Focus Friday: TPRM Actions For MadeYouReset, Ivanti Connect Secure, PostgreSQL & Plesk Obsidian
Written by: Ferdi Gül
This week’s Focus Friday zeroes in on four issues that can disrupt vendors at the edge and in the core: the MadeYouReset HTTP/2 DoS technique (our lead item), denial-of-service flaws in Ivanti Connect Secure and related gateways, PostgreSQL updates addressing info disclosure and dump/restore-chain risks, and a critical authentication bypass in Plesk Obsidian. We frame each through a Third-Party Risk Management lens—what the weaknesses mean for vendor-hosted portals, APIs, databases, and control panels; the exact questions to ask; and the concrete remediation steps to expect. If you manage a large vendor portfolio, the goal is simple: cut through noise, focus on the suppliers that can actually affect your business, and move them to resolution faster.

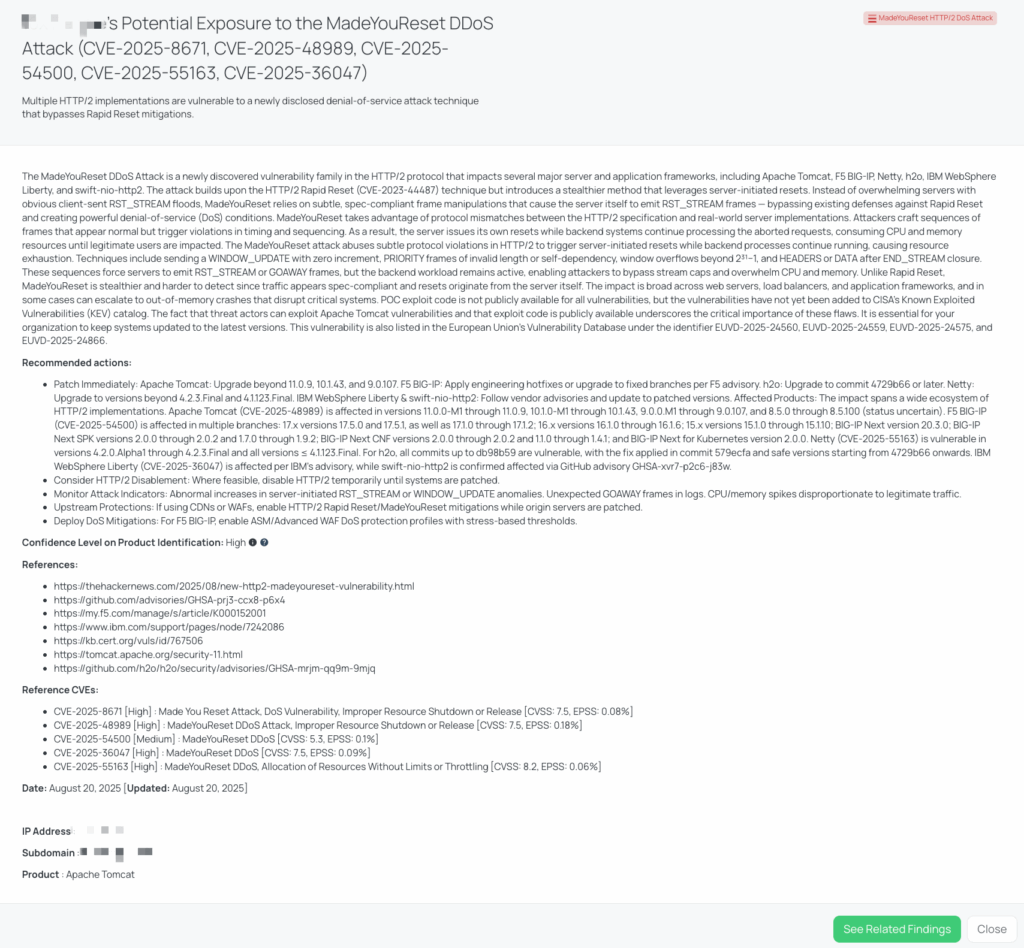
HTTP/2 “MadeYouReset” DoS Attack
What is the MadeYouReset HTTP/2 DoS?

