FOCUS FRIDAY: TPRM Insights into Mattermost Arbitrary File Write and MongoDB Denial-of-Service Vulnerabilities
Written by: Ferdi Gül
This week’s Focus Friday delves into two recently disclosed vulnerabilities that carry significant implications for third-party risk: a critical arbitrary file write vulnerability in Mattermost, and two denial-of-service (DoS) vulnerabilities in MongoDB Server. While both platforms serve distinct operational roles—collaboration and data infrastructure—their security weaknesses can have wide-reaching consequences if leveraged in targeted attacks. From improperly sanitized archive extractions to uncontrolled recursion in JSON parsing, these vulnerabilities reveal how even foundational features can be weaponized in the wrong context.
With Black Kite’s FocusTags™, Third-Party Risk Management (TPRM) teams gain direct visibility into which vendors are potentially exposed, making it easier to focus on what matters most. This edition outlines the technical risks associated with these vulnerabilities, provides actionable questions for vendor engagement, and shares remediation strategies—all tailored to support efficient, risk-informed decision-making in vendor ecosystems. The Black Kite research group issues FocusTags™ for our customers on the most critical vulnerabilities impacting third-party cyber ecosystems from the full CVE Database.
CVE-2025-4981: Mattermost Arbitrary File Write Vulnerability
Mattermost is an open-source, self-hosted messaging and collaboration platform designed primarily for team communication and workflow coordination. It is often used as a secure alternative to proprietary messaging tools like Slack or Microsoft Teams, especially in environments that require data privacy, compliance, and complete control over deployment.
What is the Mattermost Arbitrary File Write Vulnerability?
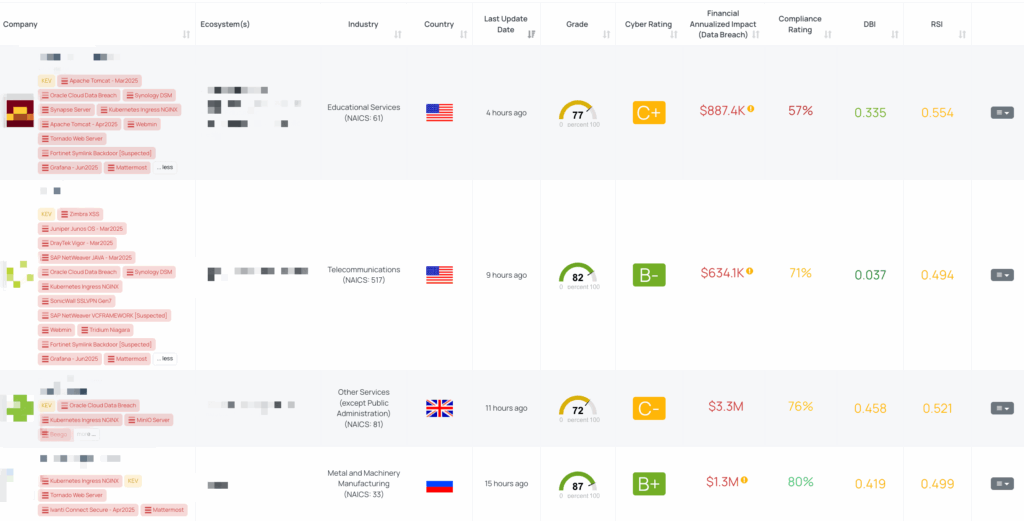
CVE-2025-4981 is a critical path traversal vulnerability in Mattermost, an open-source collaboration platform. It affects versions 10.5.x (up to 10.5.5), 9.11.x (up to 9.11.15), 10.8.0, 10.7.x (up to 10.7.2), and 10.6.x (up to 10.6.5). The flaw resides in the archive extraction component, where filenames within uploaded archive files are not properly sanitized. This allows authenticated users to perform path traversal by including sequences such as ‘../’ in archive filenames, potentially enabling them to write files to arbitrary locations on the server’s filesystem. If exploited, this could lead to remote code execution (RCE) in certain environments.
The vulnerability specifically impacts Mattermost instances where both FileSettings.EnableFileAttachments and FileSettings.ExtractContent are set to true, which are the default settings. Exploitation requires a valid authenticated session with file upload capabilities but does not necessitate elevated privileges. As of now, there is no public proof-of-concept (PoC) code available, and the vulnerability has not been added to CISA’s Known Exploited Vulnerabilities catalog. However, due to the potential for RCE through arbitrary file writes, it poses significant security implications.
