Focus Friday: Tackling Emerging Threats – Volt Typhoon, Elementor RCE, and MLflow Vulnerabilities
Written by: Kat Desy
Written by: Ferhat Dikbiyik
Additional Contributions: Ferdi Gül and Yavuz Han
Edited by: Katherine Desy
Welcome to another edition of Focus Friday, where we delve into the latest cyber threats and their implications for Third-Party Risk Management (TPRM). This week, we focus on a diverse range of critical cybersecurity issues: the Volt Typhoon campaign targeting US infrastructures, a concerning Remote Code Execution vulnerability in the popular WordPress plugin Elementor, and a newly discovered path traversal vulnerability in MLflow, an open-source machine learning platform. These developments highlight the ever-evolving landscape of cyber threats that TPRM professionals must navigate. Our discussion will shed light on the nature of these threats, their potential impacts, and how Black Kite’s Focus Tags™ provide vital insights for effective risk management strategies. Join us as we explore these pressing issues and their ramifications for cybersecurity and TPRM practices.
Understanding and Mitigating Volt Typhoon: A TPRM Focus on Nation-State Cyber Attacks
What is the Volt Typhoon Campaign?
The Volt Typhoon Campaign, making headlines recently for its elevated cyber attacks, is a significant threat in the realm of cybersecurity. Volt Typhoon, identified as a state-sponsored threat actor by several international cybersecurity authorities, including CISA, FBI, and NSA, represents a sophisticated and stealthy cyber-espionage campaign. Active since at least 2021, this campaign, linked to the People’s Republic of China, has been targeting critical infrastructure organizations across the United States, including Guam.
The campaign is notorious for focusing on stealth, employing living-off-the-land (LOTL) techniques and hands-on-keyboard activity to evade detection. LOTL techniques leverage legitimate networking tools preloaded onto operating systems, while hands-on-keyboard activity involves manual command execution by human attackers on compromised systems. These methods allow the Volt Typhoon to blend into normal network activity and maintain access for extended periods without detection.
Key vulnerabilities exploited by the Volt Typhoon include CVE-2022-47966 and CVE-2022-42475. CVE-2022-47966, found in Zoho ManageEngine ServiceDesk Plus, enables remote code execution, allowing attackers to gain unauthorized access and establish persistence within networks. CVE-2022-42475, associated with Fortinet FortiGuard devices, has also been exploited to gain access and compromise network security. The broad range of targeted sectors, including communications, manufacturing, utilities, and government, highlights the campaign’s extensive reach and the critical need for heightened cybersecurity vigilance.
Recent heightened media coverage of these attacks underscores the urgency and importance of addressing this sophisticated cyber threat, particularly for organizations within these critical infrastructure sectors. The targeted sectors span communications, manufacturing, utilities, transportation, construction, maritime, government, IT, and education, illustrating the campaign’s broad scope and potential impact.
Why Should TPRM Professionals Be Concerned About the Volt Typhoon Campaign?
The Volt Typhoon campaign’s focus on critical infrastructure sectors makes it a pivotal concern for Third-Party Risk Management (TPRM) professionals. The sophisticated nature of this state-sponsored campaign, along with its exploitation of vulnerabilities in widely used products like FortiOS and Zoho ManageEngine ServiceDesk Plus, places a significant number of third-party vendors at risk. TPRM professionals must recognize the potential for these vulnerabilities to be exploited not just for data theft, but for sustained, undetected access to their networks.
The campaign’s usage of advanced techniques, such as living-off-the-land (LOTL) and hands-on-keyboard activities, adds complexity to detecting and mitigating these threats. Since these methods involve the use of legitimate tools and manual command executions, they can easily blend into regular network activities, making early detection challenging.
Furthermore, the campaign’s broad targeting across various sectors amplifies its impact. TPRM professionals should be especially vigilant if their vendor network includes organizations in communications, manufacturing, utilities, transportation, and government sectors. Given the campaign’s focus on stealth and persistence, it’s crucial for TPRM teams to ensure that their vendors not only patch known vulnerabilities but also implement comprehensive monitoring and response strategies to identify and mitigate any potential breaches.
