Focus Friday: Addressing Critical Vulnerabilities in SonicWall, Ivanti, Progress, and GoCD
Written by: Ferdi Gül
Welcome to this week’s Focus Friday blog, where we analyze high-profile vulnerabilities and incidents from a Third-Party Risk Management (TPRM) perspective. As organizations grapple with the growing complexities of cybersecurity threats, identifying and addressing vendor-related risks becomes paramount. This week, we had a busy week focusing on vulnerabilities. In this week’s article, we examined critical vulnerabilities in widely used products, including SonicWall SonicOS, Ivanti Connect Secure, Progress WhatsUp Gold, and GoCD. These vulnerabilities underscore the importance of swift action and strategic prioritization in TPRM processes. Read on to explore actionable insights and strategies to mitigate these risks.
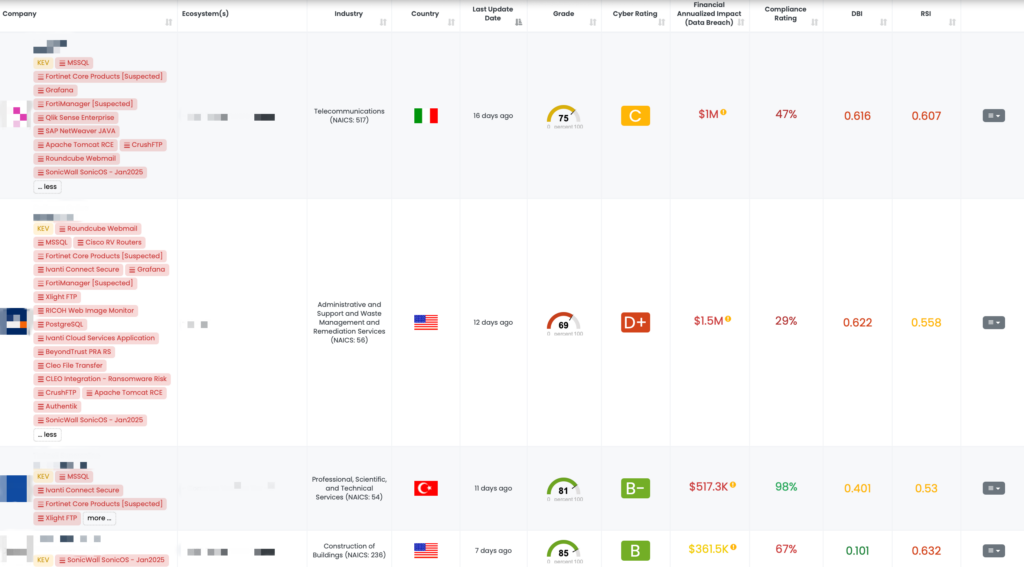
Critical Vulnerabilities in SonicWall SonicOS
What are the vulnerabilities affecting SonicWall SonicOS?
The SonicWall SonicOS platform has been found vulnerable to multiple issues that could severely impact network security. Below are the key vulnerabilities:
CVE-2024-40762: Use of Cryptographically Weak Pseudo-Random Number Generator (PRNG) vulnerability in the SSLVPN authentication token generator. This flaw allows attackers to predict authentication tokens, potentially leading to authentication bypass. (CVSS Score: 7.1)
CVE-2024-53704: Authentication Bypass vulnerability in the SSLVPN mechanism that could enable remote attackers to gain unauthorized system access. (CVSS Score: 8.2)
CVE-2024-53706: Local Privilege Escalation vulnerability in the Gen7 SonicOS Cloud platform NSv (AWS and Azure editions). This allows attackers to escalate privileges to root, potentially leading to arbitrary code execution. (CVSS Score: 7.8)
CVE-2024-53705: Server-Side Request Forgery (SSRF) vulnerability in the SSH management interface. Attackers could establish TCP connections to arbitrary IP addresses and ports, enabling further attacks. (CVSS Score: 6.5, EPSS Score: 0.04%)
These vulnerabilities were disclosed in SonicWall’s security advisory on January 7, 2025. While no active exploitation has been reported yet, similar vulnerabilities have been targeted by Chinese threat actors in the past, raising the likelihood of exploitation in future attack campaigns. As of now, these vulnerabilities are not listed in CISA’s KEV catalog.
