Ransomware Review February 2025: Clop’s CLEO Attack Pushes Victim Count to Historic High
Written by: Ekrem Selçuk Çelik
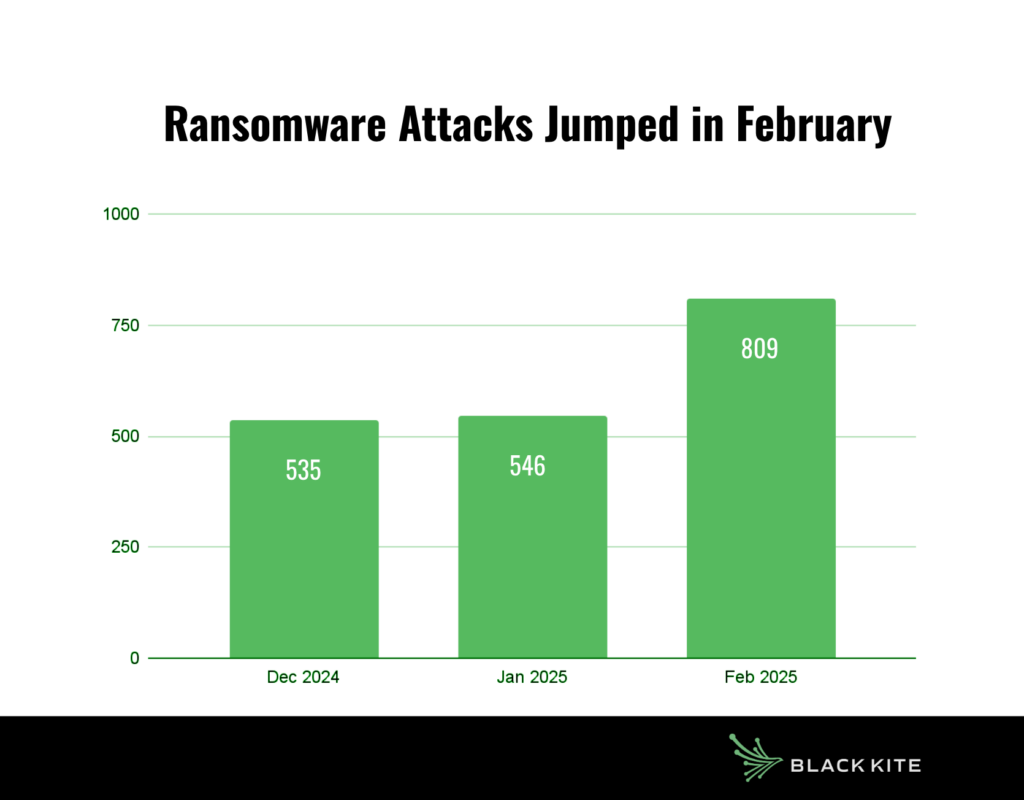
Welcome to the February 2025 ransomware update, highlighting the latest trends, threat actors, and significant events in the ransomware ecosystem to keep CISOs and third-party risk managers informed and prepared.The Black Kite Research & Intelligence Team (BRITE) tracked 809 ransomware incidents in February 2025, marking the highest monthly victim count ever recorded. Previously, the peak stood at around 590 victims, making this month’s figure especially alarming.
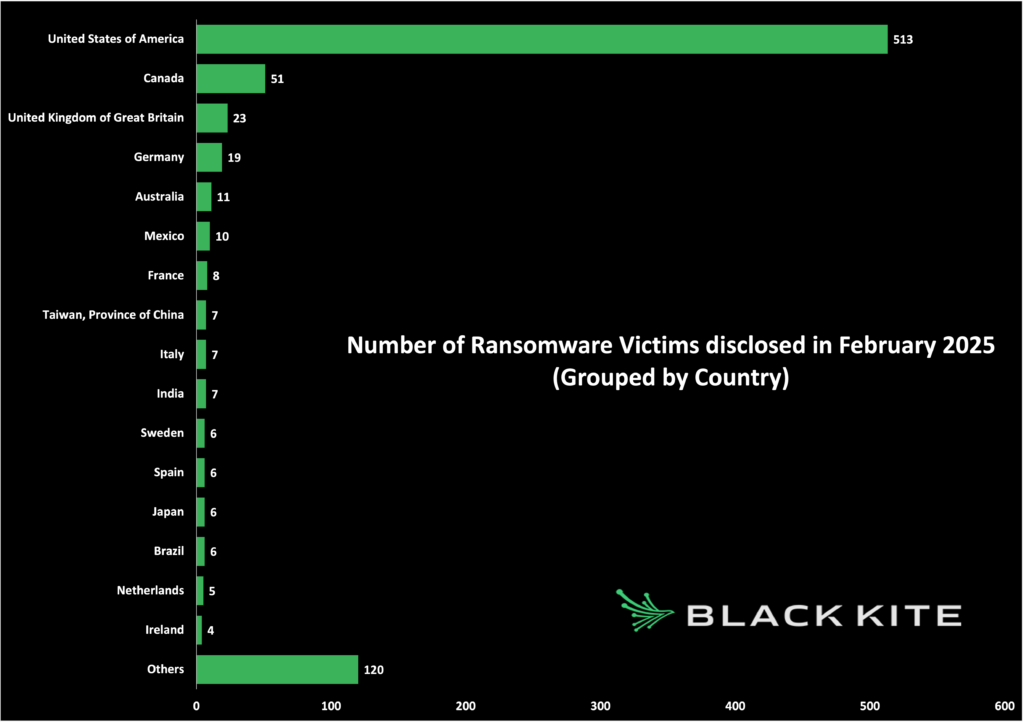
The United States once again topped the list with 513 incidents, followed by Canada with 51 and the United Kingdom with 23.
