Top 3 Actions to Take After Reading the 2025 Third-Party Breach Report
Byline: Bob Maley, Chief Security Officer
If you’ve been in the information security field as long as I have, you’re probably feeling a sense of déjà vu after reading the 2025 Third-Party Breach Report when it comes to the prevalence of ransomware in third-party breaches. Ransomware has been around for decades. It first showed up on 5.25” floppy disks that someone handed out at a healthcare conference. The ransomware fee was just $200 back then, a far cry from the record-breaking $75 million ransom that was reported in 2024. You’d think we wouldn’t be dealing with this kind of threat after all this time.
The most frustrating part? Ransomware is preventable. If organizations had stopped it—and they could have—the bad guys would have moved onto something new. But over my years spent in law enforcement and cyber security, I’ve learned that bad actors will go where the money is. Organizations haven’t made enough progress in stopping ransomware attacks, so bad actors have no reason to stop using this tried-and-true form of attack.
If anything, they’re getting better at it. Google just issued a report claiming that threat actors are using Gemini to launch even more effective ransomware attacks. Generative AI comes in handy for them doing vulnerability research, scripting and development, and crafting phishing campaigns, among other things. If organizations don’t up their game, particularly when it comes to third-party risk management (TPRM), the situation is only going to get worse.
The findings in our 2025 Third-Party Breach Report make this clear. But rather than just ringing another alarm bell, I will share three concrete steps you can take now to protect yourself from hidden vendor threats, such as ransomware. Because although criminals are becoming more sophisticated, the fundamentals of prevention haven’t changed—CISOs just need to get better at executing on them.
3 Steps to Help Protect from Hidden Vendor Threats
1. Think Like a Bad Actor—And Use Technology to Step Up Your Game
When I was in law enforcement working the midnight shift, one of our regular tasks was to drive around closed businesses looking for unlocked doors and windows. We were thinking like criminals, looking for exactly the same kinds of opportunities they might use to find a way in. Today’s CISOs need to apply this same mindset to their broader vendor ecosystem, but at a much larger scale.
Take the Colonial Pipeline ransomware attack as an example. Their breach didn’t happen because of one wide-open vulnerability. It came from a combination of small failures that, when properly exploited, created the perfect opportunity for bad actors to wreak havoc. In this case, they had remote access ports open to the public due to a legitimate business need, but they didn’t have multi-factor authentication protecting this access. The attackers were able to use leaked network credentials to get in. And once they did, they were able to move laterally throughout the network.
Most people don’t realize that the Colonial Pipeline attack didn’t actually shut down the gas pipeline. It hit their billing system. But since the bad actors could have gained access to the company’s operational systems, Colonial Pipeline proactively shut everything down. A $5 million ransom and major East Coast fuel disruptions all started because of a few small gaps in their security.
Of course, figuring out which third-party vendors could be putting your company at risk of an attack like this could be like finding a needle in a haystack using traditional methods. This is why we developed our Ransomware Susceptibility Index® (RSITM). It analyzes billions of data points the way an attacker would, helping you figure out which vendors represent your weakest link before an attack happens.
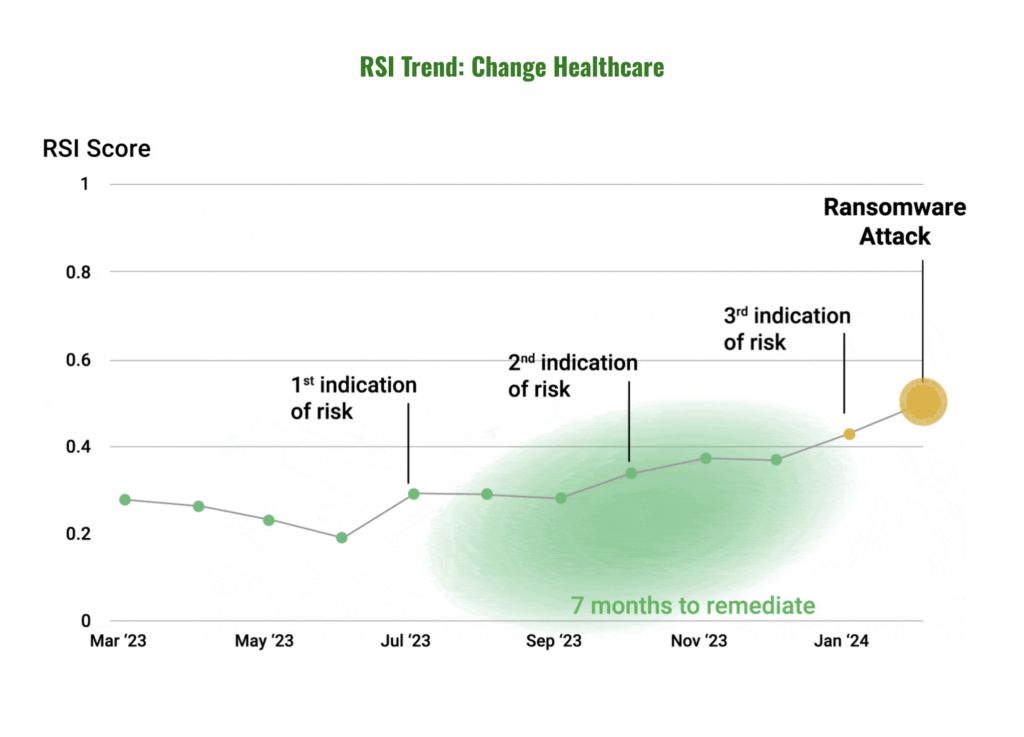
Take the Change Healthcare ransomware attack, which disrupted healthcare operations nationwide in 2024. Our RSI solution identified the vulnerabilities involved seven months before the attack occurred. Healthcare organizations with access to this early warning had the opportunity to address these vulnerabilities before they could be exploited, potentially preventing millions in damages and widespread service disruptions.