MadeYouReset is a family of HTTP/2 implementation bugs that lets an attacker use ordinary-looking frame sequencesto make the server send RST_STREAM/GOAWAY—while the backend keeps working on those requests. The result is quiet but severe CPU/memory pressure that slips past many Rapid Reset defenses.
Typical trigger patterns include:
- WINDOW_UPDATE anomalies (zero increment, or window growth past 2³¹−1)
- malformed/self-dependent PRIORITY frames
- sending HEADERS/DATA on a half-closed stream
Timeline & status. Public disclosure landed in mid-August 2025. These CVEs aren’t listed in CISA KEV. Proof-of-concepts exist for some products (e.g., Tomcat).
Vulnerabilities, severity, CVSS & EPSS (EPSS per tag):
- CVE-2025-8671 (Generic HTTP/2) — DoS; High; CVSS 7.5; EPSS 0.08%
- CVE-2025-48989 (Apache Tomcat) — DoS; High; CVSS 7.5; EPSS 0.18%
- Affected: 11.0.0-M1–11.0.9, 10.1.0-M1–10.1.43, 9.0.0.M1–9.0.107 (8.5.x unknown)
- Fixed: 11.0.10 / 10.1.44 / 9.0.108
- CVE-2025-54500 (F5 BIG-IP / BIG-IP Next) — DoS; Medium; CVSS 5.3; EPSS 0.10%
- Affected trains include 17.5.0–17.5.1, 17.1.0–17.1.2, 16.1.0–16.1.6, 15.1.0–15.1.10, BIG-IP Next ≤20.3.0, Next SPK 2.0.0–2.0.2, Next CNF 2.0.0–2.0.2, Next for Kubernetes 2.0.0
- 17.2.x called out as not affected; 14.x and earlier are EoTS and not evaluated
- CVE-2025-55163 (Netty) — DoS; High; CVSS 8.2; EPSS 0.06%
- Affected: 4.2.0.Alpha1–4.2.3.Final and ≤4.1.123.Final
- Fixed: 4.2.4.Final / 4.1.124.Final
- CVE-2025-36047 (IBM WebSphere Liberty) — DoS; High; CVSS 7.5; EPSS 0.09%
- Impact requires HTTP/2 enabled with servlet features
- Fixed in 25.0.0.9 (or APAR PH66953)
- h2o (GHSA-mrjm-qq9m-9mjq) — Vulnerable up to commit db98b59; fix introduced in 579ecfa; upgrade to 4729b66+
Where exposure really comes from (critical deployment nuance).
Seeing h2 in response headers only proves that one session used HTTP/2. The same host may serve other clients over HTTP/1.1. Exposure follows where HTTP/2 is actually terminated on the path:
- If an edge device (e.g., F5 BIG-IP) terminates HTTP/2 and proxies HTTP/1.1 to the origin, the reachable risk is the edge’s HTTP/2 stack; a Tomcat HTTP/2 bug may not be externally reachable on that route.
- If the origin (e.g., Tomcat, h2o, WebSphere Liberty, Netty) terminates HTTP/2, then its CVE is directly exposed.
Bottom line: don’t just ask which products exist—ask where HTTP/2 is negotiated and terminated.
Optional note for teams using Rust h2: versions <0.4.11 were noted as susceptible by some providers. Update the crate where applicable.
Why should TPRM professionals care?
This lives at the public protocol edge—web portals, APIs, mobile backends, partner callbacks, and control planes. One mis-placed HTTP/2 termination point or an unpatched load balancer/app server can stall logins, payments, ticketing, webhooks, or SSO. Because some stacks terminate h2 at the edge and speak HTTP/1.1 upstream, you need clarity on the exact negotiation points per vendor—not just a product inventory.
What questions should TPRM professionals ask vendors?
