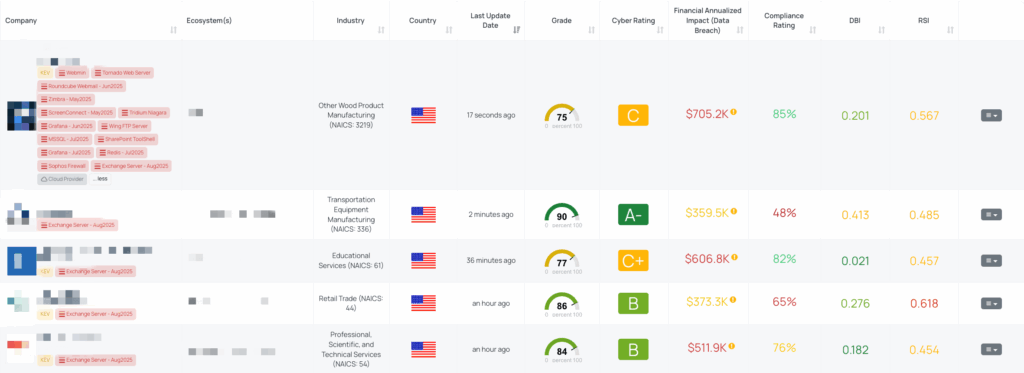
Focus Friday: TPRM Insights on Exchange Server, MSSQL, N-Able N-Central RMM, and Squid Proxy Vulnerabilities
Written by: Ferdi Gül
This week’s Focus Friday examines four critical vulnerabilities with broad implications for supply chain security and Third-Party Risk Management (TPRM). Microsoft Exchange Server and Microsoft SQL Server both received significant security updates addressing multiple privilege escalation and injection flaws. N-able N-Central RMM was patched for two actively exploited command execution vulnerabilities, underscoring the urgency of securing remote management platforms. Finally, Squid Proxy was found to contain a critical heap buffer overflow vulnerability that could lead to remote code execution and sensitive data leakage. Together, these issues highlight the importance of timely remediation, vendor coordination, and targeted risk management in protecting interconnected digital ecosystems.
Microsoft Exchange Server – CVE-2025-53786 and Related Vulnerabilities
What are the vulnerabilities in MSSQL?
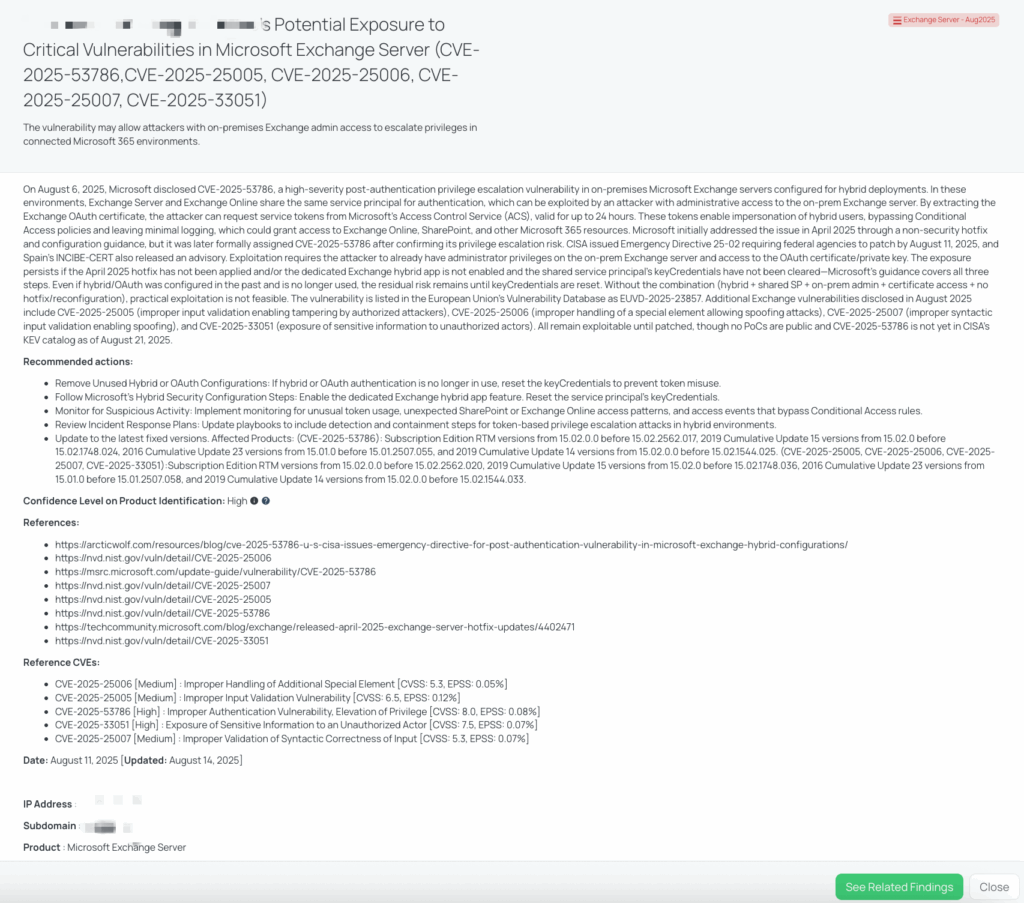
In August 2025, Microsoft disclosed five security vulnerabilities in Exchange Server, the most severe being CVE-2025-53786 (CVSS: 8.0, EPSS: 0.08%) — a high-severity post-authentication privilege escalation flaw in on-premises Exchange servers configured for hybrid deployments. In such setups, Exchange Server and Exchange Online share the same service principal for authentication. An attacker with administrator privileges on the on-prem server can extract the Exchange OAuth certificate and request service tokens from Microsoft’s Access Control Service (ACS), valid for up to 24 hours. These tokens enable impersonation of hybrid users, bypass Conditional Access policies, and allow access to Exchange Online, SharePoint, and other Microsoft 365 resources with minimal logging.
Microsoft first addressed the issue in April 2025 via a non-security hotfix and configuration guidance, later assigning it CVE-2025-53786 after confirming its privilege escalation risk. On August 6, 2025, CISA issued Emergency Directive 25-02 mandating patching by August 11, 2025, and Spain’s INCIBE-CERT released an advisory. Exploitation requires multiple conditions: the attacker must already hold administrative rights on the on-premises Exchange server, possess the OAuth certificate/private key, and the environment must still use (or retain remnants of) the shared service principal hybrid model without the April 2025 patch or an updated