Why should TPRM professionals care about these vulnerabilities?
The vulnerabilities in SonicWall SonicOS present significant risks for organizations that rely on these devices for network security:
- Authentication Bypass (CVE-2024-53704): Attackers gaining unauthorized access could compromise sensitive data, introduce malware, or disrupt critical services.
- Local Privilege Escalation (CVE-2024-53706): A successful attack could allow threat actors to execute arbitrary code, potentially leading to full control of the affected systems.
- SSRF (CVE-2024-53705): This could facilitate lateral movement or act as a pivot point for launching further attacks.
- PRNG Vulnerability (CVE-2024-40762): Weak token generation undermines the reliability of authentication mechanisms, posing a significant threat to systems reliant on SSLVPN.
These vulnerabilities directly affect SonicWall Gen6/6.5, Gen7, and TZ80 devices, often used by organizations as a critical part of their perimeter defense. Exploitation could result in compromised networks, data breaches, or service interruptions, which would affect operational and business continuity.
What questions should TPRM professionals ask vendors about these vulnerabilities?
- Have you updated all affected Gen6/6.5, Gen7, and TZ80 series devices to the recommended SonicOS versions (6.5.5.1-6n, 7.1.3-7015, 7.0.1-5165, and 8.0.0-8037 respectively) to mitigate the risk of CVE-2024-40762, CVE-2024-53704, CVE-2024-53705, and CVE-2024-53706?
- Can you confirm if you have implemented measures to limit SSLVPN and SSH management access to trusted sources or disabled access from the internet entirely to reduce exposure to the vulnerabilities CVE-2024-40762 and CVE-2024-53704?
- Have you enabled Multi-Factor Authentication (MFA) for all remote access to enhance security against the improper authentication issue in the SSLVPN mechanism (CVE-2024-53704)?
- How are you monitoring your system logs and network traffic to detect any unusual activity that may indicate attempted exploitation of the server-side request forgery (SSRF) flaw in the SSH management interface (CVE-2024-53705) and the privilege escalation issue in the Gen7 SonicOS Cloud platform NSv (CVE-2024-53706)?
Remediation Recommendations for Vendors
To mitigate the risks associated with these vulnerabilities, vendors should:
- Update Firmware: Ensure all impacted devices are updated to the fixed versions:
- Gen6 Firewalls: SonicOS 6.5.5.1-6n or higher
- Gen7 Firewalls: SonicOS 7.1.3-7015 or higher
- Gen7 NSv: SonicOS 7.0.1-5165 or higher
- TZ80 Series: SonicOS 8.0.0-8037 or higher
- Restrict Access: Limit SSLVPN and SSH management access to trusted sources or disable access from the internet entirely.
- Enable Multi-Factor Authentication (MFA): Strengthen authentication for all remote access to reduce attack surface.
- Monitor and Log: Continuously review system logs and monitor network traffic for anomalies that may indicate exploitation attempts.
How can TPRM professionals leverage Black Kite for these vulnerabilities?
Black Kite published the FocusTag™ SonicWall SonicOS – Jan2025 on January 8, 2025 to help TPRM professionals quickly identify vendors at risk. The tag provides:
- A list of vendors using affected SonicWall devices and their associated assets, such as IP addresses or subdomains.
- Insight into which vulnerabilities may impact vendors’ systems.
- An updated status on exploitation activity or new advisories.
Using this tag, professionals can narrow the scope of their risk assessments, focus efforts on high-priority vendors, and expedite their response to these vulnerabilities.