- Have you upgraded Apache Tomcat to versions beyond 11.0.9, 10.1.43, and 9.0.107, F5 BIG-IP to fixed branches as per F5 advisory, h2o to commit 4729b66 or later, Netty to versions beyond 4.2.3.Final and 4.1.123.Final, and IBM WebSphere Liberty & swift-nio-http2 to patched versions as per vendor advisories to mitigate the risk of the MadeYouReset DDoS Attack (CVE-2025-8671, CVE-2025-48989, CVE-2025-54500, CVE-2025-55163, CVE-2025-36047)?
- Have you implemented monitoring for abnormal increases in server-initiated RST_STREAM or WINDOW_UPDATE anomalies, unexpected GOAWAY frames in logs, and CPU/memory spikes disproportionate to legitimate traffic, which are indicators of the MadeYouReset DDoS Attack?
- Have you enabled HTTP/2 Rapid Reset/MadeYouReset mitigations in your CDNs or WAFs while your origin servers are being patched to protect against the MadeYouReset DDoS Attack?
- Have you deployed DoS protection profiles with stress-based thresholds on F5 BIG-IP to mitigate the risk of the MadeYouReset DDoS Attack (CVE-2025-54500)?
Remediation recommendations for vendors subject to this risk
- Patch/upgrade now: Tomcat 11.0.10 / 10.1.44 / 9.0.108; Liberty 25.0.0.9 (or PH66953); Netty 4.2.4.Final / 4.1.124.Final; h2o ≥4729b66; F5 BIG-IP/Next per vendor guidance.
- Temporarily disable HTTP/2 on vulnerable hops until fixes are verified; document ALPN/protocol maps to avoid surprises.
- Edge protections: on F5, enable ASM/Advanced WAF DoS profiles with stress-based thresholds; turn on HTTP/2 DoS controls in your CDN/WAF.
- Detect abuse quickly: alert on unusual server-side resets and protocol errors; correlate CPU/memory with traffic to catch low-and-slow patterns.
- Topology hygiene: ensure only the intended hop terminates HTTP/2; avoid accidental dual termination that broadens exposure.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite published the MadeYouReset HTTP/2 DoS FocusTag on August 20, 2025 (expires November 30, 2025). Use it to immediately narrow your portfolio to vendors whose exposed assets negotiate HTTP/2 on vulnerable stacks(F5 at the edge; Tomcat/Liberty/h2o/Netty at the origin). The tag includes asset evidence—specific IPs and subdomains—so your outreach is targeted and backed by data.
Operationally: filter by the tag, export the affected vendors, attach the questions above, and track remediation status. If coverage changes (new advisories or products), the tag’s Last Updated stamp will reflect it and your saved views inherit the update.
CVE-2025-5456 & CVE-2025-5462 — Ivanti Connect Secure / Policy Secure / ZTA / Neurons DoS
What are the Ivanti Connect Secure DoS vulnerabilities?
Two remote, unauthenticated denial-of-service issues affect multiple Ivanti access-gateway products. CVE-2025-5456 is an out-of-bounds read; CVE-2025-5462 is a heap-based buffer overflow. Both are rated High with CVSS 7.5. Use the FocusTag EPSS values when prioritizing: 0.24% for CVE-2025-5456 and 0.22% for CVE-2025-5462.
They were disclosed in mid-August 2025. At tag time, there was no public evidence of exploitation, no CISA KEV entry, and no CISA advisory specific to these CVEs.
Affected / fixed versions
- Ivanti Connect Secure (ICS): affected up to 22.7R2.7; fixed in 22.7R2.8 and 22.8R2.
- Ivanti Policy Secure (IPS): affected up to 22.7R1.4; fixed in 22.7R1.5.
- Ivanti ZTA Gateway: 22.8R2.2 affected; fixed in 22.8R2.3-723.
- Ivanti Neurons for Secure Access: affected up to 22.8R1.3; cloud environments patched Aug 2, 2025 (no customer action required there).
