Focus Friday: TPRM Insights into Zimbra, Draytek Vigor, Atlassian Jira Data Center, Tornado, and MDaemon Vulnerabilities
Written by: Ferdi Gül
This Week’s Emerging Third-Party Risks in Email Infrastructure and Web Frameworks
Welcome to this week’s edition of Focus Friday, where we provide timely insights into high-profile vulnerabilities from a Third-Party Risk Management (TPRM) lens. In today’s interconnected environment, vulnerabilities affecting one vendor’s technology stack can ripple across entire ecosystems—disrupting operations, compromising sensitive data, and escalating vendor risk exposure.
This week’s FocusTags™ spotlight several notable vulnerabilities with direct implications for organizations relying on third-party software for communication infrastructure and web application delivery. We begin with Zimbra’s CalendarInvite XSS vulnerability, already being exploited by APT28; then examine DrayTek Vigor gateway devices, which are being recruited into botnets due to a critical OS command injection flaw. We also review a newly disclosed privilege escalation vulnerability in Atlassian Jira Data Center, which allows low-privilege users to act with higher-privilege permissions, threatening issue tracking and service management workflows. In addition, we cover a Denial-of-Service vulnerability in Tornado Web Server that threatens application availability, and an actively exploited zero-day XSS vulnerability in MDaemon Email Server, used for credential theft and mailbox compromise.
Each of these incidents highlights the urgency of identifying and remediating vulnerabilities—not just internally, but across your third-party network. This blog helps TPRM professionals do exactly that.
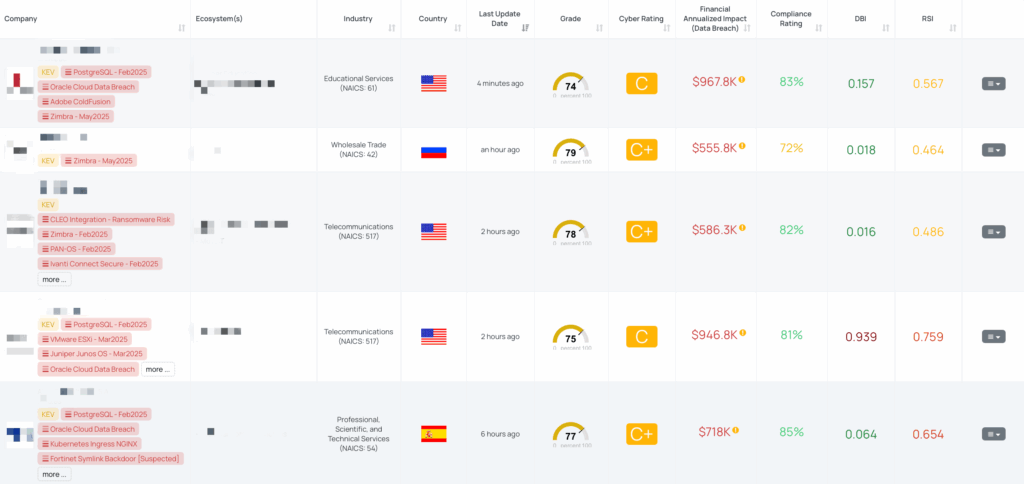
CVE-2024-27443 – Zimbra Webmail CalendarInvite XSS Vulnerability
What is CVE-2024-27443 in Zimbra?
CVE-2024-27443 is a medium-severity reflected Cross-Site Scripting (XSS) vulnerability affecting Zimbra Collaboration Suite (ZCS) versions 9.0.x (prior to Patch 39) and 10.0.x (prior to 10.0.7). The flaw resides in the Classic Webmail UI’s CalendarInvite feature, where the X-Zimbra-Calendar-Intended-For email header is improperly sanitized. This allows attackers to inject malicious JavaScript into calendar invitations.
When a user opens a crafted calendar invite in the Classic UI, the embedded script executes within their webmail session, potentially enabling attackers to:
- Steal authentication cookies
- Redirect or manipulate incoming emails
- Insert unauthorized calendar events
- Send emails or alter contact information as the user.
The vulnerability has a CVSS v3.1 score of 6.1 (Medium) and an EPSS score of 16.22%. It was patched on March 1, 2024, but was added to CISA’s Known Exploited Vulnerabilities (KEV) catalog on May 19, 2025, indicating active exploitation in the wild. Notably, the Sednit group (also known as APT28) has been linked to exploiting this vulnerability as part of Operation RoundPress, targeting governmental and defense entities in Eastern Europe and beyond.
Why Should TPRM Professionals Be Concerned About CVE-2024-27443?
Zimbra is widely used for enterprise email and calendar services. A compromise of its webmail interface can lead to unauthorized access to sensitive communications and data. The exploitation of CVE-2024-27443 allows attackers to impersonate users, exfiltrate confidential information, and potentially pivot to other systems within the organization.Given the association with APT28, a state-sponsored threat actor, the risk extends to espionage and targeted attacks against critical sectors.