The vulnerability was disclosed on June 20, 2025, and has been assigned a CVSS v3.1 base score of 9.9 (Critical) with an EPSS score of 0.23%.
Why Should TPRM Professionals Be Concerned?
Mattermost is widely used for internal communications and collaboration, often handling sensitive information. A vulnerability that allows authenticated users to write files to arbitrary locations on the server’s filesystem can have severe consequences. If exploited, attackers could potentially execute arbitrary code, leading to unauthorized access to sensitive data, disruption of services, or further compromise of the organization’s network. Given that the affected settings are enabled by default, many deployments may be vulnerable without administrators realizing it.
What Questions Should TPRM Professionals Ask Vendors About This Vulnerability?
To assess the risk posed by CVE-2025-4981 in your supply chain, consider asking vendors the following questions:
- Have you updated all instances of Mattermost to versions beyond 10.5.5, 9.11.15, 10.8.0, 10.7.2, and 10.6.5 to mitigate the risk of CVE-2025-4981?
- Can you confirm if the FileSettings.EnableFileAttachments and FileSettings.ExtractContent configuration options are enabled in your Mattermost instances? If so, have you considered disabling the ExtractContent feature to reduce the attack surface?
- Have you implemented stricter file type validation and scanning of uploaded archives for suspicious or nested path traversal sequences before extraction to prevent potential exploitation of the Arbitrary File Write vulnerability in Mattermost?
- Are you monitoring logs for unusual archive names or file write activity outside expected paths and integrating with SIEM platforms for alerting on suspicious patterns to detect potential exploitation of the Arbitrary File Write vulnerability in Mattermost?
Remediation Recommendations for Vendors Subject to This Risk
Vendors using affected versions of Mattermost should take the following actions:
- Upgrade Affected Systems: Immediately upgrade to patched versions beyond 10.5.5, 9.11.15, 10.8.0, 10.7.2, and 10.6.5 to address the vulnerability.
- Audit Configuration Settings: Review the Mattermost configuration, particularly the EnableFileAttachments and ExtractContent settings under FileSettings. If content extraction is not business-critical, consider disabling ExtractContent to reduce the attack surface.
- Restrict File Upload Capabilities: Limit file upload functionality to trusted users or groups. Enforce stricter file type validation and scan uploaded archives for suspicious or nested path traversal sequences before extraction.
- Implement Application Hardening: Run the Mattermost server with reduced privileges and apply filesystem permissions that prevent the application from writing to sensitive or executable directories. Use chroot jails or containers to further isolate file handling operations.
- Deploy Web Application Firewall (WAF): Use a WAF to detect and block file uploads containing potentially malicious path traversal patterns (e.g., ../). Configure the WAF with custom rules targeting archive file uploads to prevent exploitation.
- Enable Logging and Monitor File Activity: Ensure detailed logging of file uploads and extraction operations is enabled. Monitor logs for unusual archive names or file write activity outside expected paths. Integrate with SIEM platforms for alerting on suspicious patterns.
- Restrict Network and Role-Based Access: Ensure Mattermost services are not exposed to unnecessary networks and that only authenticated, authorized users can upload files. Apply the principle of least privilege in assigning user roles and capabilities.
- Conduct Security Testing and Code Review: Periodically perform security assessments focused on file handling and input sanitization. Review custom plugins or extensions for similar flaws in archive processing or file path handling.
- Stay Informed: Subscribe to Mattermost security advisories and monitor CVE databases for updates on related vulnerabilities. Track configuration best practices and apply security patches promptly to limit exposure to future threats.
How TPRM Professionals Can Leverage Black Kite for This Vulnerability
Black Kite published the FocusTag for CVE-2025-4981 on June 23, 2025. This tag enables TPRM professionals to identify vendors potentially affected by this vulnerability. The FocusTag provides detailed information, including the specific assets (IP addresses and subdomains) associated with the vulnerable Mattermost instances. This intelligence allows organizations to prioritize their risk assessments and remediation efforts, focusing on vendors with confirmed exposure to the vulnerability.
