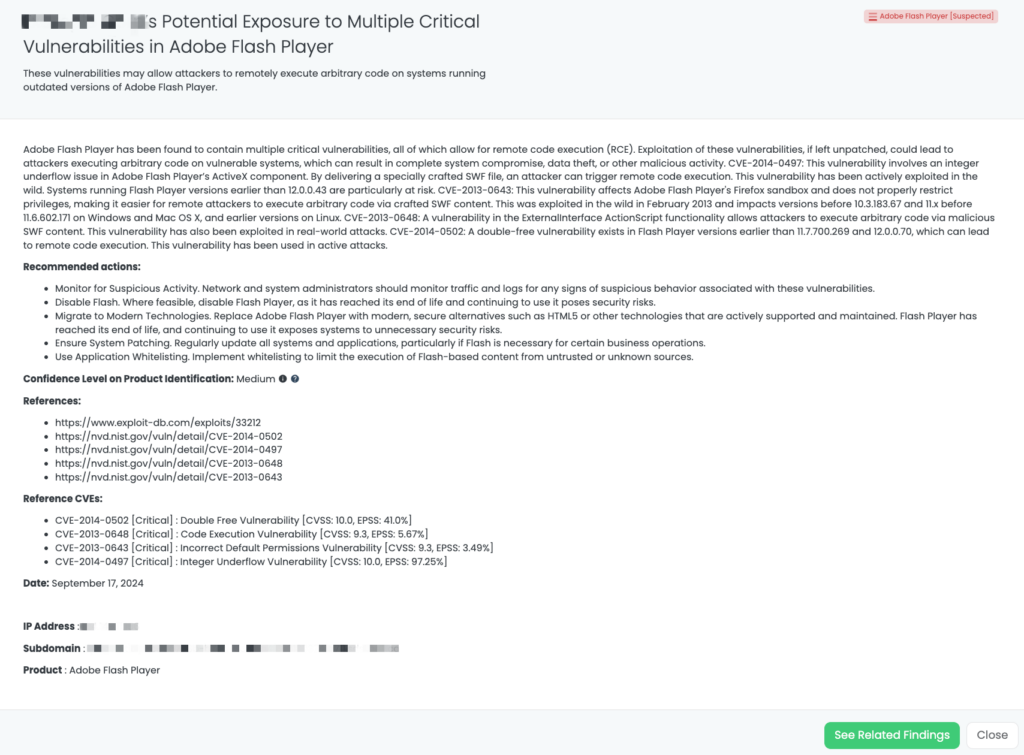
FOCUS FRIDAY: CRITICAL THIRD-PARTY RISK INSIGHTS – MSSQL AND ADOBE FLASH PLAYER VULNERABILITIES
Written By: Ferdi Gül
Contributor: Ferhat Dikbiyik
Welcome to this week’s Focus Friday blog, where we explore some of the most critical vulnerabilities impacting third-party vendors. In today’s post, we’re delving into vulnerabilities within two major software systems: Microsoft SQL Server (MSSQL) and Adobe Flash Player. These vulnerabilities pose a serious risk for companies still relying on outdated or vulnerable versions of these technologies. As part of our continuing effort to support effective Third-Party Risk Management (TPRM), we will explore the potential impacts of these vulnerabilities and provide guidance for mitigating associated risks through Black Kite’s FocusTags™. Read on to understand the severity of these risks and how to prioritize your remediation strategies.
CVE-2020-0618: Remote Code Execution in MSSQL Reporting Services
What is the MSSQL Remote Code Execution Vulnerability?