What Questions Should TPRM Professionals Ask Vendors Regarding CVE-2024-27443?
- Have you upgraded your Zimbra Collaboration to at least 9.0.0 P39 or 10.0.7 to mitigate the risk of CVE-2024-27443?
- Have you implemented the recommended hardening measures such as disabling or restricting HTML calendar rendering in the Classic UI and enforcing a Content Security Policy (CSP) to block inline scripts in email/calendar views?
- Have you reviewed your webmail access logs for suspicious calendar invite parameters and deployed IDS/IPS signatures to detect XSS payload patterns in calendar headers as recommended?
- Can you confirm if you have trained your users to view calendar invitations only from trusted senders and report unexpected invites as part of your mitigation strategy against CVE-2024-27443?
Remediation Recommendations for Vendors Affected by CVE-2024-27443
- Apply Vendor Patches: Upgrade Zimbra Collaboration to at least version 9.0.0 Patch 39 or 10.0.7.
- Harden Webmail Rendering: Disable or restrict HTML rendering in calendar invitations within the Classic UI until patching is complete.
- Enforce Content Security Policies (CSP): Implement CSP to block inline scripts in email and calendar views.
- User Training: Educate users to be cautious with calendar invites, especially from unknown senders, and to report suspicious activities.
- Monitor and Detect: Review webmail access logs for unusual calendar invite parameters and deploy intrusion detection systems to identify XSS payload patterns.
How Can TPRM Professionals Leverage Black Kite for CVE-2024-27443?
Black Kite has issued the “Zimbra – May2025” FocusTag, providing high-confidence intelligence on vendors potentially exposed to CVE-2024-27443. This tag includes detailed information such as affected assets, IP addresses, and subdomains associated with vulnerable Zimbra deployments. By utilizing this FocusTag, TPRM professionals can:
- Quickly identify and prioritize vendors at risk
- Access actionable intelligence to assess the extent of exposure
- Streamline communication with vendors regarding remediation efforts
- Reduce the burden of broad-based questionnaires by focusing on affected parties
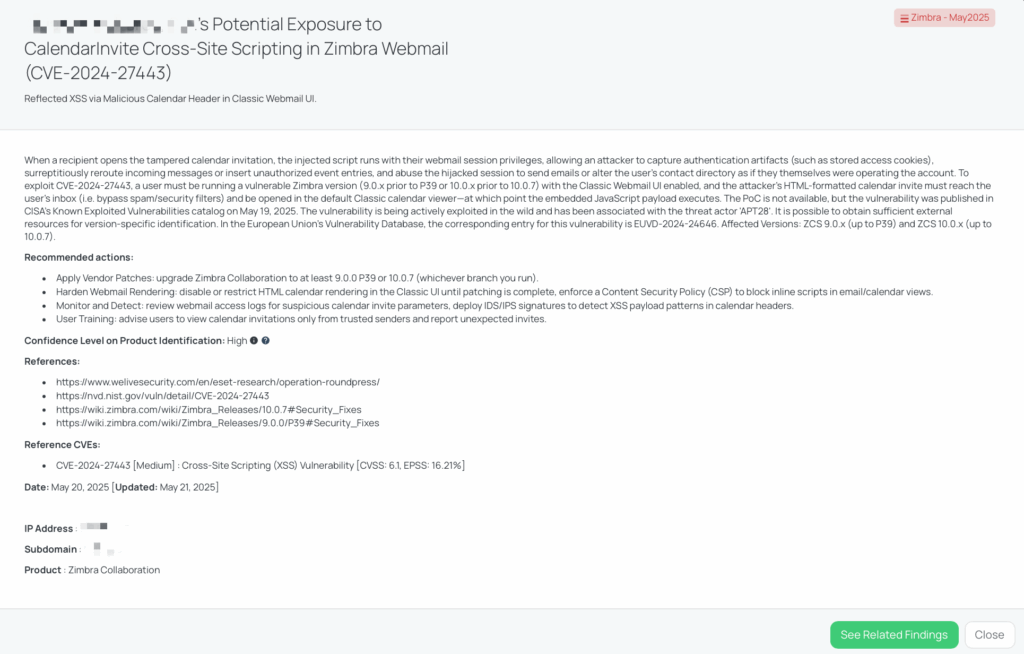
CVE-2024-12987 – DrayTek Vigor OS Command Injection Vulnerability
What is CVE-2024-12987 in DrayTek Vigor Devices?
CVE-2024-12987 is a critical OS command injection vulnerability affecting DrayTek Vigor2960, Vigor300B, and Vigor3900 routers running firmware version 1.5.1.4 or earlier. The flaw resides in the Web Management Interface’s /cgi-bin/mainfunction.cgi/apmcfgupload endpoint, where improper sanitization of the session parameter allows remote attackers to inject and execute arbitrary shell commands.