By leveraging Black Kite’s FocusTags™, TPRM professionals can streamline their third-party risk management processes, reducing the time and resources spent on broad, non-specific assessments. This targeted approach enhances the efficiency and effectiveness of vulnerability management across the supply chain.
CVE-2025-6709 & CVE-2025-6710: MongoDB Arbitrary JSON Input Handling and Stack Overflow Vulnerabilities
What are the MongoDB Denial-of-Service Vulnerabilities?
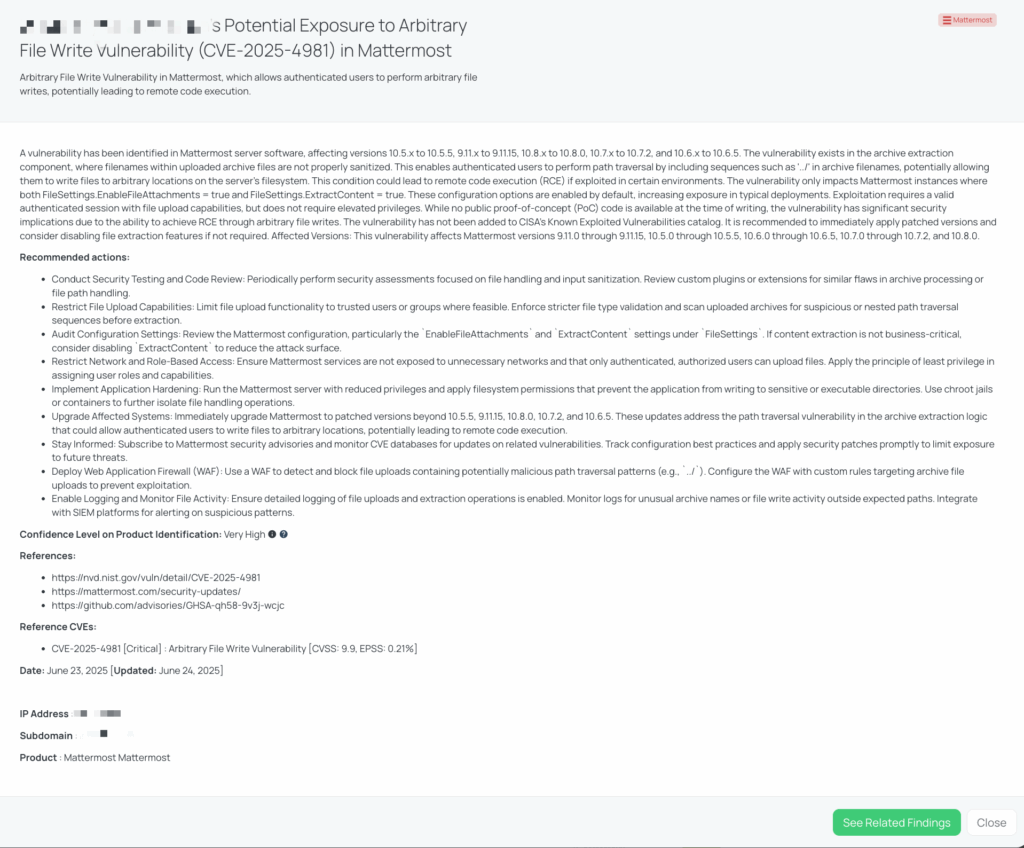
Two denial-of-service (DoS) vulnerabilities, CVE-2025-6709 and CVE-2025-6710, were publicly disclosed on June 27, 2025, affecting MongoDB Server versions prior to 8.0.5, 7.0.17, and 6.0.21.
- CVE-2025-6709 arises from improper handling of specific date values in JSON payloads during OpenID Connect (OIDC) authentication. When such malformed inputs are sent—particularly via the mongo shell—they can trigger an invariant failure and cause the server to crash. Notably, OIDC authentication is not enabled by default in MongoDB; administrators must configure it manually. In affected 7.0 and 8.0 versions, exploitation can occur pre-authentication, increasing the risk in externally exposed environments.
- CVE-2025-6710 involves a flaw in MongoDB’s JSON parsing logic that fails to limit recursive depth. A specially crafted, deeply nested JSON payload can exhaust stack memory, resulting in a stack overflow and subsequent server crash. This vulnerability can also be exploited pre-authentication in MongoDB 7.0 and 8.0, while on version 6.0, an authenticated session is required.