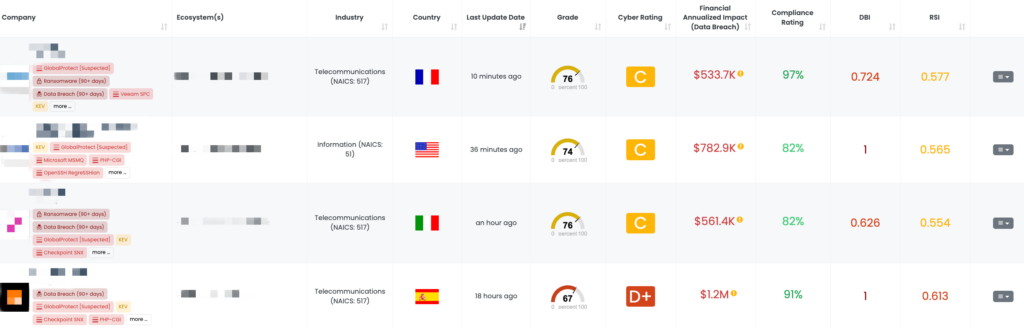
CVE-2020-0618 is a remote code execution vulnerability found in Microsoft SQL Server Reporting Services (SSRS). This vulnerability is triggered when the service mishandles page requests, allowing attackers to exploit this flaw through a specially crafted HTTP POST request to execute arbitrary code. This flaw has a CVSS score of 8.8 and an EPSS score of 97.34%, making it a high-risk vulnerability. The vulnerability was first disclosed in February 2020 and is being actively exploited in the wild by threat actor groups like Mallox.
Why Should TPRM Professionals Care About the MSSQL Vulnerabilities?
MSSQL is widely used in enterprise environments, and vulnerabilities like CVE-2020-0618 pose significant risk, particularly when SSRS is publicly exposed. TPRM professionals need to ensure that vendors with MSSQL installations have applied the necessary patches, as this vulnerability could lead to full server compromise, data theft, or the deployment of additional malicious payloads.
What Questions Should TPRM Professionals Ask Vendors About the MSSQL Vulnerability?
- Is Microsoft SQL Server Reporting Services (SSRS) in use on your systems, and if so, which versions?
- Have the February 2020 patches been applied to mitigate CVE-2020-0618?
- Are you restricting access to Reporting Services to authenticated users only?
- How do you monitor your network for unusual activity, specifically for signs of malicious HTTP POST requests?
Remediation Recommendations for Vendors Subject to This Risk:
- Immediately apply the February 2020 security patch for SQL Server Reporting Services to resolve this vulnerability.
- Ensure that only authenticated users can access the application and that anonymous users do not hold the “Browser” role.
- Consider cycling the server’s Machine Key if compromise is suspected, even after applying the patch, to mitigate residual exploitation risk.
- Monitor web traffic for unusual activity, particularly POST requests to /ReportViewer.aspx.
How TPRM Professionals Can Leverage Black Kite for This Vulnerability
Black Kite’s FocusTags™ help you identify vendors that have the MSSQL Reporting Services component installed, allowing you to focus your inquiries. The tag for this vulnerability was updated on September 18, 2024, and includes detailed asset information (such as exposed IP addresses and subdomains). Black Kite’s intelligence ensures that TPRM professionals can efficiently prioritize the vendors at risk and take immediate action.
CVE-2014-0497: Integer Underflow Vulnerability in Adobe Flash Player
What is the Integer Underflow Vulnerability in Adobe Flash Player?