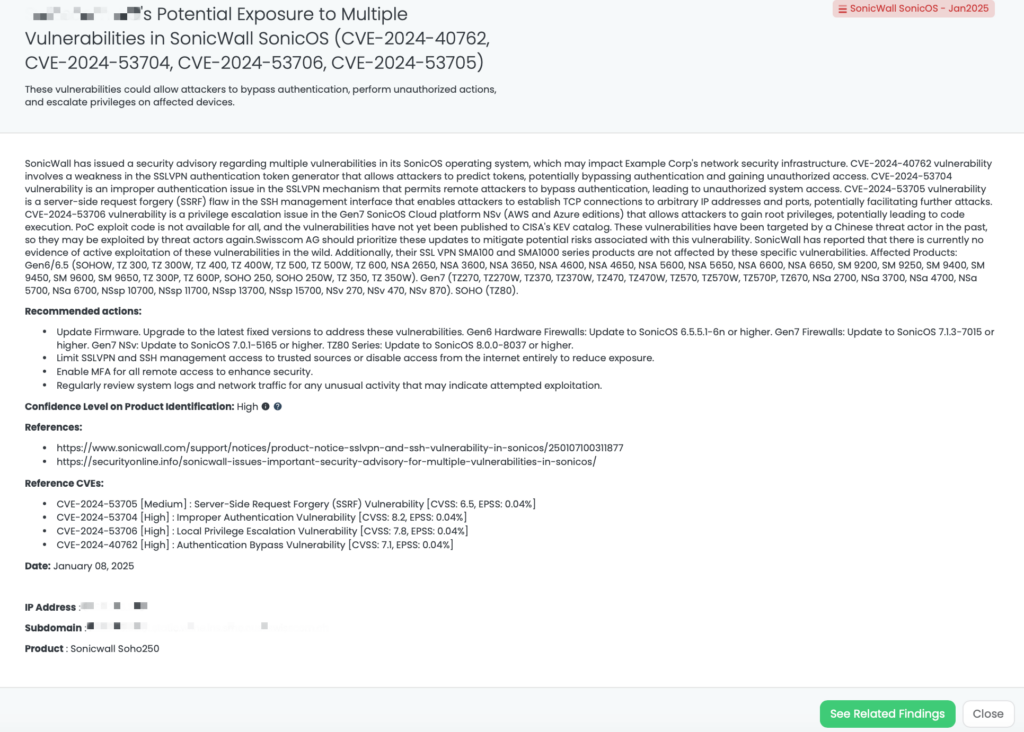
CVE-2025-0282 and CVE-2025-0283 in Ivanti Connect Secure
What are the vulnerabilities affecting Ivanti Connect Secure?
Ivanti Connect Secure, Policy Secure, and Neurons for ZTA Gateway products are affected by two critical vulnerabilities:
CVE-2025-0282: A Critical Stack-Based Buffer Overflow Vulnerability that permits unauthenticated remote code execution. This vulnerability affects Ivanti Connect Secure versions 22.7R2 through 22.7R2.4, Policy Secure versions 22.7R1 through 22.7R1.2, and Neurons for ZTA Gateways versions 22.7R2 through 22.7R2.3. It has a CVSS score of 9.0, reflecting its high severity, and an EPSS score of 0.83%, indicating a notable likelihood of exploitation.
CVE-2025-0283: A High-Severity Stack-Based Buffer Overflow Vulnerability that enables local authenticated attackers to escalate their privileges. This issue impacts the same product versions as CVE-2025-0282. It has a CVSS score of 7.0 and an EPSS score of 0.04%, suggesting a moderate risk of exploitation.
Both vulnerabilities were disclosed on January 8, 2025. CVE-2025-0282 has been listed in CISA’s Known Exploited Vulnerabilities (KEV) catalog on January 8, 2025, and is being exploited in limited incidents, particularly targeting Connect Secure appliances. Mandiant has attributed these exploitations to UNC5337, a suspected subgroup of the China-based espionage group UNC5221. No exploitation of CVE-2025-0283 has been reported.