configuration. Even if hybrid/OAuth integration is no longer active, the risk persists until the shared service principal’s key keyCredentials are cleared. Without the combination of hybrid deployment, a shared service principal, admin access, certificate access, and the lack of patching or reconfiguration, exploitation is not feasible. This vulnerability is listed in the EU Vulnerability Database as EUVD-2025-23857.
The other August 2025 Exchange Server vulnerabilities are: CVE-2025-25005 (CVSS: 6.5, EPSS: 0.12%) – improper input validation enabling tampering by an authorized attacker; CVE-2025-25006 (CVSS: 5.3, EPSS: 0.05%) – improper handling of a special element allowing spoofing; CVE-2025-25007 (CVSS: 5.3, EPSS: 0.07%) – improper syntactic input validation enabling spoofing; and CVE-2025-33051 (CVSS: 7.5, EPSS: 0.07%) – information disclosure to unauthorized actors. All remain exploitable until patched. No public proof-of-concept (PoC) code is available, and as of August 21, 2025, none have been observed in active exploitation by threat actors. CVE-2025-53786 and others are not in CISA’s Known Exploited Vulnerabilities (KEV) catalog, but Microsoft has assessed them as “more likely” to be exploited.
Why should TPRM professionals care?
These vulnerabilities, especially CVE-2025-53786, present a significant supply chain risk because they bridge on-premises and cloud environments. A compromised vendor Exchange Server in a hybrid configuration could allow attackers to access email accounts, manipulate sensitive communications, or leverage compromised identities to infiltrate Microsoft 365 resources. The potential for bypassing Conditional Access and leaving minimal detection logs increases the difficulty of detecting malicious activity, which means a vendor compromise could silently expose your organization’s sensitive data or be used to launch further attacks.
What questions should TPRM professionals ask vendors?
To assess vendor exposure and remediation efforts, TPRM teams should consider the following targeted questions:
- Have you updated all instances of Microsoft Exchange Server to the latest fixed versions (Subscription Edition RTM versions from 15.02.0.0 before 15.02.2562.017, 2019 Cumulative Update 15 versions from 15.02.0 before 15.02.1748.024, 2016 Cumulative Update 23 versions from 15.01.0 before 15.01.2507.055, and 2019 Cumulative Update 14 versions from 15.02.0.0 before 15.02.1544.025) to mitigate the risk of CVE-2025-53786, CVE-2025-25005, CVE-2025-25006, CVE-2025-25007, and CVE-2025-33051?
