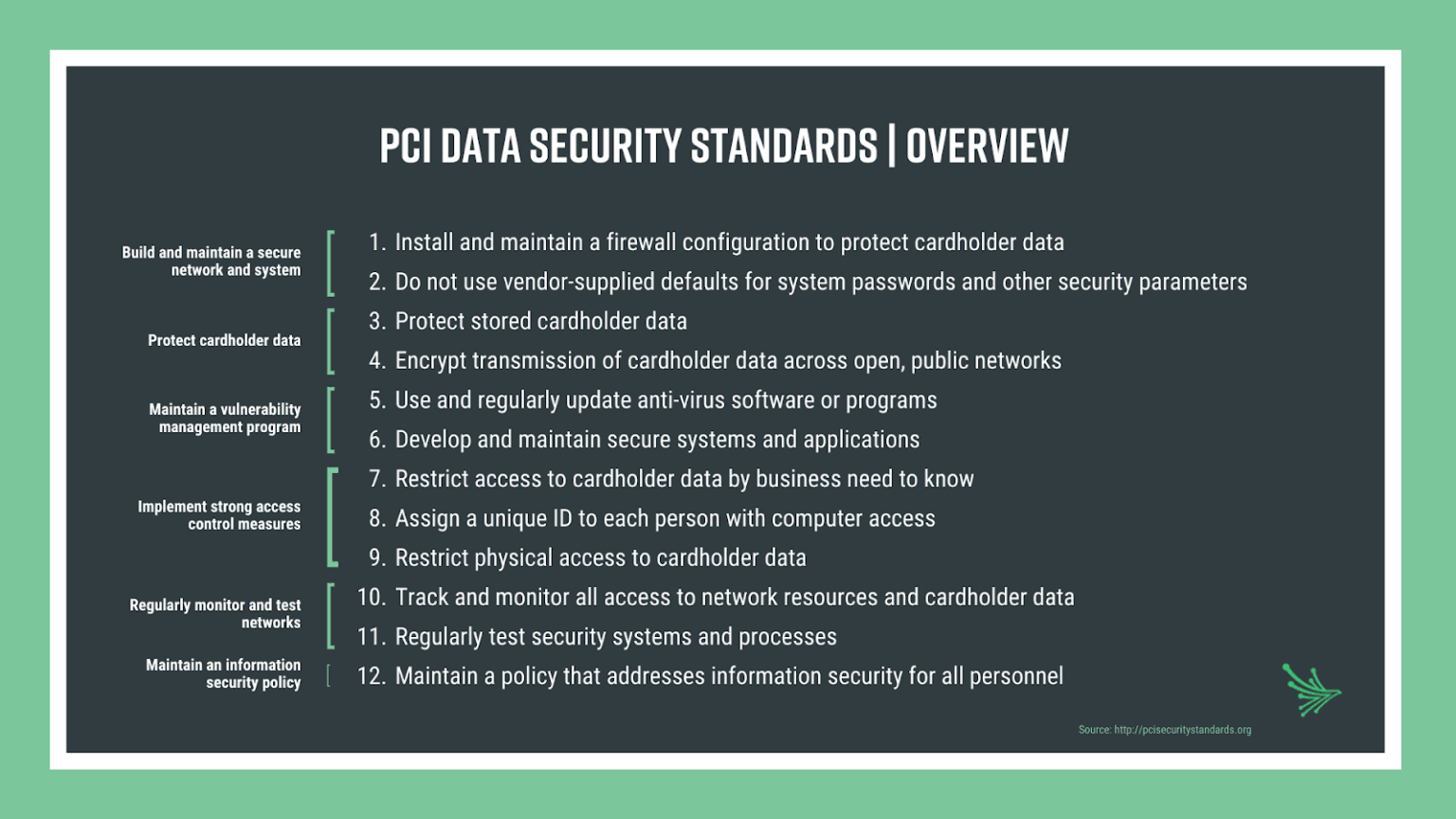
No company is a one-stop shop. Whether you outsource for web hosting applications, customer service solutions, or debt collection purposes–these third parties have a direct impact on cybersecurity and compliance because their employees or systems have access to your systems or your data and therefore consumer, or cardholder data at risk. As a result, PCI-DSS regulations extend beyond the merchant level, and all third-party service providers (TPSPs) that have access to cardholder data must maintain PCI-DSS compliance.