Why should TPRM professionals care about these vulnerabilities?
These vulnerabilities present significant risks to organizations using Ivanti products:
- CVE-2025-0282: The ability to achieve unauthenticated remote code execution could enable attackers to gain full control of affected systems, compromising network integrity and exposing sensitive data.
- CVE-2025-0283: Privilege escalation could allow an attacker with local access to execute actions reserved for administrators, further increasing the risk of insider threats or unauthorized system changes.
The active exploitation of CVE-2025-0282 highlights the urgency of addressing these vulnerabilities, particularly for organizations relying on these products for secure remote access and network security.
What questions should TPRM professionals ask vendors about these vulnerabilities?
- Have you identified any systems within your organization running vulnerable versions of Ivanti Connect Secure, Policy Secure, or Neurons for ZTA Gateways?
- Have you applied the necessary patches for these vulnerabilities, and if so, when was the patching completed?
- Are you actively monitoring systems for signs of exploitation, particularly regarding CVE-2025-0282?
- Have you implemented Ivanti’s Integrity Checker Tool (ICT) to detect compromises, and what were the results?
Remediation Recommendations for Vendors
To mitigate the risks associated with these vulnerabilities, vendors should:
- Apply Patches Immediately: Upgrade to the latest patched versions:
- Ivanti Connect Secure: Version 22.7R2.5 or higher.
- Policy Secure: Patched versions available by January 21, 2025.
- Neurons for ZTA Gateways: Patched versions available by January 21, 2025.
- Perform Integrity Checks: Use Ivanti’s Integrity Checker Tool (ICT) to detect any signs of compromise in both internal and external systems.
- Restrict Internet Exposure: Ensure that Policy Secure appliances are not exposed to the internet, reducing the likelihood of exploitation.
- Factory Reset Compromised Systems: If signs of compromise are detected, perform a factory reset before redeployment.
- Monitor Activity: Continuously review system logs and network traffic for anomalies that may indicate exploitation attempts.
How can TPRM professionals leverage Black Kite for these vulnerabilities?
Black Kite’s FocusTag™ Ivanti Connect Secure – Jan2025 enables TPRM professionals to identify vendors at risk of exposure to these vulnerabilities. This tag provides:
- Insight into which vendors utilize affected Ivanti products and their associated assets, such as IP addresses and subdomains.
- Actionable intelligence to prioritize assessments and remediation efforts.
- Updates on exploitation activity and vendor patching status to guide decision-making.
The tag was published on January 9, 2025. Leveraging this tag can streamline risk management efforts and enhance the security posture of third-party ecosystems.
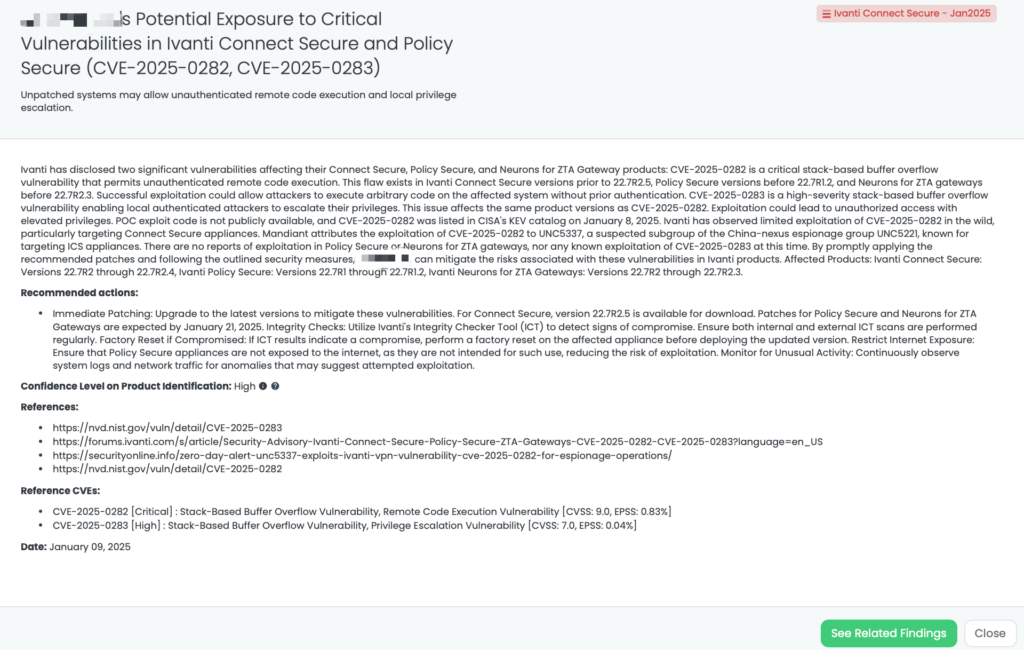
CVE-2024-12108, CVE-2024-12105, and CVE-2024-12106 Vulnerabilities in Progress WhatsUp Gold
What are the vulnerabilities affecting Progress WhatsUp Gold?