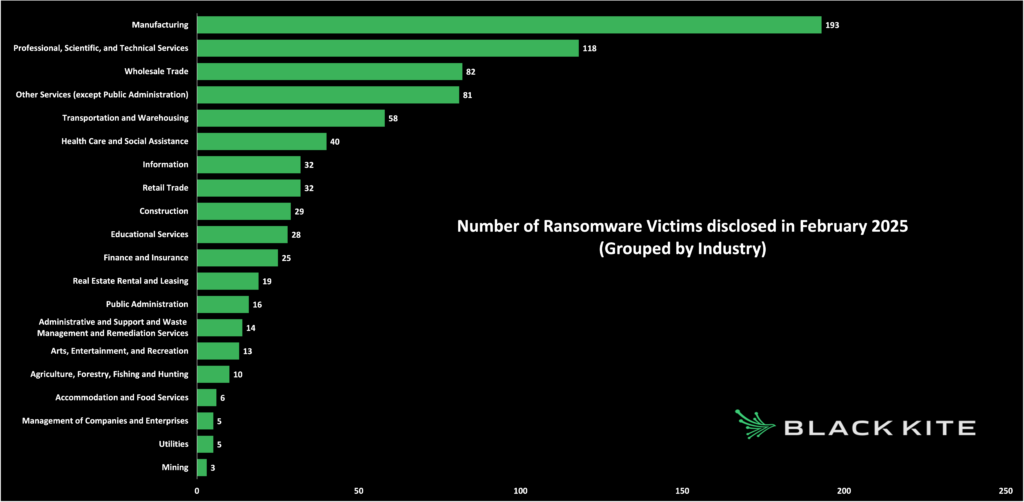
Manufacturing remained the hardest-hit sector with 193 victims, followed by Professional and Technical Services with 118, and Wholesale with 82. The gap between Manufacturing and Technical Services continues to widen as attacks intensify.
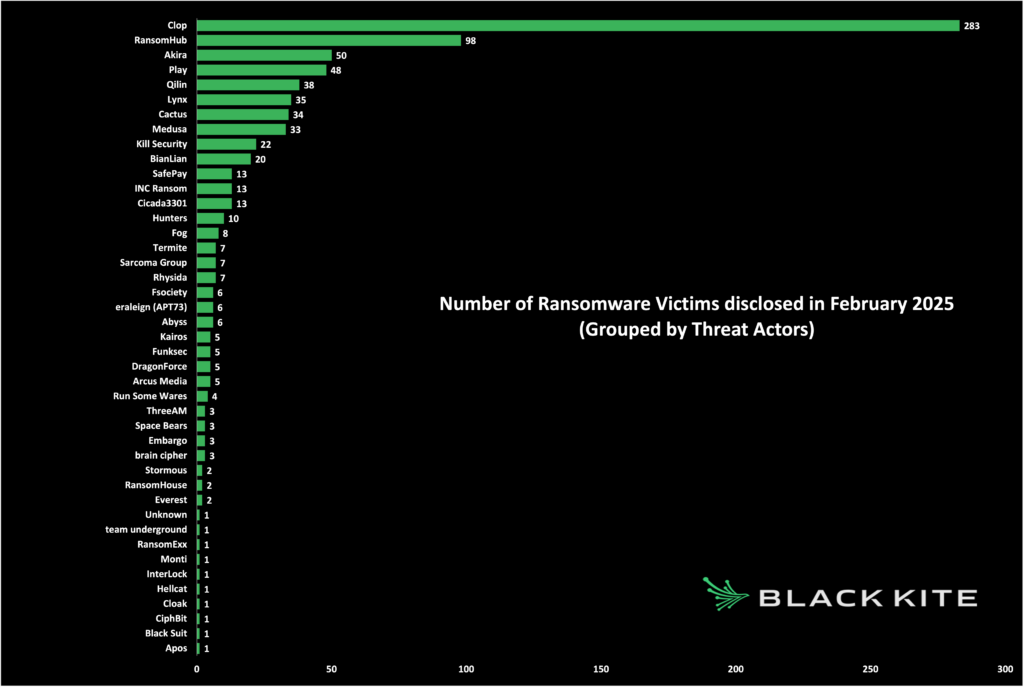
Top Threat Actors
Clop dominated February with 283 disclosed victims, retaining its leadership for the second consecutive month. RansomHub maintained its consistent presence, following with 98 victims. The Akira group kept up its recent momentum, placing third with 50 victims, closely followed by Play with 48 victims. Additionally, Qilin, Lynx, Cactus, and Medusa collectively disclosed numerous victims, contributing significantly to the month’s total.