- Have you implemented the recommended actions to remove unused hybrid or OAuth configurations and reset the keyCredentials to prevent token misuse as per Microsoft’s guidance to mitigate the risk of CVE-2025-53786?
- Have you enabled the dedicated Exchange hybrid app feature and reset the service principal’s keyCredentials as part of your security configuration steps to address the vulnerabilities CVE-2025-53786, CVE-2025-25005, CVE-2025-25006, CVE-2025-25007, and CVE-2025-33051?
- Are you monitoring for unusual token usage, unexpected SharePoint or Exchange Online access patterns, and access events that bypass Conditional Access rules as part of your response to the vulnerabilities CVE-2025-53786, CVE-2025-25005, CVE-2025-25006, CVE-2025-25007, and CVE-2025-33051?
Remediation recommendations for vendors
Vendors with hybrid Exchange deployments should immediately:
- Apply the April 2025 hotfix or later cumulative updates (Exchange Server 2019 CU14/CU15, 2016 CU23, or Subscription Edition RTM).
- Enable the dedicated Exchange hybrid app in Entra ID to replace the shared service principal model.
- Reset the shared service principal’s keyCredentials even if hybrid mode is no longer in use.
- Run the Microsoft Exchange Health Checker script to verify configurations and detect residual vulnerabilities.
- Monitor for anomalous access patterns, especially token-based authentication events bypassing Conditional Access.
- Update incident response plans to include detection and containment procedures for token-based privilege escalation attacks.
How can TPRM professionals leverage Black Kite for this Focus Tag?
Black Kite’s Exchange Server – Aug 2025 Focus Tag enables organizations to quickly identify vendors at risk from CVE-2025-53786 and related vulnerabilities. Once published, the Focus Tag includes:
- Detailed asset intelligence, such as IP addresses and subdomains associated with vulnerable Exchange instances.
- Identification of hybrid configurations and shared service principal usage to prioritize high-risk vendors.
- Publication and update timestamps, enabling TPRM teams to track whether vendors have been reassessed following the disclosure.
- “Last Updated” status when new vulnerabilities, exploit data, or remediation guidance is added.
MSSQL – Aug 2025 – Multiple Privilege Escalation Vulnerabilities
What are these MSSQL vulnerabilities?
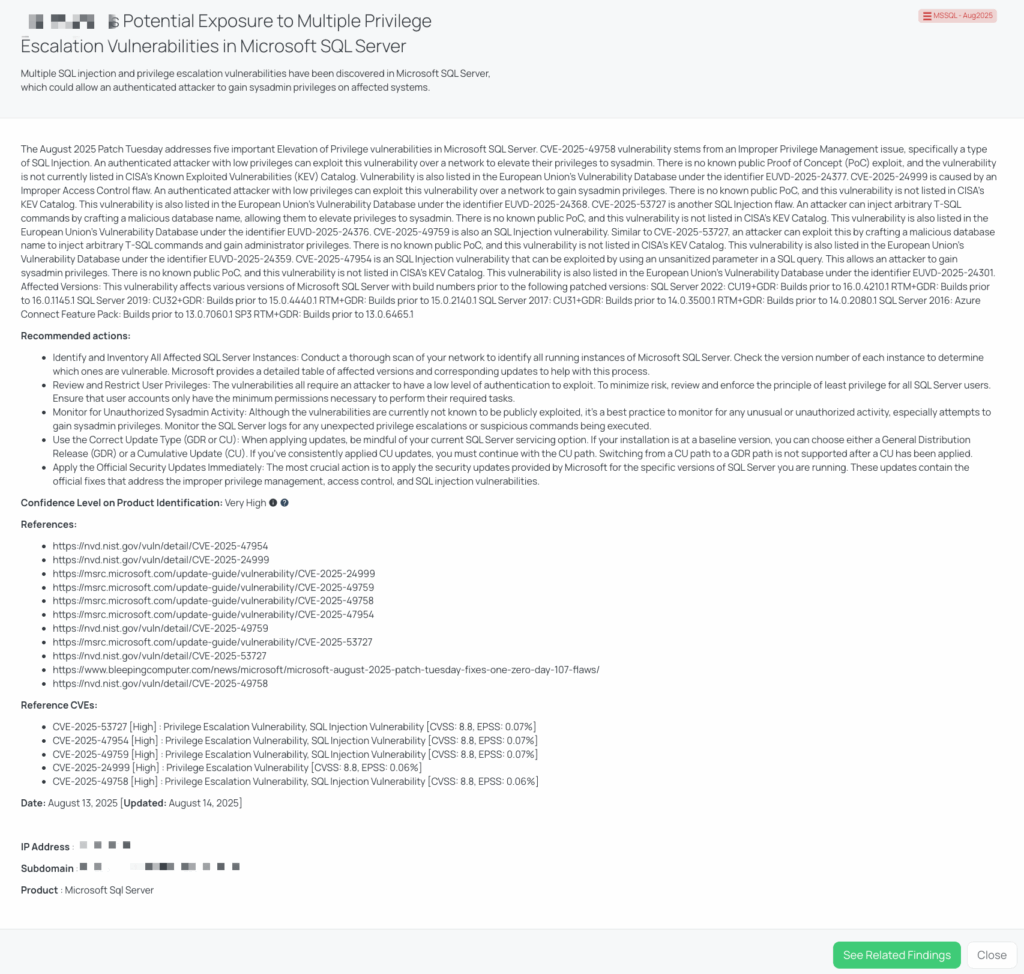
In the August 2025 Patch Tuesday release, Microsoft addressed five high-severity privilege escalation vulnerabilities in Microsoft SQL Server, all rated similarly. These include CVE-2025-49758, CVE-2025-24999, CVE-2025-53727, CVE-2025-49759, and CVE-2025-47954, each with a CVSS score of 8.8. Their EPSS scores range from 0.02% to 0.07%, underscoring varying levels of potential exploitability. Most of these issues stem from SQL injection weaknesses or improper privilege management, enabling an authenticated low-privilege user to elevate to sysadmin rights over a network. No proof-of-concept exploits are publicly available, and none of these vulnerabilities have been added to CISA’s Known Exploited Vulnerabilities (KEV) catalog as of August 2025. All five are listed in the European Union’s Vulnerability Database as EUVD-2025-24377, EUVD-2025-24368, EUVD-2025-24376, EUVD-2025-24359, and EUVD-2025-24301.