2. Stop Trusting Questionnaires and Start Verifying Everything
I’ve seen plenty of vendor security questionnaires over the years. In fairness, they were designed with an admirable goal in mind—helping CISOs identify and address potential risks in their third-party ecosystems. The problem is that they’re not nearly agile enough to handle today’s threats.
A typical questionnaire might have well-meaning questions like, “Do you have multi-factor authentication in place?” or “Are your remote access protocols secure?” The problem is that the answers vendors give are often aspirational at best. A vendor might really believe they’re following security best practices, but if you can’t verify their responses, you’re building your risk management program on trust alone.
Here, too, thinking like a criminal will serve you well. Are threat actors sending long questionnaires to their targets asking them about their security measures? Obviously not. They don’t need to. They’re using automated tools and AI capabilities to probe for vulnerabilities they can exploit. Unfortunately, the security field hasn’t caught up with the bad guys yet.
So, just like your would-be attackers do, take advantage of current technology instead of relying on lengthy assessments that take weeks or months to complete and likely won’t give you an accurate view of the threats you face. When a vendor claims that they’re using MFA to protect their remote access ports, wouldn’t you rather verify that claim right away instead of taking it at face value a few weeks or months from now?
An advanced TPRM solution can help you get this done in record time. At Black Kite, our platform can pre-answer almost all standard security questionnaires by collecting actual evidence of a vendor’s controls and compliance measures. This way, instead of chasing paper trails, you can focus on addressing the gaps that matter most to your business.
3. Put a Dollar Value on Your Vendor Risks
Most security teams can show you a dashboard full of red, green, and yellow indicators that are supposed to highlight the most important risks. But what happens when everything is marked red? Let’s say you’ve discovered ten vendors in your environment that have serious security issues requiring your attention. One of them might cost your company $10 million in damages if a breach happens, while the others might run you $50,000 each. When you use this lens to decide which risks to deal with first, your decision about where to invest your limited resources becomes a lot easier.
This is why, at Black Kite, we’ve integrated the Open FAIR™ model into our platform. Open FAIR™ can fundamentally transform how you manage vendor risk. Many security professionals still conflate vulnerabilities or system outages with risk, but real risk is about impact—specifically, the financial impact to your business. If you can’t convert a security threat into dollars and cents, then you’re missing the bottom-line perspective that your board and executive team need to make the right call.
Determining the financial impact of your vendor risks isn’t just helpful for getting budget approval. It can also help you build a more innovative and more strategic security program over the long term. When you understand the actual financial stakes involved with each vendor relationship, you can make smarter decisions about everything from the security requirements you include in your vendor contracts to how much time your team spends on assessments and monitoring.
It’s Well Past Time to Answer the Wake-Up Call
As the 2025 Third-Party Breach Report makes clear, when it comes to ransomware and other major threats, the wake-up call has come and gone. As a community, CISOs haven’t yet answered it. On the other hand, there’s never been a better time to do so. We have proven processes and great tools to make the necessary changes and make them stick.
These three actions—thinking like a bad actor, moving beyond static questionnaires, and putting a dollar value on your risks—might seem straightforward. But they require a fundamental shift in how to think about TPRM. Organizations have to stop defaulting to familiar low-entropy approaches from years gone by that don’t address modern threats and start building the kind of agility adversaries have already employed for some time now.
For more insights on the current third-party cyber risk landscape, read our 2025 Third-Party Breach Report, The Silent Breach: How Third Parties Became the Biggest Cyber Threat in 2024. No downloads required.
Dig into our full 2025 Third Party Breach Report: The Silent Breach: How Third Parties Became the Biggest Cyber Threat in 2024 – accessible instantly, no download required.