From a technical angle, an unauthenticated attacker can send specially crafted packets that trigger either an over-read or a heap overwrite, causing process crashes and service interruption on exposed gateways.
Why should TPRM professionals care?
These systems sit at the perimeter and control remote access for employees, contractors, and partners. A DoS against ICS/IPS/ZTA/Neurons can disrupt VPN/ZTNA sessions, block SSO and device compliance checks, and stall third-party workflows (ticketing, file transfer, admin portals). Even without data exposure, availability loss can cause SLA hits, operational delays, and incident overhead for you and your vendors.
What questions should TPRM professionals ask vendors?
- Have you updated all instances of Ivanti Connect Secure to version 22.7R2.8 or 22.8R2, Ivanti Policy Secure to version 22.7R1.5, Ivanti ZTA Gateways to version 22.8R2.3-723, and Ivanti Neurons for Secure Access to the latest version to mitigate the risk of CVE-2025-5456 and CVE-2025-5462?
- Can you confirm that you have run Ivanti’s external Integrity Checker Tool (ICT) after applying the updates to detect any signs of compromise that may have occurred before patching?
- Have you ensured that your organization is not using any of the Pulse Connect Secure 9.x versions, as they have reached End of Support and no longer receive security fixes, and migrated to Ivanti Connect Secure as recommended?
- Can you confirm that you have followed Ivanti’s recommended Security Configuration Best Practices to further reduce the risk to your environment, specifically in relation to the buffer over-read and heap-based buffer overflow vulnerabilities identified in CVE-2025-5456 and CVE-2025-5462?
Remediation recommendations for vendors subject to this risk
- Upgrade immediately to the fixed versions listed above (or confirm cloud remediation for Neurons).
- Run ICT post-update to check for pre-patch tampering; apply Ivanti’s security hardening guidance.
- Operational safeguards while rolling out: enforce rate-limits/connection caps, restrict management access to trusted sources, and ensure logs are retained for triage.
- Validate with synthetic probes (login/API checks) from multiple regions and document the version inventory for each exposed gateway.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite published the Ivanti Connect Secure – Aug2025 FocusTag on Aug 18, 2025 (confidence Very High, expires Nov 30, 2025). Use it to instantly filter your portfolio to vendors exposing ICS/IPS/ZTA/Neurons. The tag includes asset evidence (IPs and subdomains) tied to these gateways, enabling targeted outreach with the questions above and measurable tracking of patch adoption.
CVE-2025-8713/8714/8715 — PostgreSQL
What are the new PostgreSQL vulnerabilities?
Three issues affect supported PostgreSQL lines prior to 17.6 / 16.10 / 15.14 / 14.19 / 13.22.
- CVE-2025-8713 (Low, CVSS 3.1, EPSS 0.04%): statistics leakage lets a low-privileged user read sampled data (e.g., histograms/MCVs) otherwise restricted by ACLs or row-level security.
- CVE-2025-8714 (High, CVSS 8.8, EPSS 0.06%): a malicious superuser on the origin server can inject content into a pg_dump so that, on restore, arbitrary code runs as the client OS account; pg_dumpall is also impacted (plain-format restore via psql).
- CVE-2025-8715 (High, CVSS 8.8, EPSS 0.05%): newline-in-name injection in pg_dump enables restore-time code execution and, in some paths, SQL injection on the target; affects pg_dump / pg_dumpall / pg_restore / pg_upgrade (not present on versions older than 11.20).
These fixes shipped in the August 14, 2025 cumulative update. No public exploitation has been reported, and these CVEs were not in CISA KEV at the time of publication.
Why should TPRM professionals care?
PostgreSQL underpins customer-facing apps, analytics pipelines, and vendor platforms.
- The stats leak can expose patterns about restricted datasets (e.g., distribution of sensitive columns) that inform targeting or inference.
- The dump/restore chain is widely used for migrations and DR. The two pg_dump issues turn a routine restore into a client-side RCE risk and, in some cases, SQL injection on the restore target. If a third party maintains your data or ships dumps to you, the blast radius includes your environment during restore operations.