Why should TPRM professionals pay attention?
From a third-party risk management perspective, these vulnerabilities represent a significant vector for compromise: they allow unauthorized escalation to sysadmin privileges within a vendor’s SQL infrastructure. Such access could lead to unauthorized data exposure, malicious schema or data changes, or pivoting deeper into an organization’s systems. Since these vulnerabilities require only authenticated access to be exploited, they present an elevated supply chain risk—especially for vendors hosting customer data, business-critical systems, or maintaining direct access to downstream systems.
What questions should TPRM professionals ask vendors about these vulnerabilities?
To gauge vendor exposure and remediation readiness, TPRM teams should consider the following:
- Have you updated all instances of Microsoft SQL Server to the patched versions mentioned in the advisory (SQL Server 2022: CU19+GDR: Builds 16.0.4210.1 and above, RTM+GDR: Builds 16.0.1145.1 and above, SQL Server 2019: CU32+GDR: Builds 15.0.4440.1 and above, RTM+GDR: Builds 15.0.2140.1 and above, SQL Server 2017: CU31+GDR: Builds 14.0.3500.1 and above, RTM+GDR: Builds 14.0.2080.1 and above, SQL Server 2016: Azure Connect Feature Pack: Builds 13.0.7060.1 and above, SP3 RTM+GDR: Builds 13.0.6465.1 and above) to mitigate the risk of CVE-2025-49758, CVE-2025-24999, CVE-2025-53727, CVE-2025-49759, and CVE-2025-47954?
- Can you confirm if you have reviewed and restricted user privileges on all SQL Server instances to minimize the risk of these vulnerabilities being exploited by an authenticated attacker with low privileges?
- Are you monitoring for unauthorized sysadmin activity on your SQL Server instances, specifically looking for unexpected privilege escalations or suspicious commands being executed, as a precautionary measure against potential exploitation of these vulnerabilities?
- When applying updates to your SQL Server instances, did you ensure to use the correct update type (GDR or CU) based on your current SQL Server servicing option, as switching from a CU path to a GDR path is not supported after a CU has been applied?
Remediation Recommendations for Vendors
Here are key remediation steps for affected vendors:
- Apply the official security updates immediately, ensuring you use the correct servicing path—General Distribution Release (GDR) or Cumulative Update (CU), depending on your current deployment.
- Inventory all SQL Server instances across your environment to confirm patch status and identify any versions still vulnerable.
