How to Respond a Data Breach in Your Supply Chain
Written by: Black Kite
Cybersecurity breaches in the supply chain are a major problem to any organization’s risk posture, operational efficiency, and reputation. Security incidents often lead to data breaches and ransomware can lead to loss of customer data and intellectual property. In a report by Cybersecurity Ventures, it was estimated that global ransomware damage costs will reach $20 billion by 2025.
As everyone knows, you can never be 100% safe from attackers. So, what happens when your best effort to stop bad stuff from happening is unsuccessful? You’d better have a response plan in place BEFORE it hits the fan.

There are two elements to incident response
1) During, and
2) After.
We’ll be looking at both in this blog.
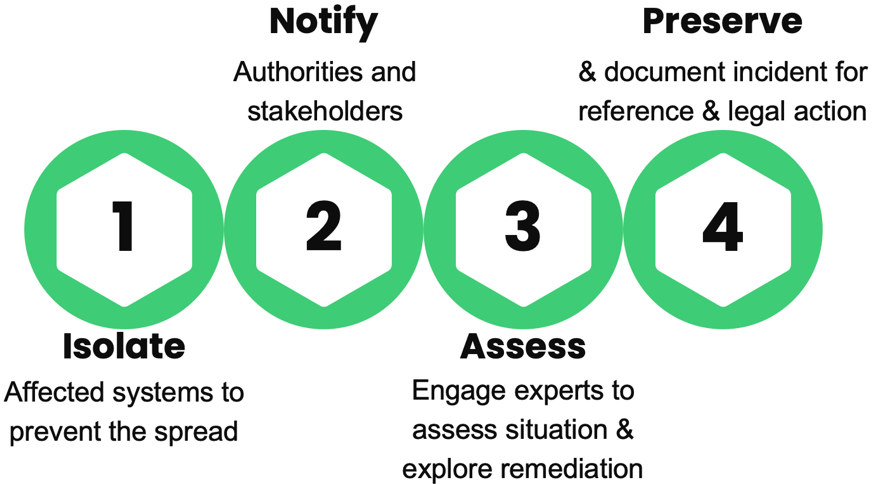
Incident response – During the Incident
In the event of a ransomware attack, taking immediate action is critical to mitigate the damage.
What to do during the attack
- Isolate systems. Once an attack is detected, it is critical to limit its ability to spread. Use network tools to segregate impacted systems; turn up monitoring tools to make sure the malicious activity is not spreading ‘under the covers.’
- Engage with cybersecurity experts to assess the situation and explore potential remediation options. If you have internal teams to address, turn them loose. If you don’t have the resources (and most organizations don’t) you may need to go out to market. It is highly suggested to have a firm on retainer.
- Begin the process of notifying relevant stakeholders – internal, external, law enforcement, regulators, etc. – according to your escalation process (you do have a documented escalation process, right?). The requirements for speed of notification will likely accelerate in the short term as a result of new SEC regulation and you need to be ready, even if you aren’t directly subject to SEC oversight.
- Ensure you have mechanisms in place to preserve evidence and document the incident for future reference and potential legal actions. You don’t want to be in a position where data and evidence is missing during postmortem investigations.
- Begin the process of working alongside your PR and communications team to put your crisis communications plan in action. You should have a plan for how to handle customer and partner relationships, bad press, and media inquiries about the breach. Have a drafted standard response and work with the team from there.
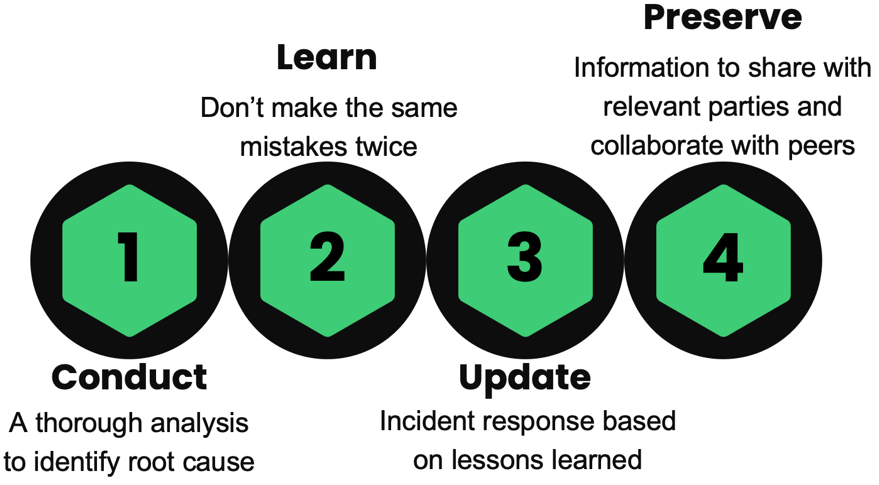
Incident response – After the Incident
What to do after the attack
When the dust settles and the attack is ‘over,’ it is crucial to learn from the experience and strengthen your organization’s cybersecurity defenses and prepare you for future attacks.
- Conduct a thorough analysis of the incident to identify root causes and vulnerabilities.
- Learn from the attack and plan to implement suggested and recommended security measures to prevent similar attacks in the future. Don’t make the same mistake twice or more.
- Review and update your incident response plan based on the lessons learned.
- Preserve what has been learned and plan to share information about the attack with relevant parties and collaborate with industry peers to improve overall cybersecurity.
Always be prepared. If you don’t have any or all of these mechanisms in place, today is a good day to start. I am reminded of a Chinese proverb, “The best time to plant a tree was 20 years ago. The second best time is now.”
Handling a cybersecurity breach in your supply chain requires a well-planned and coordinated response. It is essential to identify the breach, assess the damage, notify affected parties, and take steps to mitigate the damage. Start today.