An attacker can exploit this vulnerability by sending a specially crafted HTTP/1.0 request with a hex-encoded payload to the vulnerable endpoint, resulting in command execution with elevated privileges. A public proof-of-concept (PoC) script demonstrates this exploitation method.
The vulnerability has a CVSS v3.1 score of 9.8 (Critical) and an EPSS score of 56.05%. It was added to CISA’s Known Exploited Vulnerabilities catalog on May 16, 2025, indicating active exploitation in the wild. Notably, the Rust-based botnet “RustoBot” leverages this vulnerability to compromise DrayTek gateways, recruiting them into distributed denial-of-service (DDoS) campaigns across regions including Japan, Taiwan, Vietnam, and Mexico.
Why Should TPRM Professionals Be Concerned About CVE-2024-12987?
DrayTek Vigor devices are commonly used as network gateways in enterprise environments. A compromise of these devices can lead to unauthorized access to internal networks, data exfiltration, and service disruptions. The exploitation of CVE-2024-12987 allows attackers to execute arbitrary commands, potentially leading to full device compromise and lateral movement within the network. Given the active exploitation by botnets like RustoBot, the risk extends to participation in large-scale DDoS attacks, amplifying the potential impact on both the compromised organization and external targets.
What Questions Should TPRM Professionals Ask Vendors Regarding CVE-2024-12987?
- Have you updated all instances of DrayTek Vigor2960, Vigor300B, and Vigor3900 devices to firmware version 1.5.1.5 or later to mitigate the risk of CVE-2024-12987? If your devices were on version 1.0.5 or earlier, did you first upgrade to 1.0.7.1 before applying 1.5.1.5?
- Have you implemented a Web Application Firewall (WAF) or Access Control Lists (ACLs) to filter unexpected parameters and disable unused CGI endpoints, specifically the /cgi-bin/mainfunction.cgi/apmcfgupload endpoint, to prevent the OS command injection vulnerability?
- Have you deployed IDS/IPS signatures for CVE-2024-12987 and are you actively monitoring for inbound requests to /cgi-bin/mainfunction.cgi/apmcfgupload and anomalous User-Agent strings or unexpected HTTP/1.0 traffic patterns as part of your incident response strategy?
- Given that the RustoBot botnet is actively exploiting this vulnerability, have you reviewed your logs for signs of exploitation and prepared for rapid rollback or device restoration in case of a suspected compromise?
Remediation Recommendations for Vendors Affected by CVE-2024-12987
- Upgrade Firmware: Immediately update affected DrayTek devices to firmware version 1.5.1.5. For devices on version 1.0.5 or earlier, first upgrade to 1.0.7.1 before applying the latest firmware.
- Restrict Management Access: Limit access to the Web Management Interface to trusted administrative networks; block direct internet exposure.
- Network Segmentation: Isolate device management VLANs and implement firewall rules to prevent lateral movement.
- Monitor & Detect: Scan for inbound requests to /cgi-bin/mainfunction.cgi/apmcfgupload and anomalous User-Agent strings or unexpected HTTP/1.0 traffic patterns.
- Harden Configuration: Employ a Web Application Firewall (WAF) or Access Control Lists (ACLs) to filter unexpected parameters and disable unused CGI endpoints.
- Incident Response: Review logs for signs of exploitation, deploy intrusion detection/prevention systems (IDS/IPS) signatures for CVE-2024-12987, and plan for rapid rollback or device restoration if compromise is suspected.
How Can TPRM Professionals Leverage Black Kite for CVE-2024-12987?