The Progress WhatsUp Gold network monitoring software has been identified as vulnerable to the following critical and medium-severity security issues:
The vulnerabilities affecting Progress WhatsUp Gold include the following:
CVE-2024-12108: An Authentication Bypass by Spoofing Vulnerability that allows attackers to gain complete control of the WhatsUp Gold server via the public API. This vulnerability has a CVSS score of 9.6 and an EPSS score of 0.07%, making it critical in severity.
CVE-2024-12106: A Missing Authentication for Critical Function Vulnerability that enables unauthenticated attackers to configure LDAP settings, potentially leading to unauthorized access and data breaches. While this vulnerability is rated Critical with a CVSS score of 9.4 by the CNA, the NIST CVSS score is 7.5. Its EPSS score is 0.05%.
CVE-2024-12105: A Path Traversal Vulnerability that allows authenticated users to extract sensitive information through specially crafted HTTP requests. This vulnerability is rated Medium with a CVSS score of 6.5 and an EPSS score of 0.05%.
These vulnerabilities affect WhatsUp Gold versions prior to 24.0.2. Progress issued a security bulletin on December 12, 2024, urging users to upgrade. While no evidence of active exploitation exists, similar vulnerabilities have historically attracted threat actors targeting network monitoring systems.
Why should TPRM professionals care about these vulnerabilities?
The WhatsUp Gold vulnerabilities present critical risks to network security due to the product’s integral role in monitoring and managing network devices. Exploitation of these vulnerabilities could result in:
- Full System Compromise: CVE-2024-12108 could allow attackers to control the WhatsUp Gold server, compromising all monitored devices and exposing sensitive configurations.
- Data Breaches: CVE-2024-12106 could enable attackers to tamper with LDAP settings, leading to unauthorized access to sensitive data or services.
- Sensitive Information Exposure: CVE-2024-12105 could facilitate information disclosure, which could be leveraged for subsequent attacks.
These risks make these vulnerabilities particularly concerning for third-party risk management (TPRM) professionals monitoring vendor ecosystems. The critical CVSS scores of CVE-2024-12108 and CVE-2024-12106 highlight the need for immediate action.
What questions should TPRM professionals ask vendors about these vulnerabilities?
- Have you identified any systems within your organization running vulnerable versions of WhatsUp Gold prior to 24.0.2?
- Has your organization implemented the recommended update to version 24.0.2, and when was it completed?
- Are access controls in place to restrict unauthorized changes to LDAP configurations and prevent exploitation?
- How do you monitor and address unusual activity that could indicate exploitation attempts related to these vulnerabilities?
Remediation Recommendations for Vendors
To address these vulnerabilities, vendors should:
- Upgrade Software: Immediately update to WhatsUp Gold version 24.0.2 to patch all identified vulnerabilities.
- Restrict Access: Limit server access to authorized personnel only and ensure secure configuration of LDAP settings.