What questions should TPRM professionals ask vendors?
- Have you updated all instances of PostgreSQL to versions 17.6, 16.10, 15.14, 14.19, or 13.22 to mitigate the risk of CVE-2025-8713, CVE-2025-8714, and CVE-2025-8715?
- Can you confirm if you have implemented measures to prevent a user with low privileges from crafting a \”leaky operator\” to bypass access controls (ACLs) and row security policies, as described in CVE-2025-8713?
- Have you taken steps to prevent a malicious superuser on the origin PostgreSQL server from injecting arbitrary code into a database dump created by pg_dump, as described in CVE-2025-8714?
- Can you confirm if you have implemented measures to neutralize newlines in pg_dump to prevent a user on the origin server from injecting arbitrary psql meta-commands, as described in CVE-2025-8715?
Remediation Recommendations for Vendors subject to this risk
- Upgrade immediately to 17.6 / 16.10 / 15.14 / 14.19 / 13.22 (minor update; stop the service and replace binaries per standard procedure).
- Lock down dump/restore flows:
- Generate dumps only from trusted superusers; prefer custom/tar formats and restore via pg_restore where possible.
- Perform restores on isolated build/transfer hosts with least-privilege OS accounts; block interactive \!-style meta-commands in automation.
- Reindex BRIN (if applicable): After updating, REINDEX any BRIN indexes using numeric_minmax_multi_opsto resolve non-security bloat/inefficiency that can affect SLAs.
- Plan for lifecycle: Start migration planning if you still run PostgreSQL 13, which reaches EOL on November 13, 2025.
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite published “PostgreSQL – Aug2025” on August 18, 2025. Use the tag to filter vendors that expose PostgreSQL services or declare PostgreSQL usage in their tech stacks. The tag includes asset evidence (IPs/subdomains) where applicable and maps vendors to affected versions, enabling targeted outreach with the questions above and tracking of patch adoption over time.
CVE-2025-54336 — Plesk Obsidian
Plesk Obsidian is a widely used hosting control panel that centralizes management of websites, databases, email, DNS, SSL/TLS, and server services—often in multi-tenant environments run by hosting providers and MSPs.
What is the Plesk Obsidian authentication bypass?
This CVE is a critical authentication bypass caused by an incorrect (loose) comparison in the admin password check. If an administrator’s password matches certain patterns (for example strings beginning with 0e followed by digits), the comparison may accept arbitrary input as equivalent, allowing an unauthenticated login as admin and full server control. The issue is Critical (CVSS 9.8) with EPSS 0.04%, disclosed mid–late August 2025. At publication time there was no confirmed exploitation in the wild, the CVE was not in CISA KEV, and there was no CISA advisory specific to it. Affected versions are Plesk Obsidian before 18.0.71 Update 2 and 18.0.70 Update 4; the fix is available in 18.0.71 Update 2 and 18.0.70 Update 4.
Why should TPRM professionals care?
A single compromised Plesk panel can mean complete takeover of hosted assets across many customers: website defacement, database dumps or tampering, webshell deployment, outbound email abuse, DNS changes, and credential theft from configuration files and backups. Because Plesk often sits at the center of multi-tenant operations, one breach can cascade into dozens or hundreds of downstream properties. Even if the specific password pattern seems rare, panel compromise carries material third-party risk: fraud through legitimate-looking domains, data exfiltration from shared databases, and disruption of business-critical web services.
What questions should TPRM professionals ask vendors?
- Have you updated all instances of Plesk Obsidian to versions 18.0.71 Update 2 or 18.0.70 Update 4 to mitigate the risk of CVE-2025-54336?
- Can you confirm if you have implemented the recommended actions to secure your server, such as monitoring for signs of unauthorized access, unusual activity, or file modifications, especially in the context of the Incorrect Comparison Vulnerability and Authentication Bypass methods?