Black Kite has issued the “DrayTek Vigor – May2025” FocusTag, providing high-confidence intelligence on vendors potentially exposed to CVE-2024-12987. This tag includes detailed information such as affected assets, IP addresses, and subdomains associated with vulnerable DrayTek deployments. By utilizing this FocusTag, TPRM professionals can:
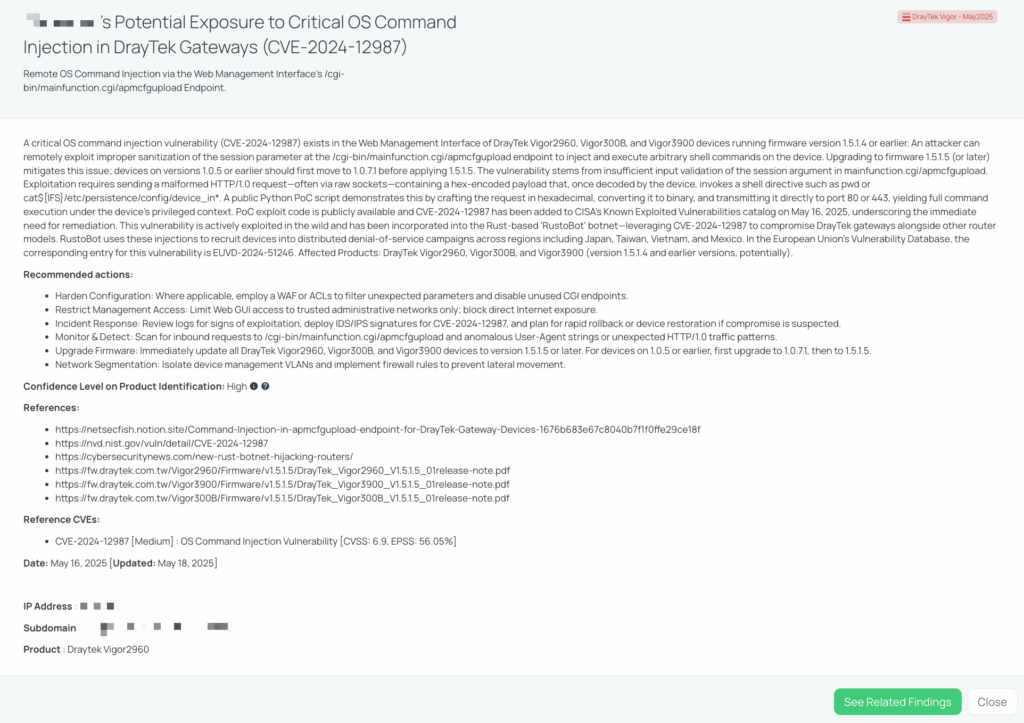
CVE-2025-22157 – Atlassian Jira Data Center Privilege Escalation
What is the Jira Data Center Privilege Escalation Vulnerability (CVE-2025-22157)?
CVE-2025-22157 is a high-severity privilege escalation vulnerability affecting Atlassian Jira Core and Jira Service Management Data Center and Server editions. This flaw allows authenticated users with low-level permissions to perform actions under higher-privileged accounts by exploiting improper permission checks in Jira’s REST API and backend handlers. The vulnerability was introduced in versions 9.12.0, 10.3.0, 10.4.0, and 10.5.0 of Jira Core, and versions 5.12.0, 10.3.0, 10.4.0, and 10.5.0 of Jira Service Management.
With a CVSS score of 7.2 and an EPSS score of 0.05%, this vulnerability poses a significant risk, allowing attackers to compromise administrative functions, alter project configurations, and disrupt service-desk operations. As of now, there is no public PoC exploit code, and the vulnerability has not been added to CISA’s Known Exploited Vulnerabilities catalog.
Why Should TPRM Professionals Be Concerned About CVE-2025-22157?
Jira Data Center is widely used for project management, issue tracking, and service management across various industries. A privilege escalation vulnerability in such a critical system can lead to unauthorized access to sensitive data, disruption of workflows, and potential compliance violations. Third-party vendors using vulnerable versions of Jira may inadvertently expose your organization to these risks.
What Questions Should TPRM Professionals Ask Vendors Regarding CVE-2025-22157?
- Can you confirm if you have upgraded all instances of Jira Core Data Center & Server and Jira Service Management Data Center & Server to the recommended versions (9.12-series → ≥ 9.12.20; 10.3-series → ≥ 10.3.5; 10.4-series → ≥ 10.6.0; 10.5-series → ≥ 10.5.1) to mitigate the risk of CVE-2025-22157?
- Have you implemented stricter privilege boundaries and temporary restrictions on low-privilege accounts until patches are applied as recommended in the advisory for CVE-2025-22157?
- Have you enabled logging and alerts for privilege-sensitive API endpoints and administrative actions to monitor potential exploitation of the privilege escalation vulnerability (CVE-2025-22157) in Jira Core and Service Management?
- Have you conducted an audit of existing project-level and read-only roles for unusual API activity as part of your response to the CVE-2025-22157 vulnerability?
Remediation Recommendations for Vendors Affected by CVE-2025-22157
- Upgrade Jira Immediately: Apply the latest patches provided by Atlassian to address CVE-2025-22157.
- Review Permissions: Conduct a thorough audit of user roles and permissions to ensure proper access controls are in place.
- Harden Access Controls: Implement stricter privilege boundaries and consider temporary restrictions on low-privilege accounts until patches are applied.
- Monitor & Alert: Enable logging and alerts for privilege-sensitive API endpoints and administrative actions to detect any suspicious activities.
How Can TPRM Professionals Leverage Black Kite for CVE-2025-22157?
Black Kite published the FocusTag for CVE-2025-22157 on May 22, 2025. This tag enables TPRM professionals to identify third-party vendors that may be affected by this vulnerability. By providing asset information such as IP addresses and subdomains, Black Kite allows for a more precise assessment of potential risks within your supply chain. Utilizing this information, you can prioritize remediation efforts, engage in informed discussions with vendors, and enhance your organization’s overall cybersecurity posture.