- Monitor Logs: Regularly review server and network logs for anomalies indicative of exploitation attempts.
- Enhance Security Measures: Implement firewalls, intrusion detection systems, and strong authentication mechanisms to mitigate potential risks.
How can TPRM professionals leverage Black Kite for these vulnerabilities?
Black Kite provides the FocusTag™ Progress WhatsUp Gold, published on January 2, 2025, to help TPRM professionals identify and address potential risks in their vendor ecosystems. This tag allows users to:
- Determine which vendors utilize affected versions of WhatsUp Gold and the associated assets.
- Access details on vulnerable IP addresses and subdomains to prioritize risk assessments.
- Leverage actionable insights to communicate effectively with vendors and ensure timely remediation.
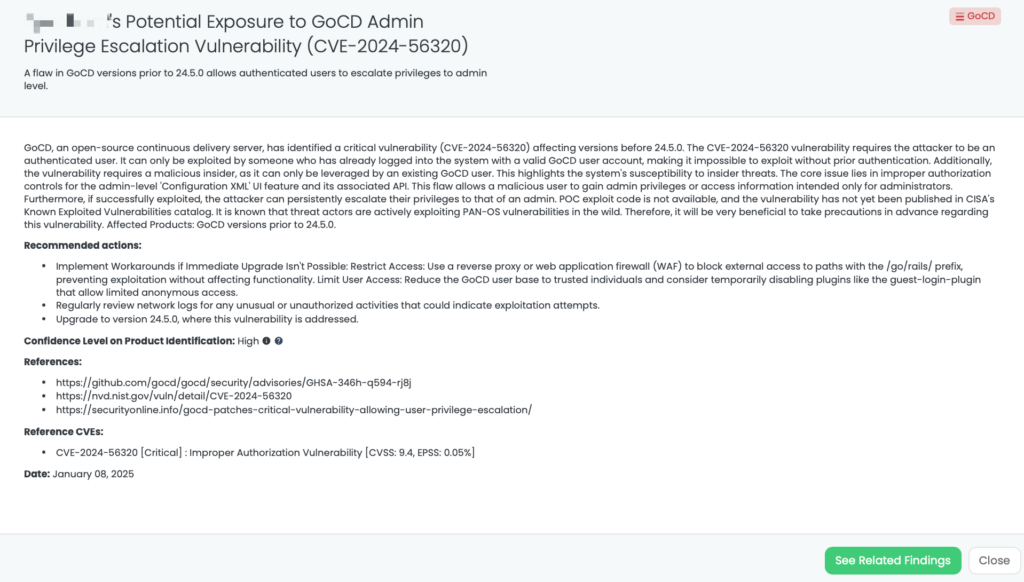
CVE-2024-56320 in GoCD
What is the GoCD Admin Privilege Escalation Vulnerability?
CVE-2024-56320 is a Critical Improper Authorization Vulnerability affecting GoCD versions prior to 24.5.0. This flaw enables authenticated users to persistently escalate their privileges to admin level, compromising the system’s integrity and security. The vulnerability arises from insufficient access controls in the admin “Configuration XML” UI feature and its associated API. The vulnerability has a CVSS score of 9.4 and an EPSS score of 0.05%, and it was published in January 2025.
This vulnerability cannot be exploited without prior authentication, requiring an attacker to have a valid GoCD user account. It poses a significant insider threat but does not currently have publicly available exploit code. As of now, it is not listed in CISA’s Known Exploited Vulnerabilities catalog.
Why should TPRM professionals care about this vulnerability?
The critical nature of CVE-2024-56320 makes it a significant concern for TPRM professionals. As GoCD is a continuous delivery server, its exploitation could:
- Compromise CI/CD Pipelines: Escalated admin privileges could allow attackers to alter build configurations, inject malicious code, or disrupt deployments.
- Sensitive Information Disclosure: Unauthorized access to admin-only data could expose credentials, API keys, and system configurations.