The recent spike in media attention around these attacks serves as a reminder of the evolving nature of cyber threats and the need for TPRM professionals to continuously adapt their strategies to safeguard their supply chains against such sophisticated adversaries.
What Specific Questions Should TPRM Professionals Ask Vendors Regarding Volt Typhoon?
In the context of the Volt Typhoon campaign, TPRM professionals should ask targeted, technical questions to vendors, especially those using FortiOS or Zoho ManageEngine ServiceDesk Plus. These questions are designed to assess the vendors’ awareness, preparedness, and response strategies related to this campaign and its exploited vulnerabilities:
- “Have you conducted a thorough assessment of your systems for the presence of vulnerabilities CVE-2022-47966 and CVE-2022-42475?”
- “What specific steps have you taken to mitigate the risks associated with these vulnerabilities, and have you applied the latest patches provided by Fortinet and Zoho?”
- “Can you describe your current monitoring protocols to detect potential LOTL or hands-on-keyboard activities typical of Volt Typhoon?”
- “How are you ensuring the security of network traffic, particularly through devices that may be targeted by Volt Typhoon, such as SOHO routers?”
- “In light of Volt Typhoon’s focus on critical infrastructure, what measures have you implemented to safeguard against unauthorized access and data exfiltration?”
- “What incident response and recovery plans do you have in place should a breach be linked to these vulnerabilities or similar attack vectors?”
These questions aim to gauge the vendors’ level of vigilance and preparedness against the sophisticated tactics employed by the Volt Typhoon and ensure that they are actively working to secure their networks against such advanced threats.
Remediation Recommendations for Vendors at Risk from Volt Typhoon Campaign
For vendors potentially impacted by the Volt Typhoon campaign, especially those using FortiOS or Zoho ManageEngine ServiceDesk Plus, specific technical remediation recommendations are essential:
FortiOS (CVE-2022-42475):
- Immediately apply the latest security updates provided by Fortinet.
- Conduct a comprehensive security audit to ensure all FortiOS instances are running the patched versions.
- Implement strict network segmentation to limit the lateral movement of potential attackers.
- Enhance monitoring of network traffic, particularly SSL-VPN traffic, to detect anomalous patterns indicative of exploitation.
- Regularly review system logs for signs of unauthorized access attempts.
Zoho ManageEngine ServiceDesk Plus (CVE-2022-47966):
- Patch all affected versions of ManageEngine ServiceDesk Plus to the fixed versions as listed in the advisory.
- For systems with SAML SSO configured, ensure that they are updated and securely configured.
- Monitor network and application logs for unusual activity, particularly relating to SAML SSO implementations.
- Conduct vulnerability assessments to identify and address any potential weaknesses in the deployment.
- Regularly update all software components to their latest versions to mitigate the risk of exploitation.
ManageEngine ADSelfService Plus (CVE-2021-40539):
- Update ManageEngine ADSelfService Plus to the latest version that patches the REST API authentication bypass vulnerability.
- Restrict network access to the ADSelfService Plus instance, allowing only authorized users.
- Implement additional layers of authentication and monitoring for access to ADSelfService Plus.
- Regularly review and update security configurations to ensure they are aligned with current best practices.
These remediation steps are critical in protecting against the sophisticated techniques employed in the Volt Typhoon campaign, thereby enhancing the overall security posture of the affected vendors.
How Can Black Kite Enhance TPRM Strategies in Response to the Volt Typhoon Campaign?