- Enforce least privilege principles, minimizing user permissions to reduce the risk of privilege misuse.
- Implement robust monitoring for abnormal sysadmin-level activities or SQL commands indicative of unauthorized escalation.
How can TPRM professionals leverage Black Kite for this vulnerability?
Black Kite’s MSSQL – Aug 2025 Focus Tag equips TPRM teams with targeted threat intel to streamline vendor risk assessments:
- It surfaces which vendors are running SQL Server instances with potentially vulnerable build numbers.
- Asset-level data like IP addresses and subdomains associated with SQL environments help prioritize outreach.
- The tag’s “Last Updated” metadata enables tracking of remediation progress over time.
- By focusing on vendors with confirmed risk indicators, you significantly reduce unnecessary questionnaire volume—targeting only those truly exposed.
CVE-2025-8875 & CVE-2025-8876 – N-able N-Central RMM
N-able N-central RMM (Remote Monitoring and Management) is a cloud-based or on-premise remote monitoring and management platform developed by N-able. Its primary purpose is to enable MSPs (Managed Service Providers) and corporate IT teams to centrally monitor and manage all devices, servers, and applications within customer or company networks.
What are these vulnerabilities?
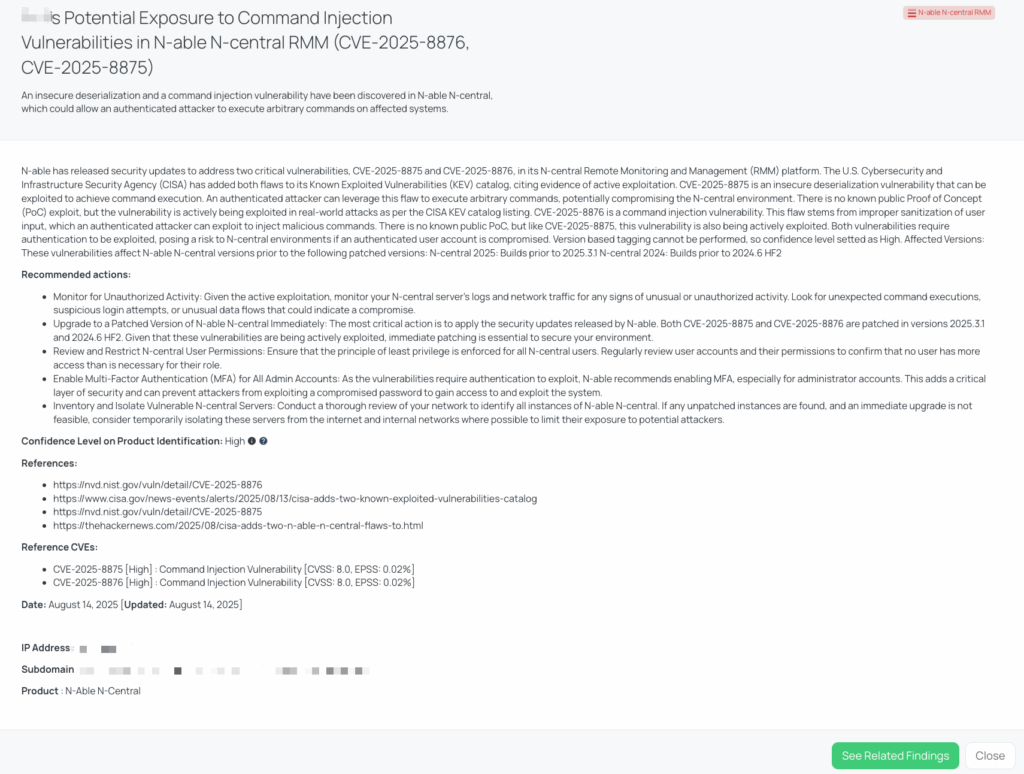
In August 2025, N-able released patches for two critical vulnerabilities affecting its N-Central Remote Monitoring and Management (RMM) platform: CVE-2025-8875 and CVE-2025-8876. Both flaws require authentication to exploit but are already being actively abused in the wild. CVE-2025-8875 is an insecure deserialization issue that allows an authenticated attacker to execute arbitrary commands on the affected system. CVE-2025-8876 is a command injection flaw caused by improper input sanitization, enabling attackers with valid credentials to inject and run malicious commands.
CISA added both vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog on August 13, 2025, following confirmation of active exploitation in real-world attacks. Although no public proof-of-concept exploits exist, the active exploitation status significantly increases the urgency for patching. These flaws impact N-Central versions prior to 2025.3.1 and 2024.6 HF2.