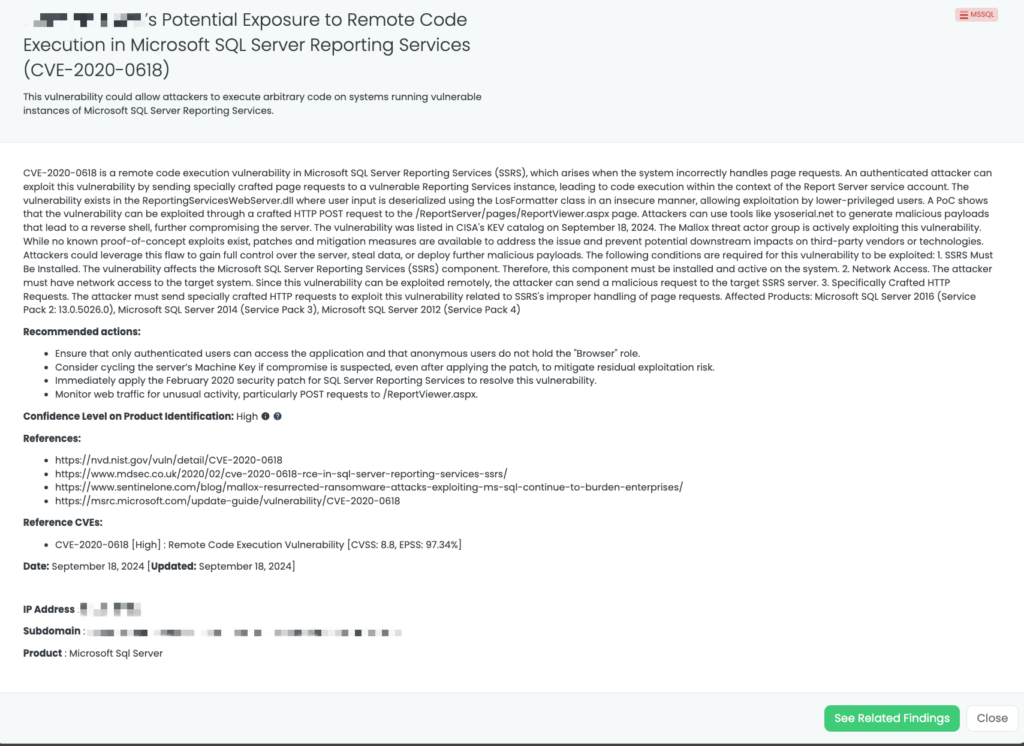
CVE-2014-0497 is a critical integer underflow vulnerability in Adobe Flash Player, primarily affecting older versions (before 12.0.0.43). This flaw allows attackers to execute arbitrary code remotely by delivering a specially crafted SWF file to a vulnerable system. The vulnerability is actively exploited in the wild, posing significant risks to systems still using outdated versions of Flash Player. Systems running Flash Player versions before 12.0.0.43 are particularly vulnerable.
Why Should TPRM Professionals Care About the Adobe Flash Player Vulnerabilities?
Adobe Flash Player has reached its end of life, but many organizations may still be using legacy systems where it is installed. TPRM professionals must ensure vendors are not using unsupported software like Flash Player. Flash-based systems are prime targets for attackers due to known vulnerabilities and the lack of ongoing support, making them a high-risk vector for exploitation, especially if they are accessible via the internet.
What Questions Should TPRM Professionals Ask Vendors About the Adobe Flash Player Vulnerability?
- Are any of your systems still running Adobe Flash Player, and if so, which version?
- Have you fully disabled or uninstalled Adobe Flash Player, and what alternatives are being used?
- If Flash is still in use for business-critical operations, what security measures are in place to prevent exploitation?
- How do you monitor legacy software to ensure vulnerabilities like this are not being exploited?
Remediation Recommendations for Vendors Subject to This Risk:
- Disable Adobe Flash Player. Given its end-of-life status, it’s crucial to disable Flash Player wherever possible. Continuing to use it exposes systems to unnecessary security vulnerabilities.
- Transition to Modern Technologies. Shift away from Adobe Flash Player to more secure, actively supported alternatives like HTML5. This transition mitigates risks tied to Flash’s outdated and unsupported nature.
- Monitor for Anomalous Behavior. Administrators should actively monitor network traffic and system logs for any suspicious activity related to potential exploitation of Flash-based vulnerabilities.
- Apply Application Whitelisting. Implement whitelisting measures to prevent untrusted or unknown sources from executing Flash-based content.
- Maintain Up-to-date Systems. Ensure all systems and applications are regularly updated. If Flash is still required for specific business purposes, prioritize patches and updates to minimize risk.
How TPRM Professionals Can Leverage Black Kite for This Vulnerability
Black Kite’s FocusTags™ pinpoint which vendors may still be using Adobe Flash Player in their systems, providing you with the data you need to assess exposure. The tag was last updated on September 17, 2024, with specific IP addresses and subdomains identified. Black Kite’s real-time intelligence allows TPRM professionals to act swiftly, making informed decisions about the vulnerability’s risks and the vendors involved.