- Operational Risks: Persistent admin-level access increases the risk of prolonged exploitation and unauthorized system changes.
This vulnerability highlights the importance of securing insider accounts and CI/CD environments, both critical for maintaining operational and data security.
What questions should TPRM professionals ask vendors about this vulnerability?
- Have you upgraded all instances of GoCD to version 24.5.0 or later to mitigate the risk of CVE-2024-56320?
- Have you implemented the recommended workarounds such as using a reverse proxy or web application firewall (WAF) to block external access to paths with the /go/rails/ prefix, and limiting GoCD user base to trusted individuals?
- Can you confirm if you have taken steps to review network logs regularly for any unusual or unauthorized activities that could indicate exploitation attempts related to CVE-2024-56320?
- Have you considered temporarily disabling plugins like the guest-login-plugin that allow limited anonymous access to further secure your GoCD instances from potential exploitation of CVE-2024-56320?
Remediation Recommendations for Vendors
To mitigate the risks of CVE-2024-56320, vendors should:
- Upgrade to GoCD Version 24.5.0: This version addresses the improper authorization flaw and prevents privilege escalation.
- Restrict Access: Implement a reverse proxy or web application firewall (WAF) to block access to vulnerable paths with the /go/rails/ prefix. This can mitigate the risk without affecting functionality.
- Limit User Base: Reduce GoCD access to a smaller group of trusted users. Temporarily disable plugins like the “guest-login-plugin” to prevent anonymous or unauthorized access.
- Monitor Logs: Regularly review system and application logs for signs of privilege escalation or unauthorized access.
How can TPRM professionals leverage Black Kite for this vulnerability?
Black Kite’s FocusTag™ GoCD provides actionable intelligence to help TPRM professionals identify vendors potentially impacted by CVE-2024-56320. The tag enables users to:
- Pinpoint vendors utilize vulnerable GoCD versions and associated assets such as IP addresses or subdomains.
- Access insights into vendors’ patch management and security practices related to CI/CD environments.
- Expedite risk assessments by narrowing the scope to the most at-risk vendors.
This FocusTag™ was published on January 8, 2025. Black Kite users can operationalize this tag to prioritize remediation efforts and minimize exposure to insider threats.
Maximizing TPRM Effectiveness with Black Kite’s FocusTags™
Black Kite’s FocusTags™ are indispensable tools for refining TPRM strategies in today’s dynamic cybersecurity landscape. This week’s vulnerabilities in SonicWall SonicOS, Ivanti Connect Secure, Progress WhatsUp Gold, and GoCD highlight the critical role of FocusTags™ in proactive risk management. Here’s how these tags empower TPRM professionals:
- Real-Time Risk Identification: FocusTags™ enable immediate identification of vendors exposed to critical vulnerabilities, such as the authentication bypass issues in SonicWall or the privilege escalation risks in GoCD. This rapid insight ensures a timely response to emerging threats.
- Strategic Risk Prioritization: By assessing both the severity of vulnerabilities and the importance of affected vendors, FocusTags™ helps allocate resources efficiently, addressing the most pressing risks first.
- Enhanced Vendor Engagement: Armed with precise information, TPRM teams can initiate targeted discussions with vendors, emphasizing their exposure to vulnerabilities like the stack-based buffer overflow in Ivanti products or the API flaws in WhatsUp Gold.
- Strengthened Cybersecurity Posture: With a comprehensive overview of the evolving threat landscape, FocusTags™ aid in fortifying an organization’s overall security defenses against vulnerabilities impacting critical vendor systems.
Black Kite’s FocusTags™ simplify the complexity of cybersecurity threats by translating intricate technical data into actionable intelligence. This capability is critical for managing third-party risks effectively and proactively, ensuring that organizations remain one step ahead in mitigating potential threats.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
About Focus Friday
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FocusTagsTM in the Last 30 Days:
- SonicWall SonicOS – Jan2025: CVE-2024-40762, CVE-2024-53704, CVE-2024-53706, CVE-2024-53705, Use of Cryptographically Weak Pseudo-Random Number Generator (PRNG), Authentication Bypass Vulnerability, Server-Side Request Forgery (SSRF) Vulnerability, and Local Privilege Escalation Vulnerability in SonicWall’ SonicOS SSLVPN, SSH Management, and Gen7 Cloud NSv SSH Config Function.