Why should TPRM professionals care?
Because these vulnerabilities are actively exploited and target a widely used RMM platform, they carry substantial supply chain implications. An exploited N-Central instance could give attackers a foothold into a vendor’s managed infrastructure, enabling further compromise of customer networks, exfiltration of sensitive data, or deployment of ransomware across connected systems. Given the centralized control RMM tools have over endpoints, a successful attack could quickly propagate, affecting multiple downstream organizations.
What questions should TPRM professionals ask vendors?
To evaluate vendor risk and remediation status, TPRM teams should consider asking:
- Have you updated all instances of N-able N-central to versions 2025.3.1 or 2024.6 HF2 to mitigate the risk of CVE-2025-8875 and CVE-2025-8876?
- Can you confirm if you have implemented multi-factor authentication (MFA) for all admin accounts to prevent potential exploitation of these vulnerabilities?
- Have you conducted a thorough review of your network to identify all instances of N-able N-central and isolated any unpatched instances from the internet and internal networks?
- Are you actively monitoring your N-central server’s logs and network traffic for any signs of unusual or unauthorized activity, such as unexpected command executions, suspicious login attempts, or unusual data flows?
Remediation recommendations for vendors
Vendors should take the following immediate steps:
- Apply the official N-able security updates to bring all instances to at least version 2025.3.1 or 2024.6 HF2.
- Monitor system logs and network activity for signs of command execution or other anomalous behavior.
- Restrict user permissions to the minimum required for operational needs, removing unnecessary admin rights.
- Enable multi-factor authentication (MFA) for all privileged accounts to prevent exploitation through stolen credentials.
- Identify and isolate any unpatched instances from both the internet and internal networks until updates can be applied.
How can TPRM professionals leverage Black Kite for this vulnerability?
Black Kite’s N-able N-Central RMM Focus Tag, published August 14, 2025, enables TPRM teams to quickly identify vendors operating potentially vulnerable N-Central instances. The tag includes asset intelligence such as IP addresses and subdomains linked to affected environments, allowing for targeted outreach. By leveraging this intelligence, TPRM professionals can prioritize engagement with at-risk vendors, verify their patch status, and reduce unnecessary questionnaires to unaffected parties.
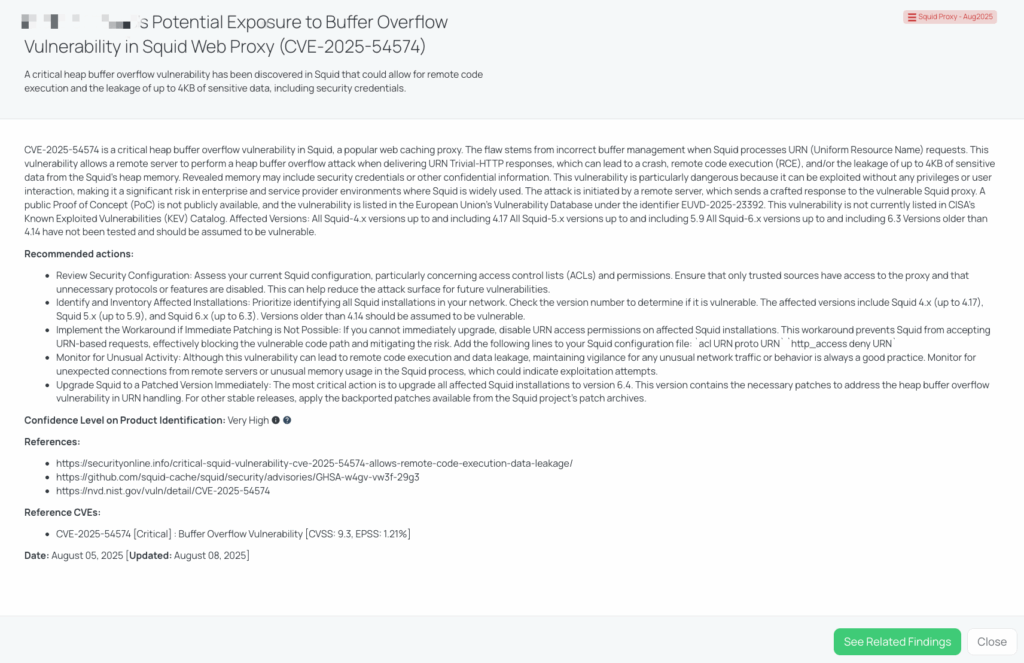
CVE-2025-54574 – Squid Proxy
What is the Squid Proxy buffer overflow vulnerability?