- Have you changed the admin password to a more secure format that does not start with “0e” followed by digits, as an immediate mitigation measure against the exploitation of this vulnerability?
- Can you provide details on how you are monitoring for potential brute-force attacks, specifically in relation to the _isAdminPasswordValid function in admin/plib/LoginManager.php, which is known to be vulnerable to such attacks due to the loose comparison operator used in password validation?
Remediation Recommendations for vendors subject to this risk
- Patch immediately to 18.0.71 Update 2 or 18.0.70 Update 4 across all instances.
- Eliminate risky passwords: Rotate the admin password and enforce policies that reject patterns like ^0e[0-9]+$, require high-entropy secrets, and prohibit dictionary variants.
- Harden access: Enforce MFA for all admins; restrict panel access to trusted IPs/VPN; rotate and scope API tokens; remove or update unneeded extensions.
- Post-patch assurance: Review panel and system logs, scan webroots for webshells/backdoors, verify scheduled tasks, rotate database credentials and any secrets exposed to the panel, and confirm mail/DNS settings haven’t been altered.
- Ongoing operations: Add the panel to continuous patching processes, enable file-integrity monitoring, and alert on high-risk actions (new admin, configuration changes, extension installs).
How TPRM professionals can leverage Black Kite for this vulnerability
Black Kite’s Plesk Obsidian Focus Tag (published August 20, 2025, expiration November 30, 2025; confidence Very High) narrows your portfolio to vendors exposing Plesk panels tied to this CVE. The tag provides asset evidence (IPs and subdomains) so you can contact the right teams with proof, use the targeted question set above, and track remediation over time.
Elevate Your TPRM Program with Black Kite FocusTags™
Black Kite’s FocusTags™ turn breaking technical findings into practical supplier actions—especially useful for issues like MadeYouReset at the protocol edge, Ivanti gateway DoS, PostgreSQL dump/restore exposures, and Plesk panel takeovers.
- Immediate vendor pinpointing: Instantly isolate which suppliers expose relevant technologies and versions—plus the specific IPs and subdomains we observed—so outreach lands on the right team the first time.
- Risk-based sequencing: Prioritize by business criticality and technical severity (e.g., HTTP/2 termination points for MadeYouReset; internet-facing VPN/ZTNA nodes for Ivanti; production DB clusters for PostgreSQL; multi-tenant admin panels for Plesk).
- Ready-to-send question sets: Use precise, product-aware questions that elicit version evidence, configuration details, and mitigation timelines—no generic questionnaires or vendor fatigue.
- Remediation tracking you can prove: Monitor version changes and control deployments over time, tying each vendor’s status to the exact FocusTag and affected assets.
- Live intelligence, less cycle time: As advisories evolve, tags update—your saved views refresh automatically, keeping follow-ups targeted and reducing back-and-forth.
- Operational fit: Export affected vendors, attach evidence, and feed updates into your ticketing or GRC system to keep owners accountable and deadlines clear.
By converting complex vulnerability intelligence into actionable insights, Black Kite’s FocusTags™ empower TPRM teams to act swiftly, allocate resources effectively, and reduce exposure to the most pressing threats in today’s rapidly evolving cyber risk environment.
About Focus Friday
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FocusTagsTM in the Last 30 Days:
- MadeYouReset HTTP/2 DoS Attack : CVE-2025-8671, CVE-2025-48989, CVE-2025-54500, CVE-2025-55163, CVE-2025-36047, MadeYouReset DoS Vulnerability in HTTP/2.
- Ivanti Connect Secure – Aug2025 : CVE-2025-5456, CVE-2025-5462, Out-of-bound Read Vulnerability, DoS Vulnerability, Buffer Overflow Vulnerability in Ivanti Connect Secure (ICS), Ivanti Policy Secure (IPS), Ivanti ZTA Gateway, Ivanti Neurons for Secure Access.