Which vendors should be PCI-compliant?
As your network of service providers grows, so does your risk exposure. Any breach on payment systems affects the entire payment ecosystem and consequences usually result in huge financial losses. Financial institutions that experience data breach lose both credibility and reliability.
Although PCI DSS recognizes that a service provider or a merchant may use a third-party to achieve its own business objectives, it does not relieve that entity of its responsibility to maintain PCI-DSS compliance. Ensuring your third parties are PCI-compliant is just as important as keeping up with internal standards because of the direct access many of your vendors, suppliers and partners have to cardholder data.
As a result, PCI-SCC developed a supplementary guide for third-party security assurance outlining guidelines for the following TPSPs:
- Organizations involved in storing, processing, and/ or transmission of cardholder data, which may include: Call center and customer service providers, e-commerce payment solutions, fraud verification, debt collectors credit reporting services, and more.
- Organizations involved in storing cardholder data, including: secure storage facilities, encryption providers, mobile-application third parties that provide software as a service.
- Resellers or integrators that are involved with installing, maintaining, monitoring or supporting systems.
- Organizations involved in the protection of the cardholder data environment (CDE), including infrastructure providers, managed firewall providers, secure data center hosts, and more.
- Organizations that may have incidental access to CHD or the CDE, such as IT delivery channels and services, web application providers, maintenance services, and more.
What specifications are there for third parties and PCI-compliance?
According to the PCI Security Standards Council, “a robust and properly implemented third-party assurance program assists an entity in ensuring that the data and systems it entrusts to TPSPs are maintained in a secure and compliant manner. Proper due diligence and risk analysis are critical components in the selection of any TPSP.”
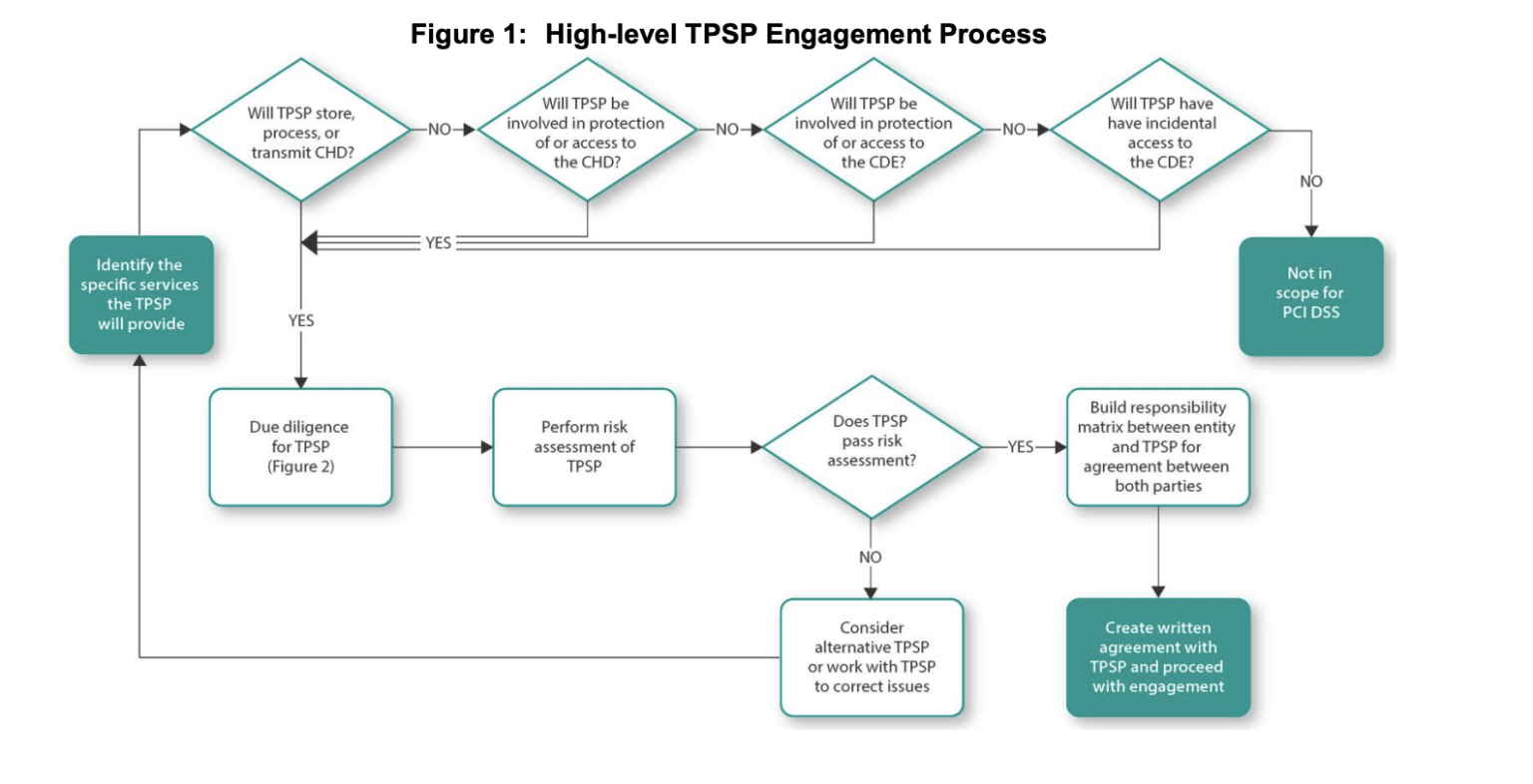
Source: PCI Security Standards Council; Third-Party Security Assurance and Shared Responsibilities Special Interest Groups
PCI Requirement 12.8 outlines policies for dealing with TPSPs, requiring organizations to develop and maintain a robust information security policy.
- PCI DSS 12.8.1: Maintain a running list and description of service providers.
The more information you collect while conducting a TPSP inventory, the easier it will be to maintain. Core elements to a thorough inventory include the TPSP name and primary points of contact, as well as the services it provides and secure data it has access to. - PCI DSS 12.8.2: Develop a written agreement that acknowledges the TPSP is responsible for the security of the shared data.
