An Attack on 3rd-Party Advertising Company Increased Cyber Risk of European E-Commerce Sites
Published
Jan 28, 2019
Updated
Jan 27, 2026
Authors
Black Kite
malicious code injected to a third-party Javascript of an advertising agency targets credit card information of online shoppers at European-based e-commerce sites. Many websites leverage Javascripts to track their visitors, collect analytics, etc. So, use of a Javascript library of an advertising agency is not uncommon. External Javascripts that run at your website pose hidden cyber risks that we usually overlook and this one is no exception.
Magecart attackers are behind the scene
Trend Micro researchers reported[1] a recent attack on a Javascript managed by Adverline, a French advertising company, with additional help from RiskIQ researcher Yonathan Klijnsma[2]. This “software supply-chain attack” (which is a part of a long-run cyber attack series known as Magecart campaign) affects some European e-commerce sites that partner with Adverline. Trend Micro stated that “Adverline has handled the incident and has immediately carried out the necessary remediation operations”.
The malicious code injected to the Javascript is a credit card skimming code (as in previous Magecart attacks), a trick which targets credit card information of users usually at checkout page.
Cyber attacks through 3rd-party Javascript
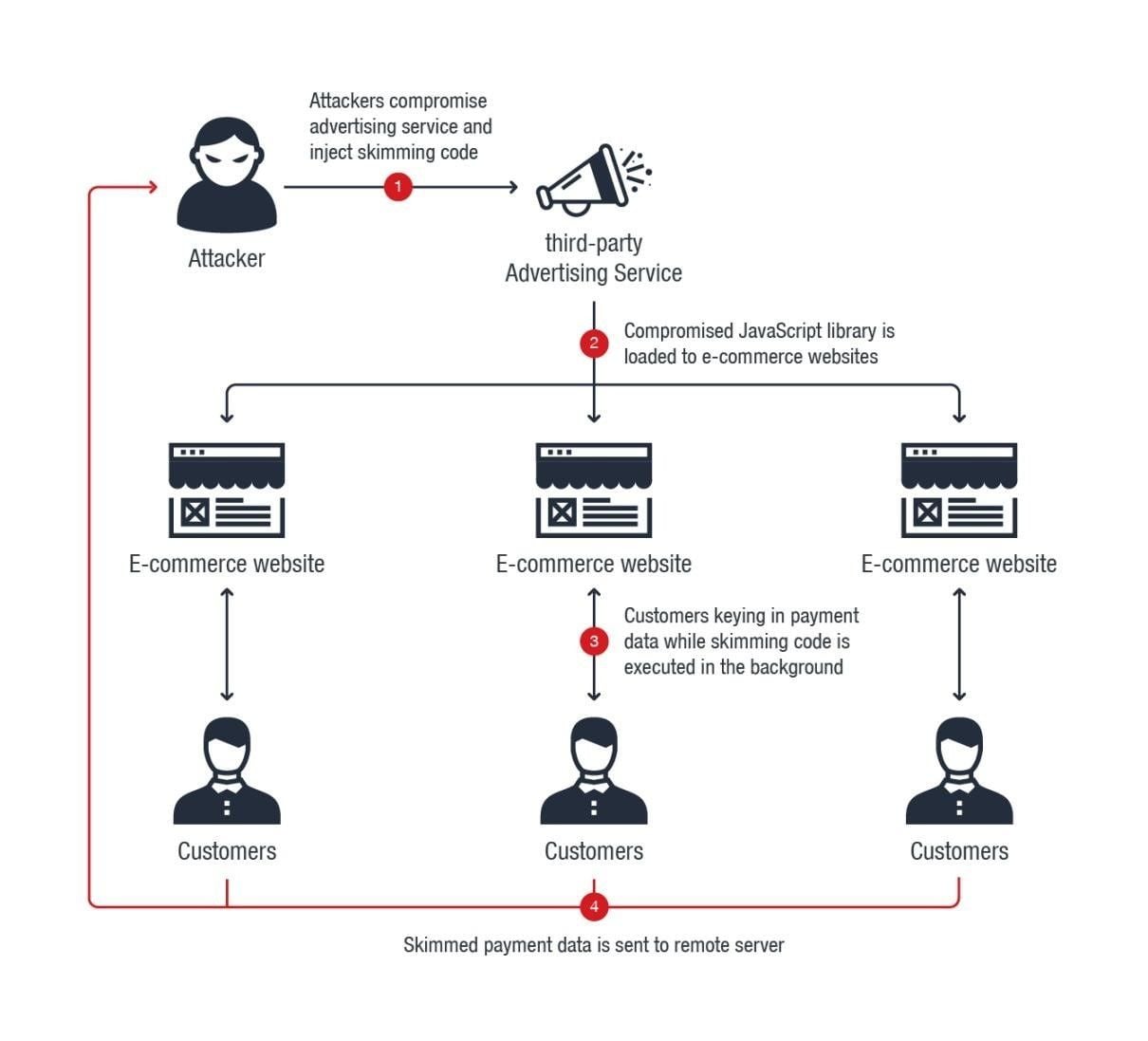
Image: TrendMicro
This is not the first time we have witnessed use of third-party Javascripts to execute a cyber attack on major companies. Here are some incidents from 2018
- 40,000 UK citizens’ credit card information were exposed at TicketMaster incident caused by a Javascript managed by a third-party company called Inbenta,
- 380,000 airline passengers’ payment and credit card information were breached in a similar fashion at British Airways incident,
- A cryptocurrency exchange called gate.io suffered Bitcoin theft because of an external Javascript managed by StatCounter.
While 3rd-party cyber attacks are on the rise, use of third-party Javascripts seems to be one of the top methods to do it by the hackers.
How to detect cyber risk of 3rd-party Javascripts
Detection of malicious JavaScripts is part of CDN (content delivery network) security. A content delivery network (CDN) is a large distributed system of servers deployed in multiple data centers across the Internet. Companies use CDNs for online libraries like JQuery. Detecting malicious code in JavaScripts is possible in your own systems with certain vulnerability scan tools on-premise. However, detecting a CDN vulnerability at a third-party supplier’s system might be beyond the reach.
Fortunately, a company can take advantage of 3rd-party cyber risk monitoring tools such as Black Kite Cyber Risk Scorecards to detect such hidden risks. Black Kite Cyber Risk Scorecards analyze the CDN content to detect possible vulnerabilities that can be exploited for a data breach. Any third-party company added to the main company’s ecosystem is checked for such vulnerabilities in CDN security. It is worth noting that Black Kite is currently the only company that checks CDN security among security-rating service providers.
To learn more about your cyber risk on many categories including CDN security, request a demo to receive a free cyber risk scorecard.