Both vulnerabilities have been assigned a CVSS v3.1 base score of 7.5 (High), but there is no known public proof-of-concept (PoC) available at this time. Additionally, neither CVE-2025-6709 nor CVE-2025-6710 has been added to CISA’s Known Exploited Vulnerabilities (KEV) Catalog as of this writing. These issues can cause immediate service disruption, making them especially impactful in high-availability database environments.
Why Should TPRM Professionals Be Concerned?
MongoDB is widely used as a back-end data store in enterprise and SaaS applications, often holding sensitive records or powering mission-critical services. A successful exploitation of either vulnerability could abruptly terminate database availability, causing cascading failures across business processes. For CVE-2025-6709, even unauthenticated attackers may trigger the crash in systems that use OIDC, amplifying exposure. Likewise, CVE-2025-6710 represents a broader risk because any component accepting external JSON input—such as web APIs or microservices—could serve as a delivery vector for malicious payloads.
For vendors relying on MongoDB, this could translate to downtime, failed transactions, or degraded performance, all of which reflect poorly on vendor reliability from a third-party risk perspective. TPRM professionals should be proactive in determining vendor exposure and ensuring proper patching and mitigations are in place.
As of now, there is no publicly available proof-of-concept (PoC) code for either vulnerability, and neither CVE-2025-6709 nor CVE-2025-6710 has been listed in CISA’s Known Exploited Vulnerabilities (KEV) catalog. Since both issues are addressed in the same patch versions, it is highly advisable to update all impacted MongoDB deployments without delay. These vulnerabilities are tracked in the EU Vulnerability Database under identifiers EUVD-2025-19228 and EUVD-2025-19230.
What questions should TPRM professionals ask vendors about the MongoDB vulnerabilities?
To accurately assess vendor exposure and risk related to these vulnerabilities, TPRM professionals can ask the following questions:
- Have you upgraded all instances of MongoDB Server to version 8.0.5, 7.0.17, or 6.0.21 to mitigate the risk of CVE-2025-6710 and CVE-2025-6709?
- Can you confirm if your MongoDB instances are configured to use OpenID Connect, and if so, have you taken steps to mitigate the risk of CVE-2025-6709?
- Have you implemented a deep packet inspection firewall or reverse proxy to validate JSON structures and block requests with excessive nesting or malformed OIDC requests?
- Are you monitoring MongoDB logs for patterns of failed authentication attempts, malformed JSON errors, and unexpected server restarts to detect potential exploitation attempts of CVE-2025-6710 and CVE-2025-6709?
Remediation Recommendations for Vendors Subject to This Risk
To mitigate the risks associated with these vulnerabilities, vendors should:
- Apply Security Updates Immediately: Upgrade to MongoDB Server versions 8.0.5, 7.0.17, or 6.0.21, which contain patches for both vulnerabilities.
- Disable OIDC Temporarily (if unused): For CVE-2025-6709, consider disabling OIDC authentication if it is not critical. This closes a pre-auth attack vector.
- Limit Network Exposure: Ensure that MongoDB is not directly accessible from public networks. Use firewall rules to limit access to internal application servers only.
- Use Input Validation Gateways: Employ reverse proxies or WAFs capable of inspecting JSON payloads. Block excessive nesting and malformed date formats.
- Implement Logging & Monitoring: Monitor authentication logs, JSON parsing errors, and server crashes. Forward logs to a SIEM for real-time alerting and analysis.
- Design for High Availability: Operate MongoDB as a replica set or sharded cluster. If a crash occurs, automatic failover can minimize service impact.
How TPRM Professionals Can Leverage Black Kite for These Vulnerabilities
Black Kite published the FocusTag for CVE-2025-6709 and CVE-2025-6710 on June 27, 2025, under the tag MongoDB – Jun2025. This FocusTag enables TPRM professionals to quickly identify vendors that may be operating vulnerable MongoDB instances, with high confidence.
Black Kite provides granular intelligence by associating specific IP addresses or subdomains with known vulnerable MongoDB versions. This asset-level visibility empowers organizations to prioritize their outreach to only those vendors at confirmed risk—dramatically reducing the noise from unnecessary assessments. Combined with vulnerability metadata, affected version ranges, and technical remediation guidance, the MongoDB FocusTag helps teams make informed, efficient decisions in real-time.