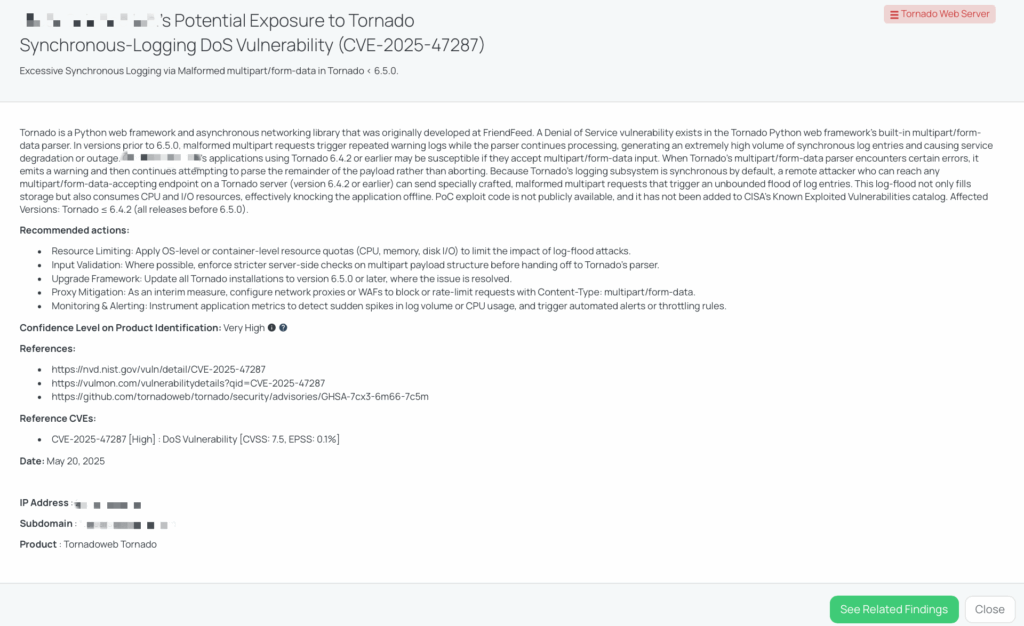
CVE-2025-47287 – Tornado Web Server DoS Vulnerability
What is the Tornado multipart/form-data Denial-of-Service vulnerability (CVE-2025-47287)?
CVE-2025-47287 is a high-severity Denial-of-Service (DoS) vulnerability affecting Tornado, a Python-based asynchronous web framework and networking library. The vulnerability arises from the way Tornado’s built-in multipart/form-data parser handles malformed inputs. In affected versions (all releases prior to 6.5.0), if the parser encounters certain structural issues in multipart requests, it logs a warning message but continues attempting to parse the rest of the request.
Because Tornado’s logging system operates synchronously by default, an attacker can remotely send a malformed multipart request to any vulnerable endpoint. This causes the application to generate a large volume of log entries, rapidly consuming disk space, CPU, and I/O resources. The attack does not require authentication or complex exploitation, and the affected parser is enabled by default.
This vulnerability carries a CVSS score of 7.5 (High) and an EPSS score of 0.10%. It was publicly disclosed on May 15, 2025, through GitHub’s security advisory system. There is no evidence of exploitation in the wild, and the issue has not been added to CISA’s Known Exploited Vulnerabilities catalog. Likewise, CISA has not issued an advisory regarding this vulnerability at this time.
Why Should TPRM Professionals Be Concerned About CVE-2025-47287?
While the vulnerability does not provide direct access to sensitive data or remote code execution capabilities, it poses a significant threat to service availability, which can have downstream effects on any integrated or dependent systems. Organizations using Tornado in public-facing APIs or web applications may experience partial or complete outages if targeted with malformed multipart/form-data payloads.
From a third-party risk management (TPRM) perspective, vendors who use Tornado in production environments without proper traffic filtering or resource limits may unknowingly expose critical services to denial-of-service scenarios. If such services are part of an enterprise’s supply chain—such as SaaS products or integration providers—disruptions may cascade into the organization’s own operations, undermining continuity and performance expectations.
Remediation Recommendations for Vendors Affected by CVE-2025-47287
Vendors who maintain Tornado-based systems should take the following technical steps to mitigate risk:
- Upgrade Framework: Update Tornado to version 6.5.0 or later, where the issue has been resolved.
- Proxy Mitigation: As a temporary measure, configure reverse proxies or Web Application Firewalls (WAFs) to block or rate-limit requests with Content-Type: multipart/form-data.
- Input Validation: Implement strict server-side validation of multipart payload structures before they are processed by Tornado’s parser.