Communication is key to a successful vendor/ customer relationship, and establishing a clear contract that addresses the sensitivity of the data shared sets the foundation for working with any service provider. - PCI DSS 12.8.3: Ensure there is an established process for engaging TPSPs, including a proper due diligence plan.
Transparency is key when it comes to engaging vendors, suppliers and partners. Due diligence checks ensure that you’re correctly vetting organizations according to their security policies and incident response plans. - PCI DSS 12.8.4: Revisit PCI-compliance level a minimum of once per year.
This year has taught us how quickly things can change when it comes to cybersecurity, which is why PCI DSS requires at least one compliance status review each year.
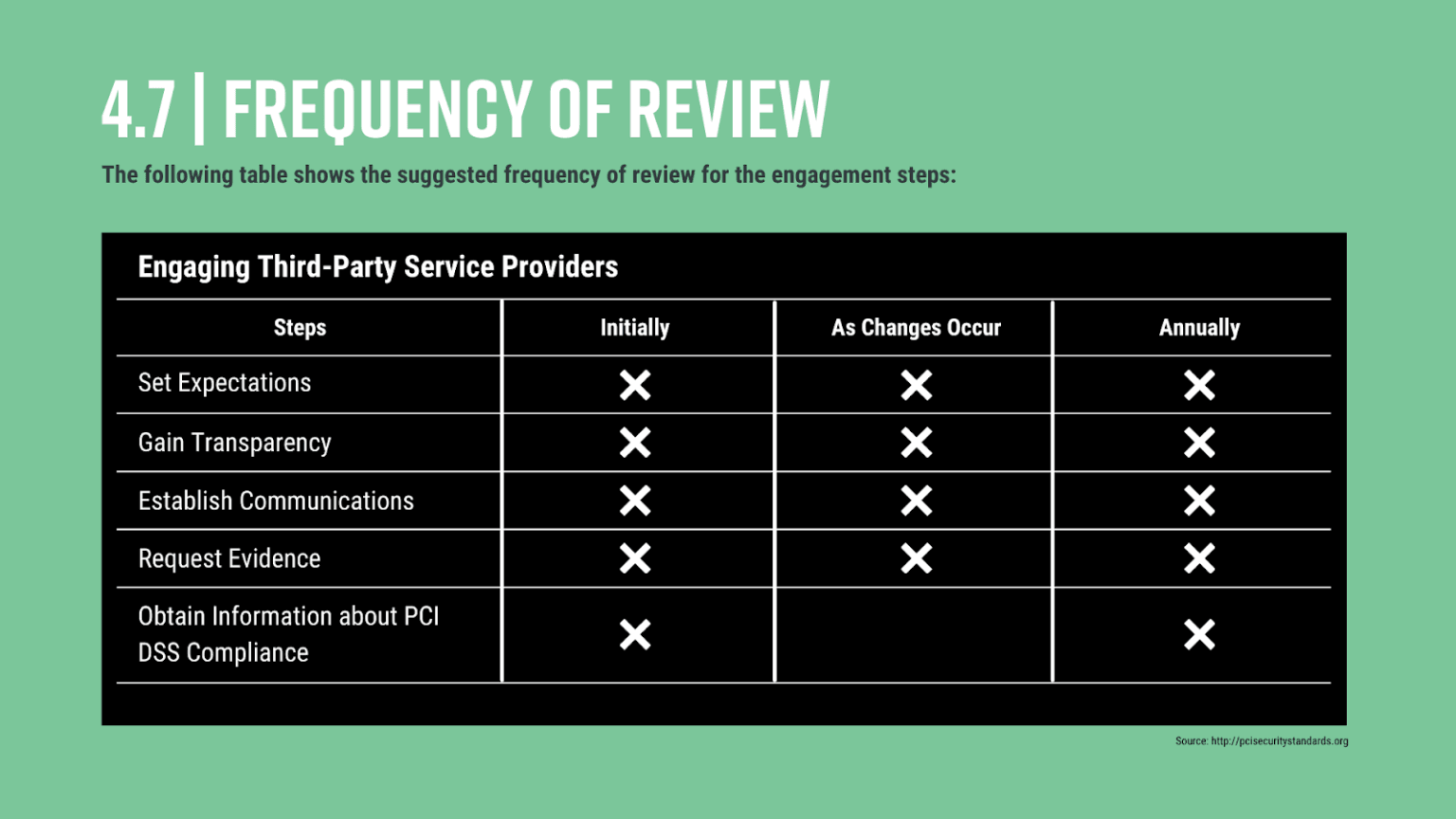
Source:PCI Security Standards Council; Third-Party Security Assurance and Shared Responsibilities Special Interest Groups
- PCI DSS 12.8.5: Maintain information about which PCI DSS requirements are owned by the entity, and which are managed by the service provider.
Ensure there are no gaps in compliance by clearly documenting which requirements each party is responsible for, as well as those that are shared. The council strongly urges companies to develop a responsibility matrix to ensure that all factors regarding technology and processes are properly addressed.