If we’re not going to take 809 victims seriously, when will we start?
The unprecedented surge of ransomware attacks in February demands attention. Throughout 2024, we occasionally reached numbers around 500 and had grown somewhat accustomed to them. But surpassing the previous all-time high of around 590, this surge significantly, especially at the beginning of 2025, highlights the disturbing trajectory of ransomware attacks and underscores the need for critical insights into the evolving ransomware landscape.
Clop Played All Its Cards
Clop started February by gradually revealing victims, initially disclosing 50, followed shortly by another batch of 50. Just when it seemed they would continue this incremental approach, the group unexpectedly released over 180 remaining victims in a single batch, suggesting they’ve now exhausted their CLEO-related victim pool.
Since the CLEO vulnerability emerged, Clop has publicly disclosed over 400 victims, confirming earlier predictions of potentially reaching around 450. In February alone, the United States (185 victims) and Canada (24 victims) were the primary targets. Manufacturing was again the hardest-hit sector with 89 victims, followed by Wholesale with 49 and Transportation and Warehousing with 35.
Yet, despite these substantial victim numbers, Clop doesn’t seem to be achieving the impact it desires. Increasingly strict ransom payment policies by companies and governments have meant organizations often prefer to absorb short-term reputational damage rather than financial loss. Clearly, media attention around Clop’s CLEO attacks is significantly lower than their previous MoveIT campaign, visibly affecting the group’s morale and possibly frustrating their ambitions.
Whether Clop will innovate its methods or shift entirely to new attack strategies remains uncertain. Still, one thing remains clear: Clop excels at ransomware operations, and its future moves will undoubtedly remain closely watched.
8Base Shutdown
The 8Base ransomware group, which had been showing sporadic activity following the arrest of Russian citizen Evgenii Ptitsyn last year, attempted a comeback in January with 25 victims. However, a significant international law enforcement operation in early February shut down 8Base’s leak site completely, resulting in the arrest of four European suspects (two women and two men) in Phuket, Thailand.
The dismantling of such a major ransomware operation, which had evolved from Phobos into a sophisticated and professionally managed group, underscores the effectiveness of global collaboration against cybercrime. This event offers a hopeful reminder of what coordinated efforts can achieve against ransomware threats.

Black Basta’s Internal Chaos Exposed
Another notable event in February was the leak of roughly 50MB of internal chat logs from the Black Basta ransomware group, revealing insights into their operations, target selection strategies, internal vulnerabilities, and organizational dysfunction. The leaked messages include numerous RDP, VPN, and proxy credentials, along with internal debates highlighting serious trust and coordination issues within the group.
Critically, the leak exposed discussions about technical shortcomings compared to rival ransomware groups, internal conflicts, and the presence of former Conti members seeking to improve operational strategies. Such leaks provide valuable insights for defenders and underscore how ransomware groups are vulnerable to internal collapse.
The Road Ahead
February’s unprecedented ransomware activity is a clear indicator of where the ecosystem is heading. The aggressive exploitation of the CLEO vulnerability by Clop, the emergence of new ransomware groups, and a surge in activity across the board have set a troubling precedent. Unless organizations and governments adopt radical security measures soon, it’s unrealistic to expect any slowdown in ransomware attacks in the foreseeable future.
Although law enforcement operations, such as the takedown of 8Base, offer some hope, the continuous emergence and rebranding of ransomware groups emphasize that defense measures must continually evolve. Collaboration, resilience, and proactive defense have never been more critical.
To keep an eye on potential ransomware targets in your cyber ecosystem, check out Black Kite’s Ransomware Susceptibility Index® (RSITM). It allows third-party risk managers to identify high-risk vendors before an attack strikes, prioritize remediation efforts, and ultimately safeguard your organization against the escalating threat.
Stay tuned for more monthly Ransomware Reviews on our blog and LinkedIn Newsletter.
Dig into our full 2025 Third Party Breach Report: The Silent Breach: How Third Parties Became the Biggest Cyber Threat in 2024 – accessible instantly, no download required.