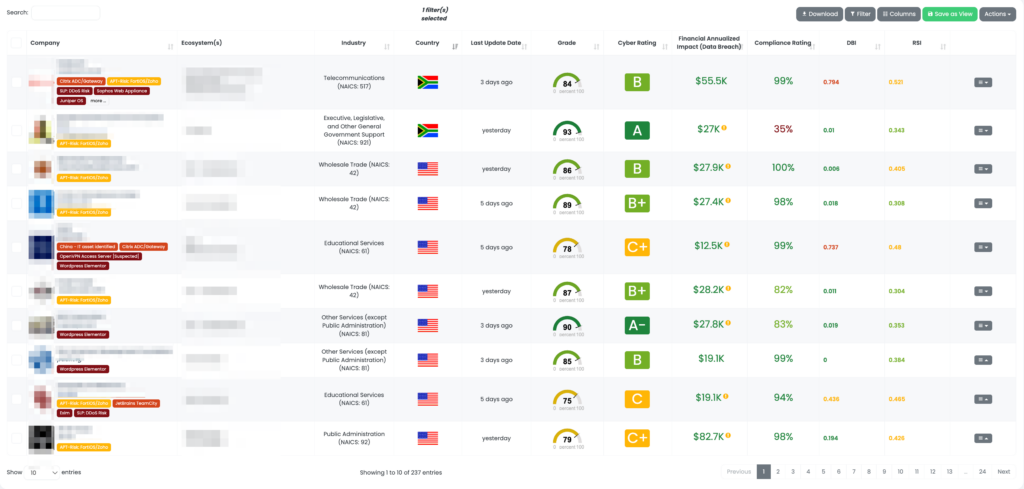
In the wake of the Volt Typhoon campaign, leveraging Black Kite’s capabilities becomes crucial for an effective TPRM strategy. Black Kite initially applied the “APT Risk: FortiOS/Zoho” tag in September, and the tag has been recently updated to reflect the latest developments in this campaign. This tag is instrumental in identifying vendors using either FortiOS or Zoho ManageEngine ServiceDesk Plus, which are at heightened risk due to the campaign.

Here’s how Black Kite supports TPRM professionals:
- Focused Vendor Assessment: Utilize the “APT Risk: FortiOS/Zoho” tag to pinpoint vendors using these specific products, allowing for a targeted approach to risk assessment.
- Detailed Asset Information: Black Kite provides detailed information about the specific IT assets on which these products are used, enabling TPRM teams to understand the scope and scale of potential exposure.
- Customizable Vendor Filtering: With Black Kite, users can further filter their vendors by industry, country, and other parameters, ensuring a comprehensive and tailored risk management strategy.
- Continuous Monitoring and Updates: Black Kite offers ongoing monitoring and updates about the evolving threats associated with Volt Typhoon, keeping TPRM teams informed and prepared for proactive responses.
By harnessing these features, Black Kite users can effectively identify and prioritize the vendors most susceptible to this campaign, streamline their risk management efforts, and ensure robust defenses against sophisticated nation-state threats like the Volt Typhoon.
TPRM Perspective: Addressing the CVE-2023-48777 Vulnerability in WordPress’s Elementor Plugin
What is the CVE-2023-48777 Vulnerability in Elementor?