- Ivanti Connect Secure – Jan2025: CVE-2025-0282, CVE-2025-0283, Stack-Based Buffer Overflow Vulnerability, Remote Code Execution Vulnerability, Privilege Escalation Vulnerability in Ivanti Connect Secure, Policy Secure, and Ivanti Neurons for ZTA gateways.
- Progress WhatsUp Gold: CVE-2024-12108, CVE-2024-12106, CVE-2024-12105, Authentication Bypass by Spoofing Vulnerability, Missing Authentication for Critical Function, and Path Traversal Vulnerability in Progress WhatsUp Gold.
- GoCD: CVE-2024-56320, Improper Authorization Vulnerability in GoCD.
- Apache Tomcat RCE: CVE-2024-56337, CVE-2024-50379, Time-of-check Time-of-use (TOCTOU) Race Condition Vulnerability, Remote Code Execution Vulnerability in Apache Tomcat.
- CrushFTP: CVE-2024-53552, Account Takeover Vulnerability in CrushFTP.
- Gogs Server: CVE-2024-55947, CVE-2024-54148, Path Traversal Vulnerability in Gogs Server.
- BeyondTrust PRA RS: CVE-2024-12356, Command Injection Vulnerability in BeyondTrust’s Privileged Remote Access (PRA), Remote Support (RS).
- Ivanti Cloud Services Application: CVE-2024-11639, CVE-2024-11772, CVE-2024-11772, Authentication Bypass Vulnerability Command Injection Vulnerability, and RCE Vulnerability SQLi Vulnerability in Ivanti Cloud Services Application.
- Cleo File Transfer: CVE-2024-50623, CVE-2024-55956, Remote Code Execution Vulnerability, Unrestricted File Upload and Download Vulnerability in Cleo Harmony, VLTrader, LexiCom.
- Qlik Sense Enterprise: CVE-2024-55579, CVE-2024-55580, Arbitrary EXE Execution Vulnerability Remote Code Execution Vulnerability in Qlik Sense Enterprise.
- SAP NetWeaver JAVA: CVE-2024-47578, Server-Side Request Forgery (SSRF) Vulnerability in SAP NetWeaver AS for JAVA (Adobe Document Services).
- PAN-OS: CVE-2024-0012, CVE-2024-9474, Authentication Bypass Vulnerability and Privilege Escalation Vulnerability in Palo Alto’s PAN-OS.
References
https://nvd.nist.gov/vuln/detail/CVE-2024-40762
https://nvd.nist.gov/vuln/detail/CVE-2024-53704
https://nvd.nist.gov/vuln/detail/CVE-2024-53706
https://nvd.nist.gov/vuln/detail/CVE-2024-53705
https://nvd.nist.gov/vuln/detail/CVE-2025-0282
https://nvd.nist.gov/vuln/detail/CVE-2025-0283
https://thehackernews.com/2025/01/ivanti-flaw-cve-2025-0282-actively.html
https://nvd.nist.gov/vuln/detail/CVE-2024-12108
https://nvd.nist.gov/vuln/detail/CVE-2024-12106
https://nvd.nist.gov/vuln/detail/CVE-2024-12105
https://community.progress.com/s/article/WhatsUp-Gold-Security-Bulletin-December-2024
https://research.checkpoint.com/2025/6th-january-threat-intelligence-report
https://nvd.nist.gov/vuln/detail/CVE-2024-56320
https://github.com/gocd/gocd/security/advisories/GHSA-346h-q594-rj8j
https://securityonline.info/gocd-patches-critical-vulnerability-allowing-user-privilege-escalation