- Resource Limiting: Enforce OS- or container-level resource quotas (e.g., for CPU, memory, and disk I/O) to prevent single services from exhausting shared system resources.
- Monitoring and Alerting: Set up logging and metric-based alerting to detect rapid increases in log volume or application latency.
How Can TPRM Professionals Leverage Black Kite for CVE-2025-47287?
Black Kite published the Tornado Web Server FocusTag on May 20, 2025, in response to the disclosure of CVE-2025-47287. This tag enables TPRM professionals to identify vendors potentially running vulnerable versions of Tornado, especially those with public-facing services that may accept multipart/form-data inputs.
The FocusTag offers very high confidence in product identification and includes granular intelligence such as subdomain and IP address visibility, helping organizations zero in on real exposure rather than issuing broad-based surveys. Operationalizing this tag allows risk teams to prioritize follow-ups with only the vendors that are relevant to this incident, saving time and reducing unnecessary noise in communication workflows.
The tag is set to expire on August 31, 2025, unless new developments warrant an update. Black Kite’s ability to tie internet-facing telemetry to software versioning ensures that customers receive actionable third-party insights rather than generic alerts.
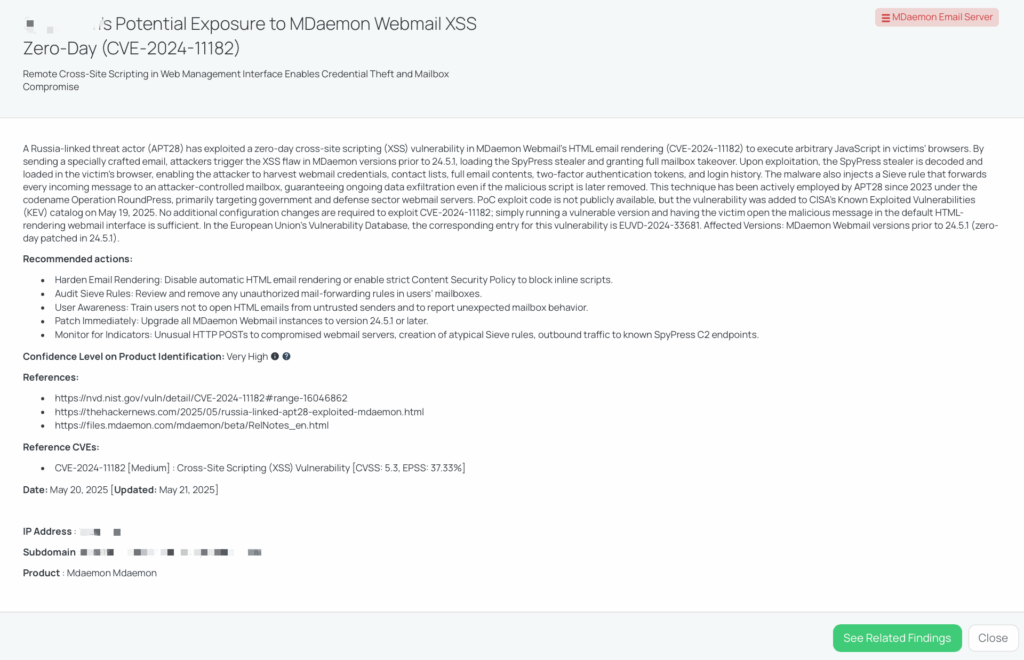
CVE-2024-11182 – MDaemon Email Server XSS Vulnerability
What is the MDaemon Webmail XSS Vulnerability (CVE-2024-11182)?
CVE-2024-11182 is a medium-severity cross-site scripting (XSS) vulnerability affecting MDaemon Email Server versions prior to 24.5.1. The flaw resides in the webmail interface’s HTML email rendering component, where improper sanitization allows attackers to inject malicious JavaScript code via specially crafted emails. This vulnerability enables remote attackers to execute arbitrary scripts in the context of the user’s browser session, potentially leading to credential theft and unauthorized access to sensitive information.
The vulnerability has a CVSS score of 6.1 and an EPSS score of 37.33%. It was actively exploited as a zero-day by the Russia-linked threat actor APT28 (also known as Fancy Bear or Sednit) in a campaign dubbed “Operation RoundPress,” targeting government and defense sector webmail servers. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added CVE-2024-11182 to its Known Exploited Vulnerabilities (KEV) catalog on May 19, 2025, highlighting its active exploitation in the wild.
Why Should TPRM Professionals Be Concerned About CVE-2024-11182?
MDaemon Email Server is widely used by organizations for email communication. Exploitation of CVE-2024-11182 can lead to unauthorized access to email accounts, exposure of sensitive communications, and potential lateral movement within an organization’s network. For third-party risk management (TPRM) professionals, this vulnerability poses significant concerns:
- Data Exfiltration: Attackers can harvest credentials, contact lists, and email contents, leading to potential data breaches.