- PostgreSQL – Aug2025 : CVE-2025-8713, CVE-2025-8714, CVE-2025-8715, Arbitrary Code Injection Vulnerability, Exposure of Sensitive Information Vulnerability in PostgreSQL.
- Plesk Obsidian : CVE-2025-54336, Incorrect Comparison Vulnerability in Plesk Obsidian.
- Exchange Server – Aug2025 : CVE-2025-53786, CVE-2025-25005, CVE-2025-25006, CVE-2025-25007, CVE-2025-33051, Improper Authentication, Input Validation, and Information Disclosure Vulnerabilities.
- MSSQL – Aug2025 : CVE-2025-49758, CVE-2025-24999, CVE-2025-53727, CVE-2025-49759, CVE-2025-47954, Privilege Escalation and SQL Injection Vulnerabilities.
- N-able N-Central RMM : CVE-2025-8875, CVE-2025-8876, Command Injection Vulnerability in N-able N-Central RMM.
- Squid Proxy – Aug2025 : CVE-2025-54574, Buffer Overflow Vulnerability in Squid Proxy.
- SonicWall SSL VPN – Jul2025 : CVE-2025-40600, Denial of Service Vulnerability in SonicWall SSL VPN.
- Sophos Firewall : CVE-2025-7382, CVE-2024-13973, and CVE-2024-13974, OS Command Injection Vulnerability, SQL Injection Vulnerability, Remote Code Execution Vulnerability in Sophos Firewall.
- Salesforce Tableau : CVE-2025-52446, CVE-2025-52447, CVE-2025-52448, CVE-2025-52449, CVE-2025-52452, CVE-2025-52453, CVE-2025-52454, and CVE-2025-52455, Authorization Bypass Vulnerability, Unrestricted File Upload Vulnerability, Path Traversal Vulnerability, Server-Side Request Forgery (SSRF) Vulnerability in Salesforce Tableau.
- SharePoint ToolShell : CVE-2025-49704, CVE-2025-49706, CVE-2025-53770, and CVE-2025-53771, Code Injection Vulnerability, Improper Authentication Vulnerability, Remote Code Execution Vulnerability, Path Traversal Vulnerability in Microsoft SharePoint.
- Grafana – Jul2025 : CVE-2025-6023, CVE-2025-6197, Cross-site Scripting (XSS) Vulnerability and Open Redirect Vulnerability in Grafana.
- MSSQL – Jul2025 : CVE-2025-49719, CVE-2025-49718, CVE-2025-49717, Information Disclosure Vulnerability, Remote Code Execution Vulnerability in Microsoft SQL Server.
See Black Kite’s full CVE Database and the critical TPRM vulnerabilities that have an applied FocusTagTM at https://blackkite.com/cve-database/.
References
https://thehackernews.com/2025/08/new-http2-madeyoureset-vulnerability.html
https://www.imperva.com/blog/madeyoureset-turning-http-2-server-against-itself
https://deepness-lab.org/publications/madeyoureset
https://blog.cloudflare.com/madeyoureset-an-http-2-vulnerability-thwarted-by-rapid-reset-mitigations
https://kb.cert.org/vuls/id/767506
https://tomcat.apache.org/security-11.html
https://my.f5.com/manage/s/article/K000152001
https://github.com/advisories/GHSA-prj3-ccx8-p6x4
https://www.ibm.com/support/pages/node/7242086
https://github.com/h2o/h2o/security/advisories/GHSA-mrjm-qq9m-9mjq
https://nvd.nist.gov/vuln/detail/CVE-2025-5456
https://nvd.nist.gov/vuln/detail/CVE-2025-5462
https://nvd.nist.gov/vuln/detail/CVE-2025-8715
https://www.postgresql.org/about/news/postgresql-176-1610-1514-1419-1322-and-18-beta-3-released-3118
https://nvd.nist.gov/vuln/detail/CVE-2025-8714
https://nvd.nist.gov/vuln/detail/CVE-2025-8713
https://support.plesk.com/hc/en-us/articles/33785727869847-Vulnerability-CVE-2025-54336