Enhancing TPRM Strategies With Black Kite’s FocusTags™
In the ever-changing cybersecurity landscape, staying ahead of critical vulnerabilities is essential for a solid Third-Party Risk Management (TPRM) strategy. Black Kite’s FocusTags™ offer a unique advantage, transforming complex cybersecurity data into actionable insights that streamline your risk management efforts.
Immediate Vendor Risk Identification: FocusTags™ provide real-time identification of vendors exposed to critical vulnerabilities like those in MSSQL and Adobe Flash Player, enabling rapid, targeted responses.
Risk Prioritization with Precision: With FocusTags™, TPRM professionals can prioritize risks based on the severity of the vulnerability and the criticality of the vendor. This helps in focusing attention where it matters the most.
Empowered Vendor Engagement: FocusTags™ enable more meaningful, security-driven conversations with vendors, ensuring they are aware of their exposure and ready to mitigate associated risks.
Holistic Security Insights: By offering a comprehensive view of the threat landscape, FocusTags™ allow you to fortify your cybersecurity defenses and manage third-party risks proactively.
For any organization committed to enhancing its TPRM strategies, Black Kite’s FocusTags™ provide the perfect toolset for staying ahead of today’s evolving threats, allowing you to make informed decisions quickly and efficiently.
Want to take a closer look at FocusTags™?
Take our platform for a test drive and request a demo today.
About Focus Friday
Every week, we delve into the realms of critical vulnerabilities and their implications from a Third-Party Risk Management (TPRM) perspective. This series is dedicated to shedding light on pressing cybersecurity threats, offering in-depth analyses, and providing actionable insights.
FocusTags™ in the Last 30 Days:
- PAN-OS Cleartext: CVE-2024-8687, Cleartext Exposure Security Flaw in PAN-OS, GlobalProtect, Prisma Access.
- FileCatalyst Workflow: CVE-2024-6633, CVE-2024-6632, Insecure Default Configuration and SQL Injection Vulnerability in Fortra FileCatalyst Workflow.
- WPML: CVE-2024-6386, Critical Remote Code Execution Vulnerability via Twig Server-Side Template Injection in WPML Plugin
- SonicWall Firewalls: CVE-2024-40766, Critical Improper Access Control Vulnerability in SonicWall Firewalls
- Dahua IP Camera: CVE-2021-33045, CVE-2021-33044, Critical Authentication Bypass Vulnerabilities in Dahua IP Camera Systems
- Microsoft Privilege Escalation Vulnerability: CVE-2024-38193, CVE-2024-38106, CVE-2024-38107, Critical Privilege Escalation Vulnerabilities in Microsoft Windows
- SolarWinds WHD: CVE-2024-28986, Critical Remote Code Execution Vulnerability in SolarWinds Web Help Desk
- Zimbra LFI: CVE-2024-33535, Local File Inclusion Vulnerability in Zimbra Collaboration Suite
- Exchange Server RCE: CVE-2021-31196, CVE-2021-34473, Remote Code Execution Vulnerabilities in Microsoft Exchange Server
- Zabbix: CVE-2024-22116, Critical Remote Code Execution Vulnerability in Zabbix Monitoring Solution
- Jenkins ClassLoaderProxy: CVE-2024-43044, Arbitrary File Read and Remote Code Execution Vulnerability in Jenkins ClassLoaderProxy
- Dahua NVR4: CVE-2024-39944, CVE-2024-39948, and CVE-2024-39949, Remote Code Execution, Authentication Bypass, and Improper Access Control Vulnerabilities in Dahua NVR4 devices
References
https://nvd.nist.gov/vuln/detail/CVE-2020-0618#match-11997218
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2020-0618
https://www.mdsec.co.uk/2020/02/cve-2020-0618-rce-in-sql-server-reporting-services-ssrs
https://nvd.nist.gov/vuln/detail/CVE-2014-0497
https://nvd.nist.gov/vuln/detail/CVE-2013-0643
https://nvd.nist.gov/vuln/detail/CVE-2013-0648
https://nvd.nist.gov/vuln/detail/CVE-2014-0502
https://securityonline.info/cisa-warns-of-actively-exploited-adobe-flash-player-vulnerabilities