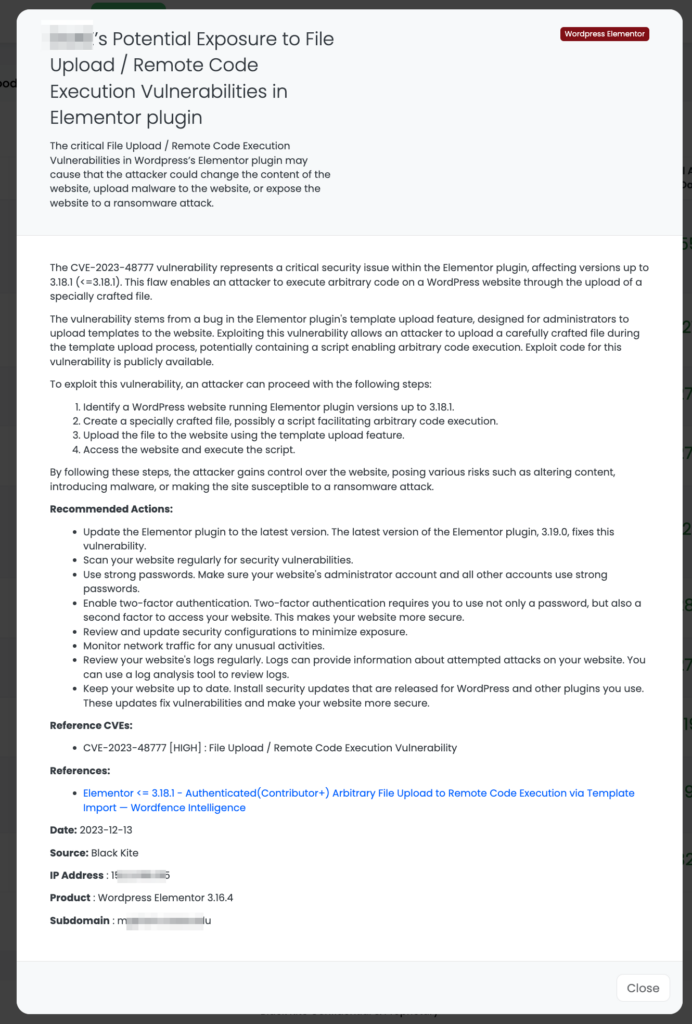
CVE-2023-48777 is a critical vulnerability in the Elementor plugin for WordPress, impacting nearly 5 million sites using the plugin. Discovered this week, this vulnerability allows authenticated users with Contributor-level access or higher to execute remote code via file upload through the template import functionality of Elementor. Specifically, it affects all versions up to and including 3.18.1, with a CVSS score of 8.8 (High).
The vulnerability originates from the handle_elementor_upload function within the Elementor AJAX function import_template, which is accessible to Contributor-level users. This function, despite using file type validation, saves the uploaded file to a temporary directory before checking its type and does not delete it if validation fails. Consequently, attackers can upload files of any type, which are then stored in a temporary directory with a randomized name. Exploiting this vulnerability enables attackers to upload malicious files and execute code on the server, potentially compromising the site.
Elementor released a patch in version 3.18.2 on December 8, 2023, to address this vulnerability. However, the initial patch in version 3.18.1 was deemed insufficient, prompting the release of the updated version. The severity of this vulnerability, combined with the widespread use of the Elementor plugin, underscores the need for immediate action by website administrators to update to the fully patched version and review their site’s security posture
Why is CVE-2023-48777 in Elementor Critical for TPRM Professionals?
The critical vulnerability CVE-2023-48777 in the Elementor WordPress plugin poses a substantial risk that TPRM professionals must urgently address. Elementor’s widespread use heightens the risk of this Remote Code Execution (RCE) vulnerability, especially considering the potential for attackers to take over websites. Such a breach could lead to the alteration of important information on vendor websites or the insertion of malicious code. This not only compromises the integrity of the website but also poses a direct threat to clients interacting with these compromised sites.
Key Questions TPRM Professionals Should Ask Vendors About CVE-2023-48777 in Elementor
In addressing the vulnerability CVE-2023-48777 within the Elementor plugin, TPRM professionals should pose specific, technically oriented questions to their vendors:
- “Have you updated the Elementor plugin to the version that patches the CVE-2023-48777 vulnerability?”
- “Can you detail the security measures in place to detect and prevent unauthorized website modifications or code insertions?”
- “How do you ensure continuous monitoring and rapid response to potential security breaches on your WordPress sites?”
- “What steps have you taken to communicate with your clients about the security of their data and interactions with your website post-remediation?”
What Remediation Steps Should Vendors Take for CVE-2023-48777 in Elementor?
Vendors impacted by the CVE-2023-48777 vulnerability in the Elementor WordPress plugin should urgently undertake the following remediation steps:
- Apply the latest patch for Elementor immediately to address the RCE vulnerability.
- Conduct a thorough review of website security configurations to prevent similar vulnerabilities.
- Regularly monitor the website for unauthorized changes or signs of compromise.
- Inform clients about the measures taken and advise them on safe interaction with the website.