CVE-2025-54574 is a critical heap buffer overflow vulnerability in Squid, a widely used web caching proxy, carrying a CVSS score of 9.3 and an EPSS score of 1.22%. The flaw is caused by incorrect buffer management when processing Uniform Resource Name (URN) requests. When a vulnerable Squid instance receives a specially crafted URN Trivial-HTTP response from a remote server, it can trigger a heap buffer overflow, potentially leading to remote code execution (RCE), process crashes, or the leakage of up to 4KB of sensitive memory contents. This exposed data may include credentials or other confidential information.
The vulnerability can be exploited without privileges or user interaction, significantly increasing the potential risk in enterprise and service provider networks where Squid acts as a critical infrastructure component. All Squid 4.x versions up to 4.17, 5.x up to 5.9, and 6.x up to 6.3 are affected. Versions older than 4.14 have not been tested but should be considered vulnerable. A patched release, Squid 6.4, and backported fixes for other supported branches have been issued. No public proof-of-concept (PoC) exploit has been released, and this vulnerability is not listed in CISA’s Known Exploited Vulnerabilities (KEV) catalog as of mid-August 2025. It is registered in the European Union’s Vulnerability Database under EUVD-2025-23392.
Why should TPRM professionals care about CVE-2025-54574?
From a third-party risk perspective, this vulnerability poses a significant threat to organizations relying on vendors that deploy Squid proxies within their infrastructure. Because the flaw can be exploited remotely and without user action, a compromised Squid instance could be leveraged to execute malicious code within a vendor’s network or exfiltrate sensitive information. In managed service environments or ISPs, exploitation could result in widespread compromise or data leakage affecting multiple downstream customers. The lack of required authentication or interaction means any vendor operating an unpatched Squid version could serve as an immediate and exploitable entry point.
What questions should TPRM professionals ask vendors about CVE-2025-54574?
When assessing a vendor’s exposure and mitigation status, TPRM teams should ask:
- Can you confirm if you have upgraded all instances of Squid to version 6.4 or later to mitigate the risk of CVE-2025-54574?
- If you are unable to upgrade immediately, have you implemented the workaround by disabling URN access permissions on affected Squid installations?
- Have you reviewed your current Squid configuration, particularly concerning access control lists (ACLs) and permissions, to ensure that only trusted sources have access to the proxy and that unnecessary protocols or features are disabled?
- Are you monitoring for unexpected connections from remote servers or unusual memory usage in the Squid process, which could indicate exploitation attempts of CVE-2025-54574?
Remediation recommendations for vendors
Vendors should take the following actions immediately:
- Upgrade to a patched version – Deploy Squid 6.4 or apply backported patches for Squid 4.x and 5.x as recommended by the project maintainers.
- Restrict URN handling – If patching cannot be completed immediately, disable URN protocol handling by adding acl URN proto URN and http_access deny URN to the configuration.
- Harden configurations – Limit proxy access to trusted sources and remove unnecessary features or protocols.
- Inventory vulnerable installations – Identify all instances of Squid in the environment and prioritize patching based on exposure.
- Implement monitoring – Track for abnormal behavior such as spikes in memory use, crashes, or unusual outbound connections that could indicate an exploitation attempt.
How can TPRM professionals leverage Black Kite for this vulnerability?
Black Kite’s Squid Proxy – Aug 2025 Focus Tag, published August 5, 2025, enables security and risk teams to pinpoint which vendors have potentially vulnerable Squid installations. The tag provides detailed asset intelligence, including IP addresses and subdomains linked to identified Squid servers, enabling targeted vendor outreach. By using this data, TPRM professionals can prioritize high-risk vendors for immediate verification and remediation, while avoiding unnecessary engagement with unaffected parties.
Maximizing TPRM Effectiveness with Black Kite’s Focus Tags™
Black Kite’s Focus Tags™ provide a decisive advantage for organizations facing critical vulnerabilities like those affecting Exchange Server, MSSQL, N-able N-Central RMM, and Squid Proxy. These tags enable:
- Real-Time Vulnerability Mapping – Rapidly identify which vendors are running affected products, allowing faster, more targeted response efforts.
- Prioritized Risk Management – Focus attention on vulnerabilities that matter most, based on vendor criticality and the potential impact on your organization’s operations.