By incorporating these insights into their third-party risk workflows, organizations can move from reactive triage to proactive, intelligence-driven risk management—strengthening their entire supply chain posture.
Enhancing TPRM Efficiency with Black Kite’s FocusTags™
As seen in the cases of Mattermost’s remote code execution risk and MongoDB’s denial-of-service vulnerabilities, third-party software can rapidly become a liability when new exploits emerge. Black Kite’s FocusTags™ are purpose-built to assist TPRM professionals in addressing these emerging challenges with precision and speed. Here’s how:
- Rapid Vendor Attribution: FocusTags™ help identify vendors whose exposed systems match affected software and configurations—whether that’s OIDC-enabled MongoDB instances or Mattermost servers with default archive extraction settings.
- Risk-Informed Prioritization: Instead of sending questionnaires to hundreds of vendors indiscriminately, organizations can zero in on those with verified exposure, optimizing internal resources and response timelines.
- Customized Vendor Outreach: FocusTags™ offer context-specific guidance for engaging vendors based on their potential exposure and system roles—empowering risk managers to ask targeted, meaningful questions.
- Asset-Level Transparency: The ability to view associated IP addresses and subdomains linked to vulnerable systems sets Black Kite apart, providing unparalleled depth for risk assessment.
By transforming raw CVE data into operational intelligence, Black Kite’s FocusTags™ enable security and risk teams to stay ahead of potential supply chain disruptions and align their actions with the dynamic threat landscape.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
About Focus Friday
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FocusTags™ in the Last 30 Days:
- MongoDB – Jun2025 : CVE-2025-6709, CVE-2025-6710, DoS Vulnerabilities in MongoDB.
- Mattermost : CVE-2025-4981, Arbitrary File Write Vulnerability in Mattermost.
- Grafana – Jun2025 : CVE-2025-4123, Cross-Site Scripting (XSS) Vulnerability, Open Redirect Vulnerability, SSRF Vulnerability in Grafana.
- Cisco ClamAV : CVE-2025-20260, CVE-2025-20234, Heap-based Buffer Overflow Vulnerability, Out-of-bounds Read Vulnerability in Cisco ClamAV.
- Elastic Kibana : CVE-2024-43706, Improper Authorization Vulnerability in Elastic Kibana.
- Tridium Niagara : CVE-2025-3936, CVE-2025-3937, CVE-2025-3938, CVE-2025-3939, CVE-2025-3940, CVE-2025-3941, CVE-2025-3942, CVE-2025-3943, CVE-2025-3944, and CVE-2025-3945, Multiple Critical Vulnerabilities in Niagara Framework, Niagara Enterprise Security.
- Roundcube Webmail – Jun2025 : CVE-2025-49113, Remote Code Execution Vulnerability, Deserialization of Untrusted Data in Roundcube Webmail.
- ScreenConnect – May2025 : CVE-2025-3935, Improper Authentication Vulnerability in ConnectWise ScreenConnect.
- Zimbra – May2025 : CVE-2024-27443, Cross-Site Scripting (XSS) Vulnerability in Zimbra Collaboration (ZCS).
- DrayTek Vigor – May2025 : CVE-2024-12987, OS Command Injection Vulnerability in DrayTek Vigor Routers.
- Atlassian Jira Data Center : CVE-2025-22157, Privilege Escalation Vulnerability in Jira Core Data Center, Jira Core Server, Jira Service Management Data Center, Jira Service Management Server.
- Tornado Web Server : CVE-2025-47287, DoS Vulnerability in Tornado Web Server.
- MDaemon Email Server : CVE-2024-11182, Cross-Site Scripting (XSS) Vulnerability in MDaemon Email Server.
- Ivanti EPMM – May2025 : CVE-2025-4427, CVE-2025-4428, Authentication Bypass and Remote Code Execution Vulnerability in Ivanti Endpoint Manager Mobile (EPMM)
See Black Kite’s full CVE Database and the critical TPRM vulnerabilities that have an applied FocusTag at https://blackkite.com/cve-database/.
References
https://nvd.nist.gov/vuln/detail/CVE-2025-4981
https://mattermost.com/security-updates
https://github.com/advisories/GHSA-qh58-9v3j-wcjc
https://nvd.nist.gov/vuln/detail/CVE-2025-6709
https://nvd.nist.gov/vuln/detail/CVE-2025-6710