- Persistent Access: The use of malicious Sieve rules allows attackers to maintain access even after initial compromise.
- Supply Chain Risks: Vendors using vulnerable MDaemon versions may become entry points for attackers into larger networks.
What Questions Should TPRM Professionals Ask Vendors Regarding CVE-2024-11182?
To assess the risk associated with this vulnerability, TPRM professionals should inquire:
- Have you updated all instances of MDaemon Webmail to version 24.5.1 or later to mitigate the risk of CVE-2024-11182?
- Can you confirm if you have implemented a strict Content Security Policy to block inline scripts and disabled automatic HTML email rendering as recommended in the advisory?
- Have you audited Sieve rules to identify and remove any unauthorized mail-forwarding rules in users’ mailboxes that could be a result of the SpyPress stealer?
- Are you monitoring for indicators such as unusual HTTP POSTs to compromised webmail servers, creation of atypical Sieve rules, and outbound traffic to known SpyPress C2 endpoints to detect any potential exploitation of CVE-2024-11182?
Remediation Recommendations for Vendors Affected by CVE-2024-11182
Vendors utilizing MDaemon Email Server should take the following actions:
- Immediate Patching: Upgrade to MDaemon version 24.5.1 or later to address the vulnerability.
- Disable HTML Rendering: Configure webmail clients to disable automatic HTML email rendering or enforce strict Content Security Policies (CSP) to mitigate XSS risks.
- Audit and Monitor: Regularly review mail forwarding rules and monitor for unusual activities, such as unexpected HTTP POST requests to known malicious domains.
- User Training: Educate users about the risks of opening emails from unknown sources and encourage reporting of suspicious activities.
How Can TPRM Professionals Leverage Black Kite for CVE-2024-11182?
Black Kite provides visibility into third-party vulnerabilities, including CVE-2024-11182. By utilizing Black Kite’s platform, TPRM professionals can:
- Identify Exposure: Determine which vendors are running vulnerable versions of MDaemon Email Server.
- Assess Risk: Evaluate the potential impact of the vulnerability on the organization’s supply chain.
- Monitor Remediation: Track vendors’ progress in addressing the vulnerability and ensure timely patching.
Strengthening TPRM with Black Kite’s FocusTags™
When high-impact vulnerabilities like those found in Zimbra, DrayTek Vigor, Atlassian Jira Data Center, Tornado, and MDaemon emerge, time is of the essence. Black Kite’s FocusTags™ offer organizations a strategic advantage by transforming complex threat data into actionable intelligence—enabling faster, more focused responses to third-party exposure.
Here’s how FocusTags™ enhance your TPRM program:
- Vendor-Specific Vulnerability Detection: Black Kite pinpoints which of your vendors are at risk based on real-world data, including IPs and subdomains associated with vulnerable assets.
- Prioritized Risk Management: FocusTags™ help organizations allocate resources where it matters most—toward vendors affected by the most critical or actively exploited vulnerabilities.
- Informed Vendor Dialogue: Instead of generic outreach, you can ask precise, vulnerability-specific questions to assess a vendor’s mitigation strategy and security posture.
- Streamlined Incident Response: With enriched threat context and timely updates, FocusTags™ empower your TPRM team to act decisively when new vulnerabilities arise.
By operationalizing Black Kite’s FocusTags™, TPRM professionals can cut through the noise and quickly narrow their focus to the vendors that truly require attention—enhancing resilience in an ever-evolving threat landscape.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
About Focus Friday
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FocusTagsTM in the Last 30 Days:
- Zimbra – May2025 : CVE-2024-27443, Cross-Site Scripting (XSS) Vulnerability in Zimbra Collaboration (ZCS).
- DrayTek Vigor – May2025 : CVE-2024-12987, OS Command Injection Vulnerability in DrayTek Vigor Routers.
- Atlassian Jira Data Center : CVE-2025-22157, Privilege Escalation Vulnerability in Jira Core Data Center, Jira Core Server, Jira Service Management Data Center, Jira Service Management Server.
- Tornado Web Server : CVE-2025-47287, DoS Vulnerability in Tornado Web Server.
- MDaemon Email Server : CVE-2024-11182, Cross-Site Scripting (XSS) Vulnerability in MDaemon Email Server.
- Ivanti EPMM – May2025 : CVE-2025-4427, CVE-2025-4428, Authentication Bypass and Remote Code Execution Vulnerability in Ivanti Endpoint Manager Mobile (EPMM)
- SysAid On-Premises : CVE-2025-2775, CVE-2025-2776, CVE-2025-2777, XML External Entity (XXE) Injection Vulnerability in SysAid On-Premises.
- Apache ActiveMQ – May2025 : CVE-2025-27533, Memory Allocation with Excessive Size Value in Apache ActiveMQ.