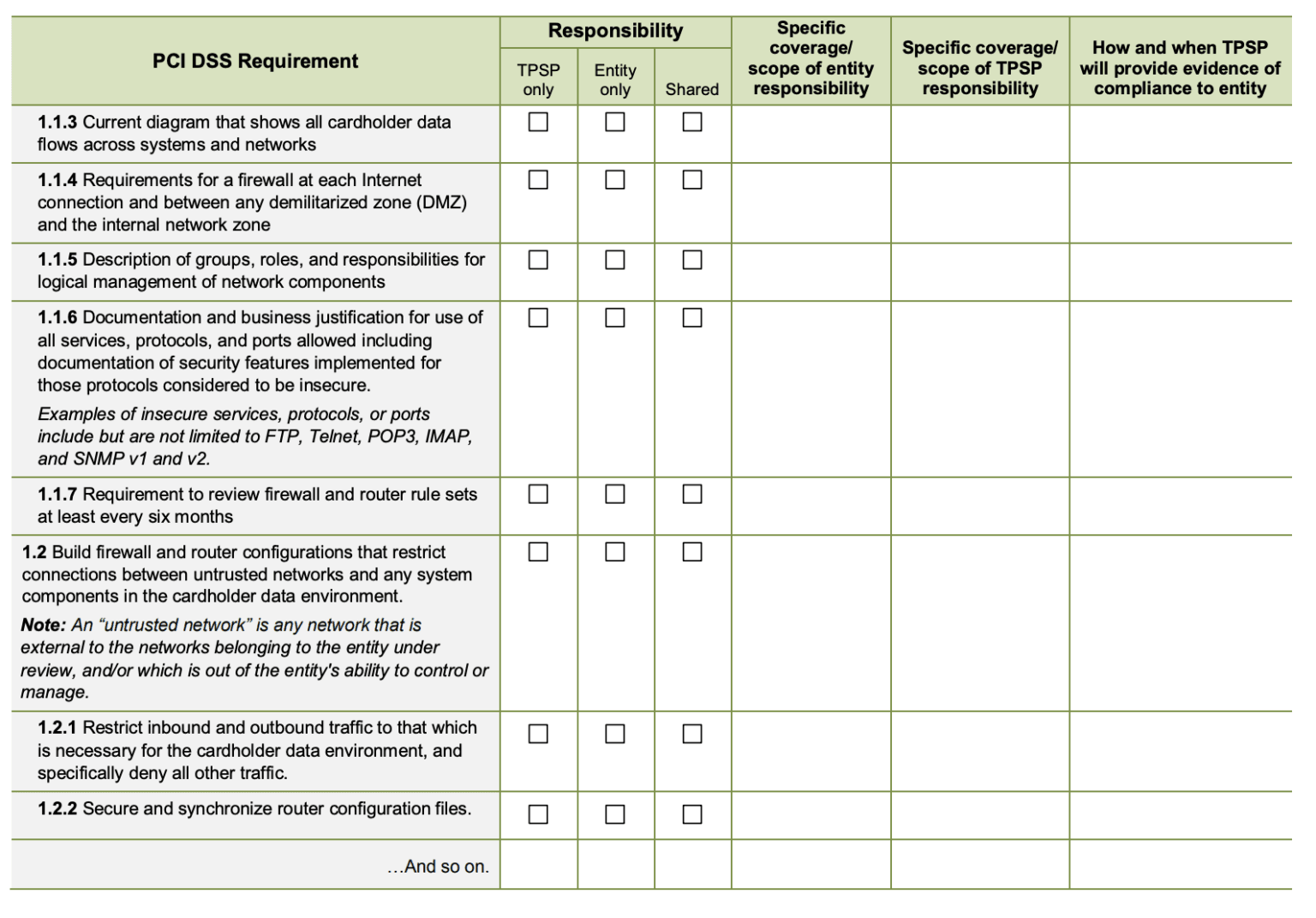
Source: PCI Security Standards Council; Third-Party Security Assurance and Shared Responsibilities Special Interest Groups
What should I know about PCI-DSS 4.0?
Slated to release early to mid 2022, PCI-DSS 4.0 will be the most significant revision since PCI DSS 3.0 was released in 2013, and will include major updates to respond to the world’s ongoing digital transformation and inherent exposure to cybersecurity risk. Although the full details of the PCI DSS Version 4.0 have yet to be announced, the customization it will offer merchants has gotten the most attention.
According to the PCI Council, “unlike compensating controls, customized validation will not require a business or technical justification for meeting the requirements using alternative methods, as the requirements will now be outcome-based.” This added rule will likely develop a more permanent solution for validating compliance with specialized security controls. However, it’s likely that this will only apply to those further along in the cybersecurity maturity process.
While details are still up in the air, one thing is for certain: this next version of PCI DSS won’t be the last. Shift the conversation from, “how do I achieve third-party PCI-compliance?” to “how can I mature my third-party risk management process across the board?”.
How can Black Kite help?
Of course, everyone starts somewhere. Black Kite’s automated compliance correlation has helped hundreds of organizations save time, money and resources by automatically measuring PCI compliance levels for any vendor within their cyber ecosystem. Request a demo today to see it in action.