Utilizing Black Kite for Effective TPRM in Light of Elementor CVE-2023-48777 Vulnerability
The recent publication of the “File Upload / Remote Code Execution Vulnerabilities in Elementor plugin” tag by Black Kite offers TPRM professionals a vital tool in addressing the risks associated with CVE-2023-48777. This tag, providing detailed information about the exact Elementor versions used by vendors and the specific IT assets affected, is essential for effective communication and risk management.
Here’s how Black Kite aids in this situation:
- Precise Vendor Identification: Black Kite pinpoints vendors using vulnerable versions of the Elementor plugin, allowing TPRM teams to focus on those most at risk.
- Asset-Level Insights: By specifying the exact IT assets using these versions, Black Kite enables targeted risk assessment and remediation efforts.
- Informed Vendor Engagement: The detailed information in the tag facilitates deeper discussions with vendors about their specific exposure and the steps they are taking to mitigate risks.
- Streamlined Remediation Process: Knowing the exact version of Elementor used by vendors streamlines the remediation process, ensuring swift and appropriate actions are taken.
Leveraging Black Kite in this context ensures a more focused and effective TPRM strategy, enabling professionals to mitigate the risks posed by CVE-2023-48777 efficiently and protect their digital ecosystem from potential threats.
Addressing the Path Traversal Vulnerability in MLflow: A TPRM Perspective
What is CVE-2023-6753 in MLflow?
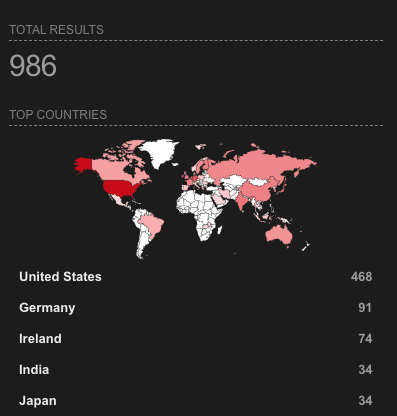
MLflow, an open-source platform widely used in the machine learning lifecycle, recently encountered a critical vulnerability, CVE-2023-6753. This vulnerability, classified as a path traversal flaw, was identified in versions of MLflow prior to 2.9.2. If exploited, it could allow attackers to access or modify files outside of the restricted directories on the server, posing serious security risks. Given the recent advancements in large language models (LLMs) and the increasing adoption of platforms like MLflow, understanding and mitigating this vulnerability becomes crucial, especially considering almost 1000 organizations, most in the US, use MLflow according to our research on internet-wide scanners like Shodan.
TPRM Implications of CVE-2023-6753 in MLflow
From a TPRM perspective, the CVE-2023-6753 vulnerability in MLflow is particularly concerning due to the platform’s growing popularity in data science and machine learning fields. For TPRM professionals, it’s vital to assess whether vendors in their network are using vulnerable versions of MLflow. If exploited, this vulnerability could lead to unauthorized access to sensitive data, potentially compromising the integrity and confidentiality of machine learning projects.
Questions TPRM Professionals Should Ask about CVE-2023-6753
- “Have you identified any instances of MLflow prior to version 2.9.2 in your network?”
- “What steps are you taking to patch or mitigate the path traversal vulnerability in MLflow?”
- “How are you monitoring for potential exploitation or unauthorized file access within MLflow environments?”
- “Can you detail your incident response plan in case of a breach through this vulnerability?”
Remediation Recommendations for CVE-2023-6753
Vendors using MLflow should take the following steps:
- Immediately upgrade to MLflow version 2.9.2 or later to patch the vulnerability.
- Ensure strict limitations on file access and directory traversal within the MLflow environment.
- Regularly scan for unusual activities that could indicate exploitation attempts.
Leveraging Black Kite for CVE-2023-6753 Risk Management
With the introduction of the “MLflow” tag, Black Kite users can effectively identify and manage the risks associated with CVE-2023-6753. The tag provides use of MLflow by vendors and the exact IT assets affected, enabling targeted risk assessments and precise vendor communication.
