Are your assets at risk of being victimized or weaponized in a Memcached DDoS attack?
Written by: Black Kite
Two record-breaking DDoS attacks, which used misconfigured Memcached servers for amplification/reflection, created 1.35 Tbps and 1.7 Tbps bogus traffic towards GitHub and an unnamed US-based company, respectively. Even though amplification/reflection DDoS attacks are not new to the cyber security world, the amount of traffic created is terrifyingly huge thanks to misconfigured Memcached servers’ amplification by a factor of 51,200.

A recent news report shows that the situation is getting worse. Now, even script kiddies, the lowest circle of hacker community, can launch massive DDoS attacks with two Memcached-oriented proof-of-concept (PoC) exploit code released online. One of the code is written in C and the other one in Python. The former lists nearly 17,000 potential vulnerable Memcached servers in its description leaving them exposed on the internet. The latter takes advantage of Shodan search engine API to get a fresh list of such servers.
The Hacker News, “Memcached DDoS Exploit Code and List of 17,000 Vulnerable Servers Released,” Mar 2018, accessible at https://thehackernews.com/2018/03/memcached-ddos-exploit-code.html

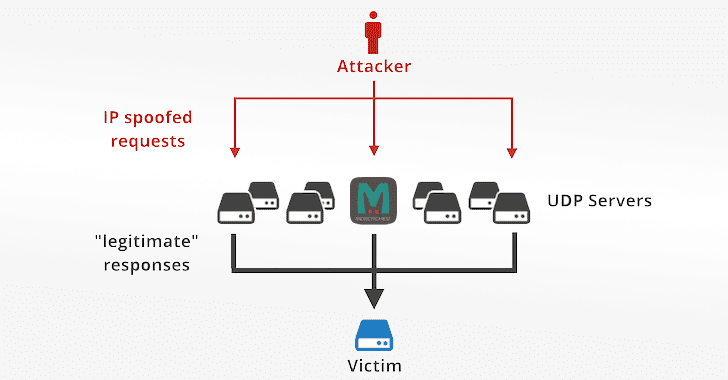
Memcached DDoS Attack, How it works?
Memcached is a widely-used open-source distributed caching system. The system works with a large number of open connections and runs over TCP or UDP port 11211. In order to increase performance and scale web applications, the Memcached amplification is used by many well-known websites (Twitter, GitHub, Reddit, etc.).
As in any other amplification DDoS attacks, hackers, by using spoofed IP addresses of victims, send a tiny request with UDP. The response is much larger than the request (e.g., records seen by Cloudfare showed that a 15-byte request may trigger a 750kB response), but this amplified response is sent to victim’s website and crates an unexpected bogus traffic.

What can happen?
The enormous traffic created by abused Memcached servers is much more than a website can handle, so services delivered by the website will be unavailable for minutes or even hours depending on the scale and consistency of the attack.
The denial of service can harm a company in many ways. For instance, for a flight company, the tickets sale cannot be done and it may lead customers to buy tickets from an adversary. If you think the number of tickets sold in a minute, the amount of financial loss may be vital. Other losses, which cannot be measured in monetary values such as reputation loss, are bonus.
How would you know that you are at risk?
A periodical cyber risk assessment may help to know. However, the risk assessment service that you use should look at right places to say whether you are at risk or not.
A firm’s resiliency against DDoS attacks is very important and, if it is not good enough, the appropriate countermeasures should be taken. Black Kite Risk Scorecard© measures DDoS resiliency (among several other factors) and gives a letter grade so that the firm’s executives (CEO, CISO) can understand easily its preparedness against DDoS attacks. Our research shows that a firm that has D or F score for DDoS resiliency is more likely to face a massive DDoS attack like Memcached-based attacks than a firm with A or B score. Black Kite Risk Scorecard© non-intrusive proprietary methods gather information from well-known databases like Censys, Shodan, etc. and analyses them to calculate how prepared your firm against DDoS attacks. Th detailed recommendations can help SOC teams to increase DDoS resiliency.
You may not be a direct victim of a DDoS attack but your assets may be weaponized by hackers to attack others. If you are unaware of such misconfiguration of your servers, you may be unwillingly helping bad people to do bad stuff. However, Black Kite Risk Scorecard© monitors information about your assets shared in deep web and sees what hackers see about your company. If any asset of your company is shared in a list of misconfigured servers to be used in such massive DDoS attacks, Black Kite Risk Scorecard© service alerts you about it. As mentioned above, this kind of lists are already released online and it can be found only if you know where to look. Black Kite Risk Scorecard’s “Hactivist Shares” and “Disclosed Information” module can hint you about such shares by analyzing your digital footprint on the internet.

The common phrase “It’s better to be late than to be sorry” does not apply to cyber world. Be aware of your cyber risk before it is too late. Take action now and see your risk score here.
The common phrase “It’s better to be late than to be sorry” does not apply to cyber world. Be aware of your cyber risk before it is too late. Take action now and see your risk score here.