- Webmin: CVE-2025-2774, CRLF Injection Privilege Escalation Vulnerability in Webmin.
- Couchbase Server: CVE-2025-46619, LFI Vulnerability in Couchbase Server.
- SAP NetWeaver VCFRAMEWORK : CVE-2025-31324, Remote Code Execution Vulnerability in SAP NetWeaver Visual Composer’s Metadata Uploader component.
- Apache Tomcat – Apr2025 : CVE-2025-31650, CVE-2025-31651, DoS Vulnerability, Rewrite Rule Bypass Vulnerability in Apache Tomcat.
- Fortinet Symlink Backdoor : CVE-2022-42475, CVE-2024-21762, CVE-2023-27997, Arbitrary Code Execution Vulnerability, Numeric Truncation Error, Heap-based Buffer Overflow Vulnerability, Out-of-bounds Write Vulnerability in FortiGate devices.
- SonicWall SSLVPN Gen7 : CVE-2025-32818, Null Pointer Dereference Vulnerability, DoS Vulnerability in SonicWall SSLVPN Gen 7 devices.
- Redis Server : CVE-2025-21605, Allocation of Resources Without Limits or Throttling in Redis Servers.
- Adobe ColdFusion : CVE-2025-24446 CVE-2025-24447 CVE-2025-30281 CVE-2025-30282 CVE-2025-30284 CVE-2025-30285 CVE-2025-30286 CVE-2025-30287 CVE-2025-30288 CVE-2025-30289 CVE-2025-30290, Deserialization of Untrusted Data, Improper Authentication, Improper Access Control, OS Command Injection, Improper Input Validation, Path Traversal Vulnerabilities in Adobe ColdFusion.
- Beego: CVE-2025-30223, Reflected/Stored XSS Vulnerabilities in Beego Web Framework.
- Ivanti Connect Secure : CVE‑2025‑22457, Stack‑based Buffer Overflow Vulnerability in Ivanti Connect Secure, Ivanti Policy Secure, and Ivanti ZTA Gateways.
- FortiSwitch : CVE‑2024‑48887, Unverified Password Change Vulnerability in Fortinet FortiSwitch web interface.
- MinIO : CVE‑2025‑31489, Improper Verification of Cryptographic Signature Vulnerability in MinIO Go module package.
- Kubernetes Ingress NGINX : CVE-2025-1097, CVE-2025-1098, CVE-2025-24514, CVE-2025-1974, Improper Isolation or Compartmentalization Vulnerability, Remote Code Execution Vulnerability in Kubernetes ingress-nginx controller.
- Synology DSM : CVE-2024-10441, Remote Code Execution Vulnerability in Synology BeeStation OS (BSM), Synology DiskStation Manager (DSM).
- Synapse Server : CVE-2025-30355, Improper Input Validation Vulnerability in Matrix Synapse Server.
- Juniper Junos OS – Mar2025 : CVE-2025-21590, Improper Isolation or Compartmentalization Vulnerability in Juniper Junos OS.
References
- https://nvd.nist.gov/vuln/detail/CVE-2024-27443
- https://wiki.zimbra.com/wiki/Zimbra_Releases/10.0.7#Security_Fixes
- https://wiki.zimbra.com/wiki/Zimbra_Releases/9.0.0/P39#Security_Fixes
- https://nvd.nist.gov/vuln/detail/CVE-2024-12987
- https://fw.draytek.com.tw/Vigor2960/Firmware/v1.5.1.5/DrayTek_Vigor2960_V1.5.1.5_01release-note.pdf
- https://fw.draytek.com.tw/Vigor3900/Firmware/v1.5.1.5/DrayTek_Vigor3900_V1.5.1.5_01release-note.pdf
- https://fw.draytek.com.tw/Vigor300B/Firmware/v1.5.1.5/DrayTek_Vigor300B_V1.5.1.5_01release-note.pdf
- https://netsecfish.notion.site/Command-Injection-in-apmcfgupload-endpoint-for-DrayTek-Gateway-Devices-1676b683e67c8040b7f1f0ffe29ce18f
- https://cybersecuritynews.com/new-rust-botnet-hijacking-routers/
- https://nvd.nist.gov/vuln/detail/CVE-2025-22157
- https://jira.atlassian.com/browse/JRASERVER-78766
- https://github.com/tornadoweb/tornado/security/advisories/GHSA-7cx3-6m66-7c5m
- https://vulmon.com/vulnerabilitydetails?qid=CVE-2025-47287
- https://nvd.nist.gov/vuln/detail/CVE-2025-47287
- https://nvd.nist.gov/vuln/detail/CVE-2024-11182#range-16046862
- https://files.mdaemon.com/mdaemon/beta/RelNotes_en.html
- https://thehackernews.com/2025/05/russia-linked-apt28-exploited-mdaemon.html