Enhancing TPRM Strategies with Black Kite’s Specialized Focus Tags™
Black Kite’s Focus Tags™ play an indispensable role in refining Third-Party Risk Management (TPRM) approaches, especially in light of recent vulnerabilities and threats like the Volt Typhoon campaign, WordPress Elementor RCE, and MLflow path traversal issues. These tags provide:
- Dynamic Vulnerability Insights: Offer immediate identification of vendors impacted by emerging threats, enabling swift and decisive responses.
- Strategic Risk Management: Assist in categorizing risks based on the severity of vulnerabilities and the criticality of affected vendors, ensuring focused attention where it’s needed most.
- Enhanced Vendor Communication: Enable TPRM teams to engage in detailed discussions with vendors, specifically addressing their exposure to recent vulnerabilities and cyber campaigns.
- Overall Security Ecosystem Strengthening: Present a comprehensive view of the evolving threat landscape, facilitating the development of more robust and adaptive cybersecurity strategies.
Black Kite’s Focus Tags™, tailored to recent cybersecurity developments, empower TPRM professionals with actionable insights, fostering more effective and proactive risk management tailored to the unique challenges of the current digital threat environment.
Want to take a closer look at Focus Tags™?
Take our platform for a test drive and request a demo today.
Focus Tags™ in the Last 30 days
- Mlflow: CVE-2023-6753, A Path Traversal Vulnerability in MLflow.
- Elemtor Plugin: CVE-2023-48777, File Upload / Remote Code Execution Vulnerabilities in The Elementor Website Builder versions identified before <=3.18.1
- APT Risk: FortiOS/Zoho: Vulnerabilities used by nation-state actors as part of Volt Typhoon campaign
- Atlassian Confluence Data Center and Server: CVE-2023-22522, Template Injection Vulnerability
- Adobe ColdFusion: CVE-2023-26360, Improper Access Control Vulnerability
- Qlik Sense: CVE-2023-48365, Unauthenticated RCE Vulnerability in Qlik Sense Enterprise for Windows
- Apache Superset: CVE-2023-40610, Privilege Escalation Vulnerability in Apache Superset <2.1.2 versions.
- OpenVPN Access: CVE-2023-46850, OpenVPN Access Server Flaw Exposes Sensitive Data and RCE Possible
- ownCloud: CVE-2023-49103, Information Disclosure Vulnerability in ownCloud’s Graphapi Component
- Atlassian Bamboo Data Center: CVE-2023-22516, RCE Vulnerability in Bamboo Data Center and Server Tagging
- Sophos Web Appliance: CVE-2023-1671 Pre-auth Command Injection Vulnerability in the version 4.3.10.3 and earlier
- Oracle Weblogic: CVE-2020-2551 Unauthenticated RCE Vulnerability over IIOP based on 10.3.6.0, 12.1.3.0, 12.2.1.3.0, 12.2.1.4.0
- Boeing Data Breach: Boeing Vendor Information disclosed in data breach
- Juniper Junos OS: CVE-2023–36845 Juniper Junos OS EX, SRX Series PHP External Variable Modification RCE Vulnerability
- SysAid: CVE-2023-47246 SysAid ITSM File System Path Traversal
- ServiceNow Data Exposure Flaw: ServiceNow clients
- SLP: CVE-2023-29552 LSP DOS
References:
https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-250a
https://www.tenable.com/blog/volt-typhoon-cybersecurity-advisory
https://www.securityweek.com/chinese-apt-volt-typhoon-linked-to-unkillable-soho-router-botnet/
https://www.manageengine.com/security/advisory/CVE/cve-2022-47966.html
https://www.fortiguard.com/psirt/FG-IR-22-398
https://patchstack.com/articles/critical-vulnerability-in-elementor-affecting-5-million-websites/
https://nvd.nist.gov/vuln/detail/CVE-2023-6753
https://github.com/mlflow/mlflow/commit/1c6309f884798fbf56017a3cc808016869ee8de4