- Informed Vendor Engagement – Drive more productive conversations with vendors by discussing their specific exposure and mitigation actions.
- Holistic Security Oversight – Gain a comprehensive understanding of the threat landscape to inform strategic cybersecurity planning.
By converting complex vulnerability intelligence into actionable insights, Black Kite’s Focus Tags™ empower TPRM teams to act swiftly, allocate resources effectively, and reduce exposure to the most pressing threats in today’s rapidly evolving cyber risk environment.
About Focus Friday
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FocusTagsTM in the Last 30 Days:
- Exchange Server – Aug2025 : CVE-2025-53786, CVE-2025-25005, CVE-2025-25006, CVE-2025-25007, CVE-2025-33051, Improper Authentication, Input Validation, and Information Disclosure Vulnerabilities.
- MSSQL – Aug2025 : CVE-2025-49758, CVE-2025-24999, CVE-2025-53727, CVE-2025-49759, CVE-2025-47954, Privilege Escalation and SQL Injection Vulnerabilities.
- N-able N-Central RMM : CVE-2025-8875, CVE-2025-8876, Command Injection Vulnerability in N-able N-Central RMM.
- Squid Proxy – Aug2025 : CVE-2025-54574, Buffer Overflow Vulnerability in Squid Proxy.
- SonicWall SSL VPN – Jul2025 : CVE-2025-40600, Denial of Service Vulnerability in SonicWall SSL VPN.
- Sophos Firewall : CVE-2025-7382, CVE-2024-13973, and CVE-2024-13974, OS Command Injection Vulnerability, SQL Injection Vulnerability, Remote Code Execution Vulnerability in Sophos Firewall.
- Salesforce Tableau : CVE-2025-52446, CVE-2025-52447, CVE-2025-52448, CVE-2025-52449, CVE-2025-52452, CVE-2025-52453, CVE-2025-52454, and CVE-2025-52455, Authorization Bypass Vulnerability, Unrestricted File Upload Vulnerability, Path Traversal Vulnerability, Server-Side Request Forgery (SSRF) Vulnerability in Salesforce Tableau.
- SharePoint ToolShell : CVE-2025-49704, CVE-2025-49706, CVE-2025-53770, and CVE-2025-53771, Code Injection Vulnerability, Improper Authentication Vulnerability, Remote Code Execution Vulnerability, Path Traversal Vulnerability in Microsoft SharePoint.
- Grafana – Jul2025 : CVE-2025-6023, CVE-2025-6197, Cross-site Scripting (XSS) Vulnerability and Open Redirect Vulnerability in Grafana.
- MSSQL – Jul2025 : CVE-2025-49719, CVE-2025-49718, CVE-2025-49717, Information Disclosure Vulnerability, Remote Code Execution Vulnerability in Microsoft SQL Server.
- Redis – Jul2025 : CVE-2025-32023, CVE-2025-48367, Buffer Overflow Vulnerability, Denial of Service Vulnerability in Redis.
- Zimbra – Jul2025 : CVE-2019-9621, Server-Side Request Forgery (SSRF) Vulnerability in Zimbra.
- Citrix Bleed 2 : CVE-2025-6543, CVE-2025-5777, CVE-2025-5349, Buffer Overflow Vulnerability, Out-of-Bounds Memory Read Vulnerability, RCE Vulnerability, and Improper Access Control Vulnerability in NetScaler ADC and NetScaler Gateway.
- Wing FTP Server : CVE-2025-47812, Remote Code Execution Vulnerability in Wing FTP Server.
See Black Kite’s full CVE Database and the critical TPRM vulnerabilities that have an applied FocusTagTM at https://blackkite.com/cve-database/.
References
https://nvd.nist.gov/vuln/detail/CVE-2025-53786
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-53786
https://nvd.nist.gov/vuln/detail/CVE-2025-47954
https://nvd.nist.gov/vuln/detail/CVE-2025-24999
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-24999
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-49759
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-49758
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-47954
https://nvd.nist.gov/vuln/detail/CVE-2025-49759
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-53727
https://nvd.nist.gov/vuln/detail/CVE-2025-53727
https://nvd.nist.gov/vuln/detail/CVE-2025-49758
https://nvd.nist.gov/vuln/detail/CVE-2025-8876
https://nvd.nist.gov/vuln/detail/CVE-2025-8875
https://thehackernews.com/2025/08/cisa-adds-two-n-able-n-central-flaws-to.html
https://github.com/squid-cache/squid/security/advisories/GHSA-w4gv-vw3f-29g3

